Preface
In recent years, frequent incidents such as network intrusion, information leakage, and network viruses have occurred. At the national level, a number of data security-related laws and regulations have been successively issued. As a key industry under strict supervision by the state, the financial industry has drafted and issued various relevant industry standards and specifications in accordance with the upper-level laws and regulations. In addition, combining with the fact that the basic infrastructure and information systems of the author's company have been constructed for many years, some application systems, management platforms, and equipment need to be updated and replaced, and reorganized. In this situation, it is of great significance to comprehensively carry out the company's cyber security planning and scientifically and reasonably promote the construction of cyber security.Given that the cyber security construction of most financial institutions is at the same level as our company, except for the leading institutions in the industry that are at the forefront of maturity and technological innovation, this planning project of our company is proposed to lead the way for discussions with fellow industry professionals.
I. Project Implementation Background
(I) The requirements for cyber security supervision are becoming increasingly strict
In response to the objective reality and urgent needs of the cyber security situation at home and abroad, a series of laws, regulations, and regulatory requirements have been successively introduced domestically, such as the 'Cyber Security Law', the series of standards of 'Cyber Security Grade Protection' (Level Protection 2.0), the 'Data Security Law', the 'Regulations on the Security Protection of National Key Information Infrastructure', and the 'Personal Information Protection Law', which have put forward more comprehensive and strict new requirements for the management of cyber security, data security, and personal information security.
(II) Cost reduction and efficiency improvement in the implementation of cyber security construction

The digital construction of the current company has entered the fast lane, and through a series of projects such as network transformation, cloud management platform construction, and enterprise service bus construction, networks are connected, resources are integrated, and interactions and sharing are achieved. Therefore, under the background of comprehensive information construction and security compliance, how to implement the synchronous construction of cyber security through overall planning and intensive construction, improve the compliance of cyber security management, and avoid excessive construction of cyber security and excessive resource investment is an urgent problem that needs to be solved.
II. Project Construction Content
(One) Overall construction思路
The company has already possessed the most basic security management infrastructure, completed the division and construction of the internal network, unified the internet exit, and also adopted a comprehensive management approach to manage all network resources and server resources.
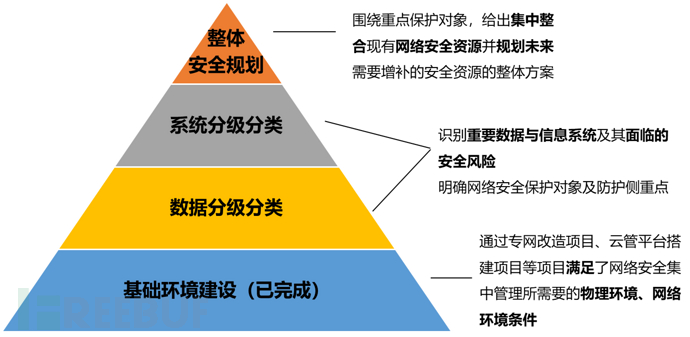 Figure 1 Framework of overall construction思路
Figure 1 Framework of overall construction思路
On this basis, it should continue to follow the principle of deep defense in network security, first clarifying the protection objects of network security and the subsequent protection efforts required through the classification and grading of data assets and the classification and grading of existing information systems.
In the overall security planning stage, it is necessary to sort out and count the existing data distribution, system analysis, and the coverage of network security resources, and combine the classification and grading results of data and information systems, as well as the identified network security technology risks and compliance risks, to provide the most reasonable network security planning solution.
The final planning approach is to allocate network security resources in stages and batches according to the different levels of protection objects and the security risks they face, ensuring that the most comprehensive security protection is provided for important data and systems at the moment, while also maximizing the use of the company's existing and future resources.
(Two) Planning project organization structure
The group leader of the project leadership group is the division leader of the company's network security, and department heads serve as members of the project leadership group.
The project manager is planned to be the head of the IT department, and the project members are the network security special posts, security officers of each department, and third-party security service suppliers.
(Three) Implementation content of each stage
1.Data classification and grading (data compliance risk assessment)
1) Data asset sorting
Work Content:
- A project launch meeting (system research + data research) is held, notifying department heads to arrange and appoint the responsible persons for data asset sorting in their respective departments to participate in the subsequent asset sorting work.
- Training on the use of data asset reporting tools is conducted for the responsible persons of data asset sorting in each department, clarifying the scope, type, and reporting methods of data statistics for the current status of data lifecycle management.
- The project team collects and summarizes the statistical results of data assets from each department, and returns the statistical results that do not meet the reporting requirements for correction.
Work Significance:
- The sorting work of existing data assets has been completed, and the basic work for the formulation of classification and grading principles has been completed.
- A preliminary investigation of the current status of data lifecycle management has been completed.
Output Results:
Data Asset Sorting Table, Data Lifecycle Management Current Status Statistics Table
2) Principle of classification and grading
Work Content:
- Refer to the 'JRT 0197-2020 Financial Data Security Data Security Grading Guidelines', and classify and grade the data summarized by each department based on the existing data classification and grading principles of the company.
- Screen out the categories applicable to the current data status of the company from the industry and group data classification and grading reference standards.
- Combined with the hierarchical classification protection requirements of the industry, the principles of classification and grading are redefined according to the existing data management environment.
Work Significance:
- The classification and grading work is completed based on best practices and the current management status, providing a basis for the subsequent system classification and grading.
- An analysis of the resources required for data security protection at all levels has been preliminarily completed.
Output Results:
Data Classification and Grading Details, Data Lifecycle Assessment Table
3) Data Risk Assessment
Work Content:
Refer to the requirements of laws and regulations such as the 'Data Security Law', 'Personal Information Protection Law', 'GB/T 35273-2017 Information Security Technology Personal Information Security Specification', 'Financial Data Security Data Lifecycle Security Specification JRT0223-2021', etc., combined with the statistical results of 'Data Asset Sorting Table' and 'Data Lifecycle Management Current Status Statistics Table', conduct risk assessment of all links of the data lifecycle through interviews, technical inspections, and other methods.
Work Significance:
Identify the technical and compliance risks of existing data security as an important reference and input for the company's subsequent safety management and overall planning.
Output Results:
Data Security Risk Assessment Report, Data Security Risk Disposal Suggestions
2.Information System Grading and Classification (Full Coverage Assessment of Level Protection)
1) Current Status Research of Information Systems
Work Content:
- Convene the project launch meeting (system research + data research) to notify department heads to arrange and appoint the responsible persons for information system sorting in their respective departments to cooperate with the subsequent research work.
- Train the responsible persons for system sorting in all departments according to the existing system classification and grading definitions of the company;
- The project team collects and summarizes the system statistics results of all departments, and returns the statistics results that do not meet the reporting requirements for correction.
Work Significance:
- Refer to the grading management principles of level protection to conduct an initial sorting of systems, as a reference for the adjustment of subsequent system grading and classification principles;
- Statistical data on the security resources invested in existing systems as an important input for the planning stage.
Output Results:
Summary Table of Information Systems (including business feature descriptions, associated data, and statistics of security resource investment)
2) Establishment of System Grading and Classification Principles
Work Content:
Based on the research results of information systems, combined with the requirements of industry-level protection, compile the classification and grading details of internal systems of the company.
Work Significance:
Compile guidance documents for the security level certification filing of existing information systems and newly constructed systems in the future.
Output Results:
Details of Information System Classification and Grading
3) System Grading and Filing Guidance
Work Content:
Conduct centralized publicity and Q&A sessions for the 'Details of Information System Classification and Grading' and the security level certification filing process for all departments.
Work Significance:
- Establish the basic environment for achieving full coverage of security level certification filing;
- Establish the basic working process for system reporting;
- Avoid over-classification and over-construction of information systems.
Output Results:
- Each department has the independent ability to classify and grade systems and to file for security level certification;
- The initial completion of the process construction for the internal filing of the system.
3.Overall Planning of Corporate Network Security (Intensive Construction, Integration, and Utilization of Existing Resources)
1) Security Management Resource Analysis
Work Content:
Based on the statistical results of security resources at the data and system research stage, combined with the classification and grading results of data and systems, analyze the rationality of the current resource allocation.
Work Significance:
As a reference for the integration of existing resources and the planning of future resources.
Output Results:
Security Management Resource Analysis Report
2) Risk Control Requirement Analysis
Work Content:
Summarize the results of the past year's safety inspections, risk assessments, and security assessment, and combine them with the results of data risk assessment to complete the analysis of risk control requirements.
Work Significance:
As a reference for resource integration and planning, define the key investment direction of security resources.
Output Results:
《Risk Control Demand List》
3)Network Security Management Resource Integration Proposal
Work Content:
Based on the current status of risk control demand and security resource allocation, provide suggestions for the integration of existing network security management resources, and prioritize the rectification content.
Work Significance:
- Define the direction of integrating existing resources;
- Ensure the necessity and effectiveness of resource investment.
Output Results:
《Network Security Management Resource Integration Proposal》
4)Network Security Resource Input Planning
Work Content:
- The project team plans security resources for other risk items after the integration of existing resources is completed, mainly involving personnel organization adjustments, process construction optimization, technical product supplements, and the utilization planning of existing products after the supplement of products;
- Comprehensively analyze the network security strategic direction of the industry and the group, and provide a network security project topic applicable to the current management and development status of the company.
Work Significance:
- Define the direction of additional resource investment within three to five years;
- Provide suggestions for the utilization of old resources within three to five years;
- Ensure the rationality of network security resource allocation within three to five years.
Output Results:
《Overall Network Security Planning Report》
3. Project Input
According to the implementation plan formulated by the project proposal, the total estimated man-days of the project are 92 man-days, and the specific estimated man-days and implementation methods are as follows:
Implementation Stage | Implementation Content | Implementation Method | Man-day Estimation |
Data Classification and Grading | Data Asset Sorting | Interview and Research | 10 |
Principles for Classification and Grading | Document Writing, On-site Reporting | 7 | |
Data Risk Assessment | Interview and Research, Technical Assessment | 14 | |
Information System Classification and Grading | Current Information System Research | Interview and Research | 10 |
Establishment of System Classification and Grading Principles | Document Writing, On-site Reporting | 7 | |
System Classification Record Guidance | Document Writing, On-site Guidance | 5 | |
Overall Network Security Planning | Security Management Resource Analysis | Document Writing, On-site Reporting | 10 |
Risk Control Demand Analysis | Document Writing, On-site Reporting | 5 | |
Existing Resource Integration Proposal | Document Writing, On-site Reporting | 10 | |
Future Resource Input Planning | Document Writing, On-site Reporting | 14 | |
Total Man-days | 92 | ||
4. Project Implementation Period and Nodes
(I) Construction Period
Construction Period: June 20XX to December 20XX
(II) Key Nodes of Project Implementation
Serial Number | Project Implementation Progress | Start Time |
1 | Project Launch | June 20XX |
2 | Data Asset/Information System Sorting Training | June 20XX |
3 | Data Asset/Information System Sorting | June to July 20XX |
4 | Principles for Classification and Grading | July to August 20XX |
5 | Data Risk Assessment | August to September 20XX |
6 | System Classification Record Guidance | September 20XX |
7 | Security Management Resource/Risk Control Demand Analysis | September to October 20XX |
8 | Resource Integration Proposal/Resource Input Planning Compilation | October to November 20XX |
9 | Resource Integration Proposal/Resource Input Planning Review | November to December 20XX |
10 | Project Acceptance | December 20XX |
评论已关闭