In the field of information system security protection, identity authentication, as a necessary means of system access, has always been an indispensable and crucial topic. Identity authentication is often explained as proving 'you' by knowing 'what', owning 'what', or being 'who'. The identity authentication information/media has evolved from traditional physical keys, passwords, to static passwords, ID cards, to CPU cards, UKeys, dynamic tokens, and even to fingerprints, faces, and irises, etc., constantly innovating and having their own advantages. Multi-factor authentication is to enhance the strength of authentication by integrating various identity authentication methods.
In terms of theory, whether it is a physical key, password, static password, ID card, or biological features such as fingerprints, faces, and irises, they are all static identity authentication information/media. Therefore, in theory, they all have risks such as being easily copied, lost, and difficult to resist replay attacks. As the most effective, most reliable, and most economical key core technology for ensuring network and information security, password technology has inherent encryption and authentication properties and has become the most natural and most powerful means to achieve identity authentication. Dynamic password authentication technology is a typical example of using password technology to achieve identity authentication.
The dynamic token is the carrier for generating and displaying dynamic passwords (OTP/One-Time Password), common bank electronic password generators, Google's Authenticator identity authentication software, all belong to the category of dynamic tokens. Due to the different implementation principles of dynamic password authentication technology, this brings some difficulties to the evaluation institutions and information system responsible units when conducting compliance inspections of information systems. This article summarizes the common dynamic password authentication technology, briefly describes the main functions and security requirements of dynamic tokens and dynamic token authentication systems, and puts forward some suggestions for the evaluation implementation and judgment of identity authentication realization of dynamic password authentication.
First, related concepts and standards
OTP: One-Time Password
HOTP: HMAC-Based One-Time Password
TOTP: Time-Based One-Time Password
HMAC: The Keyed-Hash Message Authentication Code
RFC4226 HOTP: An HMAC-Based One-Time Password Algorithm
RFC6238 TOTP: Time-Based One-Time Password Algorithm
FIPS PUB 198 The Keyed-Hash Message Authentication Code (HMAC)
GM/T 0021-2012 Technical Specification for Dynamic Password Password Application
GB/T 38556-2020 Information Security Technology Technical Specification for Dynamic Password Password Application
GB/T 37092-2018 Information Security Technology Password Module Security Requirements
GB/T 15852.2-2012 Information Technology Security Technology Message Authentication Code Part 2: Mechanism Using Specialized Hash Functions
GB/T 15843.1-2017 Information Technology Security Technology Entity Authentication Part 1: General Provisions
GB/T 15843.4-2008 Information Technology Security Technology Entity Authentication Part 4: Mechanism Using Cryptographic Check Function
Second, dynamic password operation method
For the dynamic password generation method, we mainly focus on the following elements:
- Dynamic factor
- Seed key
- Dynamic password generation algorithm
- Basic password algorithm used in dynamic password generation algorithm
For convenience, we have isolated 4 from 3, at this time the dynamic password generation algorithm does not specify a specific basic password algorithm, but a theoretically replaceable password algorithm of the same type, such as symmetric password algorithm, hash password algorithm.
- HOTP generation: HOTP(K,C) = Truncate(HMAC-HASH(K,C)), where HASH = SHA-1
- TOTP generation: TOTP(K,T) = Truncate(HMAC-HASH(K,T)), where HASH = SHA-1/SHA-256/SHA-512
- GMOTP generation: GMOTP(K,T|C|Q) = Truncate(F(K,T|C|Q)), where F = SM3/SM4
Note 1: K is the seed key, T is the time factor, C is the event factor, Q is the challenge factor, and Truncate() is the truncation function.
Note 2: The meaning of T|C|Q is that T and C are mandatory, and Q is optional, then concatenated.
Note 3: When F is the SM3 algorithm, F(X,Y) = SM3(X|Y); when F is the SM4 algorithm, F(X,Y) = SM4_ENCX(Y), using a mode similar to CBC (IV is a string of zeros, XOR is replaced by arithmetic addition, and high-order overflow is discarded).
Note 4: Other details are not elaborated in this document, such as the conversion of time factors, data encoding/filling/truncation, etc., please refer to the relevant standards.
III. Dynamic Token Implementation of Identity Authentication
Mapping dynamic factors to time-varying parameters:
- Time factor T → Timestamp
- Event factor C → Sequence number
- Challenge factor Q → Random number
Both the authentication initiating party and the verifying party possess a seed key (authentication key), and they agree on the selection of dynamic factors. Both parties calculate the same dynamic password (verification value) using the same dynamic password algorithm (verification function) for the same dynamic factor and seed key (time-varying parameters and authentication key), thus satisfyingGB/T 15843.4-2008Information TechnologySecurity TechnologyEntity AuthenticationThe4Part: Mechanism of adopting a cryptographic verification functionThe specified authentication mechanism. When it only contains time factors or event factors, it is a one-way authentication transmission; when it contains challenge factors, it is a two-way authentication transmission.
IV. Workflow of Dynamic Token Authentication System
The dynamic one-time password authentication system provides dynamic password authentication services to the application system, consisting of dynamic tokens, authentication modules, and key management modules.
Dynamic one-time password tokens generate dynamic passwords, the authentication module verifies the correctness of the dynamic passwords, and the key management module is responsible for the key management of dynamic passwords. The application system sends the dynamic passwords to the authentication module according to the specified protocol messages for authentication.
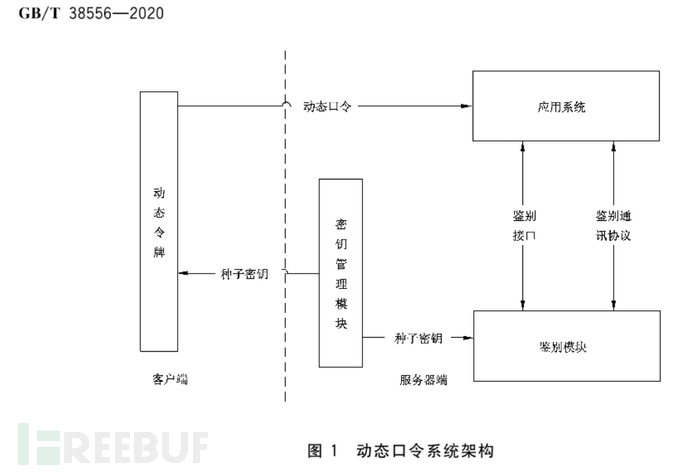
V. Time Synchronization
One-time password tokens can be regarded as offline devices that maintain the same dynamic factor with the authentication system through challenge codes generated by internal clocks, maintained counters, or application services (manually input into the token). When real-time time is generated by the internal clock as the time factor, minor deviations may occur within the lifespan of the dynamic token, at which point the token needs to be synchronized. Note that token synchronization does not involve adjusting the token itself, but rather modifying the offset of the corresponding token in the authentication system.
Synchronization with large window (±10 authentication cycle), medium window (±5 authentication cycle), and small window synchronization (±2 authentication cycle) are used to judge the size of the offset.
Six, Common Question Analysis
(1) HOTPwithTOTPWhat is the difference?
The 'H' in HOTP stands for 'HMAC-Based', meaning 'based on HMAC'. In terms of form, TOTP can also be considered a general HOTP.
Of course, the current standards have specified the dynamic factor and specific algorithms for HOTP and TOTP, so it is still necessary to distinguish in practice: HOTP uses event factor C (specifically, the counter) and calculates through HMAC-SHA-1 algorithm; while TOTP uses time factor T and calculates through HMAC-SHA-1 / HMAC-SHA256 / HMAC-SHA512 algorithm.
(2) Is the authentication using SMS verification code considered dynamic password authentication technology?
It does not belong. SMS verification code is an authentication method adopted by service providers to confirm the authenticity of the user's identity, which is different from the traditional static password verification. After receiving the client's request, a short message containing a string of fixed-length characters is sent to the user's mobile phone through a third-party service. The user enters this string into the identification interface of the application to confirm that the owner is performing login and other sensitive operations.
It is noted that only a different identification medium from the static password is used here, namely a mobile terminal (more accurately, a SIM card) that is bound to the user at the time of registration and can receive and send messages. The user's and user terminal's computing power is not utilized, and the user and user terminal do not hold the key, which is a crucial identification information. In addition, the string in the sent SMS itself is sensitive information, and in the process of legitimate identity verification (including dynamic password verification), the verifier does not send data or only sends intermediate information that does not contain explicit sensitive data. Therefore, SMS verification code authentication does not belong to dynamic password authentication technology and is not a legitimate identity verification method.
(3) NationalOTPwhether it is simply theSHAseries of hash algorithms and replace withSM3algorithm, becomes the national version based on the dynamic factor usedHOTPandTOTP?
China's National Standard One-Time Password (OTP) is not only inconsistent with the basic password algorithm and HOTP/TOTP, but the dynamic password generation algorithm itself is also different. China's National Standard OTP can adopt SM3 algorithm or SM4 algorithm. When using the SM3 algorithm, it is not the HMAC algorithm that is used to calculate the seed key and dynamic factor, but rather the seed key and dynamic factor are concatenated and then hashed with SM3; when using the SM4 algorithm, the seed key is used to encrypt the dynamic factor, and this method of using symmetric encryption algorithms is quite unique.
Dynamic factor | Seed key | Basic cipher algorithm | Dynamic password generation algorithm | |
HOTP | C | ≥128bit | SHA-1 | See Section 2 |
TOTP | T | HMAC output length | SHA-1/SHA256/SHA512 | |
National Cipher OTP (SM3) | T|C|Q | ≥128bit | SM3 | |
National Cipher OTP (SM4) | T|C|Q | ≥128bit | SM4 |
(4) How to determine the compliance of the dynamic token cipher product?
In the commercial cipher product certification system, dynamic tokens (SRK) and dynamic token authentication systems (SRT) are two types of cipher products, which are separately certified as commercial secret products. During the evaluation, it is generally necessary to separately examine the compliance of dynamic tokens and dynamic token authentication systems.
Dynamic tokens are generally hardware cipher modules, and currently, the security level of the cipher modules of dynamic tokens that have passed the commercial secret product certification is only level 1. It is not excluded that subsequent dynamic token products will pass higher-level certifications.
The dynamic token authentication system is a system-level cipher product with no cipher module grade, and it is difficult to ideally determine its form during the evaluation. It is recommended to consult with the customer and manufacturer whether there is a cipher module (server cipher machine, software cipher module, etc.) or a key management system, and if so, further trace the security level of the cipher module.
(5) The manufacturer provided a commercial secret product certification certificate for dynamic tokens, but the customer actually uses a mobile phoneAPPIs the cipher product compliant in this case?
GM/T 0021-2012 'Technical Specification for Dynamic Password Cipher Application Technology' and GB/T 38556-2020 'Information Security Technology - Technical Specification for Dynamic Password Cipher Application Technology' serve as the technical standards for this type of cipher product, mainly stipulating the requirements for hardware form dynamic tokens. In the original commercial cipher product model certificate, the prefix for the dynamic token product model is 'SRK', and the third 'K' represents the form as card-type.
In addition, for the software form of dynamic tokens, we need to investigate their lifecycle management, including the generation, distribution, storage, and use of the seed key, especially the key storage aspect, which is difficult to trace back to a reliable 'security root', which is also a pain point in the design of software cipher modules.
Of course, manufacturers may have developed related software products for the convenience of customers' use and management. Only when the software product passes the commercial cipher product certification can it be considered compliant with the cipher product. In the current commercial cipher product certification system, the numbers from the 6th to the 7th positions on the certification certificate number represent the product type, 14 represents dynamic tokens/dynamic token authentication systems, and 22 represents other cipher modules (including software cipher modules), for example, GM00441 can be learned from the business secret certification business network.142021xxxx is a dynamic token developed by a certain company. If in the future a dynamic token appears as a software form passing the commercial secret product certification, the product type may be '22' instead of '14', which is worth noting.
(6) Dynamic Token/If the dynamic token authentication system has an effective commercial password product certification certificate, can the 'key management' dimension of the related evaluation items be directly judged as compliant?
No. At least the following contents need to be considered:
- If it is used for application system identity authentication, it is necessary to test whether the dynamic password authentication has been effectively applied.
- When the dynamic token authentication system itself is used as the evaluation object at the device level, it is still necessary to evaluate the identity authentication mechanism and remote management channel when managing it.
- It is necessary to evaluate the lifecycle management of the seed key in the dynamic token/dynamic token authentication system, especially the generation/distribution, import (distribution), storage, and use processes.
- It is necessary to view the management interface of the dynamic token authentication system, such as token serial number management, key management, token status, consecutive error times, token offset, algorithm configuration, etc. (if any).
- It is necessary to check whether the evaluation level matches the security level of the password module, such as the third-level information system should adopt dynamic token products that meet or exceed the level 2 of GB/T 37092, and theoretically, the password module components contained in the dynamic token authentication system should also meet or exceed the level 2 requirements of GB/T 37092.
(7) UseGoogle AuthenticatorOrMicrosoft AuthenticatorAs a dynamic token for server operation and maintenance personnel's identity authentication, how to determine the assessment item of 'identity authentication' for the server?
Google Authenticator and Microsoft Authenticator are common OTPs in the app store. The following is a sample evaluation (not considering the OTP authentication server for the time being).
Quantitative Assessment | Risk Assessment | |||
D | A | K | ||
Google Authenticator | √ Supports HOTP and TOTP. | × Non-compliant password algorithms and dynamic password generation algorithms are used. | × Non-compliant key generation, distribution, storage, and non-compliant password products. | 1. If HOTP is used, it needs to be judged as high risk for the SHA-1 algorithm; if TOTP based on SHA-1 is used, it is judged as high risk. The risk level of key management needs to be determined according to the actual situation. |
Microsoft Authenticator | √ Supports TOTP. | × Non-compliant password algorithms and dynamic password generation algorithms are used. | × Non-compliant key generation, distribution, storage, and non-compliant password products. | 1. If TOTP based on SHA-1 is used, it is judged as high risk. The risk level of key management needs to be determined according to the actual situation. |
There are many types of open-source OTP or OTP authentication service servers on the market, such as Google Authenticator (which is not consistent with the store version and has stopped maintenance), FreeOTP/FreeOTP+, LinOTP, and others, most of which support HOTP and TOTP, and the specific conclusion is subject to the actual evaluation results.
评论已关闭