Before watching the article, everyone can pay attention to my public account, search for 'How difficult it is to do information security assessment', find 'Ability Verification Environment' in the lower menu bar, reply to the corresponding keywords to get the 2022 ability verification guidebook and VMware virtual environments for free for Linux (free), Windows, and Mysql systems, which can be used together with the article for better reproduction.
Alright, let's get straight to the point without any further talk.

Before the assessment starts, let's determine the importance of this server and the account passwords
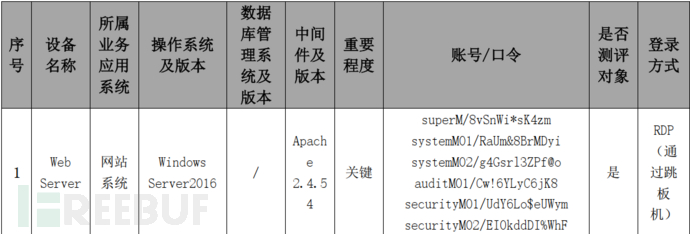
Firstly, Identity authentication
a) The user should be identified and authenticated during login, the identity should be unique, and the authentication information should have complexity requirements and be changed regularly;
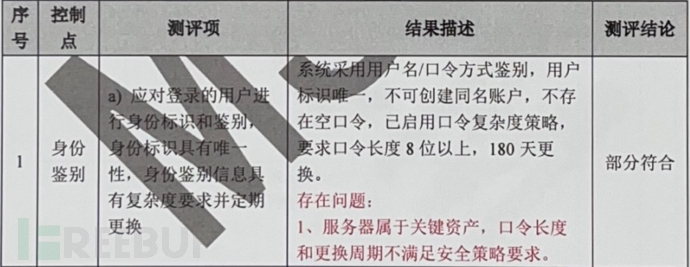
The first clause does not have any obvious pitfalls, we just need to follow the assessment process, view
Control Panel - Management Tools - Local Security Policy - Account Policy - Password Policy

Next, compare the corresponding password security policy of key assets and find thatMinimum password length, maximum password usage periodThese two parameters do not meet the requirements

The first question is relatively simple, without any doubts
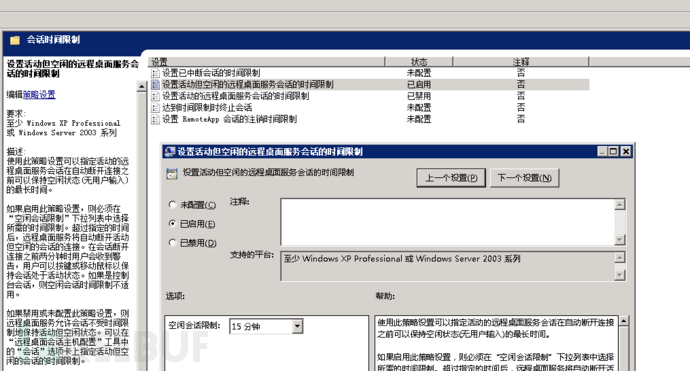
b) It should have a login failure handling function, and should configure and enable measures such as ending the session, limiting the number of illegal login attempts, and automatically logging out when the login connection times out;

Let's first look at the first point, the login failure handling function,Control Panel - Management Tools - Local Security Policy - Account Policy - Account Lockout Policy
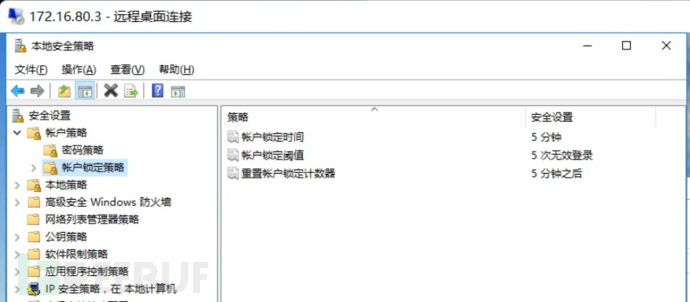
Next, let's compare the content required by the key asset in the security policy and find that it requiresLocking time is 30 minutesTherefore, it violates the requirements of the security policy

Next, let's take a look at the automatic logout function due to operation timeout,Control Panel → All Control Panel Items → Management Tools → Local Security Policy → Local Policy → Security Options → Interactive Logon: Computer Inactivity Limit
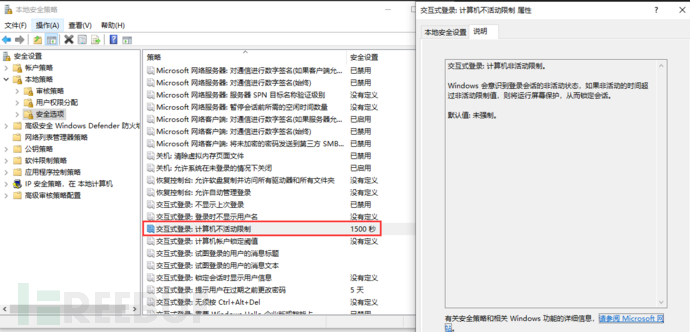
After configuring the corresponding time here, it will be directly reflected on the screen saver, even if the option 'Display login screen when resumed' is not checked, it will also require re-entering the password for identity authentication after the time is up.
At the same time, the security policy requires the configuration of key asset timeout login mechanism to be15 minutesTherefore, violating the security policy

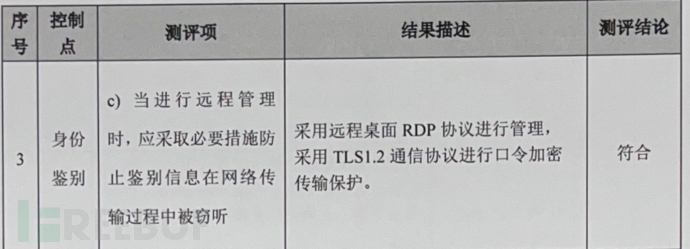
c) When performing remote management, necessary measures should be taken to prevent the interception of authentication information during network transmission;
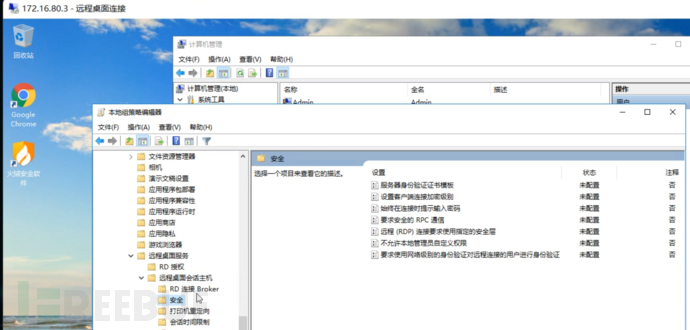
This question is a bit interesting, different from our previous viewing methods, we may have checked here before, runninggpedit.msc→Windows Components→Remote Desktop Services→Remote Desktop Session Host→SecurityA look, none were configured, it may directly draw the conclusion that does not meet the requirements.
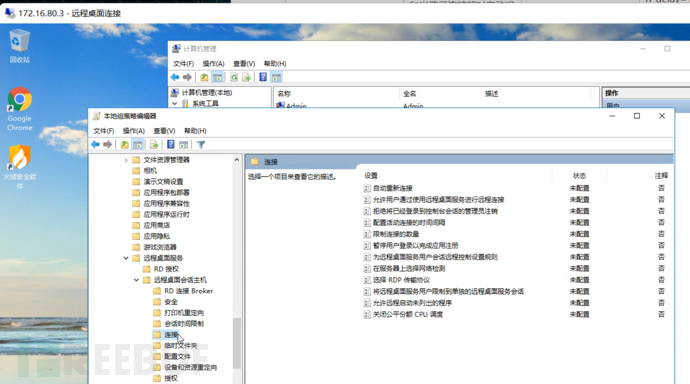
This is also based on the answer provided and the subsequent test to find the clue, we usesslscan Tool to detect the protocol used by the target port 3389, command:sslscan.exe ip:port
It was found that Windows Server 2008 defaults to only support TLS 1.0
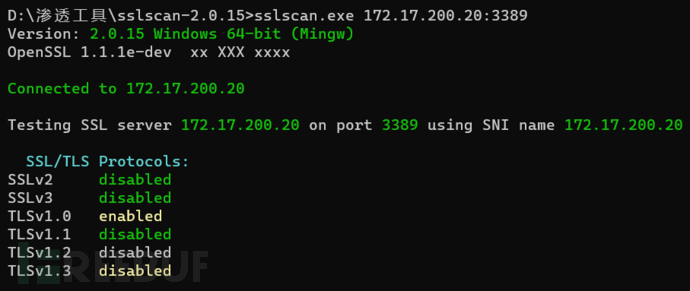
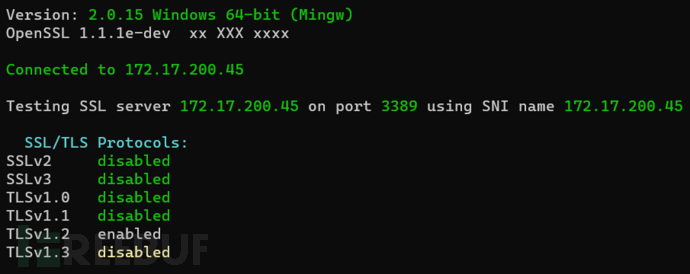
While Windows Server 2016, by default, Windows Server 2016 supports TLS1.0, TLS1.1, and TLS1.2, and needs to modify the registry to force the use of TLS1.2 for communication, we use sslscan.exe 172.17.200.45:3389
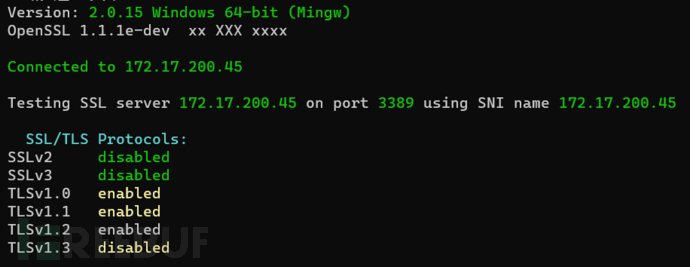
It was found that TLS1.1, 1.2, and 1.3 are all enabled. And the configuration here gpedit.msc→Windows Components→Remote Desktop Services→Remote Desktop Session Host→Security content, the detection results did not change, and alternative solutions need to be sought. Online resources are also quite scattered, and later a configuration in the registry confirmed that the target can be set to force the use of TLS1.2. Disabling TLS 1.0 and TLS 1.1 on Windows Server 2016 can be achieved by modifying the registry. Please follow the following steps to operate:
- Open the "Registry Editor". You can search for "Registry Editor" in the start menu and open it.
- In the registry editor window, expand the following path in sequence:HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols
- Under the "Protocol" folder, find the folders named "TLS 1.0" and "TLS 1.1". If these folders cannot be found, they need to be created manually.
- Under the "TLS 1.0" and "TLS 1.1" folders, create a folder named "Client" and "Serverfolder.
- Under the "Client" and "Server" folders, create a folder named "DisabledByDefaultSet the DWORD value to 1.
- Under the "Client" and "Server" folders, create a folder named "EnabledofDWORDSet the value, and set the numerical data to 0.
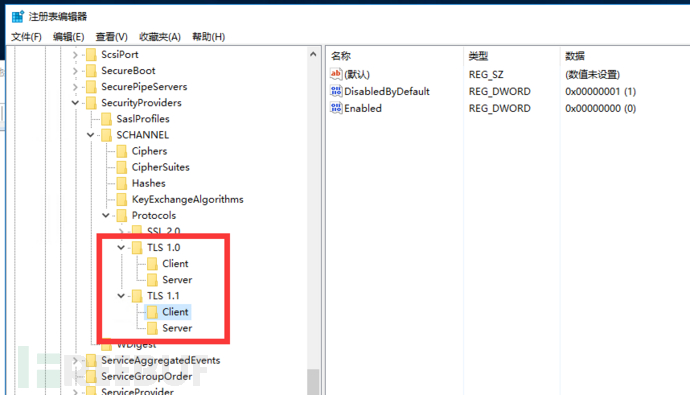
After the configuration is complete, restart and use the SSL tool for detection. It was found that the remote communication is now only allowed to use TLS1.2 protocol.
评论已关闭