First, Introduction to MongoDB
MongoDB is a database based on distributed file storage, written in C++. It aims to provide a scalable and high-performance data storage solution for web applications.
MongoDB is a product between relational databases and non-relational databases, and is the most functional and most similar to relational databases among non-relational databases. It supports very loose data structures, similar to JSON's BSON format, and can therefore store complex data types.

The installation environment of this article is Windows 10 Professional operating system, the database version is 5.0.8, the single-machine deployment process is relatively simple and will not be explained here. This article focuses on the actual operation of MongoDB security assessment, and any inaccuracies are sincerely invited to leave comments for correction, and learn together.
Second, Identity Authentication
a) The login user should be identified and authenticated, with identity identification being unique, and authentication information having complexity requirements and regular changes;
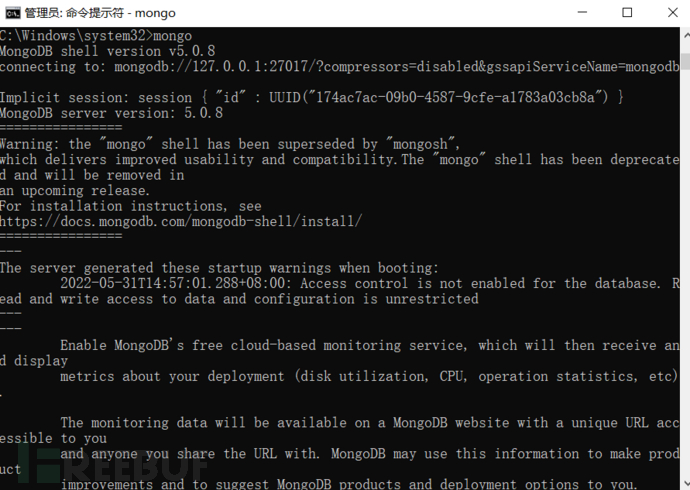
1) MongoDB service is not enabled by default after installation, with a default empty account and password, which leads to anyone being able to log into the data server without account authentication (while the uniqueness of identity identification is not met), execute the command "mongo" immediately to perform any operation on the database without authentication:
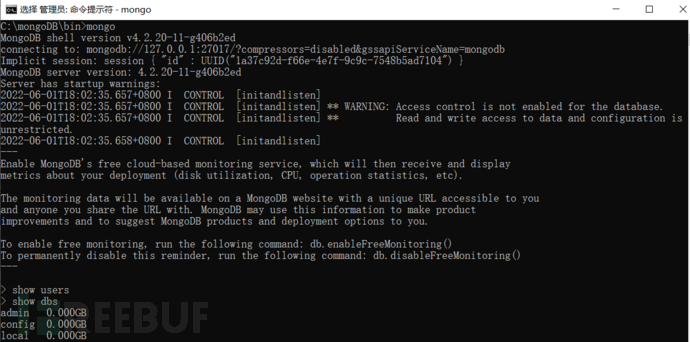
2) Check the mongod.cfg configuration file for the modification auth=true, enable authentication, and execute the command: "mongo" followed by other commands, the result shows insufficient permissions or does not display:
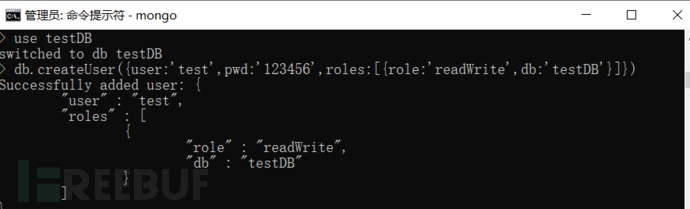
3) MongoDB itself does not have the ability to set the password complexity and regular password change strategy for login accounts, it only allows administrators to set the password complexity by themselves:
b) It should have login failure handling function, configure and enable measures such as ending the session, limiting the number of illegal login attempts, and automatically logging out when the login connection times out;
According to the information, it seems that mongoDB does not have a login failure handling function.
c) Necessary measures should be taken to prevent the interception of authentication information during network transmission when remote management is carried out;
1) Whether remote management is carried out using encrypted or other secure methods, and whether all users are localhost, if all are localhost, it can be judged as local management, which is not applicable.
2) Remote management should be judged according to the actual management situation (such as understanding what measures the database management tool takes to prevent the interception of authentication information during transmission)
d) Identity authentication for users should be carried out using two or more combinations of password technology, password technology, and biometric technology, and at least one of the authentication technologies should be implemented using password technology.
Interview the administrator and verify whether two-factor authentication technology is used, and what the authentication technology is. Implementing two-factor authentication is relatively difficult, and it is generally judged as not in compliance.
Three, Access Control
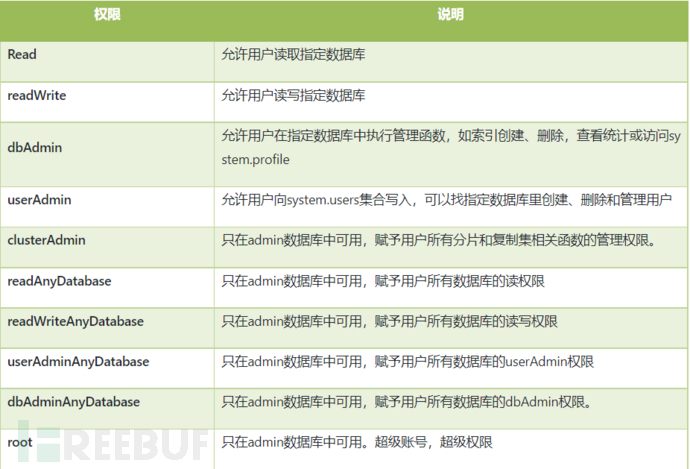
a) Accounts and permissions should be allocated to logged-in users;
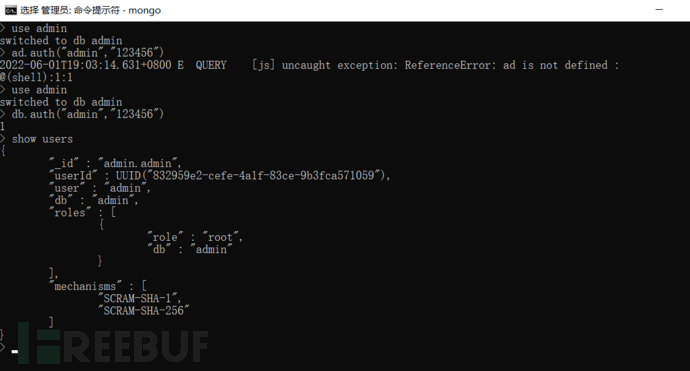
Execute the command 'show users' to view the management permissions of accounts in mongoDB:
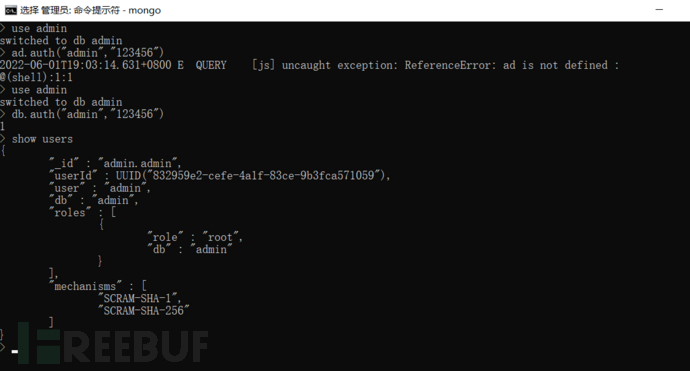
b) The default account should be renamed or deleted, and the default password of the default account should be changed
mongoDB does not have a default account, and different permission accounts can be established according to needs, and all accounts are established by users themselves.
c) Extra and expired accounts should be deleted or disabled in a timely manner to avoid the existence of shared accounts
1) Ask the administrator about the usage of accounts in the database, whether there are any unused accounts, and if so, it is recommended to delete them.
2) Check whether network administrators, security administrators, and system administrators use different accounts to log in to the database.
d) The minimum permissions required for management users should be granted to achieve the separation of management user permissions
Execute the command 'show users' to check whether the management permissions of accounts in mongoDB are different, and whether there are three levels of accounts.
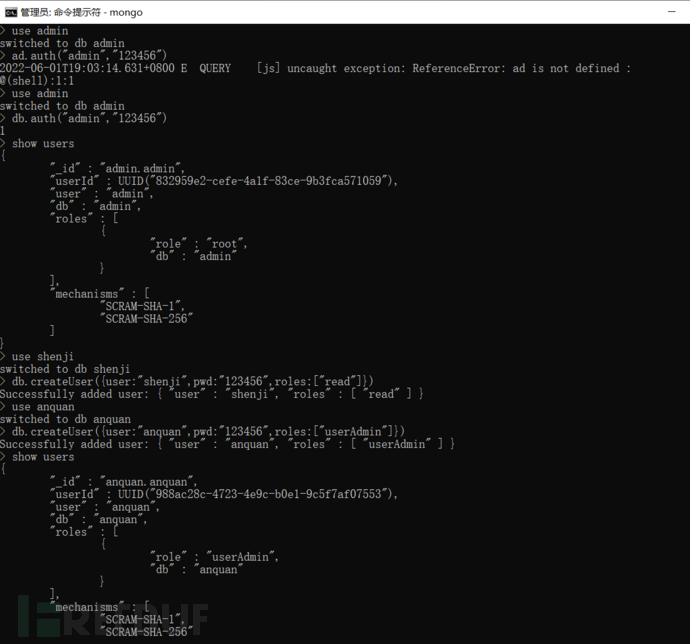
e) The access control strategy should be configured by the authorized subject, and the access control strategy stipulates the access rules of the subject to the object
1) Interview and check whether the administrator has formulated an access control strategy;
2) Check the administrator's permissions; (If mongoDB has enabled authentication and has permission separation, this evaluation point can be judged as in compliance)
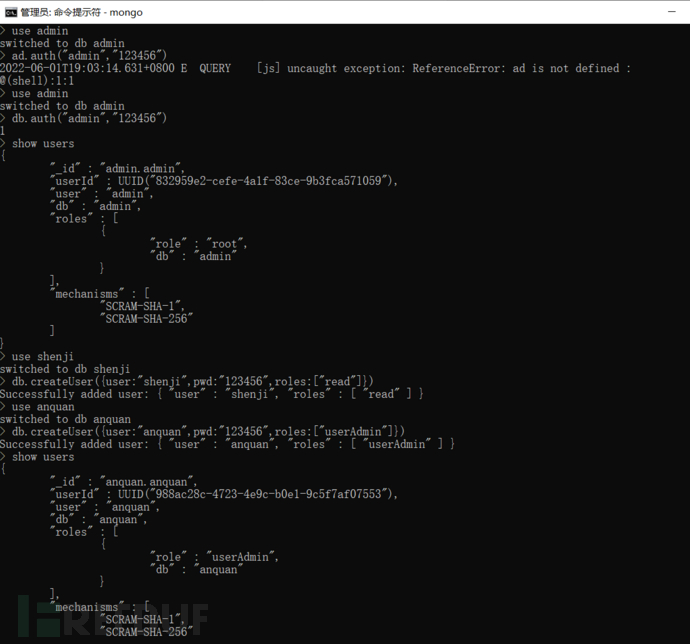
f) The granularity of access control should reach the level of subjects as users or processes, and objects as files or database tables
Combine items a), b), c), d), e), interview the administrator, and check whether the access control granularity subject is at the user level, and the object is at the database table level.
(This evaluation point is mostly judged to be in compliance by most evaluation organizations)
g) Security tags should be set for important subjects and objects, and the access of subjects to information resources with security tags should be controlled
Interview the administrator to see if security tags are set for important subjects and objects. mongoDB itself should not have this feature, which may depend on the operating system or third-party implementation. This item generally does not meet the default requirements.
IV. Security Audit
a) Should enable security audit functions, audit covering each user, auditing important user behavior and important security events
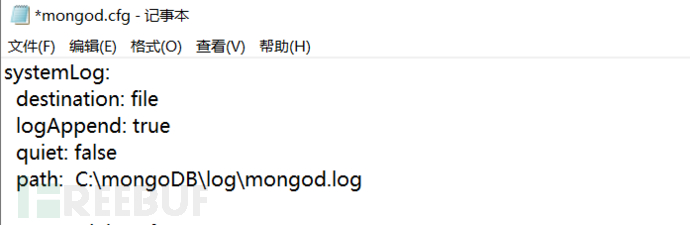
1) Ensure that the log records capture as much information security audit as possible, check whether quiet: false is added to the mongod.cfg configuration file
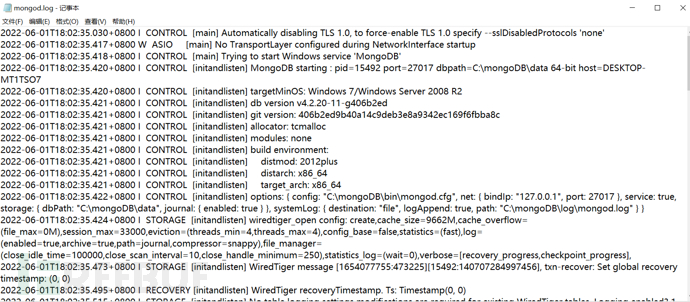
2) Check whether the log file records of mongod.log are normal:
3) Interview the administrator to see if audit data is collected and analyzed using third-party tools (database audit systems).
b) Audit records should include the date and time of the event, user, event type, whether the event was successful, and other information related to audit
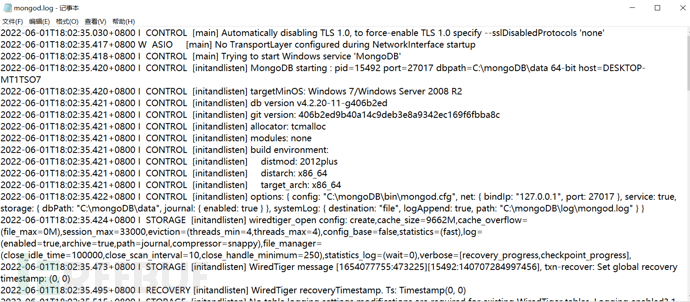
1) Check the mongod.log log file:
2) Check whether third-party tools (database audit systems) have been deployed to enhance the MySQL log function. Record the audit content of third-party audit tools and check whether it includes the date and time of the event, user, event type, whether the event was successful, and other information related to audit.
c) Should protect the audit records, backup regularly, and avoid unexpected deletion, modification, or overwriting
It should ensure that each administrator can access logs related to themselves, such as only allowing privileged accounts to access key logs
1) Interview the administrator about how to protect audit records, whether the audit records are backed up regularly, and the backup strategy.
Whether measures such as backup and archiving have been taken to protect audit records to avoid unexpected deletion, modification, or overwriting, and the local database logs are saved for more than 6 months. Using third-party database audit products, the audit records are saved for more than 6 months.
2) Whether strictly restrict user access to audit records, can be through a normal user login and then whether you can access and modify the log.
d) Should protect the audit process and prevent unauthorized interruption
According to mongoDB, various types of accounts can be established based on permissions to prevent unauthorized terminal audit processes:
V. Intrusion Prevention
a) Should follow the principle of minimal installation, installing only the necessary components and applications
This evaluation item for the database system can be deemed not applicable.
b) Should close unnecessary system services, default shares, and high-risk ports
This evaluation item is not applicable to the database system.
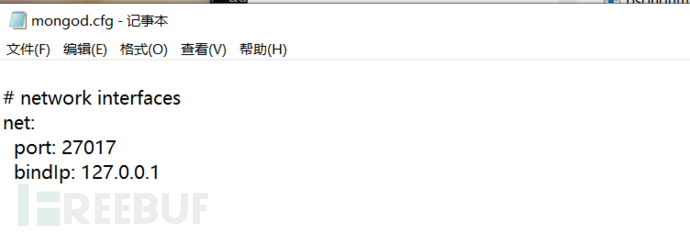
c) Should restrict management terminals that manage the network through setting terminal access methods or network address ranges
Modifying the address of bindIp to 127.0.0.1 indicates local management, if modified to 0.0.0.0, it means any address connection is allowed. Specific IP addresses can be added after 127.0.0.1, separated by commas.
d) Should provide data validity check functions to ensure that the content input through the human-machine interface or through the communication interface meets the system's set requirements
This evaluation item is not applicable to the database system.
e) Should be able to discover existing known vulnerabilities and promptly patch them after sufficient testing and evaluation
1. Whether the administrator regularly or irregularly conducts vulnerability scanning or penetration testing, with cycles in days/months/quarters/half-years/years (it is recommended that the vulnerability scanning cycle be no more than once every half year).
2. Whether high-risk vulnerabilities related to the database have been found through this vulnerability scan, and whether timely vulnerability repair has been carried out if they exist.
f) It should be able to detect intrusion behaviors on important nodes and provide an alarm when a serious intrusion event occurs
This evaluation item is not applicable to the database system.
Six, Malicious Code Prevention
Technological measures that are immune to malicious code attacks or active immune credible verification mechanisms should be adopted to timely identify intrusion and virus behaviors and effectively block them
This evaluation item is not applicable to the database system.
Seven, Credible Verification
It is possible to perform credible verification on the system boot program, system program, important configuration parameters, and application programs of computing devices based on a credible root, and perform dynamic credible verification at the key execution stages of the application, and issue an alarm when its credibility is found to be destroyed, and send the verification results to the security management center as audit records
Through interviews with administrators, whether credible technology has been adopted, credible technology is mainly based on credible chips and credible roots, and the possibility of realizing this technology is not great at present, and it is determined to be non-compliant.
Eight, Data Integrity
a) Password technology should be used to ensure the integrity of important data during transmission, including but not limited to identification data, important business data, important audit data, important configuration data, important video data, and important personal information.
The integrity during transmission is generally realized through communication protocols, common ones including TLS, SSH, etc. For databases, check whether secure protocols have been enabled for data communication, and also ask the administrators to confirm whether there are other measures to ensure the integrity of data transmission.
(Local management is deemed not applicable, remote management is determined according to the actual situation)
b) Password technology should be used to ensure the integrity of important data during storage, including but not limited to identification data, important business data, and important personal information.
To perform an integrity check on the database configuration file, it is necessary to configure the hash value of the initial可信 status of the configuration file, and then generate a hash value based on the current file, compare the consistency before and after, and confirm whether the data has been tampered with. According to understanding, most databases do not have this mechanism themselves, and ask the administrators whether they have used third-party software to perform integrity verification on important database data.
According to some technical personnel on the Internet, summarize a method of data integrity verification (which may not be correct): mongoDB ensures data integrity under unexpected failures through journaling, and MongoEvent is used to verify the data (the specific implementation method is still looking forward to guidance through comments).
In practical operations, it is possible to verify the existence of hash fields in the business data and audit data in the database tables. According to information, data is generally transmitted in front-end through json or xml formats, and the related database table fields have integrity check fields. Currently, it is generally not possible to achieve this, and it is determined to be non-compliant.
Nine, Data Confidentiality
a) It should adopt password technology to ensure the confidentiality of important data during transmission, including but not limited to identification data, important business data, important audit data, important configuration data, important video data, and important personal information, etc.;
Here, the main parameters related to the transmission of identification information (other data such as business data, audit data, and configuration data are generally not encrypted) are roughly as follows:
SCRAM-SHA-256 belongs to the challenge-response architecture, which can prevent password sniffing on untrusted connections and support storing passwords in the form of password hashes on the server, which is considered secure.
MD5 uses a custom security question-response mechanism with low security. It can prevent password sniffing and avoid storing passwords in plain text on the server, but if the attacker manages to steal the password hash from the server, it does not provide protection. (The MD5 hash algorithm is no longer considered a secure algorithm)
If the password is transmitted to the database in plain text, it is recommended not to use it in the production environment. If the database has not enabled SSL, I may capture the data packets during the database authentication process using Wireshare, and may find information about the transmitted password field.
In summary, the most direct way to verify is to capture packets to verify whether important encrypted data (such as identification data, business data that needs to be encrypted, personal information, etc.) is transmitted in plain text.
b) It should adopt password technology to ensure the confidentiality of important data during storage, including but not limited to identification data, important business data, and important personal information, etc.
Check whether the important data in the database tables is stored in plain text, according to experience, in addition to identification data, business data and audit data are actually rarely encrypted, so they generally do not conform to or only partially conform to. If the database encryption function is used, it can meet the requirements. The main types of database encryption are database encryption and external encryption. Database encryption mainly refers to the encryption function called by the database itself, and external encryption mainly refers to the encryption function of third-party vendors' databases.
According to information, MongoDB database itself provides encryption mechanisms, which implement storage encryption in the database kernel. This encryption method can prevent sensitive data leakage caused by disk loss and file copying. However, for attackers who control the database system, it is open and does not have protective capabilities. Moreover, the key management usually does not open to database users, and the security cannot be guaranteed.
Ten, Data Backup and Recovery
a) It should provide local data backup and recovery functions for important data;
1) Access the backup strategies for administrator configuration data, audit data, and business data, check whether the backup status of the strategy is consistent with what the administrator said, and whether there are recovery test records.
(1)MongoDB database backup: mongodump -h dbhost -d dbname -o dbdirectory
Parameter description:
-h: The address of the MongDB server, for example: 127.0.0.1, of course, the port number can also be specified: 127.0.0.1:27017
-d: The database instance to be backed up, for example: test
-o: The location of the backup data, of course, this directory needs to be established in advance, and this directory stores the backup data of the database instance.
(2) MongoDB database recovery: mongorestore -h dbhost -d dbname --dir dbdirectory
Parameter or name:
-h: The address of the MongoDB server
-d: The database instance to be restored, for example: test, of course, the name can also be different from the backup time, such as test2
--dir: The location of the backup data, for example: /home/mongodump/itcast/
--drop: When restoring, delete the current data first, and then restore the backup data.
2) Backups can be performed through database management tools such as navicat, which have mongoDB's built-in logical backup. The backup principle is to connect to the mongoDB database through the protocol, and query out the data that needs to be backed up.
b) It should provide real-time off-site backup functions, using communication networks to back up important data in real time to the backup site;
Deploy a backup data center in a different location and regularly perform off-site backup through the backup strategy and network.
c) Hot redundancy for important data processing systems should be provided to ensure the high availability of the system;
Cluster deployment and dual-machine hot backup can both be judged as in line with the requirements.
Eleven, Remaining Information Protection
a) It should be ensured that the storage space where the identification information is located is completely cleared before it is released or reallocated;
Generally, the kernel layer of the database system cannot realize the remaining information protection function by default, which requires third-party tools to achieve.
b) It should be ensured that the storage space containing sensitive data is completely cleared before it is released or reallocated.
Generally, the kernel layer of the database system cannot realize the remaining information protection function by default, which requires third-party tools to achieve.
Twelve, Personal Information Protection
a) Only the necessary user personal information for business should be collected and saved;
Check whether personal information is stored in the database, if so, check the personal information protection mechanism and the personal information protection management system
b) Unauthorized access and illegal use of users' personal information should be prohibited.
Check the personal information protection mechanism and the personal information protection management system, and verify whether unauthorized personnel can access the relevant components of the personal information storage.
Thirteen, Summary
During the equal protection assessment inspection, it will be found that many mongoDBs do not meet the requirements of some control points of equal protection. Its functions are not much more than MySQL and Oracle. After the equal protection assessment organization proposes rectification issues, it is also a relatively difficult task for the database using unit to strengthen, which may require the assistance of third-party tools to complete the rectification and reinforcement work, which is still a麻烦 matter.
评论已关闭