Author: Track-Tobisec
0x1 Preface
Here, I share some common information collection tactics with the elders, mainly for cases where we encounter some like the case I want to share this time, which is very common, such as the unified identity authentication in deusrc or using student numbers as accounts, and then the last six digits of the ID card as passwords, etc. Generally, it is common to need to collect relevant account passwords for information collection.
0x2 Information Collection Tactics

Generally speaking, the email of what edu school or some HW action corporate group is more ideal for querying emails
For example, sometimes when you search for an email of an edu university, you can actually look fromThe email can find student numbers and work numbers
https://hunter.io/search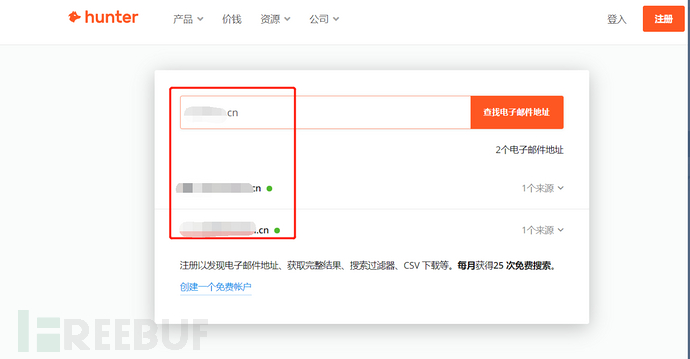
There is also the Google syntax, which is very common on the internet, and I have summarized some commonly used ones for the elders
1.site: domain intext: management|background|login|username|password|verification code|system|account|manage|admin|login|system2.site: domain inurl: login|admin|manage|manager|admin_login|login_admin|system3.site:domain intext:"manual"4.site:domain intext:"forgot password"5.site:domain intext:"employee number"6.site:domain intext:"excellent employee"7.site:domain intext:"ID card number"8.site:domain intext:"phone number"
Then, there is also a tool written by the great master. You put the keywords you want to search for into it, and the tool will give you the Google grammar for information collection, such as the following tool. Those who are interested can download it from github.
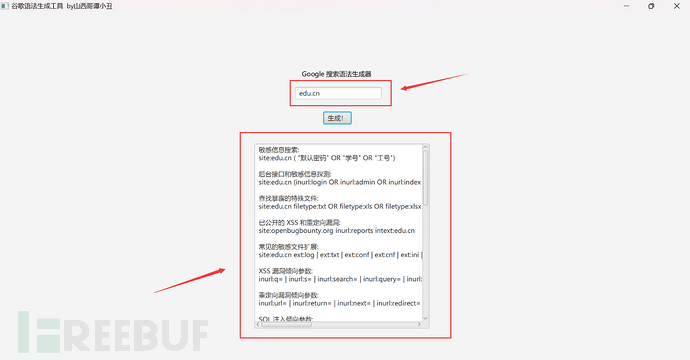
0x3 Practical example
Information collection for account passwords
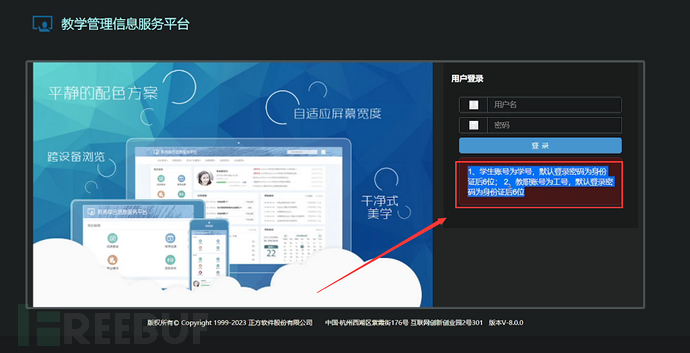
Teachers can see that the educational information service platform of the school I found is
This prompts us that the account is the student number, and the default password is the last six digits of the ID card. When I see such an edu site, I will first check my school reserve library to see if there is any related student number information in it before. Then, I will look for some ID card-related information on the Internet using some Google grammar.
The following uses the syntax provided by the Google grammar tool directly.
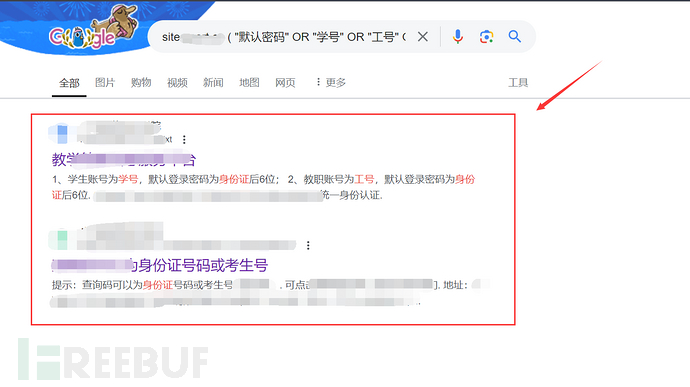
site:domain ("default password" OR "student number" OR "employee number" OR "ID card")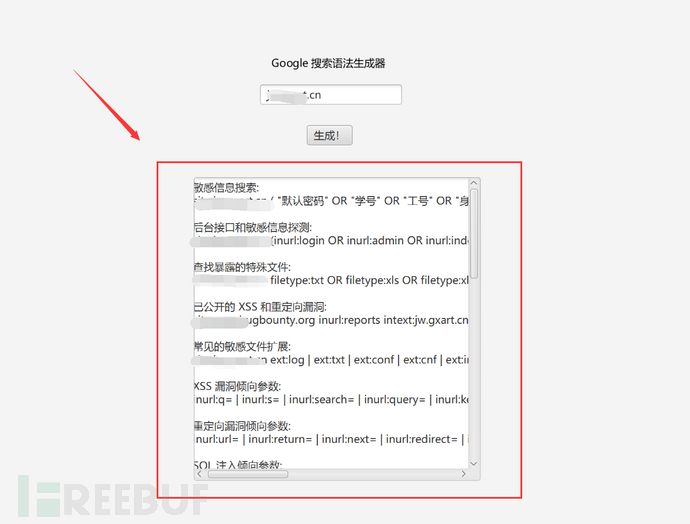
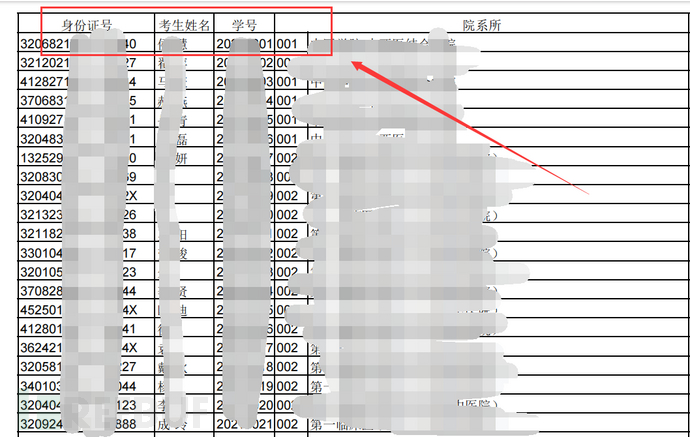
Then, I found the leaked student numbers and ID card numbers of the school in this interface. Later, I logged into the background of several students using this student number plus the last six digits of the ID card. Most of them have changed the initial password, but I believe there are still some students who do not want to change the initial password of the last six digits of the ID card becauseConvenient
However, this vulnerability was fixed after it was submitted to the eudsrc platform, and the pdf document is also not available now.
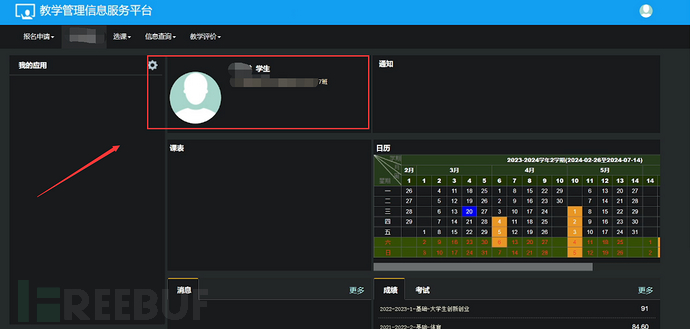
Later, I logged in directly to the background of the teaching platform with the account and password collected by information collection.
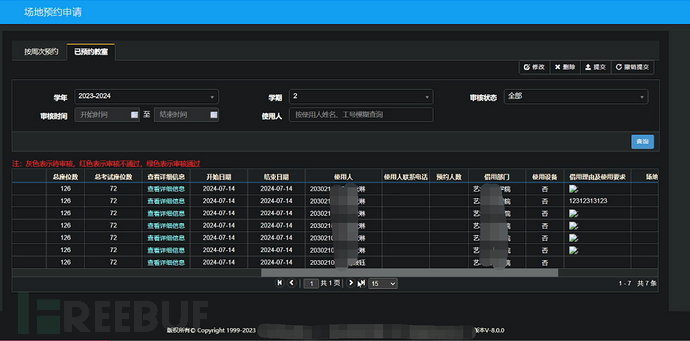
0x4 Summary
The case shared above is a real one. By using some information collection methods, such as some search syntax on the Internet, such as Google hacker syntax, you can find some information that you may not find in your daily life. However, by using some hacker syntax, you can find relevant information, and then use the collected information to attack this test site. The website also has XSS and SQL injection vulnerabilities, but I will not demonstrate them for the teachers. This sharing is mainly to share the importance of information collection with the teachers, including some common information collection methods.
All sensitive information involved in the article has been blurred for processing. The article is only for the purpose of sharing experience and should not be taken seriously. Unauthorized attacks are illegal! All sensitive information in the article has been processed with multiple blurring. Any direct or indirect consequences and losses caused by the use of the information provided in this article shall be borne by the user himself/herself, and the author shall not bear any responsibility for it. Once the consequences occur, please bear them yourself!
评论已关闭