Preface
A CyberVolk ransomware that has recently gained popularity, also known as the ".cvenc" file virus. It is designed to encrypt files and add the ".cvenc" extension to the file names. CyberVolk will also display a pop-up window and create a disk file named "CyberVolk_ReadMe.txt", which contains ransom information. CyberVolk is not spread through email. Similar to other ransomware (such as GandCrab, WannaCry, etc.), CyberVolk not only encrypts the computer of the victim but also demands ransom payment to decrypt all encrypted files.
Ransomware process



Open the file for modification:
C:\Users\Admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\desktop.ini
File created:
C:\Users\Admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\desktop.ini.cvenc
File created:
C:\Users\Admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\CyberVolk_ReadMe.txt
Behavioral analysis
Detect It Easy (DIE) is a cross-platform tool for identifying file types, also commonly used for malicious software analysis. It has an open architecture that allows users to customize recognition rules and algorithms.
The main functions of Detect It Easy include:
- Identify multiple file types:DIE can identify over 200 file types, including common executable files, script files, compressed files, and more.
- Identify file packers and obfuscators:DIE can identify common file packers and obfuscators, such as UPX, ASPack, and others.
- Analyze file entropy:DIE can calculate the entropy value of the file, helping to identify files that may have been encrypted or obfuscated.
- View file structure:DIE can display file header information, segment information, import table, export table, and more, helping to analyze the internal structure of the file.
- Use scripts to customize recognition rules:DIE supports the use of scripting languages to write custom recognition rules, expanding its functionality.
The scan results indicate that ransom.exe is a 32-bit Windows executable file that runs on the Windows Vista operating system and uses console mode. The file is compiled by the Microsoft Visual C/C++ compiler using version 2017 (v.15.5-6) and version 19.36.33522, and linked with Microsoft Linker 14.36.33522. The final program was created in Visual Studio 2022 version 17.6, and it appears to be unobfuscated.

After opening with IDA, click the HexView-1 tab directly to display the hexadecimal window. This window can display the hexadecimal dump content and the corresponding ASCII characters. By default, the hexadecimal window is synchronized with the disassembly window, which means that the selected byte data in the disassembly window will be highlighted in the hexadecimal window. This synchronization feature helps to mark memory addresses.
The hexadecimal view window (hex view window) not only displays the hexadecimal dump content, but also displays the string information in the executable file (exe). These string information usually includes various text data used in the program, such as error messages, debugging information, file paths, user interface text, etc. By viewing these strings, analysts can obtain clues about the program's functions and behaviors, which helps to understand and reverse engineer the executable file.
Here we can view the relevant ransom information! The ransomware is named "CyberVolk ransomware". All files of the victim have been encrypted. The ransomware demands that the victim pay 1000 USD in Bitcoin (BTC) to obtain the decryption key. The ransomware provides their Telegram channel (@hacker7) and team website (https://t.me/cubervolk) as contact information. The ransomware warns the victim not to try to recover the files themselves, otherwise the files may be permanently lost.

and you can also see the ransomware EXE,0042A7E0-0042A8F0: Here are some common Windows API functions, such asMessageBoxW,BeginPaint,InvalidateRect,LoadImageW,FindWindowA,DialogBoxParamW,SystemParametersInfoW,KillTimer,SetRect,GetDlgItem,wsprintfW,SetClipboardData,LoadBitmapW,MessageBoxA,EmptyClipboard,CloseClipboard,DrawTextA,SetTimer,GetDlgItemTextA,OpenClipboard,ShowWindowetc., these functions provide basic means of interaction with the Windows operating system, used to create and manage windows, handle messages, process images, operate the clipboard, format text, and timers, and various other tasks

It also calls some functions in Windows system DLLs, such as functions in USER32.dll and GDI32.dll, and finally calls the SHGetFolderPathA function in SHELL32.dll, which may be related to file operations. Well, that's all for the hexadecimal view window for now; roughly, you can also view some processes in this way, depending on personal preference.

desktop.ini file
As introduced earlier, all files seem to be encrypted through a desktop.ini file, and the encrypted file is like this desktop.ini.cvenc, (from5fe19b0927...Starting) may be actual encrypted data. This data is very likely to be a binary file or text encrypted by some encryption algorithm (such as AES, RSA).

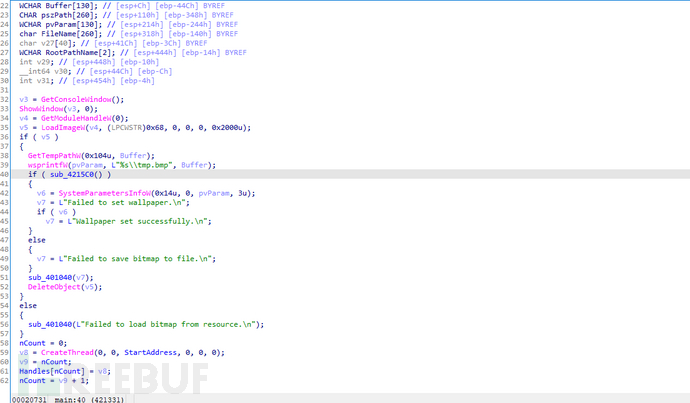
Wallpaper setting action
The code calls the SystemParametersInfoW function, which is a Windows API used to set and retrieve system parameters, including changing the desktop wallpaper. The first parameter of the SystemParametersInfoW function call is 0x14 (SPI_SETDESKWALLPAPER), indicating that the desktop wallpaper is to be set. The third parameter pvParam is the path of the new wallpaper file. The fourth parameter is 3u, indicating that the settings are updated immediately (including in the registry).
mov ecx, offset aFailedToSetWal: Move the address of the string"Failed to set wallpaper.\n"toecx. This string may be used to display error messages when the operation fails.mov edx, offset aWallpaperSetSu: Move the address of the string"Wallpaper set successfully.\n"toedx. This string may be used to display success messages when the operation is successful
[SystemParametersInfoW API Parameters]
At first, I didn't find any registration addition actions, but later it might have been due to the reason of using the API, taking advantage of the registry modification. To verify my specific case, I had to look it up
C:\Users\otsan\AppData\Local\Temp\\tmp.bmp

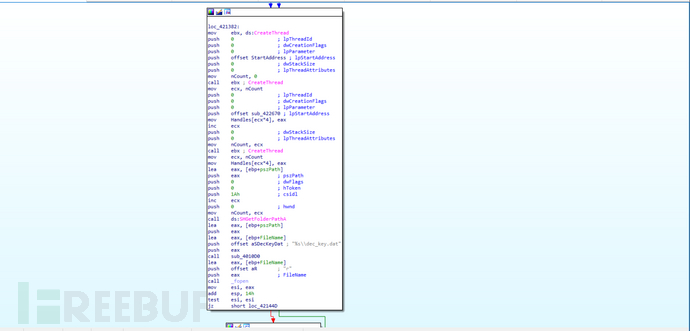
File creation action
[File Creation]
By creating threads with CreateThread, and then callingSHGetFolderPathAfunction, get the path of the specified folder, and]}pszPathaddress is loaded into the registereax.push offset aSDecKeyDat ; "%s\dec_key.dat": Push the string-formatted address (including the format string "%s\\dec_key.dat" for path and filename) onto the stack.aSDecKeyDatis pushed onto the stack assub_4010D0function's parameters to generate file paths. Specifically,sub_4010D0function will replace%splaceholder to generate the complete file path for storage.


Enum drive
Enum drive allows ransomware to scan the entire computer system, including all connected hard disk drives and network drives. This ensures that as many files as possible are encrypted, thus maximizing the ransomware's potential profits.

- Initialize the drive letters from
'a'to'z'(that is, from97to122()). - In the loop, by modifying
RootPathNameto traverse each drive letter and callGetDriveTypeWfunction checks the drive type. GetDriveTypeWThe returned value minus2The return value is mapped to0,1or2indicates an invalid drive.- If
GetDriveTypeWThe returned type does not equalDRIVE_NO_ROOT_DIR,DRIVE_REMOVABLEandDRIVE_FIXEDis considered a valid drive. - For valid drives, create a new thread (
sub_422100)for processing.
IOC
CyberVolk_ReadMe.txt
MD5 ce7ff0a9361571a2dcb08f50500ace3f SHA1 5d8bed459f55a37e2fcb801d04de337a01c5d623 SHA256 894bc59f5227b4d545412b2a2897367d7ac88090c86f5a1728bf733e70bd93ee SHA512 bba6d46fae5b4099b047b192f7df21fdf01675b09f3da38a365710fc9aa5b126cc6a2c2547be48deecfaa360e1521cf04a9793af083735de4a8cb7be9bd4c52a
ransom.exe
MD5 648bd793d9e54fc2741e0ba10980c7de SHA1 f5d0c94b2be91342dc01ecf2f89e7e6f21a74b90 SHA256 102276ae1f518745695fe8f291bf6e69856b91723244881561bb1a2338d54b12 SHA512 d1428b934a360d7f3651947d11081892c93c7cd29a17dc38190cbb46c95939928ac6f805adf586be2937e27fc20aec8bd1fc2c782c681e7e94e9e8d33b8ebf15
The evolution of ransomware strategies
Be alert to the incoming new ransomware, the ransom note information uses German!
Has the 'new king' of ransomware appeared? RansomHub has targeted 600 enterprises in 2024
Cybercrime has shifted to social media, with attack volume reaching an all-time high.
Let's talk about neurodiversity in cybersecurity
The rise of Ransomware as a Service
hire hacker in kolkata(Kolkata)
Eight ways microlearning makes cybersecurity training more effective
From the perspective of devices, the medical industry has become a key area of cybersecurity
Follow the Cybersecurity Medicine Water Brother to fight the target field (emergency response)
评论已关闭