Abstract
With the rise of cloud manufacturing technology, reversible watermark technology in the encryption domain has gradually received more attention. However, the majority of existing algorithms can only be applied to carriers with high redundancy such as images and videos, and are difficult to resist common attacks, and even can only extract watermarks in a single domain. In response to this, this paper proposes a completely separable two-dimensional vector graph encryption domain robust reversible watermark algorithm for two-dimensional vector graphics with low redundancy. Firstly, the content owner uses the encryption key to displace the polar angle of the vertices under the polar coordinate system to encrypt the graphics. Subsequently, the watermark embedder maps the encoded watermark bits to different vertices under the control of the embedding key and the hash function, and then slightly adjusts the polar angle of the vertices to embed the watermark. Since the decryption operation does not affect the watermark that has been embedded, the algorithm can extract watermarks in the plaintext domain or the ciphertext domain separately. Experimental results and analysis show that the algorithm not only has good invisibility but also can effectively resist common operations such as rotation, translation, scaling (RST), and entity reordering, and even can resist malicious attacks such as the addition or deletion of vertices or entities.
Introduction

In recent years, with the popularization of computer-aided design/computer-aided manufacturing technology (CAD/CAM), two-dimensional vector graphics have been widely used in the design industries of many fields such as the mechanical industry, construction industry, and clothing industry. As an important manufacturing data, the intellectual property protection and content integrity authentication of two-dimensional vector graphics are extremely important. Although the existing watermark methods [1]-[9] can provide a certain degree of protection for the plaintext two-dimensional vector graphics, they are either irreversible [1]-[3] or not robust enough [4]-[9], and more importantly, they cannot adapt to the application needs of the current cloud manufacturing development. Since the two-dimensional vector graphics stored in the cloud are completely exposed to third parties, data is prone to leakage, so data encryption is usually used to protect the content of two-dimensional vector graphics. At the same time, in order to facilitate the management of encrypted data in the cloud, managers also hope to add some additional information in an invertible way in the encrypted two-dimensional vector graphics, such as source information, authentication data, or copyright information, etc. To solve this problem, reversible information hiding technology in the encryption domain has received extensive attention in recent years. This technology first encrypts the carrier to ensure data security, and then embeds watermark information into the carrier through reversible watermark technology to achieve copyright protection, secret information transmission, and other functions.
Currently, research on reversible information hiding in the encrypted domain mainly focuses on raster images [10]-[20], and research on two-dimensional vector graphs is relatively less [21]. In addition, most existing reversible watermarking algorithms in the encrypted domain do not have the robustness of watermark extraction, that is, after the decryption of the carrier is modified to a certain extent, the watermark cannot be extracted correctly, which cannot meet the needs of applications such as copyright authentication and carrier tracing. Therefore, how to improve the robustness of watermark extraction in reversible watermarking algorithms in the encrypted domain has become an important problem that needs to be solved in the field of reversible information hiding in the encrypted domain. To this end, this article proposes a completely separable two-dimensional vector graph encryption domain robust reversible watermarking algorithm. The main contributions of this article include:
1. A completely separable two-dimensional vector graph encryption domain robust reversible watermarking scheme is proposed. According to public literature, this scheme is the first vector graph watermarking scheme that can robustly extract hidden information separately in the plaintext domain or ciphertext domain. 2. A watermark mapping method based on the graphic polar coordinate system, hash message authentication code, and erasure coding is proposed. The relationship between watermark redundancy and watermark full coverage probability is analyzed. Experimental results show that compared with existing similar algorithms, this watermark mapping method has good robustness against common operations and malicious attacks. 3. The maximum distortion and average distortion of the two-dimensional vector graphic watermark are theoretically analyzed, and the experimental results also verify the correctness of the theoretical analysis. In addition, the experimental and analytical results of the proposed algorithm show that the proposed algorithm is not only reversible but also has good invisibility.
The rest of the article is organized as follows: the second part introduces and analyzes the relevant work of existing reversible watermarks in the encrypted domain; the third part introduces the relevant technologies used in this article; the fourth part proposes a two-dimensional vector graph encryption domain reversible watermarking algorithm; the fifth part is the experimental results and analysis; and the sixth part is the conclusion.
Related work
Information hiding in the encrypted domain is hidden in the early research stage, which simply combines encryption and information hiding, using part of the carrier data for encryption, and the rest for embedding information. For example, the reversible encryption and watermarking algorithm for video compression proposed by Lian S et al. [22]. The algorithm only encrypts the symbols of intra-frame prediction mode, motion vector difference, and DCT coefficients, while embedding the watermark into the amplitude of the DCT coefficients. Since this type of method only encrypts part of the carrier, there is a risk of information leakage when the data correlation of the carrier is high. Currently, existing research organically combines two technologies, and the existing methods can be divided into two major categories according to the different embedding spaces before and after encryption: pre-encryption space (VRBE) and post-encryption space (VRAE) [23].
Space Allocation Before Encryption
The algorithms of the VRBE class need to perform additional preprocessing operations before encryption to allocate space for the information to be embedded. Kede Ma et al. proposed the first VRBE method [10], in which the content owner embeds the least significant bit (LSB) of specific pixels into other pixels using traditional reversible information hiding methods [24] to allocate space. The preprocessed image is then sent to the data hider. The data hider can directly hide information in the LSB of these specific pixels. Yi et al. proposed a reversible information hiding method for encrypted images based on the binary block embedding (BBE) method [11]. After allocating space with BBE and encrypting the image, secret information can be embedded in it. Cao et al. proposed a large-capacity reversible information hiding method for encrypted images based on sparse block representation [12]. This method generates a prediction error sequence with smaller information entropy through sparse block representation, thus allocating more space, making the algorithm have higher capacity. However, due to the need for negotiation between the content owner and the data hider in such methods, there is a risk of information leakage.
Space Left After Encryption
Compared with the previous method, the original carrier does not need to undergo additional preprocessing before encryption. Based on the timing of extracting hidden information, the VRAE method can be further divided into three basic categories: plaintext domain extraction algorithm, ciphertext domain extraction algorithm, and dual domain extraction algorithm.



Preliminary Knowledge

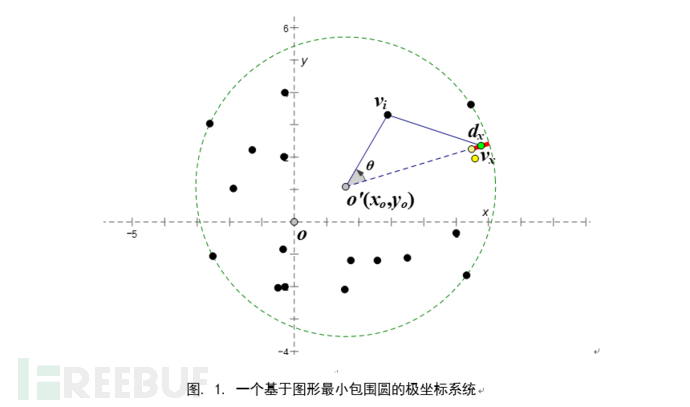
Polar Coordinate System Based on Minimum Bounding Circle
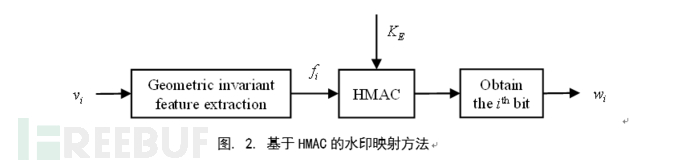
Watermark Mapping Method Based on HMAC
Erasure Code


Algorithm Description
Graphics Encryption

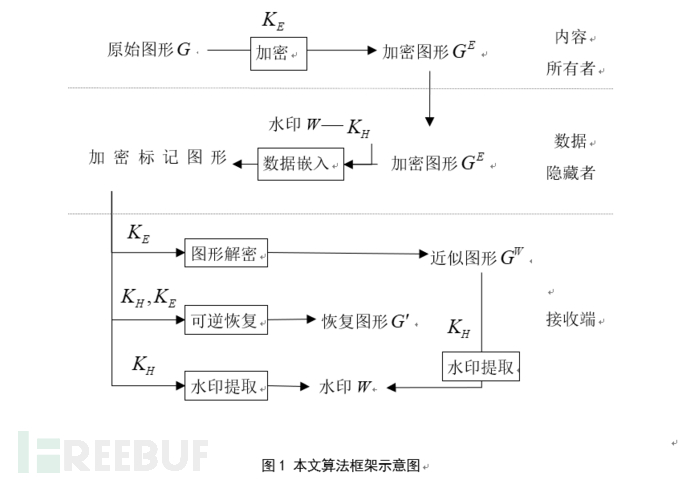

Watermark Embedding



评论已关闭