出台历程
- Implementation Process
- On September 7, 2018, the 13th National People's Congress Standing Committee announced the legislative plan (a total of 116 items), where the Cryptography Law of the People's Republic of China belongs to the first category of projects: laws with relatively mature conditions and are proposed for consideration during the term of office.
- The draft of the Cryptography Law was submitted for consideration at the 11th Meeting of the 13th National People's Congress Standing Committee on June 25, 2019.
- The 14th Meeting of the 13th National People's Congress Standing Committee passed the Cryptography Law on October 26, 2019.
The Cryptography Law was formally implemented on January 1, 2020.
Regulatory Interpretation
1. What is cryptography?Article 2
The term 'cryptography' as used in this Law refers to the technology, products, and services used to encrypt and protect information and carry out secure authentication by adopting specific transformation methods.
Article 2 of the Cryptography Law clearly defines the term 'cryptography', which does not include commonly known terms such as 'bank card password', 'login password', as well as facial recognition, fingerprint recognition, voiceprint recognition, etc. These passwords are formally called 'passwords', which are a series of characters composed of numbers, letters, and special symbols, used for identity authentication.

2. What do core cryptography, common cryptography, and commercial cryptography refer to separately?The state implements classified management of cryptography.
Cryptography is divided into core cryptography, common cryptography, and commercial cryptography.
Article 7Core cryptography and common cryptography are used to protect state secret information, where the highest security level of the information protected by core cryptography is top secret, and the highest security level of the information protected by common cryptography is confidential.
Core cryptography and common cryptography are state secrets. The cryptography management department shall strictly and uniformly manage core cryptography and common cryptography in accordance with this Law and relevant laws, administrative regulations, and national regulations.
Article 8Commercial cryptography is used to protect information that is not a state secret.
Citizens, legal persons, and other organizations may use commercial cryptography to protect network and information security in accordance with the law.
3. Is it necessary to conduct a cryptography security assessment?
Article 27Key information infrastructure protected by commercial cryptography as required by laws, administrative regulations and relevant national regulations shall be protected using commercial cryptography, and the operator shall conduct a commercial cryptography application security assessment on their own or entrust a commercial cryptography testing institution to do so. The commercial cryptography application security assessment should be connected with the key information infrastructure security detection and evaluation, and the cybersecurity level evaluation system to avoid duplicate assessment and evaluation.
If the operator of a key information infrastructure procures network products and services involving commercial cryptography that may affect national security, it shall, in accordance with the provisions of the Cybersecurity Law of the People's Republic of China, undergo national security review organized by the national cyberspace administration and other relevant departments, including the national cryptographic management department.
Article 37If the operator of a key information infrastructure violates the first paragraph of Article 27 of this Law, fails to use commercial cryptography as required, or fails to carry out a commercial cryptography application security assessment as required, the cryptography management department shall order correction and give a warning; if correction is refused or leads to consequences such as harm to network security, a fine of more than 100,000 but less than 1 million yuan shall be imposed, and a fine of more than 10,000 but less than 100,000 yuan shall be imposed on the directly responsible person in charge.
If the operator of a key information infrastructure violates the second paragraph of Article 27 of this Law, uses products or services that have not been safety reviewed or have not passed safety review, the relevant competent department shall order the cessation of use and impose a fine of more than one times but less than ten times the amount of procurement; for the directly responsible person in charge and other directly responsible persons, a fine of more than 10,000 but less than 100,000 yuan shall be imposed.
The release of this 'Cybersecurity Law' has the biggest impact on non-secret enterprises and institutions, which is that they must actively carry out 'cryptographic security assessment'.
4. Connection with other regulations
- Article 4 of the Cybersecurity Law stipulates: take data classification, important data backup andEncryptionand other measures to maintain network operation security.
- Level Protection 2.0 provisions:Information systems at the third level and above should adopt cryptographic protection, and use cryptographic technologies, products, and services recognized by the national cryptographic management department; pre-launch security testing should be carried out, and a security test report should be issued The security test report should include relevant content of cryptographic application security testing.
- Basic Requirements for Network Security Level Protection (GB/T 22239-2019): Taking the third level as an example, it involves communication transmission in secure communication networks; identity authentication, data integrity, and data confidentiality in secure area boundaries; security scheme design, product procurement and use, and test verification in security construction management; cryptographic management in security operation and maintenance management; mirror and snapshot protection in cloud computing security extension requirements, access control in mobile internet security extension requirements, and other security points, all of which have clear requirements for the use of cryptographic technologies.
- The National Cryptographic Administration'sGM/T 0054-2018 Basic Requirements for Password Application in Information SystemsIt is proposed that the third-grade information system protection should adopt cryptographic technologies that are in line withGM/T 0039-2015 Security Test Requirements for Cryptographic ModulesandGM/T 0028-2014 Security Technical Requirements for Cryptographic ModulesImplement cryptographic operations and key management through corresponding grade cryptographic modules or hardware cryptographic products approved by the national cryptographic management department.
Countermeasures
An encryption system generally consists of three parts:
- Data: the object to be encrypted, the location of the data has a significant impact on the encryption scheme
- Encryption engine: actually performs encryption and decryption operations, with the highest requirements for security and performance
- Key management: handles keys and passes them to the encryption engine
How the three parts are combined determines the ultimate security, which is a common mistake in many encryption schemes. In actual applications, these three parts will be decoupled, such as the encryption engine is in the application, the data is in the DB, and the key is managed by a dedicated facility. Or DB uses TDE (Transparent Encryption), the engine and data are in one system, but the key is elsewhere.
Aliyun Key Management Service:https://help.aliyun.com/product/28933.html
1. Password protection
All data encryption is determined by the location of the data: application, database, file, storage
- Small amount of data encryption/decryption: suitable for encrypting and decrypting data less than 4KB
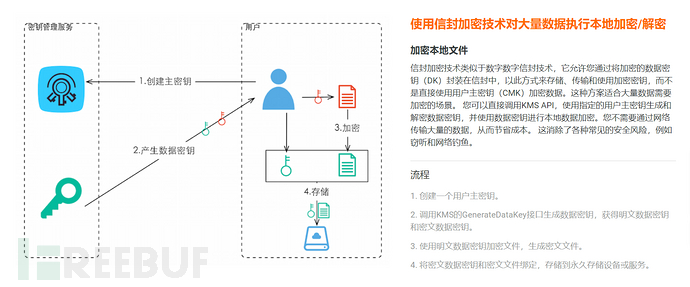
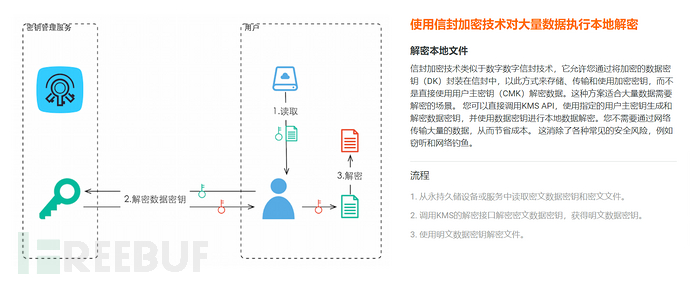
- Envelope encryption: an encryption scheme that comprehensively utilizes symmetric encryption and asymmetric encryption technologies, the purpose of which is to take advantage of the high performance of symmetric encryption and the ease of management of asymmetric encryption. Data is used in storage or communication processesData key (DEK)WithSymmetric encryptionmethod of encryption, and DEK is encrypted throughMaster key (CMK)AdoptAsymmetric encryptionEncryption method for protection, and during decryption, the sender transmits the ciphertext of the data and the DEK ciphertext together, and the receiver first decrypts the plaintext of the DEK, and then decrypts the plaintext of the data through the DEK.
Directly use KMS to encrypt/decrypt a small amount of data

Use envelope encryption technology to perform local encryption/decryption on a large amount of data
2. Key management
Key managementThe lifecycle of the key (generation, authorization, distribution, use, storage, update, backup, destruction) and permission management
Object | Data | Demand | Solve |
Object | Data | Demand | Solve |
Website or application development | Certificate, key | My program needs to use keys and certificates for encryption or signing, and I hope that the key management function is secure and independent. No matter where my application is deployed, I can safely access the keys. I absolutely do not accept deploying plaintext keys everywhere, which is too dangerous. | Using envelope encryption technology, the master key is stored in the KMS service, only the encrypted data key is deployed, and the KMS service is called to decrypt the data key only when needed. |
Background service development | Password, login key, configuration | I do not want to bear the responsibility of the security of the customer's keys and data. I hope that the user manages his own keys; with authorization, I will use the key specified by the user to encrypt his data. In this way, I can focus on the development of service functions. | Based on the envelope encryption technology and the KMS open API, the service can integrate KMS, use the master key specified by the user to complete the encryption and decryption of data keys, and can easily meet the requirement of plaintext not being stored on disk, without having to worry about managing the user's keys. |
CSO | I hope that the company's key management can meet the compliance requirements. I need to ensure that all keys are authorized reasonably, and any use of keys must be audited | KMS service access RAM service to achieve unified authorization management |
3. Password Security Assessment
Currently, the main basis for China's password security assessment isGM/T 0054-2018 Basic Requirements for Password Application in Information SystemsIt has made detailed provisions for the security assessment of the application of passwords in the planning, construction, and operation stages of the information system:
- In terms of password algorithms, the password algorithms used in the information system should comply with the provisions of laws and regulations and the relevant requirements of national, industry and professional standards related to passwords. For example, using the commercially approved password algorithms SM2, SM3, SM4, etc.
- In terms of password technology, the standard password protocols involved in the password technology should comply with domestic relevant password standards. If it is a customized password protocol, the design should be secure and reasonable, and also follow relevant password standards. For example, for SSL-related applications, the design standards should follow the 'GM/T 0024-2014 SSL VPN Technology Specification'.
- In terms of password products, the password products and modules used in the information system should be approved by the national password management department. For example, if the password module used in the information system should have a commercial secret model certificate.
- In terms of password services, the password services used in the information system should be licensed by the national password management department.
4. Other Alternative Solutions
- Tokenization: Replaces sensitive data with random segments of data. The actual sensitive data and token mapping exist in another strictly controlled database, and non-sensitive tokens can be circulated throughout the system.
- Data Masking: Replaces sensitive data with random data. Unlike Tokenization, these two data do not store a correspondence. Masking can be one-way, used in test environments, and also used in dynamic Masking, based on specific fields with access rights.
- FPE: Format Preserving Encryption, obfuscates sensitive information, data is unreadable.
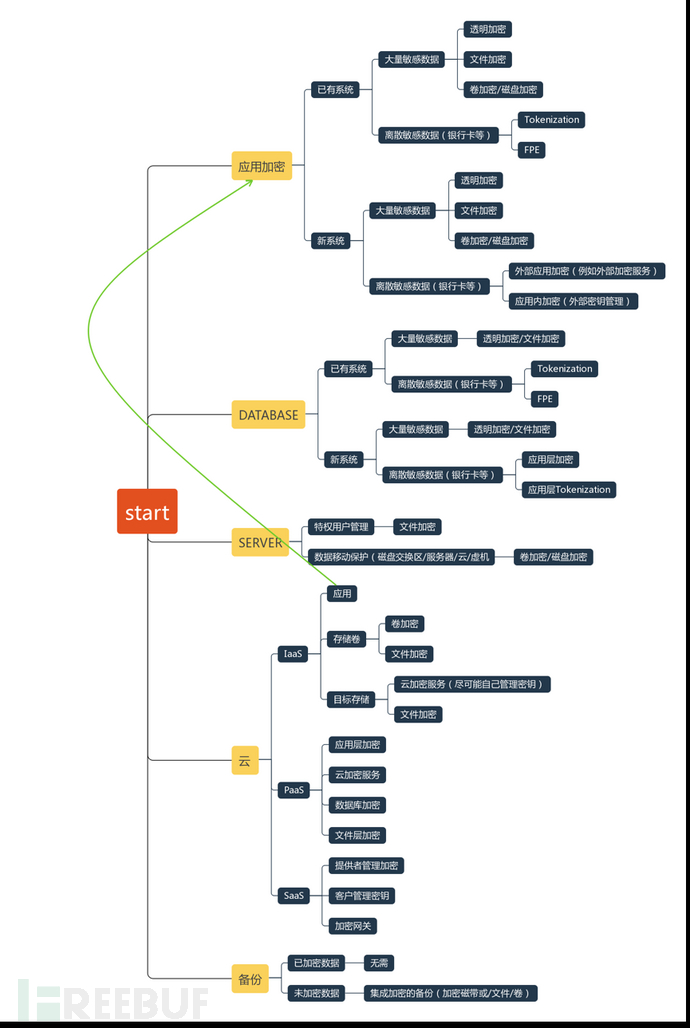
5. Decision Tree
评论已关闭