Introduction:
Automation has appeared in various forms for decades, and it is only now that we are beginning to see its full potential.
Automating the Software Development Life Cycle (SDLC) can significantly improve quality assurance, developers' productivity, and reduce the time spent on specific tasks. Companies have begun to invest more in their security practices throughout the entire SDLC to protect their data and prevent malicious software attacks.

With the changes in the industry, security practices are also evolving. They have moved from traditional security practices (where security was considered to be out of the scope of the development team) to treating security as a priority in the SDLC. The trend of adopting a shift-left mindset is on the rise, which means starting from security before the development stage of the SDLC. This helps companies adopt a more flexible approach to handling network security.
What is Zero Trust security?
Zero Trust security is an IT security framework that treats everyone and everything as adversaries (in a good way!). Therefore, the Zero Trust security model grants the lowest privilege access to all IT resources, which means that no one should be trusted except those who are explicitly granted access. Instead, only authenticated and authorized networks, applications, users, IP addresses, and devices can enter the network according to strict protocols.
The implementation of this zero trust framework involves advanced and secure technologies to verify user identity and achieve system security. Some of the well-known technologies used for this purpose are Role-Based Access Control (RBAC), Multi-Factor Authentication (MFA), Identity and Access Management (IAM), identity protection, and endpoint security technologies. In addition, strict and dynamic user authentication methods are enforced before granting any access.
In addition, continuous potential threat scanning and detection will be conducted.
Why is it necessary to ensure security in the SDLC?
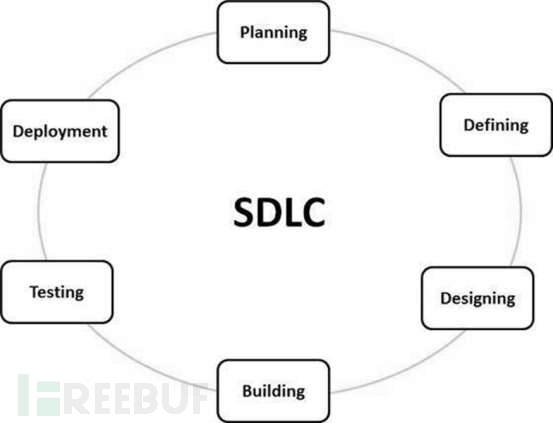
The Software Development Life Cycle (SDLC) is the process of designing, developing, and testing high-quality software in the software industry. The SDLC aims to produce high-quality software that meets or exceeds customer expectations, completed on time and within cost estimates.
Every company wants to release new features to customers faster, and security needs to keep pace with the pace of innovation. In addition, organizations are transferring their workloads to the cloud, utilizing cloud computing services, and the cloud provides dynamic scaling. Security must be expanded to match the scale of the cloud. Today's companies cannot afford to have service interruptions for a second, so security becomes crucial in automated event response recovery.
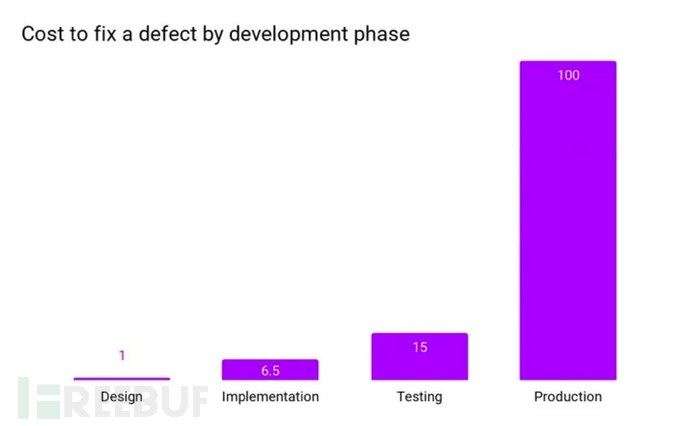
The cost of fixing errors in production can make your customers uncomfortable and bring a lot of overhead to the development team, so security experts strongly urge the establishment of security checkpoints at every stage of the SDLC.
To successfully and securely leverage automation, it is necessary to emphasize security more throughout the entire SDLC. This is whatDevSecOpsAs an integrated way of thinking in cloud-native technology, it unifies development, operations, and security into a process within the SDLC. It advocates for the adoption of a shift-left approach in the early stages of the SDLC to promote security (shift-left security).
The Challenges of Implementing DevSecOps
Implementing security in the DevOps workflow presents many challenges. Here are some of the main ones:
- DevOps is a fast-paced game: As DevOps primarily focuses on rapid development, deployment, and release, keeping up with the pace of this fast-paced competition becomes challenging.
- Isolated team approach: The security team usually uses different tool sets and processes, and they often lack complete SDLC visibility. This consideration of viewing dev and sec as two independent teams becomes challenging.
- Scalability and integration: With the invention of containerization and the creation of virtual VMs, DevOps has provided many new attack surfaces for attackers. Various tools and technologies such as Jenkins, Docker, etc., add different security challenges when expanding and can create complex layers (literally).
- Skill set: The DevOps field lacks security principles, proof of concepts, and skill sets, making it challenging to recruit real security professionals. Moreover, businesses often ignore the security team, not allowing them to participate in major decisions, whether it is choosing a new platform or tool, updating policies, etc., so the overall vision of placing security first is easily blurred.
- Incorrect tool selection: Choosing inappropriate tools and making poor decisions ultimately become liabilities. This can be achieved by involving the security team in design considerations, tool selection, policy making, compliance, governance, and so on.
Security best practices in the SDLC
Here are some tips for implementing zero-trust security in the DevOps pipeline:
- Implement DevSecOps as the foundation of the SDLC and make the shift-left approach mandatory.
- It is mandatory to generate a Software Bill of Materials (SBOM) every time you collaborate with third-party tools and suppliers.
- Conduct regular security training to instill security awareness and ownership in your development and operations teams.
- Have security checkpoints at every stage of the SDLC and verify that only good code, not confidential data or secrets, is exposed to the outside world.
- Integrate static code analysis into the build process.
- Develop threat modeling plans to identify and mitigate potential security risks involved in the development process.
- Consider continuous security as a foresight. Utilize best practices in security and compliance and adopt a continuous improvement strategy.
- Use security tools that integrate well with your SDLC and easily achieve security and governance automation with little or no manual intervention.
- Ensure that your toolkit includes powerful security vulnerability detectors and comprehensive software composition analysis solutions.
- Establish strong security threat response management strategies to deal with any security threats that may occur.
- with access control strategies that have clear boundaries for access rights, roles, and responsibilities to eliminate conflicts between teams.
a renowned security tool
- JFrog Xray:JFrogXray is a knownSecurity Vulnerability Toolscan scan all your open-source software artifacts and their dependencies to find vulnerabilities and license compliance issues. It scans repositories, build packages, and container images. It can detect any violations in damaged licenses and software components, ensuring that your end-to-end software lifecycle runs as smoothly as possible.
- SonarQube:SonarQubeis an open-source tool for continuous code inspection. It collects and analyzes source code and provides reports on the quality of the project code. By using it frequently, SonarQube can ensure common coding standards within your organization while ensuring the sustainability of applications.
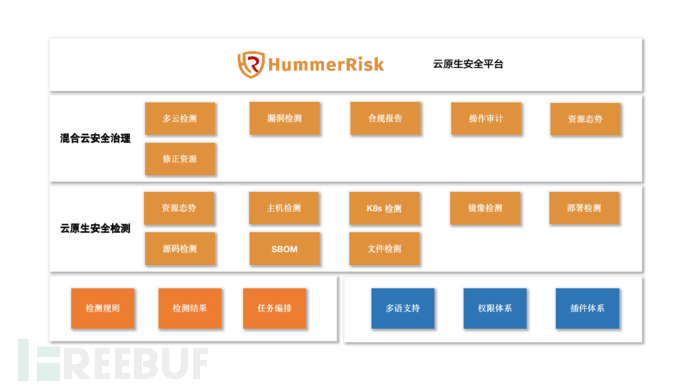
- HummerRisk:HummerRiskis a cloud-native security platform that includes hybrid cloud security governance and container cloud security detection, providing one-stop security detection features to help you quickly identify security vulnerabilities.
- Vdoo: Vdoo is a highly recommended security tool that enables security teams to reveal and reduce software risks involved in applications, containers, embedded, IoT, and edge devices. With Vdoo, security teams can automate and configure security audits in minutes. Note:JFrog recently acquired Vdooto enhance its security game in the cloud-native field.
- Aqua Security: AquaSecurityThe platform implements security automation throughout the application lifecycle to protect builds, cloud infrastructure, and workloads, regardless of where they are deployed.
- WhiteSource:WhiteSourceis a license compliance management platform that ensures teams can effectively manage and trust their open-source assets. It detects and resolves security and compliance issues throughout the entire SDLC. It alerts and helps developers find and fix issues when problems occur.
- Logz.io: Logz.ioThis is designed to provide more reliable observability for systems through log management and log analysis services. The tool offers a centralized platform for security and operations teams, specifically for cloud-native environments.
Protect your
Security becomes crucial at every point in the SDLC to reduce the risk of human error. Most companies believe that,Left shiftMake security everyone's job, and it will enhance the security aspect of the entire SDLC. But is that all? Protecting the SDLC is not just about making security everyone's job.
Here are some key points on how to start protecting your SDLC:
- Create reliable security coding best practices, guidelines, and frameworks for developers to integrate into the SDLC.
- Ensure that every developer joining your company receives security training.
- Utilize the best-in-class tools for security vulnerabilities, static code analysis, and end-to-end supply chain protection.
- Make code review, scanning, penetration testing, and architecture analysis an integral part of the development work.
- Integrate security into your CI/CD pipeline using tools such as JFrog Xray, Vdoo, SonarQube, etc.
- Ensure that each tool included in your SDLC has a security checklist. For example, if you use platforms such as Docker and Kubernetes, make sure to use only official Docker images and provide advanced cluster security for your workloads on Kubernetes.
- If you use open-source tools in the SDLC, make sure to use software composition analysis (SCA) tools to analyze open-source code, libraries, and dependencies, etc.
- Having a custom dashboard or tool that helps you view what is happening in the SDLC in a single pane. Perhaps, combined withDynatrace
- It is recommended to use a tool with an overall security approach in a single window - an end-to-end platform that connects all points and builds a zero-trust security system, making it difficult for attackers to penetrate and gain access. For SDLC, your binaries and all dependencies are important input data for further steps.
- Firstly, you need a process and a set of tools to protect the security of binary files to the edge, integrate security data for effective decision-making, and an end-to-end delivery system with the highest integrity.
Conclusion
Regardless of which industry and stage you are in your cloud-native journey, the zero-trust principle has become a necessity and is adopted by small and medium-sized enterprises to ensure that their systems are always highly secure and available. By embedding security principles, best practices, and tools to ensure a solid security foundation, security threats can be mitigated.
About HummerRisk
HummerRisk is an open-source cloud-native security platform that solves cloud-native security and governance issues in a non-intrusive way. Core capabilities include hybrid cloud security governance and K8S container cloud security detection.
HummerRisk covers both parts of CSPM and CNAPP defined by Gartner, which can well meet the security needs in cloud-native environments.
Github Address:
https://github.com/HummerRisk/HummerRisk
Gitee Address:
https://gitee.com/hummercloud/HummerRisk
评论已关闭