With the development of Internet technology, IT, IoT, and OT technologies have integrated into traditional industries, especially the digitalization of the medical industry has greatly improved daily work and medical care efficiency. However, the emergence of new technologies also brings greater risks, and the increasing network security risks that are difficult to manage and control. According to the research report of Forescout Technologies, the number of IoT devices is increasing rapidly in recent years and is still threatened by the traditional IT industry.

Forescout Technologies conducted a survey on the cybersecurity of the current medical industry and published the results of the survey on 75 survey targets. The survey targets included more than 10,000 virtual local area networks (VLANs) and 1.5 million devices in the Forescout cloud, with the main focus on 1,500 medical VLANs and more than 430,000 devices.
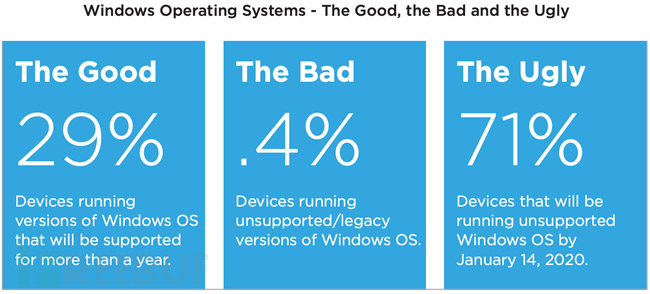
Overview of the current status of Windows devices
The likelihood of medical equipment being attacked is gradually increasing
Researchers have found that, on the medical network, the most common devices are still traditional computer equipment, accounting for about 53%, followed by Internet of Things (IoT) devices, accounting for about 39%. IoT devices include network printers, VoIP phones, tablets, and smart TVs, among others. OT devices include general medical equipment, intensive care systems, building automation systems, and public facilities involving physical security, accounting for 8% of the total network medical equipment.
In the category of OT devices, the three most common medical devices are patient tracking identification systems, infusion pumps, and patient monitors, accounting for 38%, 32%, and 12% respectively. With the increasing frequency of vulnerabilities in OT devices, the threats to the medical environment are also increasing.
Windows systems occupy the largest proportion
Among all the medical products investigated, the survey of cloud devices shows that about 71% of the devices use Windows systems, including Windows 7, Windows 2008, and Windows Mobile, which will all expire around January 14, 2020.
Running unsupported operating systems may bring risks of vulnerabilities or exposure of critical information, and also have an impact on regulatory compliance.
Too many types of operating systems and suppliers
The diversity of medical equipment suppliers and systems has increased the complexity of their network security to a certain extent, and has also brought greater challenges in terms of security. According to the research, 40% of medical equipment has deployed more than 20 different operating systems. Among all the VLAN objects investigated, Windows systems account for 59%, and the remaining 41% are distributed among mobile, embedded firmware, and network infrastructure.
In addition, more than 30% of medical equipment may have more than 100 related equipment suppliers. (The existence of so many suppliers is also to deal with some possible unforeseeable emergencies)
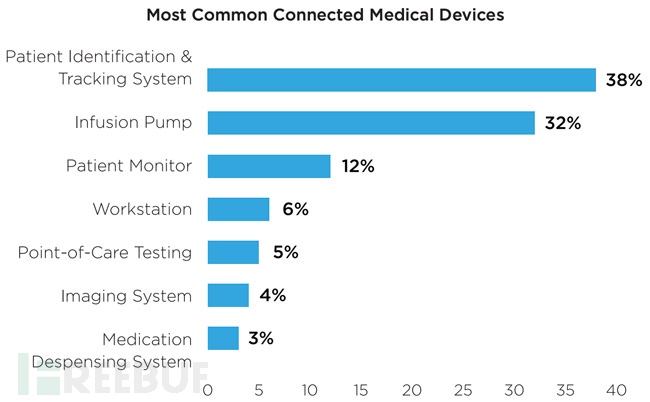
Proportion of common medical equipment
The threat to the protocol is increasing
Among all medical devices using the Windows operating system, more than 85% of the devices have enabled the SMB protocol, which may allow external attackers to enter the network system and obtain administrative privileges. Many manufacturers will enable the corresponding port by default, and this behavior is often ignored by IT or security personnel.
Medical information is of great value. In recent years, the electronic medical records, hospital cloud computing, and long-distance consultation have been carried out vigorously in the medical field. Information such as identity information, residential address, medical history, and bank accounts are directly linked to wealth, making medical data a favorite target for the black industry. As an important issue concerning people's livelihood, the information security in the medical field will also be a top priority for network development in the near future.
*Reference Source:helpnetsecurityCompiled by Karunesh91, please indicate the source as FreeBuf.COM when reproduced
评论已关闭