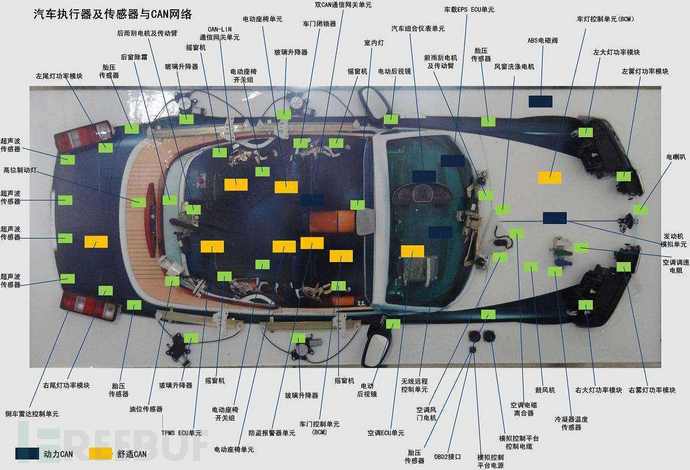
The vehicle bus (Automotive Bus) refers to the system used for communication and data transmission between different electronic control units (ECU) within the vehicle. It acts as a data transmission medium between various electronic modules within the vehicle, enabling different vehicle systems to collaborate and exchange information.

The vehicle bus allows various control units on the vehicle to exchange data and communicate in real-time to achieve various vehicle functions, such as engine control, braking system, seat adjustment, instrument panel display, etc. It provides a standardized interface and communication protocol to ensure interoperability between different control units and reliable transmission of data.
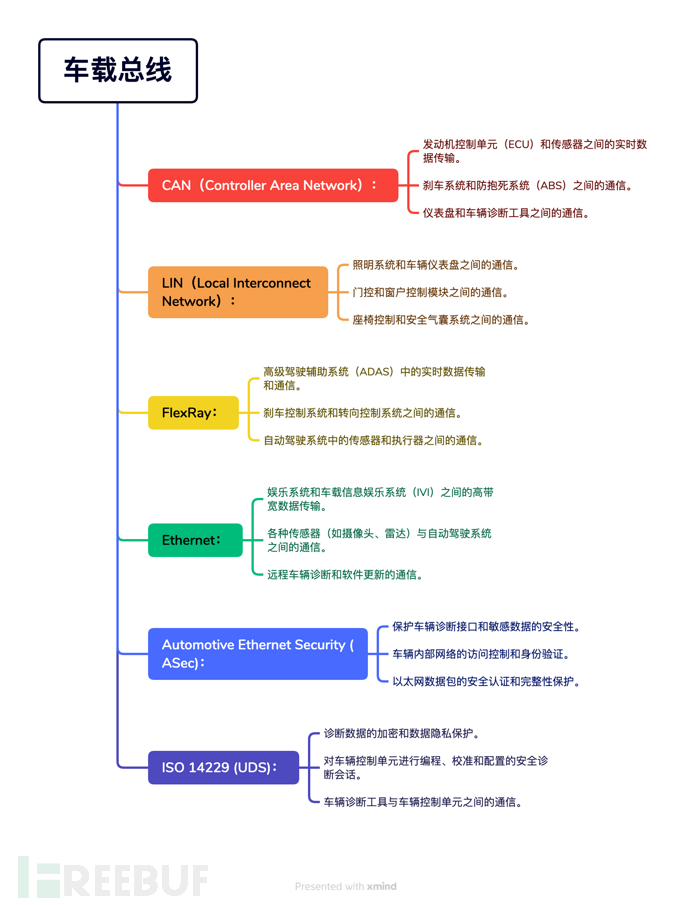
CAN (Controller Area Network):
CAN is one of the most commonly used protocols in vehicle network communication. However, the original CAN protocol does not have built-in security mechanisms, so modern vehicles typically use CAN protocol security extensions, such as CAN-FD (CAN with Flexible Data-Rate) and CAN-XCP (CAN with Extended Calibration Protocol) to enhance security.
The characteristics of the CAN protocol include:
Reliability: CAN uses redundancy mechanisms and error detection and correction techniques to ensure the reliability of communication. It has error detection and error response mechanisms that can detect and handle errors in communication.
Real-time: The CAN protocol is designed for real-time control applications, with efficient message transmission mechanisms and low latency characteristics.
Simplicity: The CAN protocol is relatively simple, easy to implement and deploy. It uses broadcast communication and message filtering mechanisms based on identifiers.
However, the original CAN protocol has some security challenges, such as the lack of authentication and encryption mechanisms, making it vulnerable to deception and man-in-the-middle attacks. To enhance the security of the CAN protocol, modern vehicles typically use CAN security extension protocols, such as CAN-FD (CAN with Flexible Data-Rate) and CAN-XCP (CAN with Extended Calibration Protocol). These extension protocols provide additional security features, such as message authentication, data integrity protection, and encryption.
Security risks:
- CAN bus attack: Hackers may tamper with or forge CAN messages to affect the normal operation of vehicles, such as manipulating the braking system or engine control.
- Data injection: Hackers may inject false CAN messages, causing the vehicle system to make incorrect decisions or operations.
Actual case:
- Jeep vulnerability (2015): Hackers successfully exploited a vulnerability on the CAN bus to remotely control a Jeep vehicle, including functions such as brakes and steering wheel.
- Tesla Model S attack (2016): Hackers invaded a Tesla Model S through the CAN bus, achieving remote control of various vehicle functions.
LIN (Local Interconnect Network):
LIN protocol is used for low-speed data transmission in vehicles, such as door control, lighting, and dashboard, among others. LIN itself does not provide strong security, so it can be combined with other secure communication protocols for applications requiring higher security levels.

The characteristics of LIN protocol include:
Cost-effectiveness: Due to the lower rate and simplicity of the LIN protocol, it is more cost-competitive. It is suitable for simple control and monitoring tasks within vehicles.
Simplicity: The LIN protocol is relatively simple, easy to implement and deploy. It uses a master-slave architecture, where a master node controls multiple slave nodes.
However, compared to CAN, LIN protocol has limited functionality in terms of security. It does not have built-in encryption and authentication mechanisms, so it can be combined with other secure communication protocols, such as CAN-FD and LIN security extensions, for applications requiring higher security levels.
In summary, CAN and LIN are common protocols in vehicle communications. CAN is mainly used for high-speed, real-time control communications, while LIN is mainly used for low-speed, simple control communications. To enhance security, modern vehicles typically adopt security extension protocols for CAN and LIN to add security features and protect communications from attacks.
Security risks:
- Spoofing attack: Hackers may impersonate legitimate LIN devices to communicate with the LIN network within the vehicle and execute malicious operations.
- Eavesdropping attack: Hackers may intercept LIN communications within the vehicle to obtain sensitive information, such as vehicle control commands or sensor data.
Actual case:
- BMW i3 attack (2018): Hackers invaded a BMW i3 electric vehicle through the LIN bus, successfully controlling the vehicle's door locks and windows, among other functions.
- Ford Focus attack (2019): Hackers attacked the window control system of a Ford Focus vehicle through the LIN bus, successfully achieving remote opening and closing of windows.
FlexRay:
FlexRay is a high-speed vehicle network communication protocol used for systems with high bandwidth and real-time requirements, such as braking, steering, and suspension control. FlexRay provides some security mechanisms, such as message authentication and data integrity protection.
The characteristics of FlexRay protocol include:
High bandwidth and flexibility: FlexRay supports communication rates up to 10 Mbps, meeting the needs of vehicle systems for large-scale data transmission. It also provides flexible network configuration options, allowing for various communication topologies.
Real-time: FlexRay uses Time Division Multiple Access (TDMA) technology, by dividing the communication cycle into fixed time slots, to achieve strict real-time communication. This is crucial for vehicle control systems that require high precision and reliability.
Security: FlexRay provides mechanisms for message authentication and data integrity protection to ensure the security of communication data. It uses message authentication codes (MAC) and data signatures and other technologies to verify the authenticity and integrity of messages.
Security risks:
- Message Interference: Hackers may interfere with FlexRay message transmission, causing communication errors or message loss, affecting the real-time and reliability of the vehicle.
- Information Theft: Hackers may steal sensitive information from FlexRay communications, such as instructions for autonomous driving systems or sensor data.
Actual case:
- Ford Escape Vulnerability (2013): Hackers intruded into Ford Escape vehicles via the FlexRay bus, successfully controlling the vehicle's braking and acceleration functions.
- Jaguar Land Rover Vulnerability (2016): Hackers exploited vulnerabilities in the FlexRay bus to intrude into Jaguar Land Rover vehicles, successfully controlling the vehicle's steering and braking functions.
Ethernet:
The application of Ethernet in the vehicle field is becoming more and more widespread, especially for high-bandwidth data transmission and internal communication within the vehicle. To enhance security, the Ethernet used in vehicles usually adopts security extensions such as Ethernet AVB (Audio Video Bridging) and TSN (Time-Sensitive Networking).
Characteristics of Ethernet protocol include:
Ethernet AVB (Audio Video Bridging): Ethernet AVB is a set of standards for audio and video transmission, aimed at providing strict real-time and synchronization capabilities. It has traffic scheduling and clock synchronization mechanisms to ensure high-quality audio and video transmission and provide a better user experience for in-car entertainment and communication systems.
TSN (Time-Sensitive Networking): TSN is a set of extended Ethernet standards designed to meet the needs of applications with high requirements for real-time and reliability. It provides strict time synchronization and traffic scheduling mechanisms, supporting high-real-time communication requirements in vehicles such as autonomous driving and advanced driving assistance systems.
Security risks:
- Network Intrusion: Hackers may intrude into the vehicle's Ethernet system via the network, obtain unauthorized access privileges, and perform malicious operations or data theft on the vehicle.
- Remote Attack: Hackers may remotely connect to the vehicle's Ethernet system, exploit system vulnerabilities or weaknesses to intrude into the vehicle and control its functions.
Actual case:
- Remote Attack on Tesla (2016): Hackers infiltrated the vehicle through the Ethernet interface of Tesla vehicles, successfully controlling the vehicle's door locks, dashboard, and driving system functions.
- Remote Attack on Volkswagen (2019): Hackers infiltrated the vehicle through Volkswagen's Ethernet interface, successfully controlling the central control unit and dashboard functions of the vehicle.
Automotive Ethernet Security (ASec):
ASec is a set of standards and protocols for implementing security in automotive Ethernet. It includes support for message authentication, data integrity, access control, and secure key management.
Characteristics of Automotive Ethernet Security (ASec) protocol include:
Message Authentication and Integrity Protection: ASec provides mechanisms for message authentication and data integrity protection. It uses encryption algorithms and digital signatures to ensure the authenticity and integrity of messages, preventing messages from being tampered with or forged.
Access Control: ASec defines access control mechanisms to ensure that only authorized devices and entities can access the vehicle's Ethernet system. It can be based on authentication, access permissions, and role assignments for access control.
Security Key Management: ASec provides mechanisms for generating, distributing, and managing secure keys to ensure the confidentiality and security of keys. Key management is an important component of implementing secure communication, used for encrypting and decrypting communication data.
Security risks:
- Key Cracking: Hackers may attempt to crack the encryption keys used in the ASec protocol to gain unauthorized access to vehicle communication.
- Information Tampering: Hackers may tamper with the security authentication and integrity protection mechanisms in the ASec protocol to modify or forge messages in vehicle communication.
Actual case:
- Vehicle Remote Intrusion Attack (2019): Hackers successfully remotely infiltrated the vehicle's Ethernet system through a vulnerability in the ASec protocol, obtaining sensitive information and control of the vehicle.
ISO 14229 (UDS):
Unified Diagnostic Services (UDS) is a standard for vehicle diagnostics and communication. UDS defines a series of security mechanisms and services to protect the security of diagnostic communication and prevent unauthorized access.
Characteristics of UDS protocol include:
Secure Access: UDS defines a secure access mechanism to ensure that only authorized entities can access the vehicle's diagnostic interfaces and sensitive data. It uses challenge-response authentication and controls access permissions through secure access levels.
Data Privacy: UDS supports encryption of diagnostic data and data privacy protection. It uses encryption algorithms and data masking techniques to prevent unauthorized access and data leaks.
Security Diagnostics Session: UDS provides a mechanism for security diagnostics sessions, allowing sensitive diagnostic operations to be performed in a secure environment. Security diagnostics sessions typically involve programming, calibration, and configuration operations for vehicle control units.
Security risks:
- Unauthorized access: Hackers may attempt to access the vehicle's diagnostic interface in an unauthorized manner to obtain sensitive information or perform unauthorized operations.
- Diagnosis data leakage: Hackers may steal diagnosis data transmitted through UDS protocol, obtaining sensitive information or personal privacy of the vehicle.
Actual case:
- Automotive remote attack (2020): Hackers successfully carried out remote attacks on vehicles by exploiting the vulnerability of UDS protocol, including remote control and manipulation of various vehicle functions.
Real case explanation
Keen Lab
- Remote cracking security research results of multiple BMW models
In May 2018, researchers at Tencent Keen Lab found 14 security vulnerabilities in multiple BMW models. The research project lasted from January 2017 to February 2018, and they reported these issues to BMW afterwards. Because of this research, Tencent Keen Lab was awarded the first 'BMW Group Digital and IT R&D Technology Award', commending their outstanding research in promoting automotive security. - Cracking Tesla
- Announcing the crack
On September 21, 2016, Tencent Keen Lab officially announced that they had successfully intruded into Tesla cars in a 'remote without physical contact' way, which was the first in the world. In simple terms: their researchers can complete the remote control of Tesla simply by sitting in the office. - Process
This research on Tesla's vulnerability by Tencent Keen Lab took two months, with many researchers participating. They used a 2014 Model S P85 for security research and also conducted retesting on a new Model S 75D purchased by a friend, both of which were installed with the latest firmware, proving that this research can affect multiple Tesla models.
This attack was realized through the inter-network of Tesla vehicles, which is the premise for them to achieve 'remote without physical contact'. Theoretically, any Tesla model worldwide may be attacked by this kind of attack, as everyone's system is the same.
After successful intrusion, Tencent Keen Lab can replace the central control screen and LCD instrument panel of Tesla with the laboratory logo. At this time, any touch operation by the user will be invalid. Of course, the harm brought by this vulnerability is far beyond this kind of 'trick'. What they can do can be roughly divided into two categories, namely remote control in vehicle parking state and driving state. [8] - Re-cracking
In June 2017, the security researcher of Tencent Keen Lab successfully cracked the system of Tesla Model X, remotely controlling the brakes, doors, trunk, manipulating the headlights, and broadcasting. The researchers achieved the cracking of the vehicle system under both Wi-Fi and cellular connections, searched for computer vulnerabilities through the vehicle's web browser, sent malicious software, and realized hacker attacks.
- Announcing the crack
Technical Learning: Experimental Security Research of Tesla Autopilot
Summary
Vehicle bus refers to a system used for communication and data transmission between different electronic devices in a car. It plays an important role in the vehicle electronic system, realizing interconnection and collaboration among various components. The following are some key points for learning about vehicle buses:
- Vehicle Bus Types: Common vehicle bus types include CAN bus (Controller Area Network), LIN bus (Local Interconnect Network), FlexRay bus, Ethernet, etc. Each bus has different characteristics and application scenarios.
- Functions and Applications: Vehicle buses are used to connect and transmit data and signals between various electronic devices. They can connect engine control units, braking systems, instrument panels, entertainment systems, etc., to achieve functions such as data sharing, information transmission, and control command transmission.
- Data Transmission: Vehicle buses achieve communication by passing messages and data between various components of the vehicle. These data can be vehicle status information collected by sensors, control commands, fault codes, etc.
- Performance and Bandwidth: Different vehicle buses have different performance and bandwidth characteristics. CAN bus is suitable for real-time control and high-reliability applications, while Ethernet provides higher bandwidth and flexibility, suitable for high-speed data transmission and connecting complex systems.
- Safety: With the development of vehicle interconnectivity and automation, the safety of vehicle buses has become particularly important. Malicious attackers may manipulate vehicle buses to affect vehicle functions, steal sensitive information, or perform remote control. Therefore, the protection of vehicle bus safety is one of the important considerations in vehicle design and development.
- Standards and Protocols: To ensure compatibility and interoperability between different devices, vehicle buses usually follow specific standards and protocols. For example, CAN bus follows the ISO 11898 standard, while FlexRay follows the ISO 17458 standard, etc.
In general, studying vehicle bus systems can help understand the working principles, data transmission methods, and considerations of safety in vehicle electronic systems. This is crucial for vehicle manufacturers, engineers, and safety experts to ensure the performance, reliability, and safety of vehicles.
评论已关闭