Before the evaluation, first collect information about the assets, check the version of the corresponding system
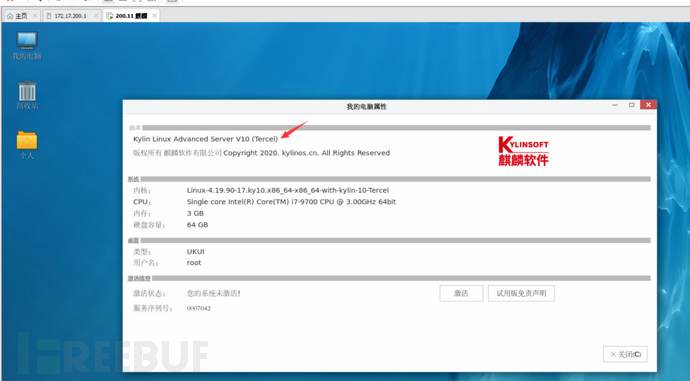
Right-click My Computer → Properties

First of all, Identity Authentication
a) Identify and authenticate the user logging in, with unique identity identification and complex authentication information requirements that need to be changed regularly
1. Current Situation
Confirm whether the user has adopted identity authentication measures during the login process (usually username + password) and whether there is an empty password account. cat /etc/passwd The second field of each user in this file is not empty. Confirm whether the current password has complexity and whether it is changed regularly. The same as the way to view in Linux
According to the default configuration of the previous Linux system, local test can be done without password login
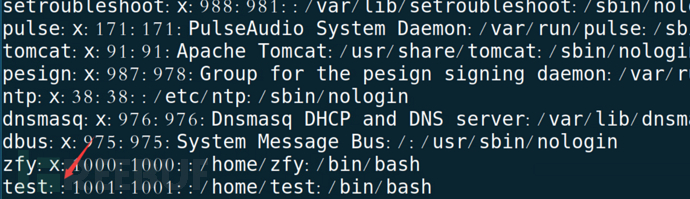
But Kirin OS has done corresponding security reinforcement configuration by default. After installation, check /etc/ssh/sshd_configThe default value of the file PermitEmptyPasswords is no, which cannot log in via SSH with an empty password (SSH empty password login requires PermitEmptyPasswords yes)
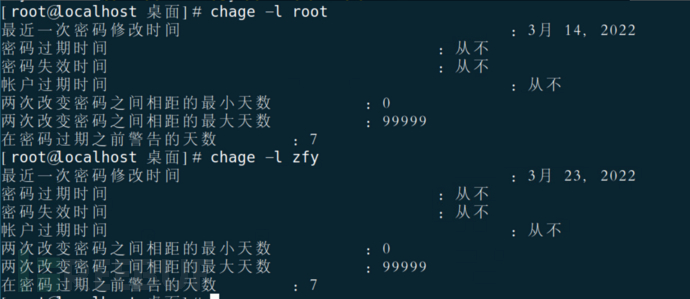
View the last modification date of the password and the maximum changeable date of the password
chage -l username
2. Operating System Mandatory Policy
① Password Complexity
Configuration file:/etc/security/pwquality.conf
The corresponding mandatory password complexity strategy is already configured by default
Parameter Description:
debug: Write debug information to the log (don't understand, won't test)
type=xxx: When adding/modify password, the default prompt given by the system is 'New UNIX password' and 'Retype UNIX password'. This parameter can be used to customize the prompt for inputting the password. (e.g., password requisite pam_cracklib.so type=1111111)
retry=N: The number of retries allowed for password modification, returning an error when the password modification fails
difok=N: The number of different positions required between the new password and the old password
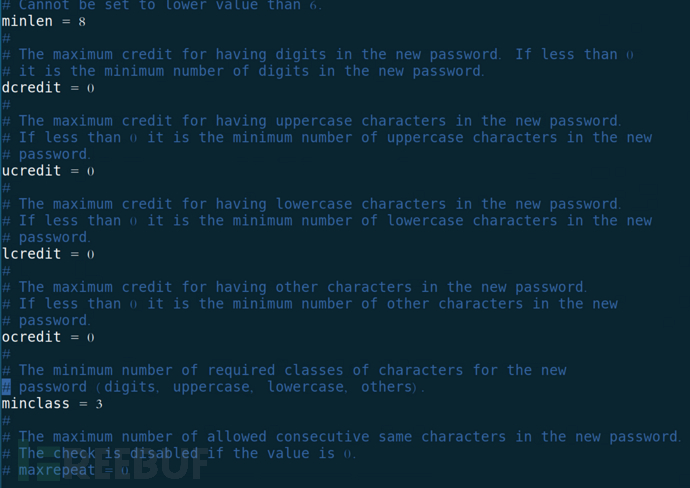
dcredit=N: N >0 The maximum number of digits in the password plus 1;
N<0 The minimum number of digits in the password
lcredit=N: Number of lowercase letters
ucredit=N: Number of uppercase letters
ocredit=N: Number of special letters
minclass=N: Password composition (uppercase/lowercase letters, numbers, special characters)
minlen=N: Minimum password length
In the Linux operating system, `minclass` is a parameter of the password complexity strategy, used to define the minimum required number of character categories in the password. Character categories include uppercase letters (A-Z), lowercase letters (a-z), numbers (0-9), and special characters (such as !@#$%^&*()).
When `minclass` is set to a positive integer value, it means that the password must contain at least the number of character categories specified by that integer value. For example, if `minclass` is set to 2, the password must contain at least two different character categories (such as numbers and uppercase letters).
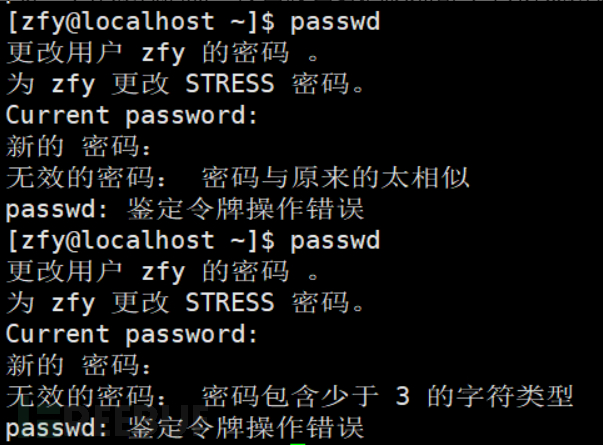
Test minclass=3, and it is not possible to configure a simple password successfully
② Password Expiration Time
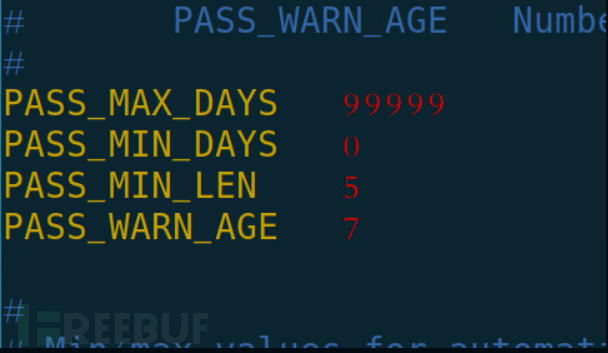
Configuration file:/etc/login.defs
By default, it is still 99999 days
b) It should have login failure handling functions, and related measures such as session termination, limiting the number of illegal logins, and automatic logout when the login connection times out should be configured and enabled
1. Login Failure Handling Function
Configuration file:/etc/pam.d/password-auth
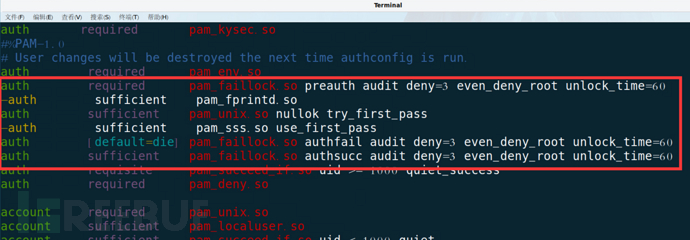
By default, logging in fails 3 times and locks for 60 seconds, including all accounts, both local login and SSH remote login
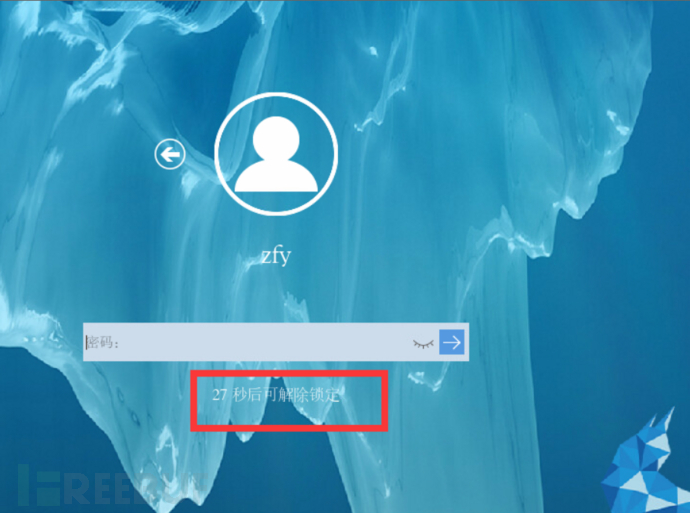
2. Operation Timeout
Graphical desktop: Control Panel → Power Management
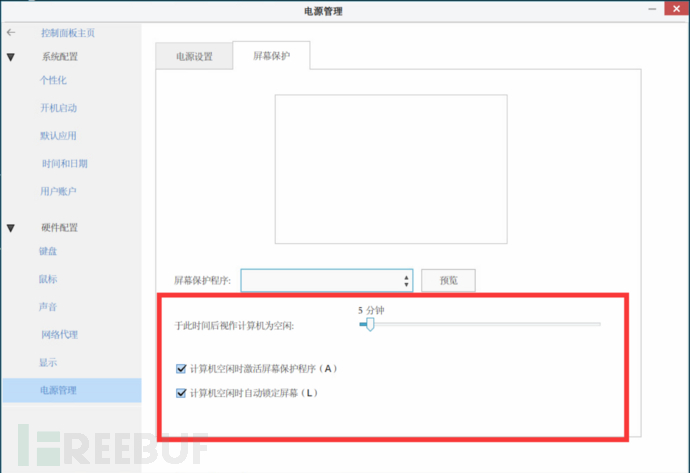
Default is 5 minutes
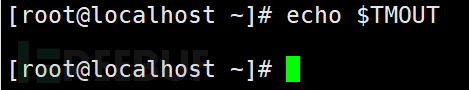
Check the TMOUT value in SSH remote management mode
echo $TMOUT to check for corresponding output, default is none
c) When performing remote management, necessary measures should be taken to prevent the interception of identification information during transmission over the network
netstat -tlnp|more to view the remote management method, and confirm whether only SSH is used for management
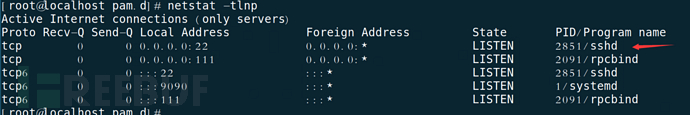
d) Adopt identification technologies such as passwords, password technologies, biometric technologies, and combinations of two or more to identify users, and at least one identification technology should be realized by password technology
On-site inspections generally only use username + password or username + key for management.
Second, Access Control
a) Assign accounts and permissions to the users logging in
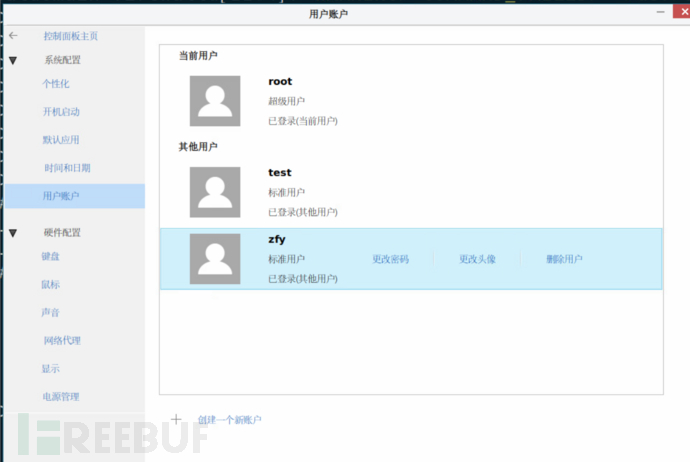
1. Determine the current account status
By checking the /etc/passwd, /etc/shadow, /etc/group files, you can view which ordinary accounts are available for login, as well as the user group situation.
Control Panel → User Accounts can also be viewed
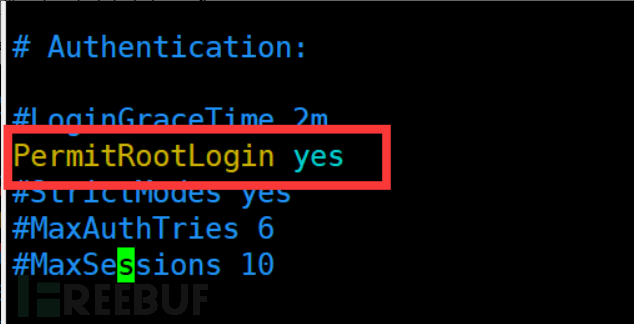
2. Determine whether to limit root account permissions
Configuration file:/etc/ssh/sshd_config
Confirm that PermitRootLogin is set to no
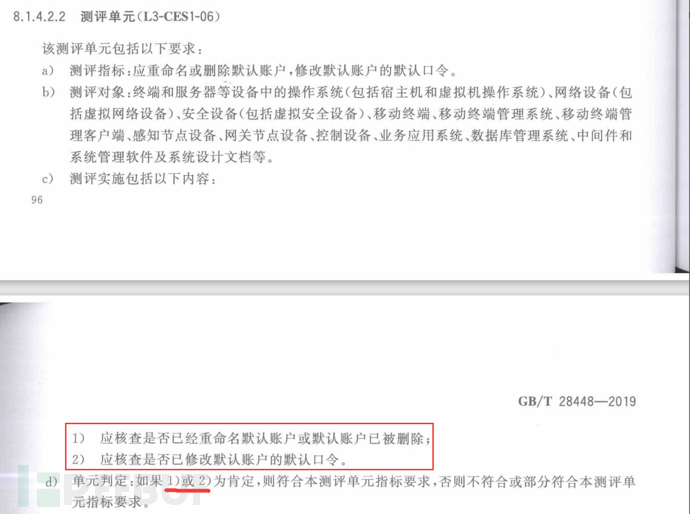
b) Rename or delete the default account, and change the default password of the default account
Based on the determination requirements of 28448, it can be judged as compliant if it meets 1 or 2
评论已关闭