



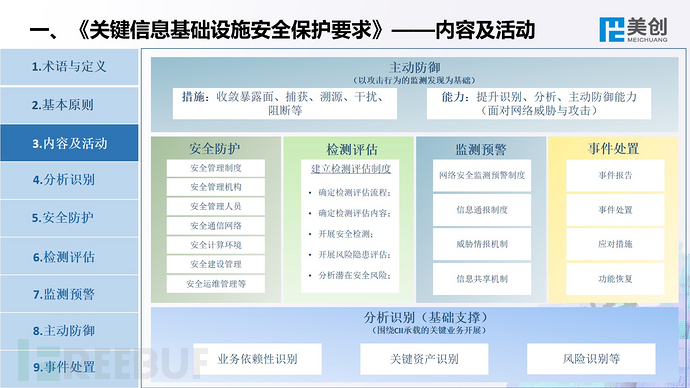
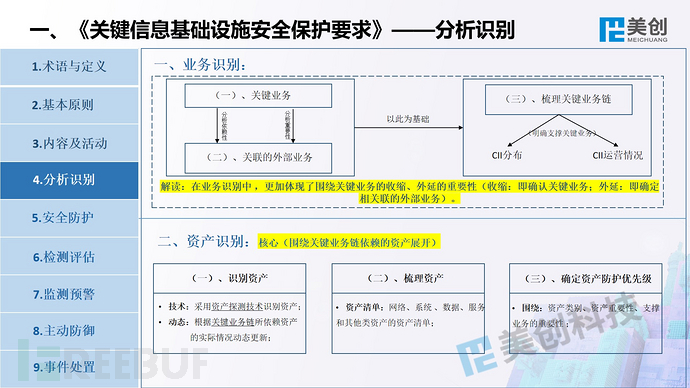
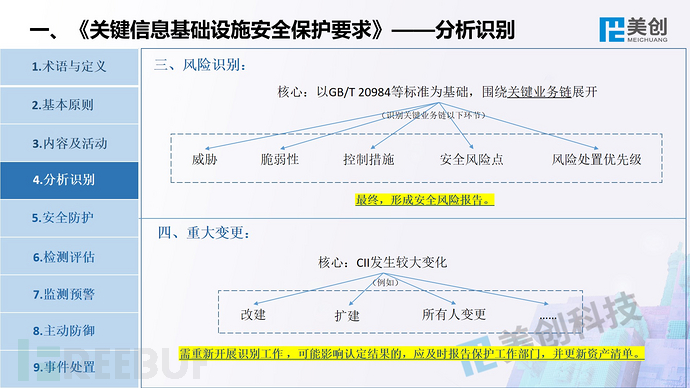


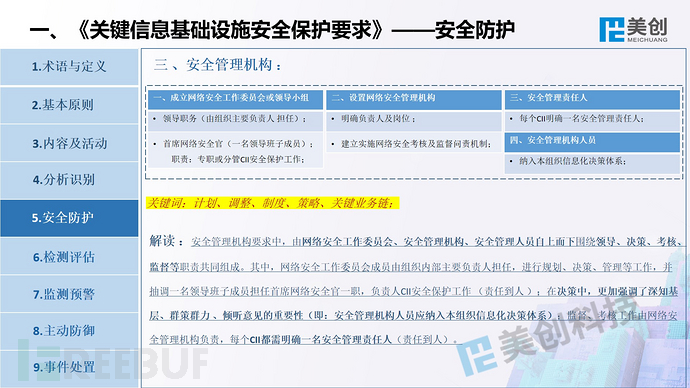

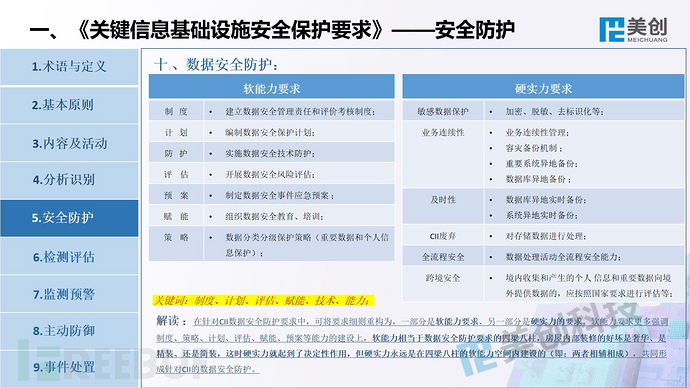
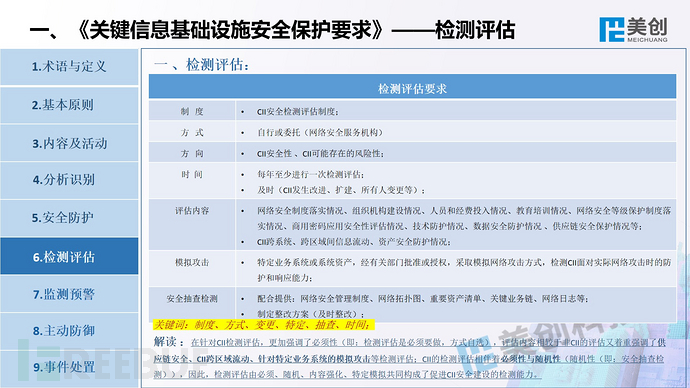

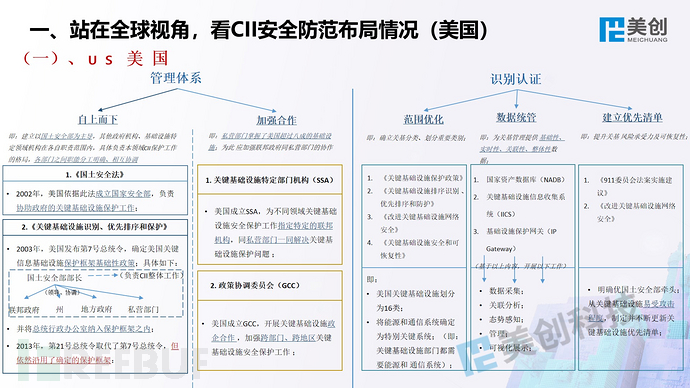

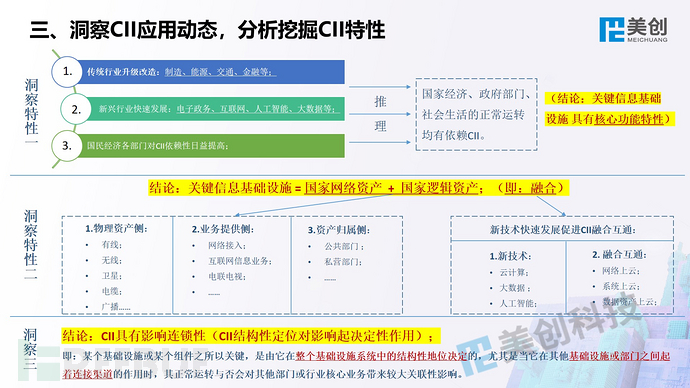


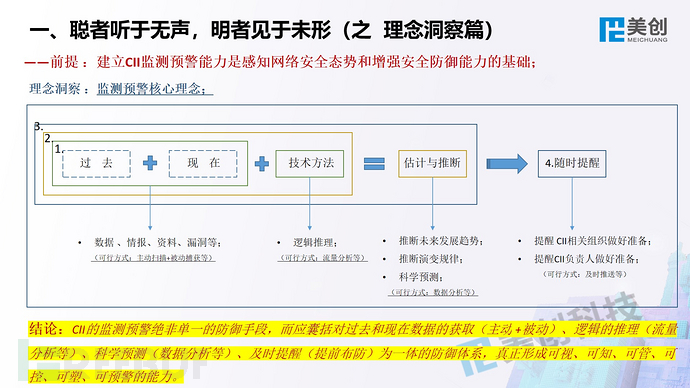
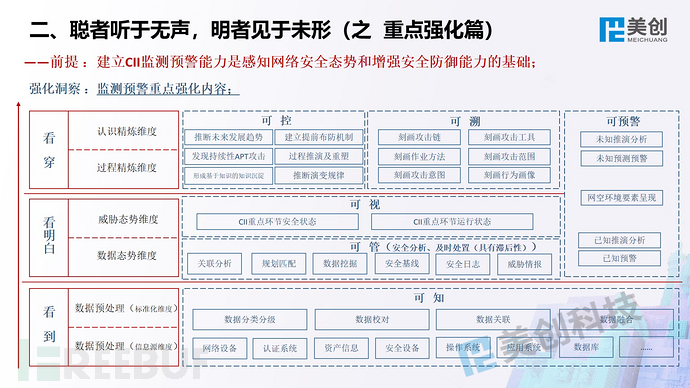
 This is the perspective of Meicreate experts, welcome everyone to communicate and correct
This is the perspective of Meicreate experts, welcome everyone to communicate and correct
你可能想看:
最后修改时间:
Interpretation and Practice of the Requirements for the Registration and Declaration of Medical Device Network Security
上一篇
2025年03月30日 10:43
Intersection & Union Types (Intersection and Union Types)
下一篇
2025年03月30日 11:06
评论已关闭