Preface
Is it okay to just put the information system that carries and supports business operations somewhere without using it, ignore it, or dispose of it arbitrarily?
The life cycle of an information system generally includes five stages: planning, design, construction, operation, and termination. The focus of public concern is often on how to carry out corresponding network security protection work in the planning, design, construction, and operation stages of information systems, but insufficient attention is paid to the network security protection of the termination stage of information systems. Today, the author will talk about how to scientifically and correctly handle the termination of information systems from the perspective of network security protection to ensure the security of information assets (especially data assets).

This article applies to the network security protection work during the termination of non-secret information systems. Secret information systems can, according to national relevant requirements and combined with the actual situation of the enterprise, refer to this article to carry out corresponding network security work.
1. Forms of information system termination
If the information system itself belongs to a key information infrastructure, the termination of the information system is also known as the shutdown or decommissioning of the key information infrastructure. In the context of key information infrastructure, 'termination' is synonymous with 'shutdown' and 'decommissioning and abandonment'. The origin of 'shutdown' can be found in the 'Regulations for the Security Protection of Key Information Infrastructure (Draft for Comments)', and the origin of 'decommissioning and abandonment' can be found in the national standard 'Information Security Technology Security Protection Requirements for Key Information Infrastructure (Review Draft).
To get back to the point, is the termination of the information system simply not to use it at all, completely discontinuing the entire object? It is not entirely true. Some information system terminations are not truly废弃, and generally, they can be divided into three types:
1. Complete termination
The complete termination of the information system refers to the complete discontinuation of the system, and all information of the information system needs to be cleared.
2. Partial termination
Partial termination refers to the discontinuation of some functions or equipment of the information system, such as the need to remove certain system functions due to business changes. The information to be terminated in the information system should be cleared.
3. Transfer
The transfer of information systems generally includes the following forms:
(1) Migrating from a traditional physical environment to a cloud environment or another traditional physical environment;
(2) Migrating from one cloud environment to another cloud environment;
(3) Migrating from a cloud environment to a physical environment;
(4) Improving technology or transforming business to new information system objects, such as functional integration, system upgrades, etc.;
(5) Other forms.
In this case, it is necessary to ensure the security of information transfer and equipment migration.
The main work requirements for information system termination
Before discussing how to ensure the security of information assets during the termination of the information system, let's first talk about the main work requirements in terms of network security protection during the termination of the information system.
1. If the termination of the information system is determined, the enterprise should report the relevant situation of the information system to be terminated in a timely manner to the relevant user units and management departments. If the information system belongs to a key information infrastructure, it should also report the relevant situation of the key information infrastructure to be shut down to the national industry主管部门 or regulatory authorities (see Article 20 of the 'Regulations on the Security Protection of Key Information Infrastructure').
2. It should follow relevant policies, laws and regulations, and standards to formulate an implementation plan for information system termination, clarify the relevant security disposal content of information assets, and implement it strictly according to the plan.
3. Risk response measures should be formulated before the start of the information system termination activity to prevent emergencies during implementation and to respond promptly. During the implementation process, potential unexpected situations should be monitored, and contingency measures should be prepared.
4. Before termination, partial termination, or transfer of the information system, devices or storage media containing data should be completely, thoroughly, and securely erased or overwritten according to the data security management strategy to ensure that they cannot be restored and reused. For important devices or storage media containing sensitive information, it is recommended to choose qualified institutions for secure destruction and keep detailed records of the handling process.
5. Before the transfer of the information system, data should be backed up as needed. During the transfer, the business migration specifications should be strictly followed to ensure a smooth and secure migration of the business, and to meet the requirements of business availability, stability, and continuity.
6. The safety management department, business department, and user department should be organized, and external experts should be invited when necessary, to jointly review the rationality and applicability of the implementation plan for information system termination.
7. If an external organization is entrusted to assist in the termination of the information system, a confidentiality agreement should be signed with the external organization.
The main steps of information system termination
The main steps of information system termination include preparation for information system termination activity, compilation and review of information system termination implementation plan, fulfillment of approval/reporting procedures, implementation of information system termination activity, and compilation of summary report, etc.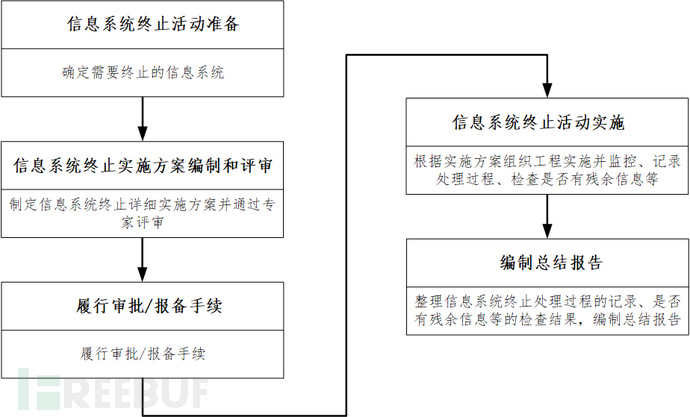
1. Preparation for information system termination activity
(1) Determine the need for information system termination
In response to changes and impacts of national or industry policies, market factors, as well as the possibility of information system termination due to its own technical upgrade, transfer, etc., the enterprise/organization shall carefully assess whether the information system needs to be terminated. If it is determined that the information system needs to be terminated, the enterprise/organization shall compile the information system termination statement, including the reasons for termination, specific form, person in charge, and other information.
(2) Report to relevant departments
The enterprise/organization shall report to the relevant internal departments in a timely manner. If the information system belongs to the key information infrastructure, it shall also report the relevant situation of the shutdown of the key information infrastructure to the national industry competent department or regulatory authority, and properly keep the related receipts.
(3) Sort out the list of information systems to be terminated
The enterprise/organization shall collect relevant information about the information systems to be terminated, such as network topology, equipment asset list, etc., to form a list of information systems to be terminated. The content of the list generally includes:
1) List of relatively independent information system objects to be terminated;
2) Overview of each information system object to be terminated;
3) Boundary of each information system object to be terminated;
4) Location and current status of each information system object to be terminated;
5) Service scope of each information system object to be terminated;
6) Other.
2. Compilation and review of the information system termination implementation plan
(1) Compilation of the information system termination implementation plan
Based on the list of information systems to be terminated, the enterprise/organization shall compile the implementation plan according to the form of the information system to be terminated. The content of the implementation plan mainly includes:
1) Overview
Describe the policy background, basis, necessity, and activity objectives of the information system termination.
2) Content of information system termination
Describe the detailed handling plan for the information system to be terminated, including the handling method, process, key technologies, and hardware and software tools required.
3) Implementation plan
Describe the personnel arrangement and time schedule during the implementation process.
4) Risk response measures
Describe the unexpected situations that may be encountered during the implementation process, as well as the risk response measures that can be taken.
(2) Review of the implementation plan
The enterprise/organization shall organize the safety management department, business and user departments, experts, and others to review the safety requirements together, make good review records, and modify the implementation plan report according to the review opinions.
The review content generally includes:
1) Whether the list of information systems to be terminated is complete;
2) Whether the implementation schedule and personnel arrangement are reasonable;
3) The rationality and feasibility of the content of the information system to be terminated, and whether the hardware and software tools used during the implementation process meet the actual needs;
4) Whether the risks encountered during the implementation process are considered comprehensively, and whether the risk response measures are in place.
3. Fulfill the approval/reporting procedures
Enterprises/organizations should clearly define the authorization and approval matters, approval departments, and approvers (such as the cyber security department) for each department and position, establish approval procedures for important operations in the implementation plan for decommissioning and abandonment, and implement the approval process according to the approval procedures. Where necessary, a hierarchical approval system can be established.
The approval process can adopt electronic approval, paper approval, and other forms. Enterprises/organizations should properly preserve the relevant approval materials for future reference.
Enterprises/organizations should regularly review and approve matters, and timely update the matters that require authorization and approval, as well as the approval departments and approvers.
4, Implementation of information system termination activities
Enterprises/organizations should implement the implementation plan strictly in accordance with the plan, monitor unexpected situations that may occur during the implementation process, record the processing process of the information systems to be terminated (including the participants, the methods of handling, the current location of the information systems to be terminated, etc.), and check whether there is residual information.
Implementation activities mainly include the following contents:
(1) Prepare the tools, materials, and other items needed for the implementation process, as well as coordinate related matters.
(2) Obtain the processing permissions for the information systems to be terminated, such as copying, clearing permissions, etc.
(3) If the form of information system termination is transfer, data backup is required as needed.
(4) Strictly implement the implementation plan for the information systems to be terminated, monitor unexpected situations that may occur during the implementation process, and record the processing process in detail (including the risk response process).
(5) Check whether there is residual information in the information systems to be terminated, as well as whether there are physical or logical connections with other systems, and whether the connections are closed.
(6) If the form of information system termination is partial abandonment, in addition to checking the abandoned part, it should also be checked whether the changes have introduced new risks.
(7) Summarize the processing process records of all information systems to be terminated, and check the results of whether there is residual information, etc.
(8) Return the permissions, related materials, and tools for handling the information systems to be terminated.
5, Compile the summary report
After the implementation is completed, enterprises/organizations should organize the results of the check on the processing process of the information systems to be terminated and whether there is residual information, and compile the information system termination report.
Summary reports generally include the following contents:
(1) Overview
Information systems are terminated based on changes and impacts of national or industry policies, market factors, or due to the system's own technical upgrades or transfers.
(2) Detailed description
In combination with the list of information systems to be terminated, the records of the processing process, and the results of risk assessment, a detailed description of the entire implementation process is provided, and a new business application including the current location of each information system to be terminated and the transfer object is formulated.
(3) Conclusion
By analyzing the entire information system termination process, conclusions can be drawn on whether the termination process is standardized, whether it is abandoned or transferred reasonably, and whether there are any omissions.
Four, the main activities of information system termination
The termination of information systems involves a wide range of contents, this article focuses on the security of information assets during the termination process of information systems, mainly including information transfer, temporary storage and deletion, equipment migration or scrapping, as well as the deletion or destruction of storage media.
1. Information transfer, temporary storage, and clearing
During the processing of the information system to be terminated, appropriate measures should be taken to securely transfer or temporarily store information assets that may be used in other information systems into recoverable media, ensuring that they can be used in the future, and at the same time, use secure methods to clear information from the objects to be discarded.
(1) Determine the information assets to be transferred, temporarily stored, and cleared
List the inventory of information assets to be transferred, temporarily stored, and cleared, see Chapter 3 Information System Termination Activity Preparation for details.
(2) Compilation, review, and approval of information asset transfer, temporary storage, and clearing plans
Formulate the handling methods and procedures for information assets, and if they contain sensitive or classified information, they should be transferred, temporarily stored, and cleared according to the regulations of relevant national departments.
It should organize the review and evaluation of the rationality and feasibility of the information asset handling plan, and provide modification suggestions.
The information asset handling plan should be reviewed and approved by the leader of the cyber security department before implementation.
(3) Transfer, temporary storage, and clearing of information assets
Strictly follow the information asset handling plan for the transfer, temporary storage, and clearing of information assets, monitor unexpected situations during the implementation process, and record the process of information transfer, temporary storage, and clearing, including personnel involved, transfer, temporary storage, and clearing methods, and the current location of the information.
2. Device migration or disposal
Ensure that no sensitive information is included in the equipment to be migrated or disposed of after the termination of the information system, and the handling method of the equipment should comply with the requirements of relevant national departments. The general steps are as follows:
(1) Determine the retired and discarded hardware and software equipment
List the inventory of hardware and software equipment to be migrated or disposed of, see Chapter 3 Information System Termination Activity Preparation for details.
(2) Compilation, review, and approval of hardware and software equipment handling plans
According to regulations and actual conditions, formulate a handling plan for hardware and software equipment, including the migration of equipment, disposal of equipment, and methods for clearing sensitive information.
It should organize the review and evaluation of the rationality and feasibility of the device handling plan, and provide modification suggestions.
The device handling plan should be reviewed and approved by the leader of the cyber security department before implementation.
(3) Handling of hardware and software equipment
Strictly follow the device handling plan for device migration or disposal. If the device contains sensitive or classified information, the handling process should comply with the regulations of relevant national departments; monitor unexpected situations during the device handling process, record the process of device migration or disposal, including personnel involved, handling methods, and the current location of the devices; check for any residual information.
3. Clearing or destroying storage media
Through the adoption of reasonable methods, information clearing or destruction of storage media (including tapes, disks, printouts, and documents, etc.) is carried out to prevent the leakage of sensitive information within the media. The general steps are as follows:
(1) Determine the media to be cleared or destroyed
List the inventory of storage media to be cleared or destroyed, see Chapter 3 Information System Termination Activity Preparation for details.
(2) Compilation, Review, and Approval of Storage Medium Handling Plans
The handling plan for storage media should be formulated based on the sensitivity of the information carried by the storage media, including data clearing and storage medium destruction, etc. If the storage medium contains sensitive information, it should be handled in accordance with the regulations of relevant national departments.
It should organize the rationality and feasibility review of the storage medium handling plan and provide modification suggestions.
The storage medium handling plan should be reviewed and approved by the leader of the cyber security department.
(3) Storage Medium Clearing and Destruction
Strictly follow the storage medium handling plan to clear or destroy storage media, supervise the risks in the medium handling process, record the clearing or destruction process (including participants and handling methods), and check for residual information, and so on.
V. Main Technologies for Information System Termination
This article does not describe all the technologies involved in the termination process of information systems, but focuses on business migration, data backup, data destruction, and data encryption technology. Readers who wish to have a comprehensive understanding of other technologies can refer to other guidelines and general practices.
1. Business Migration
Business migration is not a simple physical relocation process, but a process of system and business reconstruction, including database migration, system migration, cloud service migration, and so on. For those objects that are not truly废弃 but need to be transferred, business migration technology is required, such as changing cloud service providers, and the data and business systems of the original cloud computing platform should be migrated to the new cloud computing platform. Migration technology includes application-based migration, volume management-based migration, and storage layer-based migration, and so on.
2. Data Backup
Data backup refers to copying the database structure, objects, and data to other storage media. In the event of operational errors or system failures that may cause data loss, backup of the data of objects to be transferred during the retirement and scrapping process should be performed as needed. After the retirement and scrapping process is completed, backup data should be securely cleared. Data backup technology includes full backup, incremental backup, and differential backup, and so on.
3. Data Destruction
Data destruction refers to the use of various technical means to ensure that the data stored in the medium is completely cleared, so that it cannot be recovered or transmitted externally. Data deletion and formatting cannot completely eliminate data, and data can be easily restored. Data destruction technology should be used to permanently delete data. Data destruction technology includes data overwriting, strong degaussing, incineration and high-temperature destruction, physical destruction, and chemical corrosion, and so on.
4. Data Encryption
Data is converted from plaintext to ciphertext through encryption algorithms and encryption keys, and then restored to plaintext through decryption algorithms and decryption keys, thereby improving the security and confidentiality of the data transmission process. If sensitive information needs to be migrated, data encryption technology should be used during data transmission. Data encryption technology includes full-disk encryption technology, driver-level technology, and so on.
Summary
When implementing the termination of an information system, enterprises/organizations should first clarify the boundaries and scope of the information system to be terminated, focus on the main forms and technologies of information system termination, standardize the implementation process, and ensure the smooth progress of information system termination activities and the security of information assets.
评论已关闭