Preface
In the article 'On the Establishment of Special Security Management Organizations for Operators of Key Information Infrastructure', the author introduces the establishment of special security management organizations for operators. Today, the author shares with readers how operators should revise and improve security management systems to meet the needs of the security protection work of key information infrastructure.
The necessity of revising and improving security management systems
Security management systems play a role of constraint and control in the protection of key information infrastructure. If the security system is not sound or cannot run through all links and stages of the protection of key information infrastructure, especially when 'old systems manage new technologies', there is a lack of dynamic and continuous management systems. In addition, the internal constraint mechanism is not perfect and the supervision and guidance are not in place, which may lead to the inability to identify and quickly solve cyber security risks and hidden dangers in time.

The saying 'three parts technology, seven parts management' is a common saying in the industry, which readers must not be unfamiliar with. However, in practice, we often see that a large amount of funds are invested in the procurement and development of cyber security products/systems, while the security management system is often ignored or the implementation is weak. A common phenomenon is that the attention to the security management system is far less than that to cyber security technology.
Security management systems guide, standardize, and constrain all kinds of cyber security activities. In our routine security operation practices, they are actually everywhere. For example: when conducting security vulnerability scanning, we usually need to avoid peak business hours; when business systems are launched or updated, it is usually necessary to conduct security tests in the test environment first, and then allow them to go online in the formal environment... This series of operational procedures are actually implemented based on the security management system, and then a series of operational procedures for cyber security activities are formed. It can be said that the implementation of a standardized cyber security activity must also be the process of executing the security management system. And the standardized implementation of cyber security activities can also eliminate and avoid potential security risks and non-compliance incidents as much as possible.
Therefore, carrying out the revision and improvement of security management systems and continuously maintaining their applicability is the cornerstone for operators to carry out the security protection work of key information infrastructure.
Outer requirements for revising and improving security management systems
At present, China's relevant policies, laws and regulations, and standards and specifications all put forward requirements for operators to carry out the revision and improvement of security management systems. As shown in the following table:
Legal regulations/standard specifications | Relevant provisions |
Cyber Security Law | Article 21The state implements the system of classified protection for cyber security. Network operators shall comply with the requirements of the system of classified protection for cyber security and fulfill the following security protection obligations to ensure that the network is free from interference, destruction, or unauthorized access, and to prevent the leakage or theft, or tampering of network data: (i) Formulating internal safety management systems and operational procedures, determining the cyber security person in charge, and implementing the responsibility for cyber security protection; |
The Law of the People's Republic of China on Cyberspace Security | Article 15 Institutions engaged in core cipher, common cipher scientific research, production, service, testing, equipment, use, and destruction (hereinafter collectively referred to as cipher work institutions) shall, in accordance with laws, administrative regulations, national regulations, and the requirements of core cipher and common cipher standards, establish and improve safety management systems, take strict confidentiality measures and confidentiality responsibility systems to ensure the security of core ciphers and common ciphers. |
The Law of the People's Republic of China on Data Security | Article 27When carrying out data processing activities, it shall be in accordance with the provisions of laws and regulations, establish and improve the full-process data security management system, organize data security education and training, take corresponding technical measures and other necessary measures to ensure data security. When carrying out data processing activities through the Internet and other information networks, the above-mentioned obligations for the protection of data security shall be fulfilled on the basis of the cyber security level protection system. |
Regulations on the Protection of Key Information Infrastructure Security | Article 13Operators shall establish and improve cyber security protection systems and responsibility systems, ensure the investment of human, financial, and material resources. The person in charge of the operator shall be fully responsible for the protection of key information infrastructure security, lead the work of key information infrastructure security protection and major cyber security incident disposal, and organize the research and resolution of major cyber security issues. Article 15 The specific responsibility for the protection of key information infrastructure security of the unit shall be undertaken by the special safety management organization, which shall perform the following duties: (i) Establishing and improving cyber security management and evaluation and assessment systems, drafting plans for the protection of key information infrastructure security; (ii) Organizing and promoting the construction of cyber security protection capabilities, carrying out cyber security monitoring, detection, and risk assessment; (iii) In accordance with the national and industry cyber security incident emergency response plans, formulating the emergency response plan of the unit, regularly conducting emergency drills, and dealing with cyber security incidents; (iv) Identifying key cyber security positions, organizing the assessment of cyber security work, and proposing suggestions for rewards and penalties; (v) Organizing cyber security education and training; (vi) Fulfilling the responsibilities for the protection of personal information and data security, and establishing and improving the system for the protection of personal information and data security; |
Regulations on Cyber Security Level Protection (Draft for Comments) | Article 6Network operators shall legally carry out network grading, filing, safety construction rectification, level assessment, and self-inspection, etc., adopt management and technical measures to ensure the security of network infrastructure, network operation, data, and information security, effectively respond to cyber security incidents, and prevent cyber criminal activities. Article 20Network operators shall perform the following safety protection obligations in accordance with the law to ensure the security of the network and information: (i) Determining the responsible person for the protection of cyber security level protection work, establishing a responsibility system for cyber security level protection work, and implementing the system of responsibility pursuit; (ii) Establishing safety management and technical protection systems, including systems for personnel management, education and training, system safety construction, and system safety operation and maintenance; |
The 'Basic Requirements for Network Security Level Protection of Information Security Technology' (GB/T 22239-2019) | Taking the third level of classified protection as an example 8. 1.6. 1 Security Policy Overall guidelines and security policies for network security work should be formulated, explaining the overall objectives, scope, principles, and security framework of the organization's security work. 8.1.6.2 Management System This requirement includes: a) Security management systems should be established for various management contents in security management activities; b) Operational procedures should be established for daily management operations performed by management personnel or operators; c) An integrated security management system should be formed consisting of security policies, management systems, operational procedures, record forms, etc. 8.1.6.3 Formulation and Publication This requirement includes: a) Special departments or personnel should be designated or authorized to be responsible for the formulation of security management systems; b) Security management systems should be issued through formal and effective means and controlled by version. 8.1.6.4 Review and Revision It should regularly demonstrate and approve the rationality and applicability of security management systems, and revise security management systems that are insufficient or require improvement. |
The 'Information Security Technology Requirements for the Security Protection of Key Information Infrastructure' (Draft for Review) | 6.2 Security Management System Operators shall: a) Establish a network security protection plan suitable for the organization, combine it with the security risk report of the key business chain, clarify the objectives, security policies, organizational structure, management systems, technical measures, and other contents of the security protection work of key information infrastructure, strengthen the resource guarantee of institutions, personnel, funds, equipment, engineering, etc., and support the security protection work of key information infrastructure. The network security protection plan should be documented and approved before being released to relevant personnel. The network security protection plan should be revised at least once a year or revised when there are major changes. Note 1: Security policies include but are not limited to: secure interconnection policies, security audit policies, identity management policies, intrusion prevention policies, data security protection policies, automated mechanism policies (configuration, vulnerabilities, patches, virus libraries, etc.), supply chain security management policies, and security operation and maintenance policies. Note 2: Management systems include but are not limited to: risk management systems, network security assessment and supervision and accountability systems, network security training and education systems, personnel management systems, business continuity management and disaster recovery backup systems, three-synchronous systems (synchronous planning, construction, and use of security measures), supply chain security management systems, etc. b) Establish or improve security policies and systems based on the security needs of key business chains, supply chains, etc., and adjust them in response to the changes in security risks and threats faced by key information infrastructure. |
Note 1: After the formal release of the 'Regulations on the Protection of Information Security Level Protection' (Draft for Comments) and the 'Information Security Technology Requirements for the Security Protection of Key Information Infrastructure' (Draft for Review), operators shall sort out relevant security management systems in accordance with the latest requirements.
Note 2: After the formal implementation of the 'Data Security Law of the People's Republic of China' and the 'Regulations on the Security Protection of Key Information Infrastructure', operators should revise relevant safety management systems in accordance with the law.
III. Main Work Requirements for the Revision of Safety Management Systems
When operators establish special safety management organizations, they should clarify their main work requirements. The main work requirements include:
(1) When revising safety management systems, operators should comply with the requirements of national policies, laws, regulations, and standards in their respective industries and fields, and meet the actual needs of protecting their key information infrastructure.
(2) When revising safety management systems, operators should follow the 'three synchronous' principle of 'synchronous planning, synchronous construction, and synchronous use', and synchronize the planning, preparation, and implementation of safety management systems.
(3) Operators should establish safety management systems for various management contents in safety management activities.
(4) Operators should establish operational procedures for daily management operations performed by management personnel or operators.
(5) Operators should form a comprehensive information security management system framework consisting of safety strategies, management systems, operational procedures, and record forms.
(6) Safety management systems should be revised at least once a year or revised in a timely manner when there are major changes.
(7) Operators should establish mechanisms for the revision, review, publication, implementation, inspection, and change of safety management systems.
(8) If network security service agencies participate in the revision of safety management systems, operators should sign confidentiality agreements with them.
IV. Safety Management System Framework
Operators should establish safety management systems for various management contents in safety management activities, standardize daily management operations performed by safety management personnel or operators, and establish standardized, normalized, and proceduralized operational procedures.
The safety strategy, safety management system, operational procedures, and record forms constitute a comprehensive safety management system framework. The framework of the safety management system is shown in the figure below:
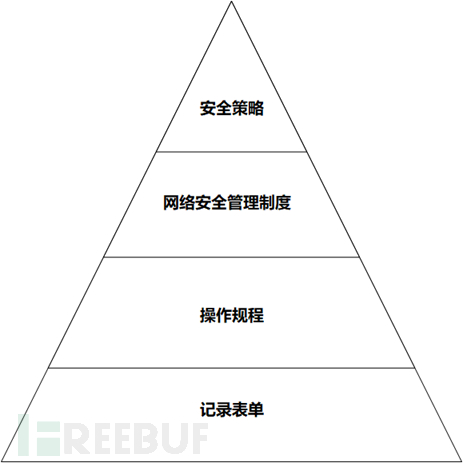
The safety management system framework is divided into four levels:
First level: Safety strategies. Clarifying the overall objectives, scope, principles, and safety framework of the operator's safety work.
Second level: Safety management systems. Establishing management systems for various contents of network security activities to constrain relevant network security behaviors.
Third level: Operational procedures. Establishing operational procedures through daily activities of safety management personnel or operators is a specific technical implementation detail for standardizing safety management systems.
Fourth level: Records, forms. Forms, operation records, and other documents that need to be recorded and filled out when implementing safety management systems and operational procedures.
V. Design of Safety Management System Framework Content
5.1 Composition of Safety Management System Framework Content
Operators should have a complete set of safety management systems to guide, standardize, and constrain relevant network security behavior activities for the protection of key information infrastructure.
The comprehensive safety management system for key information infrastructure consists of the safety management system of network security compliance and the content of safety management system framework of network security.
5.2 Sorting Methods for Safety Management System
Generally speaking, operators can start from the following eight dimensions to sort out the complete content of the safety management system, as shown in the table below:
Serial Number | Sorting Dimensions | Explanations of Safety Management System Content |
1 | Requirements of the Network Security Compliance System | Operators, based on the requirements of the network security compliance system and in combination with the actual situation of their units, should establish and improve a related safety management system, including safety strategies, safety management systems, operational procedures, and record forms. |
2 | Requirements of Policies and Laws and Regulations on the Protection of Key Information Infrastructure in Our Country | Operators, based on the requirements proposed by the relevant policies, laws and regulations related to the protection of key information infrastructure at the current stage of our country, and in combination with the actual situation of their units, should establish and improve relevant safety management systems. |
3 | Supervision and Management Requirements for the Protection of Key Information Infrastructure by Protection Work Departments | Operators, based on the supervision and management requirements for the protection of key information infrastructure proposed by the protection work departments of the industry and field in which they are located, and in combination with the actual situation of their units, should establish and improve relevant safety management systems. |
4 | Network security activities related to all stages and links of key information infrastructure protection | Operators, combining the planning and design, development and construction, operation and maintenance, and decommissioning and scrapping stages of key information infrastructure protection, as well as the various management contents and daily operations involved in the analysis and identification, security protection, detection and evaluation, monitoring and early warning, technical countermeasures, and event handling, should establish and improve corresponding safety management systems for various network security activities. |
5 | Risk Management of Key Information Infrastructure | According to the relevant requirements of the Regulations and the basic principle of 'dynamic protection oriented by risk management' for key information infrastructure, it is necessary to establish and improve relevant systems for network security risk management to guide, standardize, and constrain network security risk management activities. |
6 | Specific Application Scenarios | Based on the actual needs for protecting key information infrastructure in specific application scenarios such as cloud computing, big data, industrial control, Internet of Things, mobile internet, etc., combined with relevant policies, laws and regulations, and standards and specifications, it is necessary to establish and improve safety management systems. |
7 | Special Safety Management Needs | To guide, standardize, and constrain a certain type of special network security activities, it is necessary to establish and improve relevant safety management systems. |
8 | Others | To guide, standardize, and constrain other network security activities, it is necessary to establish and improve relevant safety management systems. |
It should be noted that when operators refer to the above eight dimensions to formulate or improve the content of safety management systems, there may be phenomena of repetition. Operators can remove and screen the relevant safety management systems accordingly.
5.3 Safety Management System Enumeration
The author, based on the relevant policies, laws and regulations, and standards and specifications related to the protection of key information infrastructure in our country, combined with practice, has sorted out the safety management systems that operators should possess. Operators can refer to the table below, combined with the actual situation of their units, to sort out the safety management systems.
Serial Number | Regulation Name | Main Content | Complementary Documents |
1. | Cybersecurity Management Charter | Provisions on cybersecurity strategy, policies, overall objectives, and security framework | Relevant systems, operation procedures, and record forms |
2. | Cybersecurity Protection Plan | Description of the objectives, security strategies, organizational structure, management systems, technical measures, implementation specifications, and resource support for cybersecurity protection work of key information infrastructure | Relevant systems, operation procedures, and record forms |
3. | Cybersecurity Management Measures | Overall requirements for cybersecurity management | Relevant systems, operation procedures, and record forms |
4. | Document Management Norms | Normative specifications for the formulation, revision, review, publication, inspection, and abandonment of safety management systems (including security strategies, management systems, operation procedures, record forms, etc.) | Relevant systems, operation procedures, and record forms |
5. | Regulations on Document Review | Description of review requirements, methods, and contents for various activities such as requirements, plans, budgets, systems, etc. | Related record forms of review templates |
6. | Implementation Norms for Compliance | Normative requirements for the design, construction, operation, assessment, and continuous improvement of cybersecurity compliance systems | Relevant systems, operation procedures, and record forms |
7. | Cybersecurity Risk Management Plan | Description of the content, priority, schedule, protective measures, and explanation of the degree of gap reduction or improvement of the cybersecurity risk management plan | Relevant systems, operation procedures, and record forms |
8. | Methods for Establishing Security Management Organizations | Description of how to organize security management organizations and key responsibilities and obligations | Authorization documents, work records, and related record forms |
9. | Management Regulations for Security Personnel | Provisions on the recruitment, review, screening, training and education, off-duty and departure, and responsibility separation of security personnel | Related systems, record and form |
10. | Management Measures for the Whole Life Cycle Security of Key Information Infrastructure | Provisions on the work requirements, main contents, work processes, methods, change control, and risk avoidance at each stage of the planning, retirement, operation and maintenance, retirement and abandonment, and inspection and evaluation of key information infrastructure | Relevant systems, operation procedures, and record forms |
11. | Guidelines for the Identification and Certification of Key Information Infrastructure | Provisions on the requirements, methods, steps, procedures, review, information registration, and reporting for the identification of key information infrastructure in this unit | Relevant systems, operation procedures, and record forms |
12. | Guidelines for the Protection and Inspection and Evaluation of Key Information Infrastructure | Detailed guidance on the requirements, forms, content, rectification, and precautions for the protection and inspection and evaluation of key information infrastructure in this unit | Relevant systems, operation procedures, and record forms |
13. | Regulations on Risk Management of Key Information Infrastructure | Provisions on the risk identification, risk analysis, risk monitoring, and risk transfer methods of key information infrastructure in terms of risk management | Relevant systems, operation procedures, and record forms |
14. | Security Protection Requirements and Control Measures for Key Information Infrastructure | Provisions on the basic requirements, protection strategies, and measures for the security protection of key information infrastructure | Relevant systems, operation procedures, and record forms |
15. | Cybersecurity Monitoring Guidelines | Provisions on cybersecurity monitoring requirements, implementation standards, measures, information review, reporting, and notification, etc. | Relevant systems, operation procedures, and record forms |
16. | Cybersecurity Early Warning Guidelines | Provisions on the description of early warning levels, early warning publication, response and disposal, upgrade and downgrade, and dissolution, etc. | Relevant systems, operation procedures, and record forms |
17. | Regulations on Information Notification, Sharing and Publication | Regulations on the content norms, release process, approval, filing, and precautions for the release of cybersecurity threat information | Relevant systems, operation procedures, and record forms |
18. | Data Classification and Grading Guidelines | Specific description of how to carry out data classification and grading, and provide detailed classification and grading guidelines | Relevant operation procedures and record forms |
19. | Cybersecurity Incident Classification and Grading Guidelines | Content on the classification of cybersecurity incidents, the method of incident grading, and the basis for grading determination | Related systems, record and form |
20. | Business Continuity Management Measures | Content on the stable duration requirements for the continuity of key business, the recovery and remediation time for the destroyed, and the support measures for business continuity | Relevant systems, operation procedures, and record forms |
21. | Cybersecurity Incident Disposal Management Measures | Regulations on the disposal procedures, methods, requirements, reporting/announcement, and summary for different types of cybersecurity incidents | Relevant systems, operation procedures, and record forms |
22. | Cybersecurity Emergency Response Management Measures | Regulations on the requirements, procedures, methods, tools, resources, coordination, reporting/announcement, and summary for cybersecurity emergency response in emergency conditions | Relevant systems, operation procedures, and record forms |
23. | Cybersecurity Emergency Response Plan Management Measures | Regulations on the norms for cybersecurity emergency response, including the classification and grading of cybersecurity incidents and early warning information, organizational structures and responsibilities, monitoring and early warning, emergency response, investigation and evaluation, preventive work, and guarantee measures | Relevant systems, operation procedures, and record forms |
24. | Cybersecurity Emergency Drills Management Measures | Regulations on the purposes, principles, forms, planning, participating departments and responsibilities, implementation process norms, summary, approval, reporting, and guarantee measures for emergency drills | Relevant systems, operation procedures, and record forms |
25. | Personal Information Protection and Important Data出境 Assessment Security Management System | Regulations on the specific types of personal information protected, protection measures, scope of use, types of important data出境, assessment scope, types of reported assessments, assessment requirements,出境changes, and reward and punishment measures | Relevant systems, operation procedures, and record forms |
26. | Management Measures for the Security Inspection of On-line and Off-line Important Information Systems | Regulations on the security inspection requirements, work processes, rectification of vulnerabilities/baselines, reporting, and approval for the on-line and off-line security of important information systems | Relevant systems, operation procedures, and record forms |
27. | Cybersecurity Change Management Measures | Regulations on the situations, requirements, control measures, approval, and precautions for cybersecurity changes | Relevant systems, operation procedures, and record forms |
28. | Management Measures for External Personnel Access | Regulations on the relevant matters for external personnel visiting | Related records and forms |
29. | External Access Security Management Measures | Content on the security requirements, approval, and precautions for external personnel to access | Related records and forms |
30. | Cybersecurity Matters Approval Management Measures | Regulations on various cybersecurity activities that require approval, approval procedures, and the approval of approval activities | Relevant operation procedures and record forms |
31. | Cybersecurity Matters Reporting Management Measures | Regulations on the types of cybersecurity matters to be reported, approval procedures, approvers, management闭环, and other aspects | Relevant systems, operation procedures, and record forms |
32. | Cybersecurity Communication and Cooperation Control Management Measures | Regulations on the forms, contents, requirements, mechanisms, and precautions for various forms of cybersecurity communication and cooperation | Relevant systems, operation procedures, and record forms |
33. | Cybersecurity Inspection and Evaluation Management Measures | Regulations on the forms of various inspections and evaluations, matters of cooperation for internal/external security inspections, inspection and evaluation content, summary, and notification | Relevant systems, operation procedures, and record forms |
34. | Network security confidentiality system | Regulations on the requirements, forms, and content of network security confidentiality | Related records and forms |
35. | Management system for network security training | Regulations on the forms, content, objects, and requirements of network security training | Related records and forms |
36. | Management regulations for network security rewards and punishments | Regulations on the requirements, forms, content, and applicable situations of network security rewards and punishments | Related records and forms |
37. | Implementation and assessment methods for the implementation of the responsibility system for network security work | Regulations on the specific assessment requirements, indicators, and reward and punishment measures for the implementation of job responsibilities and obligations of network security personnel | Related records and forms |
38. | Management regulations for the supply chain of network security products and services | Content on supply chain management requirements, possible risks, and protective measures | Relevant systems, operation procedures, and record forms |
39. | Management regulations for the classification and filing of network security level protection | Regulations on the methods, processes, and changes of the classification and filing of key information infrastructure level protection | Relevant systems, operation procedures, and record forms |
40. | Management regulations for the construction of network security level protection | Regulations on the design, construction, and implementation of network security level protection | Relevant systems, operation procedures, and record forms |
41. | Management regulations for network security level protection assessment | Regulations on the requirements, applicable situations, coordination matters, and rectification of network security level protection assessment | Relevant systems, operation procedures, and record forms |
42. | Management regulations for the procurement of network products and services | Regulations on the procurement forms, requirements, processes, and review of network products and services | Relevant operation procedures and record forms |
43. | Management system for software safe development | Regulations on the control methods of self-developed or outsourced software development, personnel behavior standards, software design guidelines, version control, monitoring, detection, and review, etc., including supporting systems such as code writing safety specifications and software design and use guidelines | Relevant systems, operation procedures, and record forms |
44. | Management regulations for engineering acceptance and delivery | Regulations on the requirements, acceptance tests, and delivery list for engineering acceptance and delivery | Relevant systems, operation procedures, and record forms |
45. | Management regulations for network security service organizations | Regulations on the selection of network security service organizations, service forms and contents, service requirements, service review, change, reward and punishment measures, and legal liability | Relevant systems, operation procedures, and record forms |
46. | Machine room safety management system | Regulations on the management of the entry and exit of the machine room, the special person responsible for the machine room, machine room maintenance, and precautions | Relevant systems, operation procedures, and record forms |
47. | Asset management system | Regulations on the sorting, registration, maintenance, change, identification management, information classification and identification methods, and the use, transmission, and storage of information | Relevant systems, operation procedures, and record forms |
48. | Medium management system | Regulations on the maintenance or destruction process of the medium, control of personnel selection, packaging, delivery, and other aspects during the physical transmission process of the medium, the use process of the medium, dispatch for maintenance, encryption and monitoring management when taken out of the working environment, and the classification and identification of the medium | Relevant systems, operation procedures, and record forms |
49. | Regulations for the safe operation and maintenance management | Regulations on the requirements, processes, content, approval, change, overseas operation and maintenance, and other aspects of the operation and maintenance of key information infrastructure | Relevant systems, operation procedures, and record forms |
50. | Security vulnerability management regulations | Describe the requirements, processes, and precautions for the detection, repair, avoidance, exceptions, and publication of security vulnerabilities | Relevant operation procedures and record forms |
51. | Malicious code prevention management regulations | Describe the provisions on the types, prevention requirements, prevention measures, and precautions of malicious code | Relevant systems, operation procedures, and record forms |
52. | Security audit management system | Describe the requirements, forms, specifications, content, and precautions of internal security audits, as well as the types, coordination matters, content, and precautions of external audits | Relevant systems, operation procedures, and record forms |
53. | Password management regulations | Describe the provisions on the scenarios, requirements, selection of password technologies and products, and changes of password usage | Relevant systems, operation procedures, and record forms |
54. | Backup and recovery management system | Describe the provisions on the types of backup data, backup methods, selection of backup technologies and products, backup frequency, backup cycle, recovery strategy, recovery program, and recovery requirements | Relevant systems, operation procedures, and record forms |
55. | Network security baseline configuration specifications | Describe the baseline requirements for security configurations of network devices, security devices, hosts, databases, operating systems, and application systems | Relevant systems, operation procedures, and record forms |
56. | Management regulations/specifications for the division of security domains | Describe the division levels, methods, and principles of security domain division | Relevant systems, operation procedures, and record forms |
57. | Management regulations for the retention of network security-related logs | Describe the provisions on the types, retention time, storage methods, technical support means, and precautions of network security-related logs | Relevant systems, operation procedures, and record forms |
58. | Knowledge base management regulations | Describe the provisions on the construction, use, maintenance, update, and authorization scope of the knowledge base | Relevant systems, operation procedures, and record forms |
59. | ... ... | ... ... | ... ... |
Note 1: The name of the system is not fixed. When operators sort out safety management systems by referring to this table, they should judge whether it is necessary to formulate or revise this safety management system and its supporting operation procedures, record forms, etc. based on the main content of this document;
Note 2: The safety management systems listed in this table may not necessarily cover all network security activities of an operator or meet all actual needs. Operators may make additions, deletions, and modifications based on the actual situation of their units, focusing on the eight dimensions of the safety management system system content proposed in this chapter, and sort out the safety management systems (sets) that need to be established in combination with the actual situation of their units.
Management of the safety management system system
The operator shall design work procedures or mechanisms for the formulation, revision, review, publication, implementation, inspection, and abandonment of safety management systems to guide and standardize the management of safety management systems.
The operator shall specify or authorize a special department or personnel to be responsible for the formulation and revision of safety management systems, and design clear review and revision procedures to maintain the safety management systems; publish them through formal and effective means, and carry out version control; at the same time, ensure the implementation and enforcement of safety management systems through certain institutionalized methods, and regularly inspect the implementation and content compliance of safety management systems.
Generally speaking, the management procedures of a complete safety management system are shown in the figure below.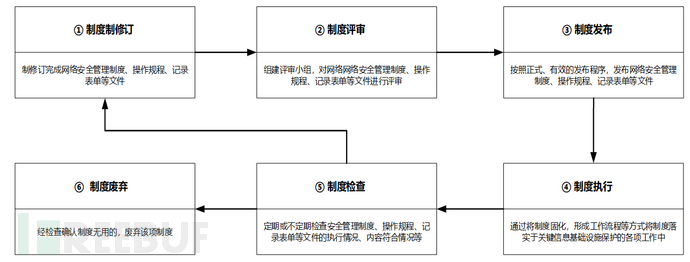
6.1 Revision of Safety Management System
The operator should designate or authorize a special department or personnel responsible for revising the safety management system and carry out version control. Each safety management system should have a corresponding responsible person responsible for maintenance.
The operator should design clear procedures or mechanisms for revising the safety management system. Among them:
(1) For new information infrastructure that has not yet established a safety management system, the operator should organize special resources, concentrate on formulating a batch of safety management systems, operation procedures, record forms, etc. that can约束 related network security activities of the key information infrastructure protection;
(2) For existing systems related to the protection of key information infrastructure, the operator should regularly or according to actual needs, examine whether there are any outdated or lacking in constraints on certain types of network security behaviors, operation procedures, etc., and according to the examination situation, invest the resources that correspond to the revision work, and carry out the revision of the safety management system;
(3) For the safety management system documents that need to be revised after the review, the operator should clearly specify the personnel to complete within the deadline; the review and revision of confidential information security strategies, regulations and relevant operational procedures documents should be carried out within the corresponding scope. If necessary, the secretariat for confidential management can participate in the revision of the documents, and it is necessary to seek the opinions of relevant national departments.
(4) After the revision of the safety management system is completed, record the network security responsible person and carry out version control.
(5) When revising the safety management system, the content should be clear, terms should be standardized, words should be accurate, and expressions should be concise. The safety management system should have strong operability, unity, stability, and timeliness, covering all aspects of the protection of the key information infrastructure.
The name of the safety management system is generally prefixed with the name of the operator's unit or the name of the key information infrastructure, ending with 'methods', 'articles', 'regulations', 'norms', 'requirements', 'guidelines', 'system', etc. For example: 'XXX System Safety Management Methods', 'XXX Network Security Management Articles', 'XXX System Online Security Inspection Regulations', 'XXX Host Security Baseline Configuration Norms', 'XXX Network Security Early Warning Guidelines', 'XXX External Personnel Access Management System', etc.
The operator should at least revise the safety management system of the key information infrastructure once a year or revise it when there is a major change.
6.2 Review of Safety Management System
After the revision of the safety management system is completed, the operator should organize a special safety management organization, business and using departments, experts, and others to jointly review the safety protection plan, do a good job of review records, and modify the safety management system according to the review opinions, and retain the revision records of the version. It is necessary to review the revision plan again if necessary.
The operator should record the review process of the safety management system in the form of documents for archiving, as evidence of the review results.
The review content of the safety management system generally includes:
(1) Review whether there are defects in the safety management system;
(2) Review the rationality, applicability, suitability, and effectiveness of the safety management system;
(3) Review whether all network security activities related to the protection of key information infrastructure are covered and whether each network security activity has a guiding, standardizing, and restrictive effect;
(4) Review the records of the revised versions of the safety management system.
The operator shall establish a clear review procedure to carry out programmed and periodic reviews of the effectiveness of the safety management system, and retain necessary review records and evidence.
6.3 Release of Safety Management System
The operator shall design a clear release procedure. The safety management system should be released after review and approval through formal and effective means. When releasing, the scope of release should be noted and there should be a record of receiving and sending documents.
The operator shall design an archiving mechanism for the safety management system. After the safety management system is released, a designated person should be responsible for keeping it; borrowing regulations should be formulated, the borrowing scope should be limited, and approval and registration by the corresponding level of responsible person should be obtained.
6.4 Implementation of Safety Management System
The operator shall establish clear procedures or mechanisms to ensure that the safety management system is implemented in all aspects of the protection of key information infrastructure. For example, the work process stipulated by the safety management system can be solidified into an electronic process, or operational procedures can be established in network security activities to constrain related network security activities.
6.5 Checking of Safety Management System
The operator shall establish a checking procedure or mechanism for the safety management system. After the safety management system is released and implemented, it should be checked regularly or irregularly on the implementation of the safety management system, the rationality and applicability of the content of the safety management system.
(1) For the implementation of the safety management system, relevant approval process records, forms, and other procedural archived documents should be checked. For the implementation of the safety management system that is not forceful or does not meet the requirements of the safety management system, improvement opinions should be proposed and deadlines for improvement set, and a safety inspection report should be formed and reported.
(2) For the content of the safety management system that is unreasonable or not timely, it is necessary to revise the existing deficiencies or the safety management system that needs improvement. For the useless or outdated safety management system, it should be abandoned.
The operator shall keep records and archive the results of the safety management system inspection.
6.6 Abandonment of Safety Management System
The operator shall design the disposal procedure for the safety management system. If, after review or inspection, it is considered that the safety management system is useless or outdated, the operator may initiate the disposal procedure and abandon the system.
The operator shall keep records and archive the results of the disposal process.
Summary
The author, based on the relevant policies, laws, regulations, and standards and specifications for the protection of key information infrastructure in our country, combined with practice, elaborates on the main work requirements, system framework, content design, and management process of the safety management system. This article only represents the author's own thoughts and does not necessarily mature or meet the actual needs of any operator. Any shortcomings, please correct them.
评论已关闭