The China Software Evaluation Center (China Software and Integrated Circuit Promotion Center of the Ministry of Industry and Information Technology) issued an announcement on October 20, 2021, planning to select a batch of excellent technical support units with high technical level and strong sense of social responsibility in the fields of APP products, mobile Internet security, and other enterprises and institutions. As of November 8, more than 40 units have applied for the second batch of technical support units for the MIIT Mobile Internet APP Product Security Vulnerability Database. The Special Working Group for Vulnerability Management has conducted preliminary review of the application materials, selected some units for review and defense, and a total of 7 units have passed the capability examination. From the date of this announcement, the following 7 units are newly added as technical support units for the CAPPVD vulnerability database (in no particular order):
01 Shanghai Douxiang Information Technology Co., Ltd.
02 Beijing Hongteng Intelligent Technology Co., Ltd.
03 Wuhan Antiy Information Technology Co., Ltd.
04 Software Research Institute of China United Network Communications Co., Ltd.
05 Beijing Yongxinzheng Technology Co., Ltd.
06 Beijing Anpuno Information Technology Co., Ltd.
07 Beijing Baidu Netcom Technology Co., Ltd.
At the same time, the Special Working Group for Vulnerability Management plans to conduct capability examinations for the following applicants from November 26, 2021, to December 25, 2021. During this period, the units under examination are required to report vulnerabilities on the MIIT Mobile Internet APP Product Security Vulnerability Database platform to prove their relevant capabilities.
Currently, the units that need to be examined for capabilities are (in no particular order):
Beijing Nagas Information Technology Development Co., Ltd., Beijing Huitert Technology Co., Ltd., Beijing Times Newwei Information Technology Co., Ltd., Beijing Yunce Information Technology Co., Ltd., Beijing Zhenan Tianxia Technology Co., Ltd., Xinjiang Quantum Communication Technology Co., Ltd., Jiangsu Tongfudun Information Security Technology Co., Ltd., Jiangsu Junan Information Technology Evaluation and Certification Co., Ltd., Zhejiang Yuanan Information Technology Co., Ltd., Shandong Xinchao Information Technology Co., Ltd., Zhejiang Dahua Technology Co., Ltd., Zhaowang Digital Technology (Shenzhen) Co., Ltd., Shenzhen Net Security Computer Security Detection Technology Co., Ltd., Shenzhen Nengxin'an Science and Technology Co., Ltd., Zhengzhou Yunzhixin Security Technology Co., Ltd.
The Special Working Group for Vulnerability Management will continue to select and publicize some support units based on the relevant capabilities reported by the units during the examination period.
The attached table is the list of technical support units for the CAPPVD vulnerability database as of November 26, 2021:
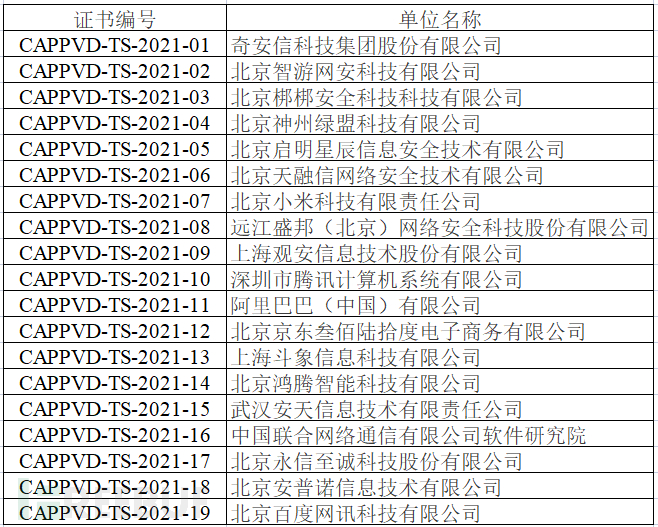
Contact Person: Huang Zeng/Qin Xiaolei
Contact Phone: 13811563856/18510844188
Email: cappvd@cstc.org.cn
Address: No. 66 Zizhu Yuan Road, Haidian District, Beijing
China Software Evaluation Center
(China Software and Integrated Circuit Promotion Center of the Ministry of Industry and Information Technology)
November 25, 2021
Source: https://mp.weixin.qq.com/s/uaYBFw9lacI0kg4VTqSexw
评论已关闭
