At the beginning, due to the limited space and not wanting to deviate too far from the topic, many contents in the article have not been further discussed. If the readers are interested, they can chat privately or discuss in the comments.
1. Background
ATT&CK;Attack Matrix(Enterprise)There are a total of11column, separating and summarizing the attack technologies of different links and different打击 targets, which is of great reference significance to the defense sideSOCThe coverage capabilities of security devices, defensive means, detection rules, intelligence, etc. can be mapped in the matrix, thus sensing the currentSOCthe detection and defense capabilities, and plan the future direction.


HoweverATT&CK;The matrix is not a silver bullet, and there are many issues worth thinking about:
(First)The matrix coverage evaluation of defensive and detection capabilities should be0and1right?
(Second)for a certain technical link, if the current situation can completely defend or detect, will it no longer need to pay attention or invest human resources in the future?
(三)for the different regional environments of the enterprise for a certain attack technology(headquarters and branches, various suppliers,(BYOD)whether they have the same defensive and detection capabilities?
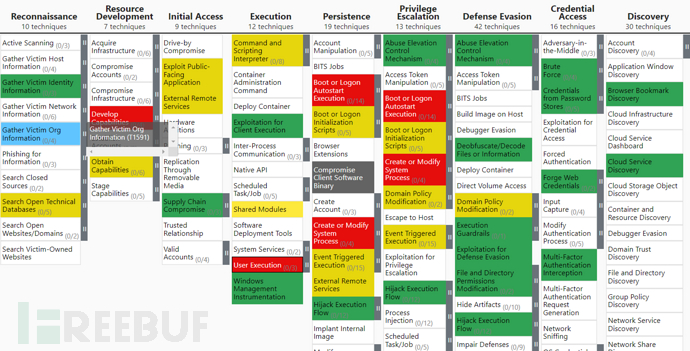
BITS Jobs--T1197 | Security device coverage | Defensive capabilities | Detection capabilities |
Beijing Headquarters | EDR DLP | Strong | Strong |
Shanghai Branch | DLP | Weak | Strong |
Guangzhou Branch | None | None | Weak |
(四)in the matrix11column, whether it has the same importance for the resource investment of the defense side? If not, what is the priority order?
(五)whether the different technologies and sub-technologies in each column of the matrix have the same importance for the resource investment of the defense side? If not, what is the priority order?
This series of articles, the author will analyze in detailATT&CK;the technology of the matrix, and discuss each technology in depth, as well as the defensive and detection deployment that the enterprise environment should make for these technologies.
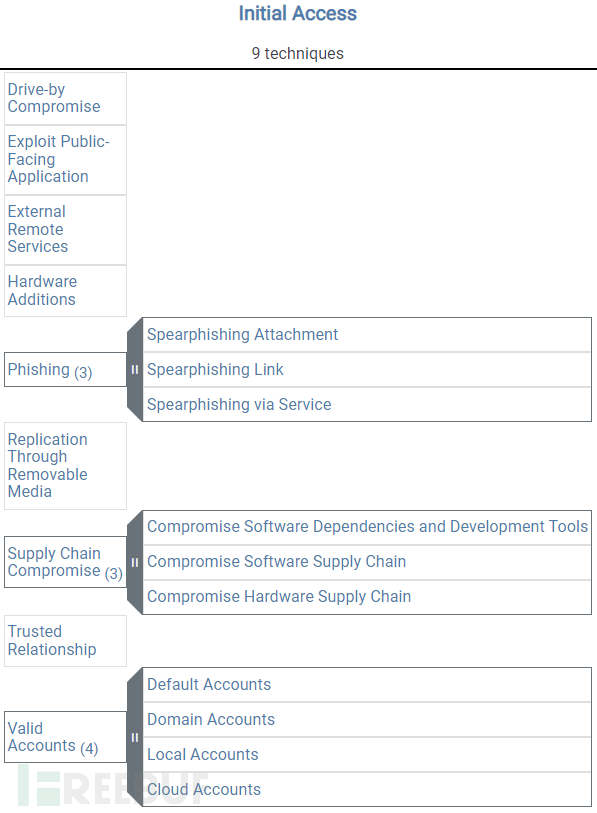
In this article, let us enterATT&CK;The third column of the matrix:Intial Access,详细分析其中的技术有哪些,涉及企业安全工作建设中的哪些内容。
二、技术总体介绍
(First)Drive-by Compromise
主要思路是水坑攻击,笔者上一篇文章已经详细介绍过这个技术及SOC做防御需要收集的日志,请参考https://www.freebuf.com/articles/es/336620.html.
(Second)Exploit Public-Facing Application
直译为"利用面向公众的应用程序",翻译过来就很好理解了,其实就是广大渗透测试者、众多CTF竞赛中最常见的攻击方式,攻击对外暴漏的服务(任意外网可访问的系统),具体包含的攻击目标不限于:Web系统、邮件服务、VPN服务、负载均衡。其中最喜闻乐见的应该是Web系统,由于各种语言、框架、组件层出不穷,针对性的漏洞也是一批又一批,可以说是给了安全工作者牢靠的饭碗。
同时,企业对Web系统攻防对抗的投入,应该是资源占比最大的,下一代防火墙、WAF、流量分析设备、HIDS,RASP等等安全设备、应用、机制,都很好的保护着面向公众的应用程序。
(三)External Remote Services
外部远程服务,主要指的是企业开放给内部员工、供应商的外部服务,如VPN,API,SSH服务、RDP服务、Citrix等云桌面、邮件系统等等。这些服务通常有针对性的服务对象,所以可以做一定的限制,如限定源IP访问、MFA、端口敲门技术(ReferenceATT&CK-T1205.001),MAC绑定等。

(四)Hardware Additions
添加硬件到目标环境中,主要是物理渗透的场景,比如物理接触目标机器,通过PE系统进入机器完成攻击;在目标公司大厅扔一个U盘、BadUSB进行钓鱼等等。

(五)Phishing
钓鱼,笔者认为,是HW等各种攻防对抗中,最简单易行且杀伤力最强的攻击手段。钓鱼邮件漫山遍野,企业环境中不配置一个商用的邮件网关和Exchange防病毒模块,都不好意思说自己是重视安全的。

SPF,DKIM,DMARC、邮件防病毒模块一样不落,面对APT级别的攻击者时有用吗?没有用!对邮件投递做白名单限制,限制附件后缀,不允许投递可执行文件、不允许投递加密的压缩包,但攻击者还可以通过钓鱼页面钓鱼(ReferencegophishFramework), no matter how many security awareness training sessions are conducted, we must firmly believe that ordinary users will definitely be deceived.

However, can phishing only be done through email? Not at all. The delivery process of email can be completely monitored, controlled, and analyzed by the enterprise, but other channels may not be the same. WeChat,QQ, DingTalk, and variousIMSoftware, can also be used for phishing, and the cost of defense is huge. In the recent phishing incident of Sohu, the attacker adopted a new method of QR codes. When seeing a QR code, the normal reaction of most people is to take out WeChat and scan, this"Scan"The subsequent process is completely uncontrollable to the security defense personnel, and it is really difficult to prevent.

(Six)Replication Through Removable Media
Replication through portable media mainly refers toUSBAnd other portable devices, deliver malicious programs to the target machines, and then complete the execution of malicious programs through various automatic execution techniques.
(Seven)Supply Chain Compromise
Supply Chain Attack, an easily understandable attack method, attacking the upstream hardware equipment used by enterprises, such as backdoors at the chip level; attacking the software source used by enterprises, such as the incidents that occurred beforePYPIwarehouse, if youPythonpackage reference, accidentally poisoned therequestswritten asrequest, then unfortunately, your computer or even your colleague's computer may already belong to others.
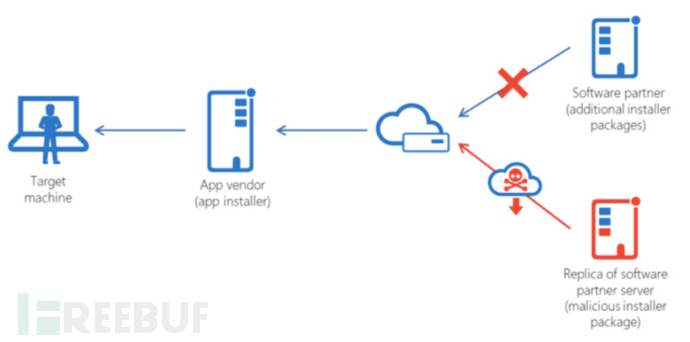
(Eight)Trusted Relationship
Through trust relationship attacks, enterprises usually have more or fewer suppliers, contracting different service contents, and suppliers usually need to access some or all of the internal systems. Authorizing suppliers is unavoidable, and the relationship between suppliers and the company"Trust"Relationship, whether it can be trusted or not?
This year in early JanuaryLAPSUS$Organizations, publicly announce in a loud voice: they are through"Purchase","Fraud"Methods, directly obtain the accounts of enterprise users or suppliers, and simply completeInitial Access. Therefore, access control is also very important.

(Nine)Valid Accounts
Effective accounts, like"No matter how many security awareness training sessions are conducted, we must firmly believe that ordinary users will definitely be deceived."This conclusion is the same, and we still firmly believe that the account passwords in the enterprise environment will be exposed to attackers, that is to say, attackers are definitely able to obtain the account passwords of some systems in the enterprise environment.
Why am I so sure?
Firstly, weak passwords are difficult to eliminate. Even with complex password policies, there will always be clever users who cleverly bypass the password policy and set some"Weak Password"For example, setting the password policy to require uppercase letters, lowercase letters, numbers, and special characters, and the length must be not less than8Position, it seems to be a very strong strategy, however, there will definitely be users who set their passwords to:"Aa123!@#", obviously this password is in line with our high-complexity password policy, but is this password weak? Very weak! Just find a dictionary commonly used by attackers, and you will definitely find it.
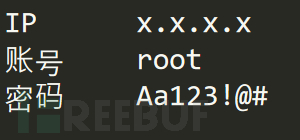
Secondly, it is a common practice for different systems to reuse the same password, which is also easy to understand because withoutonepasswordsuch tool, we cannot remember a large number of different passwords with the human brain(Unless the password is recorded in a.txtfile, and then put this file on the desktop. That's right, attackers like you to record passwords in this way, hahaha), and if different systems use the same password, it is easy to lead to the leakage of external system passwords in the social engineering library(It cannot be guaranteed that all systems salt and hash the storage of passwords, nor can it be guaranteed that salt and hash are always effective)Thus, it is equivalent to leaking the password of the company's system.

Third, summary and extension
(First)Initial AccessContent summary
The target of the attack technology in this link is what? From the above introduction, it is not difficult to see that it is actually what the red team often says"punching". Although it is not necessary to use all the technologies in one attack,ATT&CK;Each technology in the matrix, but this11The list of technologies is still arranged in order,Initial AccessAfter the technology completes the attack, it will go toExecutionlink,ExecutionWhat is it? It is the execution of malicious software, so the step before execution is actually to contact the target environment, deliver malicious samples, and only after delivery can execution take place.

(Second).extension of attack technology
ATT&CK;inInitial Accessin9types of technology(Techniques)can be summarized as follows in the table below6types, then theseSpecific attack programs for different types of attack technologies(Procedures)and how to defend(Mitigations)and how to detect(Detection)What aboutWhat's next? Let's start with a detailed analysis.
Serial number | Attack types | Characteristics |
1 | phishing | Simple and effective |
2 | Waterhole Attack | High difficulty in implementation |
3 | Physical contact -- portable media devices | A certain degree of physical contact is required |
4 | Internet boundary vulnerabilities | The focus of corporate security defense work |
5 | Supply chain attack | High difficulty in implementation, with extremely strong destructive power |
6 | Social worker obtains permission | It is difficult for the defense to avoid |
1.phishing
There are various phishing methods, based on email,IMSoftware, customer service, and other delivery channels, obtain passwords through phishing pages, deliver malicious programs through attachments, and impersonate headhunters,HRdeceiving employees, impersonating customers and suppliers to deceive customer service, and other social engineering types.
Although there are various attack methods, they belong to"Easy to attack but hard to defend"In this field, but we security workers cannot just lie down and relax; we still need to make the efforts we should:
a.Strengthening the infrastructure of email, such asSPF,DKIM,DMARC, email antivirus module, sandbox detection(try to shift left as safely as possible),YARAdetection
b.Strengthen the network infrastructure, such as disabling unsupportedMFAnetwork protocols such asPOPetc.
c.Strengthen user browsers, you can refer to the browser isolation solution
d.坚持不懈的进行用户安全意识培训
e.Regular internal phishing and publicity
f.制定好用户被钓鱼后的应急预案,尽量通过SOARAutomation
g.制定针对钓鱼邮件的SIEMDetection Rules(If readers are interested in this part, a separate article can be written to introduce it later)
h.enable as many application systems as possibleMFA, for those who cannot enableMFAsystem or user should be subject to special monitoring. AlthoughMFAIt is not a foolproof strategy either, throughTLSIntercept the reverse proxy as a man-in-the-middle and the attack can still be completed, but security itself is about countering, you have a strategy, I have a way to climb over the wall
g.Threat Intelligence, analyze the phishing information inURLsuch as file hash information for threat intelligence analysis, and decide the follow-up forwarding strategy based on the analysis results

2.Waterhole Attack
Waterhole attacks are a browser-based attack method that lures the victim to a compromised website and then redirects through a series of redirections to a vulnerability exploitation page, where exploitation tools for browsers and browser plugins are deployed, delivering the payload directly to the victim's machine.
Waterhole attacks are actually a complex and high-difficulty attack method that is relatively uncommon. Browser isolation solutions can perfectly counter attacks targeting browsers: users surf the internet through a browser web proxy, the browser proxy parses and renders the page, and presents the final image to the user terminal. If there is a vulnerability in the browser and the malicious page of the attacker is accessed, it will only be executed in the web proxy, and will not affect the user's terminal.

Even without using browser isolation solutions, there will still be a large number of attack characteristics in waterhole attacks. For corporate defense work, this is consistent with the work content of defending against ordinary malicious programs, anti-rootkit, spyware, mining software, ransomware, and other threats. This is also the difference between the perspective of defenders and attackers. Defense is targeted at specific strategies based on the attack surface, while attacks are initiated from attack points and vectors.
3. Portable Media Devices
There are mainly two types of attacks on portable media: one is physical contact with the user's machine,PEsystem enters the machine or throughBadUSBTo conquer machines, this type of attack requires the attacker to infiltrate the corporate environment, which is usually quite difficult, so it will not be analyzed in detail. Another method is to deceive users into inserting the attacker's portable device into their own computer, and then deliver and execute the malicious program through automatic execution, automatic playback, and other methods. This type of attack does not require the attacker to personally contact the target machine, so it is relatively easy to complete. The following mainly discusses this type of attack.

There are many ways to implement attacks, examples are as follows:
(1)By autorun.inf to automatically run other executable files.
(2)By automatic playback(autoplay)to implement the execution of malicious programs.
(3)Place executable files in portable devices and deceive users into clicking, for example:
a.Dual file extensions, for examplea.pdf.exeSo that the victim mistakenly believes it ispdffile to complete the click
b.Byunicode 202EMirror the file name for display, and deceive the victim into clicking
(4)Mask the network device as aUDisk(It can also be a power bank, even a charger), realizing traffic hijacking, keyboard recording, and other functions.
Defense strategyThere are many, such as
a.Directly prohibit the use of portable devices through group policy, and whitelist based on serial number
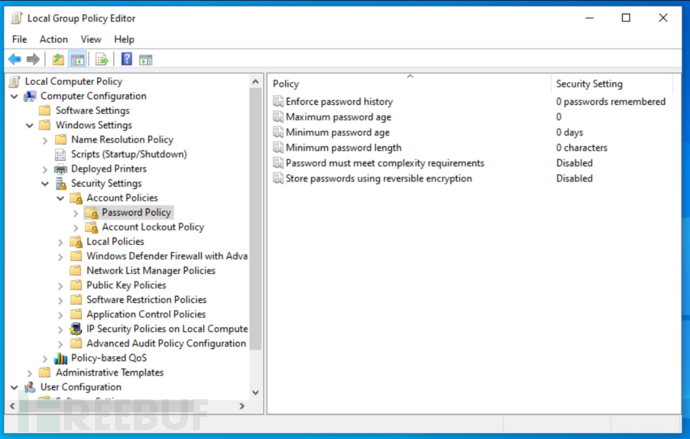
b.Enable within the domainapplocker, specify fine-grained control policies, and limit the execution of malicious programs
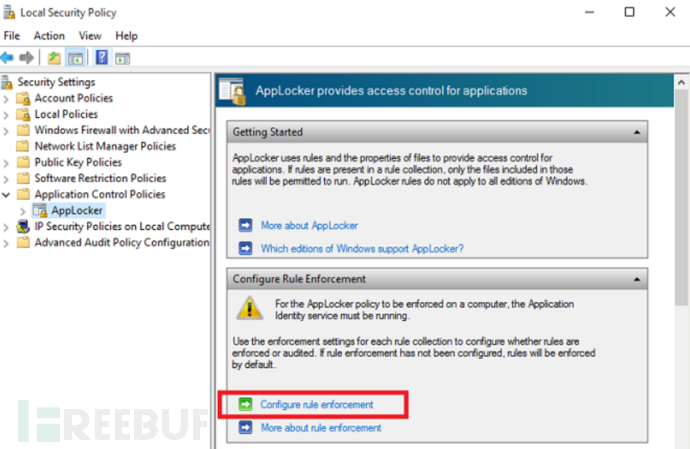
c.Use forUSBsecurity protection software
...
Of course, physical contact is not limited to using portable media devices, but also to access the enterprisewifiThenARPPoisoning,DNSDeception,TLSMan-in-the-middle attack,LLMNRPoisoning to obtainNet-NTLM Hash爆破and other methods...
4. Internet boundary vulnerability
The protection of boundary services requires enterprises to invest a large amount of manpower, material resources, and time to do it well, and will not elaborate in detail. The following is a simple example:
a.Patch software applications
b.Patch the operating system
c.DeploymentWAFsuch as next-generation firewalls, traffic analysis, and other security devices
d.Operate the strategies of security devices
e.Handle the alarms of security devices
f.Targeted0-dayTimely and effective response to vulnerabilities

5.Supply chain attack
6.Social worker obtains permission
I can't write anymore...To be continued in the next article!
评论已关闭