Article background
These days, just finished a project, felt inspired, wrote this test guide by hand, which includes some testing methods of online banking machines, convenient for everyone to learn from and for customers to learn testing independently.
What? You don't know what an online banking experience machine is! It's this device (including both touch screen and built-in keyboard versions):

Fake hackers, who would a serious person wear a mask?
Real hackers, directly physical black into
The humble security and service test keeps photos

Test guidelines
Test ideas
To get back to the point, the so-called online banking experience machine testing is mainly to find the defects in the sandbox design, escape the sandbox, obtain the execution command permission of cmd, and thus obtain the management permission of this device.
The design principle of the online banking experience machine can be shown as follows:
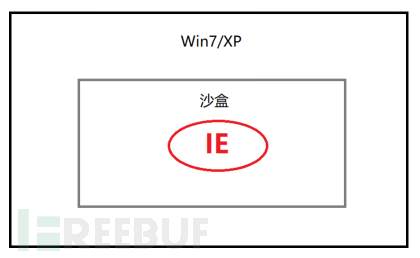
Most online banking experience machines are integrated with WIN7/XP systems, and then use the sandbox to encapsulate IE completely inside, so that it runs completely in this seamless (full-screen mode) framework, avoiding direct attacks.
Test process
The following pictures, in order to avoid information leakage, can only be marked thickly
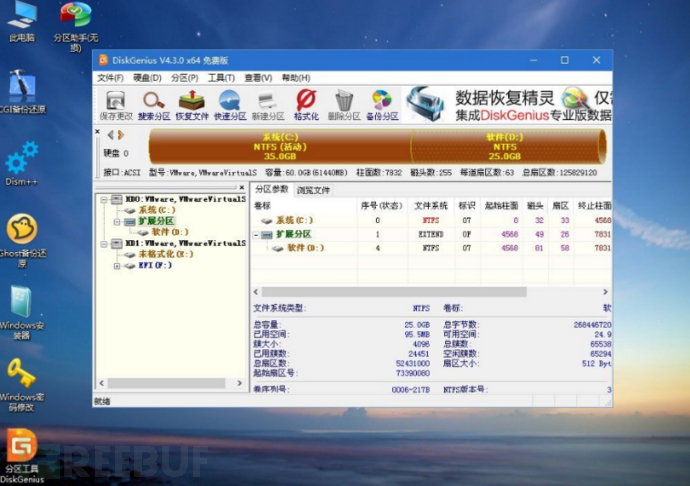
System level
In our daily tests, we mainly focus on this aspect for testing. The following provide some bypass ideas:
Escape interface
It can be roughly understood as clicking the screen, keyboard, and other ways to jump out of the sandbox to perform background operating system operations
1. Use the right mouse button, when the prompt information appears, if the right-click menu is not well shielded, it can be used directly.
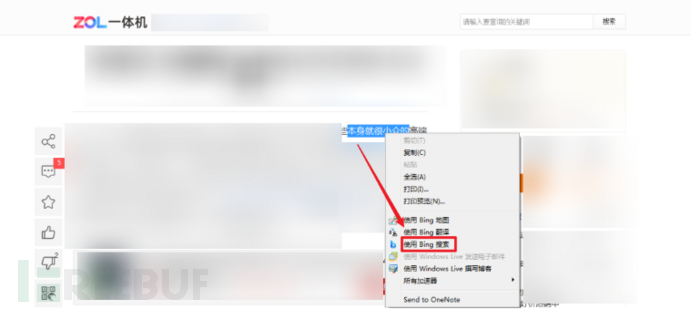
It is not necessary to be limited to the right-click menu of the desktop components and the sandbox internal, third-party components may also have escape situations. For example, the escape situation caused by the input method in the figure below:
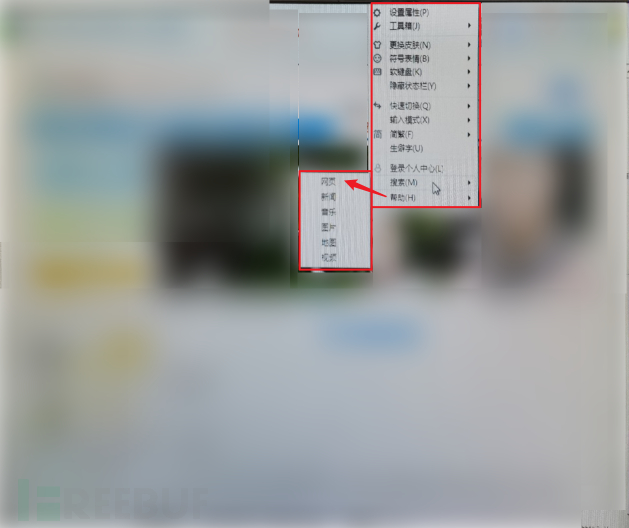
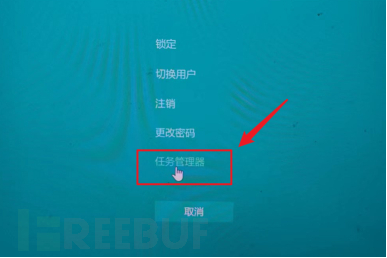
2. Use the CTRL+ALT+DELETE combination key to open the security window, and then select to open Task Manager to open the command line. Currently, this kind of relatively basic vulnerability rarely appears, and if this problem exists, it is basically unnecessary to look at the remaining problems.
Specifically click: File - Run New Task
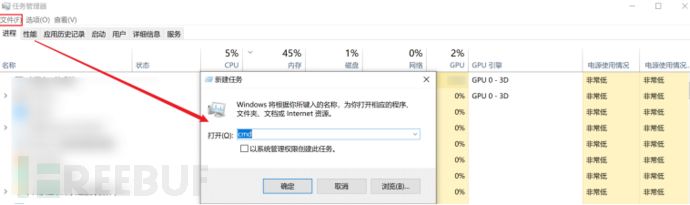
Here you can also directly useWIN+RKey, open the Run dialog box
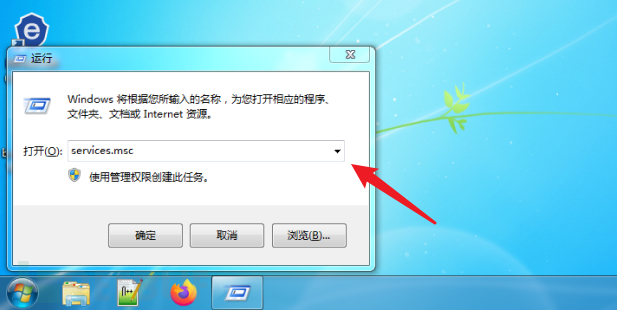
Common commands:
Open the root directory: C:\
Open the current user folder: C:UsersUserName
Open the cmd Command Prompt: cmd
Open the File Explorer: explorer
Open the Registry Editor: regedit
Local Service Settings: services.msc
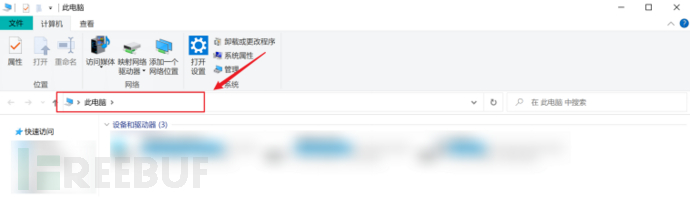
3. Open the File Explorer. Some online banking experience machines have an exit function, but after exiting, they will still be forced back to the page. Therefore, there is a time difference in returning when exiting. By quickly clicking to enter the File Explorer (My Computer), as shown in the figure below, you can enter cmd or the path of cmd, that is, C:windowsSystem32cmd.exe
You can also directly use the shortcut key Win+E to perform the test
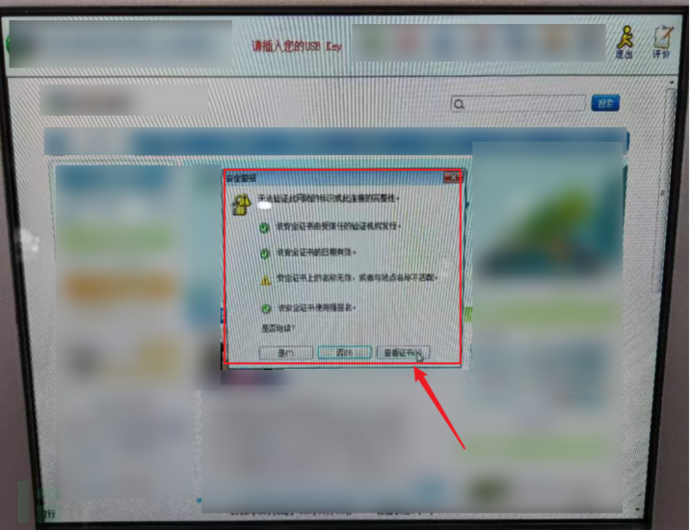
4.Certificate Defect.Taking advantage of the design flaw of online banking during the HTTPS communication process, many online banking services are considered to have problems with the server certificate by the browser, resulting in a pop-up warning message. This is very frequent and can easily cause problems, so it needs to be paid attention to.
By using the Internet Options, you can access the Control Panel at the highest level
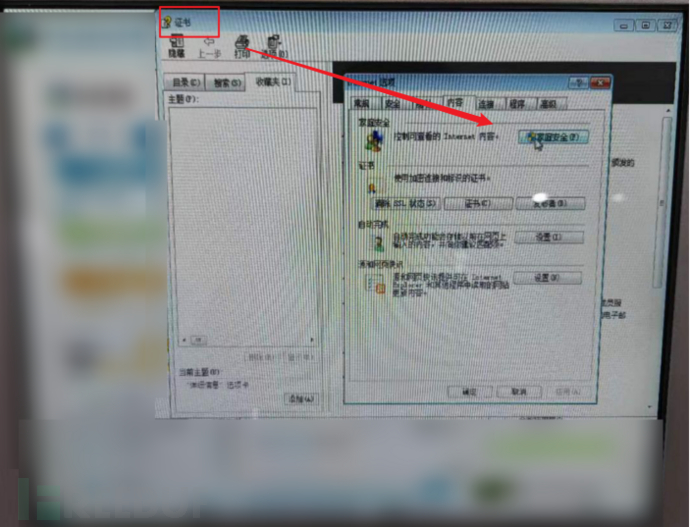
There is also the following situation:
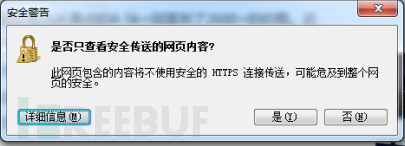
By entering Windows Help and Support through detailed information, you can then re-enter the browser to check whether the newly popped-up traffic analyzer can stabilize the bypass of the sandbox.
In addition, there are many pop-ups similar to certificates, which will not be demonstrated one by one, but you can try each option if they appear.
5.Download InterfaceBy selecting the save location, you can choose the path yourself and enter the resource manager, then enter the path of cmd and execute the cmd command to enter the DOS interface.
You need to carefully search for each download interface in the device, as each may constitute a leak.
For example, the most common ones are:
①Download the drivers for the USB KEY provided
②Online Banking Machine Client Download
The following figure shows a demonstration of exploiting after downloading the file:
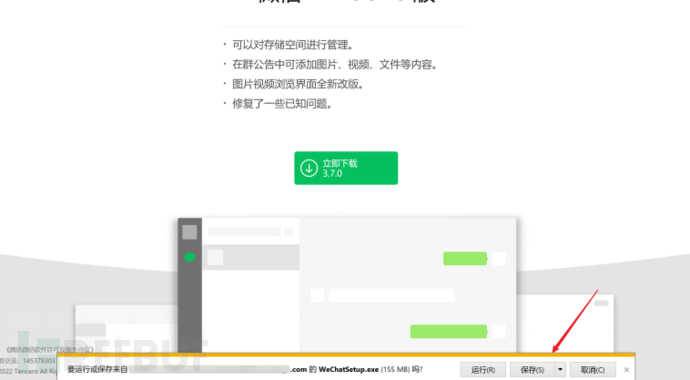
However, some systems limit the user's ability to choose the save location, but you can enter the resource manager by first downloading the file and then checking the actual file address.
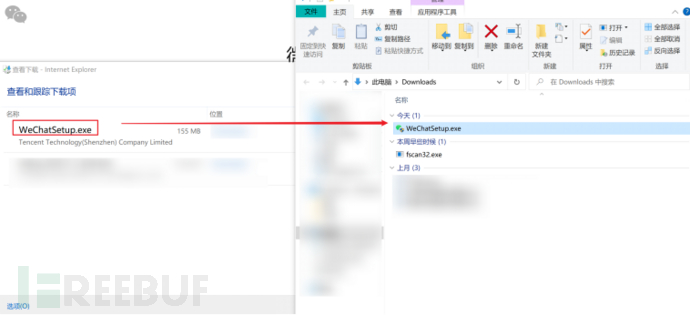
Error Prompt
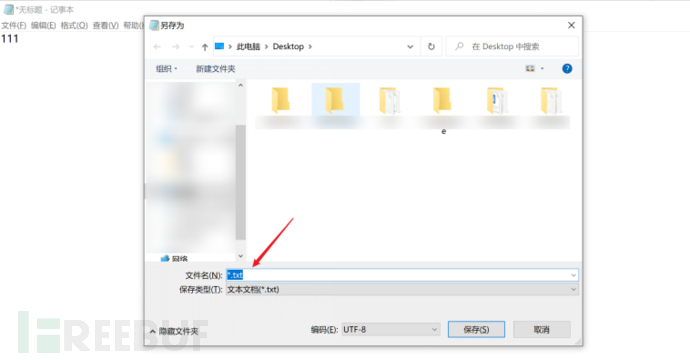
1.When entering error information or other operations, the system pops up an error prompt. By checking the error information, a text file in .txt format will pop up. You can view and write any file in text format with notepad, but you cannot execute files. For example, by writing a script ending with .bat, you can combine it with other vulnerabilities for exploitation.
Example: Save the file test.bat (you can also use cmd directly)
cmd /k
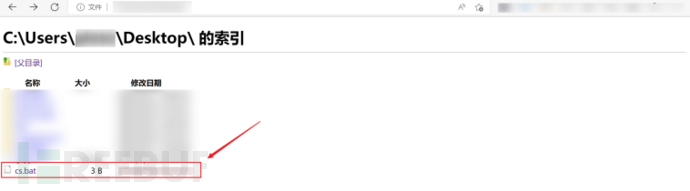
2.By clicking on links contained in error messages, you can access the browser. (Don't limit yourself here, as many browser interfaces are involved in online banking experience machines, but if there are restrictions, the global ones can't be opened), by entering the address 'C:' in the browser, you can enter the file manager and view any files and execute executable files such as '.bat' and '.exe'.

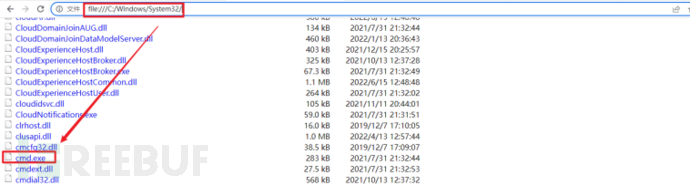
However, more often than not, browsers do not have execution permissions for scripts such as .bat, so you can download cmd.exe from the System32 folder to see if you can download files and pop up a cmd window
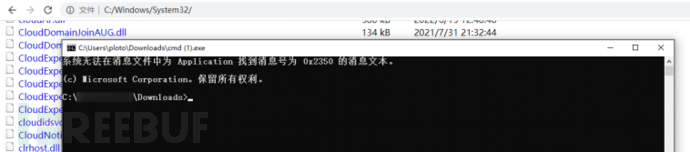
Download files and try to open them directly

Physical Level
1.Interface Leak
Interfaces such as USB, network port, and power port are not visible to ordinary users.
①USB Interface
USB needs to be restricted according to specific circumstances, and some online banking machines require the insertion of a USB key, at which point strict control over USB control permissions is required, allowing only specific devices to connect.

In the design of USB keys, there may sometimes be design flaws, and you can check your certificate information, and at this time, it is likely to have import functions; in addition, when updating certificates, if you use expired certificates to update in the online banking, you can also bypass some sandbox restrictions;
And if the device does not completely restrict the USB interface, you can directly restart and connect to the PE system to forcibly change the password of the online banking experience machine.
The USB interfaces of some devices are sealed, and the cover must be opened to connect USB keyboards and mice and operate the background system. These devices need to be checked to see if they are properly locked. If not locked, you can directly connect keyboards and mice and other control devices, because the USB ports here are basically not restricted.
Tips: When testing, you can try badusb directly to check the control situation. Similar to this, try harmless operations with the Digispark development board.
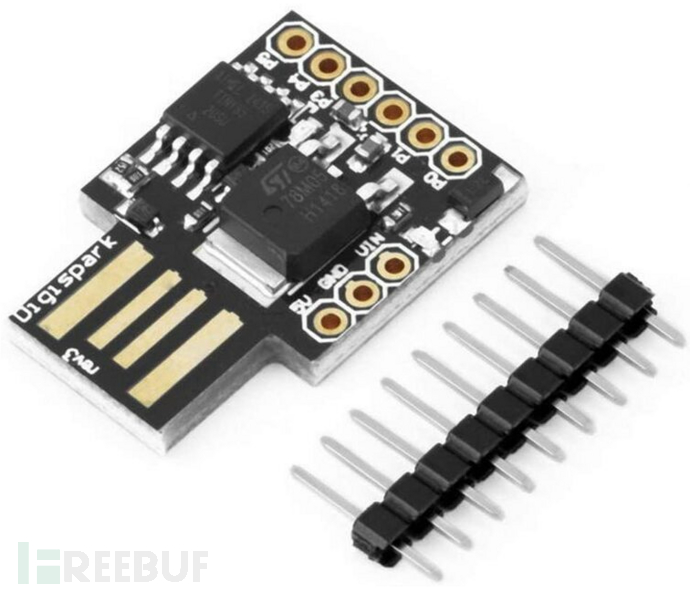
Code section:
# include "DigiKeyboard.h"
# define KEY_ESC 41
# define KEY_BACKSPACE 42
# define KEY_TAB 43
# define KEY_PRT_SCR 70
# define KEY_DELETE 76
void setup() {
DigiKeyboard.delay(500);
//win+r cmd
DigiKeyboard.sendKeyStroke(KEY_R, MOD_GUI_LEFT);
DigiKeyboard.delay(200);
DigiKeyboard.sendKeyStroke(KEY_SPACE, MOD_CONTROL_LEFT);
DigiKeyboard.delay(500);
//DigiKeyboard.println(F("cmd"));
DigiKeyboard.println(F("cmd /q /d /f:off /v:on /k MODE con: cols=15 lines=1"));
DigiKeyboard.delay(1200);
}
void loop() {
}
If you want to learn more about this topic, you can continue to read my other articles.
② Network port
By directly inserting the network port, check if you can connect directly to the online banking machine or connect to the local area network. This part of the interface must be hidden and cannot be leaked.

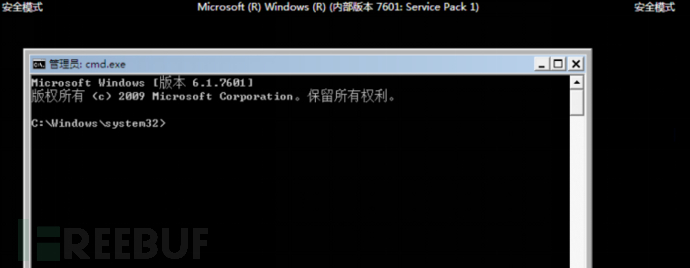
2. Enter safe mode
Press the power button when starting upF8Enter "Secure mode with command prompt"
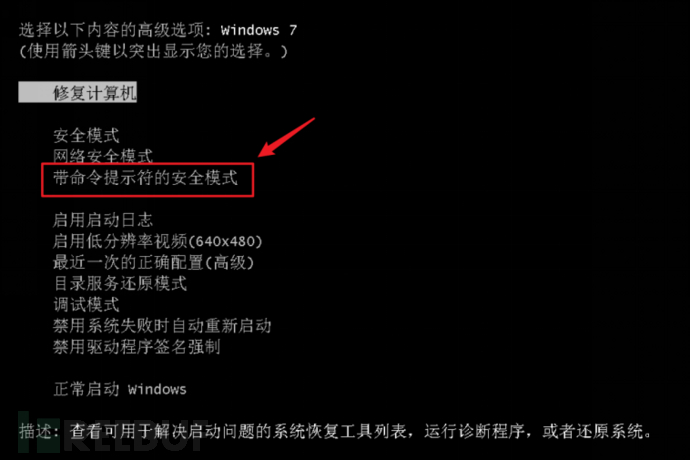
Similarly, you can also press the power button when starting upCTRLEnter this mode
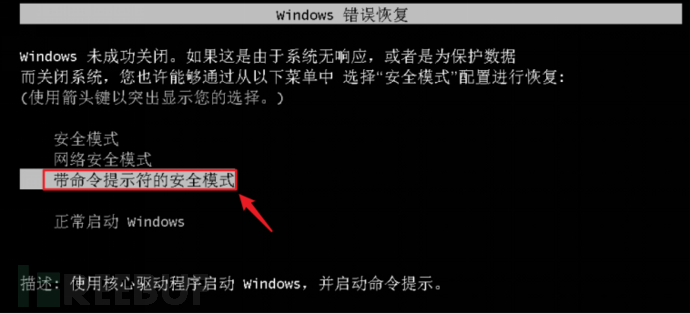
Secure mode with command prompt as shown in the following figure:
3. Start the repair mode
On win7, you can use the sticky key feature to change sethc to cmd, thus bypassing the password restriction
You can check the article I wrote before for the specific operation
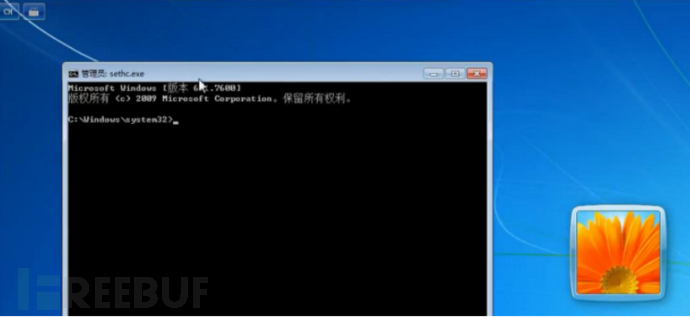
By modifying the sticky key sethc to cmd
The specific operation can be viewed in the article I wrote beforeArticle
Note: The operation may cause disk failure due to forced restart, and should be used with caution.
It should be noted that since this operation involves a forced restart, if the device cannot be shut down directly on the system, it needs to be shut down physically through means such as pulling the power cord, which may affect disk safety and should be used with caution.
Summary
The test of the online banking experience machine ultimately boils down to bypassing sandbox technology, which is as follows: quick key exit, error/download exit, and interface exit. During actual testing, if both conventional shortcuts and operations are prohibited, you can click on any part of the page or press any key on the keyboard at will. No matter if it's a white cat or a black cat, the one that can catch the mouse is a good cat.
评论已关闭