There is a significant gap in cloud adoption rate (85% vs. 43%) and willingness to migrate to the cloud between users in the United States and China. For most people, the cloud is still a foreign concept. Everything is stable now, so why leave this comfort zone to try something unknown? This is the mindset of most enterprises today.
Figure 1: Cloud Platform Usage by Enterprises across China in 2018
(Source: 'China Enterprise Cloud Index (2018)')
The root cause is mainly that cloud computing suppliers lack or are not sufficiently完善 in terms of user cases for migrating to the cloud and integrating applications, which cannot help enterprises migrate to the cloud quickly and switch seamlessly. This is also a pain point in the global cloud computing market. No matter how beautiful the future of the cloud is described by cloud suppliers, the various problems accompanied by migration are all out of our hands, and this situation is something that most enterprises are unwilling to take the risk of.
However, before migrating to the cloud, enterprises need to make various preparations in advance, the first being whether the migration will affect the normal operation of the business. According to a cloud security survey report by AWS, 85% of traditional solutions cannot be replicated and run normally in the cloud.
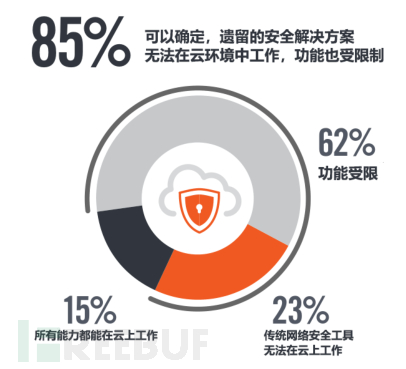
Figure 2: Applicability of traditional methods in the cloud environment
Moreover, there is a compliance requirement; the compliance of enterprises moving to the cloud is a necessity, and this year this necessity also covers the issues of data protection and personal information protection. According to AWS Cloud Security Report, the most concerned focus of cloud security isdata leakage preventionanddata privacyandviolation of confidentialityDue to the successive introduction of the 'Data Security Law (Draft)' and the 'Personal Information Protection Law (Draft)', they will soon be officially promulgated, and enterprises should lay out relevant security strategy deployment in advance.
The starting point of this article is the following questions:
Why are domestic users reluctant to move to the cloud? What are the concerns?
Why can AWS occupy the first cloud market share in the world? What is its excellence?
Why do users believe in AWS and are willing to migrate to AWS? What are its advantages?
Based on the above issues, I will start to introduce the successful experience and methods of AWS in encouraging users to move to the cloud one by one. We can learn and draw on the practices and thinking of this 'big brother' in the cloud computing market.
Before we start, let's go over a few things again. It's also about the three questions mentioned above. From my research on the cloud market, domestic users are reluctant to move to the cloud mainly because we may not have done enough (including AWS also believes that there are still many things that need to be improved), and cannot guarantee the compatibility and stability of users' systems when moving to the cloud, as well as the cloud-native ecosystem of functions, tools, and skills. Moreover, from the comments of netizens, it takes a month to submit a work order after a problem occurs, and this is just a routine fault issue; if it is a functional requirement, it may take even longer or be uncertain. In this regard, AWS is different; they not only have powerful and comprehensive products but also a complete cloud ecosystem and services, and AWS is genuinely customer-oriented, seriously solving customer problems while improving its products and services (this is why AWS has such rich and complete product functions today). Here is a quote from AWS CEO Andy Jassy:
“Some companies like to do some cool things and want others to think they are cool. But we AWS are not progressing actively to pursue coolness; everything we do and think is just to help our customers.”
AWSof the 6R migration strategyWhat is
The Rehost method has the highest customer acceptance, the Repurchase method is the cheapest and fastest, the Replatform method has moderate workload and difficulty, while Refactor/Re-architect is the most expensive and the most difficult, but it provides the advantages of optimizing applications and utilizing cloud-native features. The following figure is a two-dimensional plane graph showing the cost, difficulty, and integration time required for the 6R migration strategy. Gartner had already launched the 5R migration model in 2011 (reference: 'Gartner's 5R Security Migration Model'), and AWS has evolved its own 6R migration strategy based on this model.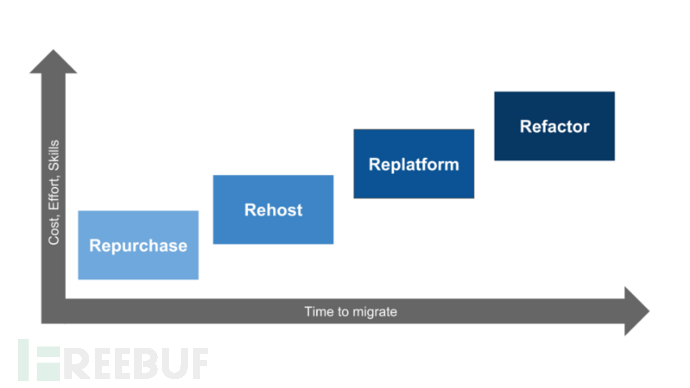
Figure 3 Cost of AWS 6Rs migration strategy (source: CloudSoft)
Let's take moving as an example to illustrate several patterns simply for easy understanding.

Rehost——Hualala moving。Take the existing household and items to the new house by car and place them in the original position, it is still a familiar environment, familiar household, and familiar items, but the house has changed.

Repurchase——buy what is missing。It may be that after moving in, some furniture and items are purchased according to needs. It may also be that there is no need to move, but I will purchase some domestic services to help do some household chores at home.
Replatform——remodeling and placement。After moving in, the layout and配套设施(electricity, water pipes, etc.)of the new house are different from the previous house, and the furniture and items need to be redesigned and placed according to the room structure, which will have some differences from the old house.

Refactor——raw house。The new house is a raw house, everything needs to be remodeled and wired, and all furniture and items need to be repurchased. After moving in, it is a completely new environment.

Retire——useless household and items。Some items that are not used or outdated can be directly thrown away without occupying space in the new house.
Retain——do not move。Moving costs are too high, and the new experience may not be as good as the current community, so you can choose not to move.
Enterprises usually consider how to plan in the 'migration process' (portfolio discovery and planning).Determine what is in the environment, what the dependencies are, which parts of the migration are relatively easy, which parts are relatively difficult, and when to migrate which application。By using AWS's 6R strategy, enterprises can plan how to migrate applications and the order of migration.
AWS recommends starting with lower difficulty applications because migration is relatively easy——this will help the enterprise build some confidence, or use it as a successful case of 'quick migration' during the learning process. Before migration, several issues should be clarified:
Does it have an emergency event or corporate pain point——Rehost
评论已关闭