Introduction
The author believes that, whether it is the operator of key information infrastructure (hereinafter referred to as the operator) or other network operators, the human factor is crucial in the process of cyber security assurance. In the practice of secure operation, it is generally believed that the integration and continuous improvement of people, tools, and processes are essential to carry out secure operation work. Today, combining the relevant policies, laws and regulations of China's key information infrastructure protection, the requirements of the national standard specifications to be released in the future, and the ITIL practice, as well as the practice of operators in the construction, operation, and security assurance of cyber security, the author discusses how operators can establish special security management organizations to implement the main responsibility for cyber security and promote the security protection work of various key information infrastructure projects.
First, the positioning of the special security management organization
According to the relevant laws and regulations of our country, as the main body of key information infrastructure protection, operators are responsible for the operation and management of key information infrastructure, fulfill the obligations of network security protection, and accept the supervision and management of the national Internet information office, the Ministry of Public Security of the State Council, and the competent departments and supervision and management departments of industries and fields (hereinafter referred to as the protection work departments).

As an entity, the key information infrastructure protection work of operators needs to be designated by the internal departments or teams to implement. The special security management organization is the main entity department within the operator responsible for the protection of the unit's key information infrastructure, and is responsible for fulfilling the responsibilities and obligations of key information infrastructure protection.
Second, the responsibilities and obligations of operators
Before discussing how operators should establish a special security management organization, readers need to first understand what responsibilities and obligations should be included in the protection of key information infrastructure carried out by operators.
When operators carry out the protection of key information infrastructure, in addition to meeting the actual needs and inherent requirements of their units, they must also comply with the policies, laws and regulations, and standard specifications on the protection of key information infrastructure proposed by our country and the industries and fields to which they belong at this stage.
The inherent requirements of various operators vary, and the author will not enumerate them. In addition, due to the wide distribution of key information infrastructure across industries and fields, the author will only list the responsibilities and obligations proposed by the state for operators as follows:
Laws and regulations/standard specifications | Relevant provisions |
Network Security Law | Article 21The state implements a network security level protection system. Network operators shall fulfill the following security protection obligations in accordance with the requirements of the network security level protection system to ensure that the network is not interfered with, damaged, or accessed without authorization, and to prevent the leakage or theft, and tampering of network data: (I) Formulate internal security management systems and operational procedures, determine the network security person in charge, and implement the responsibility for network security protection; (II) Adopt technical measures to prevent computer viruses, network attacks, and other behaviors that危害网络安全 that harm network security; (III) Adopt technical measures for monitoring, recording the status of network operations, and network security incidents, and retain relevant network logs for at least six months in accordance with regulations; (IV) Adopt measures such as data classification, important data backup, and encryption; (V) Other obligations stipulated by laws and administrative regulations. Article 25 Network operators shall formulate emergency plans for network security incidents, promptly handle system vulnerabilities, computer viruses, network attacks, and other security risks; when a network security incident occurs, immediately activate the emergency plan, take corresponding remedial measures, and report to the relevant competent authorities in accordance with regulations. 第二十八条Article 28 Network operators shall provide technical support and assistance to public security organs and national security organs for the lawful maintenance of national security and the investigation of crimes.Article 34 In addition to the provisions of Article 21 of this Law, operators of key information infrastructure shall also fulfill the following security protection obligations: (1) Set up special security management institutions and responsible persons for security management, and conduct security background checks on such responsible persons and personnel in key positions; (2) Conduct regular network security education, technical training, and skill assessment for personnel; (3) Carry out disaster recovery backup for important systems and databases; (4) Formulate emergency plans for network security incidents and conduct drills regularly; (5) Other obligations stipulated by laws and administrative regulations.If the purchase of network products and services by the operators of key information infrastructure may affect national security, they shall go through the national security review organized by the National Internet Information Office together with relevant departments of the State Council. Article 36When purchasing network products and services, operators of key information infrastructure shall enter into security and confidentiality agreements with providers in accordance with regulations, clearly defining security and confidentiality obligations and responsibilities. Article 37Personal information and important data collected and generated by the operators of key information infrastructure within the territory of the People's Republic of China shall be stored within the territory. If it is necessary to provide it to overseas due to business needs, it shall be subject to a security assessment in accordance with the methods formulated by the National Internet Information Office together with relevant departments of the State Council; if there are other provisions of laws and administrative regulations, they shall be implemented accordingly. Article 38Operators of key information infrastructure shall conduct self-inspection or entrust network security service institutions to conduct annual security and risk assessment of their networks at least once, and report the situation of inspection and assessment and improvement measures to relevant departments responsible for the security protection of key information infrastructure. Article 40Network operators shall strictly keep the collected user information confidential and establish and improve the user information protection system. Article 41Network operators collecting and using personal information shall follow the principles of legality, legitimacy, and necessity, publicly disclose collection and use rules, explicitly state the purposes, methods, and scope of collection and use of information, and obtain the consent of the collectors. Network operators shall not collect personal information unrelated to the services they provide, shall not collect, use personal information in violation of the provisions of laws and administrative regulations or agreements between both parties, and shall process the personal information they save in accordance with the provisions of laws and administrative regulations and agreements with users. Article 42Network operators shall not disclose, alter, or damage the personal information they collect; without the consent of the collectors, they shall not provide personal information to others. However, exceptions are made for information that cannot be identified as specific individuals after processing and cannot be restored. Network operators shall take technical measures and other necessary measures to ensure the security of the personal information they collect, prevent information leakage, damage, or loss. In the event of or the possibility of personal information leakage, damage, or loss, immediate remedial measures shall be taken, and users shall be informed in accordance with regulations, and relevant competent departments shall be reported to. Article 47Network operators shall strengthen the management of information published by their users. Where information prohibited from being published or transmitted by laws and administrative regulations is found, the transmission of such information shall be immediately stopped, and disposal measures such as elimination shall be taken to prevent the spread of information, save relevant records, and report to relevant competent departments. Article 49Network operators shall establish a system for receiving complaints and reports on network information security, publish information such as complaint and report methods, and promptly receive and handle complaints and reports related to network information security. Network operators shall cooperate with the cybersecurity department and other relevant departments in the legal supervision and inspection they carry out. Article 55In the event of a cybersecurity incident, the emergency plan for cybersecurity incidents shall be immediately initiated to investigate and evaluate the cybersecurity incident, require network operators to take technical measures and other necessary measures to eliminate potential hazards, prevent the expansion of harm, and timely release public warnings related to the public. Article 56When the departments of the people's governments at or above the provincial level find that there are significant security risks in the network or that security incidents have occurred during the performance of their cybersecurity supervision and management duties, they may, in accordance with the prescribed authorities and procedures, engage in talks with the legal representatives or major responsible persons of the operators of the network. Network operators shall take the required measures, carry out rectification, and eliminate risks. |
The Cryptography Law of the People's Republic of China | Article 14National secrets information transmitted in wired and wireless communications, as well as information systems for storing and processing national secrets information, shall be encrypted and protected and undergo secure authentication using core passwords and common passwords in accordance with laws, administrative regulations, and relevant national provisions. Article 27For key information infrastructure that requires the use of commercial cryptography for protection according to laws, administrative regulations, and relevant national provisions, the operators shall use commercial cryptography for protection and conduct self-assessment or entrust commercial cryptography testing institutions to carry out safety assessments of commercial cryptography applications. The safety assessment of commercial cryptography applications shall be connected with the safety detection and evaluation of key information infrastructure and the cybersecurity level assessment system to avoid repeated assessment and evaluation. Where the acquisition of network products and services involving commercial cryptography by the operators of key information infrastructure may affect national security, it shall be subject to national security review organized by the national Internet information department in conjunction with the national cryptography management department and other relevant departments in accordance with the provisions of the Cybersecurity Law of the People's Republic of China. |
The Data Security Law of the People's Republic of China | Article 27: The conduct of data processing activities shall be in accordance with the provisions of laws and regulations, establish and improve the full-process data security management system, organize data security training and education, adopt corresponding technical measures and other necessary measures to ensure data security. Data processing activities carried out through the Internet and other information networks shall fulfill the above obligations for data security protection on the basis of the cybersecurity level protection system. The processors of important data shall clearly define the person in charge of data security and the management organization, and implement the responsibility for data security protection. Article 30 The processors of important data shall regularly carry out risk assessments of their data processing activities in accordance with the regulations and submit risk assessment reports to the relevant competent departments. The risk assessment report shall include the types and quantities of important data processed, the situation of data processing activities, the data security risks faced and their countermeasures, etc. Article 31 The security management of the export of important data collected and generated during the operation of key information infrastructure within the territory of the People's Republic of China shall apply the provisions of the Cybersecurity Law of the People's Republic of China; the security management measures for the export of important data collected and generated during the operation within the territory of the People's Republic of China by other data processors shall be formulated by the national cyber information department in conjunction with relevant ministries and departments of the State Council. |
Personal Information Protection Law of the People's Republic of China | Article 40 The operators of key information infrastructure and personal information processors who process personal information in accordance with the number specified by the national cyber information department shall store the personal information collected and generated within the territory of the People's Republic of China. If it is necessary to provide it overseas, it shall go through a security assessment organized by the national cyber information department; if it is stipulated by laws, administrative regulations, and the national cyber information department that a security assessment does not need to be conducted, it shall follow the relevant provisions. |
Regulations on the Security Protection of Key Information Infrastructure | Article 4 The security protection of key information infrastructure adheres to comprehensive coordination, division of responsibility, legal protection, strengthens and implements the main responsibility of the operator of key information infrastructure (hereinafter referred to as the operator), gives full play to the role of the government and all sectors of society, and jointly protect the security of key information infrastructure. Article 6 In accordance with the provisions of these regulations, relevant laws, administrative regulations, and mandatory requirements of national standards, the operator shall, on the basis of network security level protection, adopt technical protection measures and other necessary measures to respond to network security incidents, prevent network attacks and illegal and criminal activities, ensure the safe and stable operation of key information infrastructure, and maintain the integrity, confidentiality, and availability of data. Article 11 If there are significant changes in the key information infrastructure that may affect the identification results, the operator shall promptly report the relevant circumstances to the protection work department. The protection work department shall complete the re-identification within 3 months from the date of receiving the report, notify the operator of the identification results, and inform the Ministry of Public Security of the State Council. Article 12Security protection measures shall be planned, constructed, and used in sync with the key information infrastructure. Article 13The operator shall establish and improve the network security protection system and responsibility system, and ensure the investment of human, financial, and material resources. The main person in charge of the operator is responsible for the overall security protection of key information infrastructure, leading the work of security protection and major network security incidents, and organizing the study and resolution of major network security issues. Article 14 The operator shall establish a special security management institution and conduct security background checks on the responsible persons of the special security management institution and key position personnel. During the review, the public security organs and national security organs shall provide assistance. Article 15: The specific security management institutions of the unit are responsible for the security protection of key information infrastructure within the unit, and shall perform the following duties: (One) Establish and improve network security management, evaluation and assessment systems, and formulate security protection plans for key information infrastructure. (Two) Organize and promote the construction of network security protection capabilities, carry out network security monitoring, detection, and risk assessment; (Three) Develop emergency plans for the unit in accordance with national and industry network security incident emergency response plans, regularly carry out emergency drills, and deal with network security incidents; (Four) Identify key positions in network security, organize and carry out network security work assessment, and put forward suggestions for rewards and penalties; (Five) Organize network security education and training; (Six) Fulfill personal information and data security protection responsibilities, establish and improve personal information and data security protection systems; (Seven) Implement security management for services such as design, construction, operation, and maintenance of key information infrastructure; (Eight) Report network security incidents and important matters in accordance with regulations. Article 16: Operators shall ensure the operation expenses of special security management institutions, equip them with corresponding personnel, and involve personnel from special security management institutions in decisions related to network security and informationization. Article 17: Operators shall carry out network security detection and risk assessment at least once a year on key information infrastructure by themselves or by entrusting network security service institutions, promptly rectify any security issues found, and report the situation in accordance with the requirements of the protection work department. Article 18: When a major network security incident occurs or a major network security threat is discovered, the operator shall report to the protection work department and public security organs in accordance with relevant regulations. When there is a major network security incident such as the overall interruption of operation or major functional failure of key information infrastructure, leakage of national basic information and other important data, large-scale personal information leakage, significant economic losses, and the large-scale spread of illegal information, or when a major network security threat is discovered, the protection work department shall report to the national cyber information department and the Ministry of Public Security of the State Council in a timely manner after receiving the report. Article 19: Operators shall prioritize the procurement of secure and reliable network products and services; for network products and services that may affect national security, safety review shall be conducted in accordance with national network security regulations. Article 20: When purchasing network products and services, operators shall enter into security confidentiality agreements with providers in accordance with national regulations, clarify the technical support, security confidentiality obligations, and responsibilities of the providers, and supervise the performance of obligations and responsibilities. Article 21: If an operator undergoes mergers, divisions, dissolution, and other situations, it shall report to the protection work department in a timely manner and dispose of key information infrastructure in accordance with the requirements of the protection work department to ensure safety. |
Regulations for Network Security Level Protection (Draft for Comments) | Article 6Network operators shall carry out activities such as network level classification and filing, safety construction rectification, level assessment, and self-inspection in accordance with the law, adopt management and technical measures to ensure the safety of network infrastructure, network operation, data, and information security, effectively respond to network security incidents, and prevent network criminal activities. Article 20Network operators shall legally fulfill the following cybersecurity protection obligations to ensure network and information security: (One) Determine the person responsible for cybersecurity level protection work, establish a responsibility system for cybersecurity level protection work, and implement the system of responsibility pursuit; (Two) Establish security management and technical protection systems, establish systems for personnel management, education and training, system security construction, and system security operation and maintenance; (Three) Implement systems for facility security management, equipment and medium security management, and network security management, and formulate operational specifications and work procedures; (Four) Implement management and technical measures for identity recognition, prevention of malicious code infection and spread, and prevention of network intrusion attacks; (Five) Implement management and technical measures for monitoring, recording network operation status, cybersecurity incidents, and illegal activities, and retain relevant network logs that can be traced back to network illegal activities for more than six months as prescribed; (Six) Implement measures for data classification, important data backup, and encryption; (Seven) Legally collect, use, and process personal information, and implement personal information protection measures to prevent the leakage, damage, tampering, theft, loss, and abuse of personal information; (Eight) Implement measures for the discovery, blocking, and elimination of illegal information, and implement measures to prevent the large-scale spread of illegal information and the loss of evidence of illegal activities; (Nine) Implement the responsibilities of network connection registration and user real-name verification, etc; (Ten) For incidents occurring in the network, a report shall be submitted to the local public security organs within 24 hours; for the disclosure of state secrets, a report shall also be submitted to the local administrative department in charge of secrecy protection at the same time. (Eleven) Other cybersecurity protection obligations stipulated by laws and administrative regulations. Article 21In addition to fulfilling the cybersecurity protection obligations stipulated in Article 20 of these Regulations, operators of networks at the third level and above shall also fulfill the following cybersecurity protection obligations: (One) Determine the cybersecurity management organization, clarify the responsibilities of cybersecurity level protection, and establish a hierarchical approval system for matters such as network changes, network access, operation and maintenance, and technical support unit changes; (Two) Formulate and implement a comprehensive cybersecurity plan and overall security protection strategy, formulate a safety construction plan, and have it reviewed and approved by professional technical personnel; (Three) Conduct security background checks for cybersecurity management personnel and key position personnel, and implement the system of certified employment; (Four) Conduct security management for institutions and personnel that provide network design, construction, operation and maintenance, and technical services; (Five) Implement cybersecurity situation awareness monitoring and early warning measures, build a cybersecurity protection management platform, conduct dynamic monitoring and analysis of network operation status, network traffic, user behavior, and cybersecurity incidents, and connect with同级 public security organs; (Six) Implement redundancy, backup, and recovery measures for important network equipment, communication links, and systems; (Seven) Establish a cybersecurity level assessment system, carry out level assessments regularly, and report the assessment results and safety rectification measures, as well as the rectification results, to public security organs and relevant departments; (Eight) Other cybersecurity protection obligations stipulated by laws and administrative regulations. Article 50Above-county-level public security organs shall supervise and inspect the following situations of network security work carried out by network operators: (I) Daily network security prevention work; (II) Rectification of major network security risk隐患; (III) Emergency response and recovery work for major network security incidents; (IV) Implementation of network security protection work for major activities; (V) Other situations of network security protection work. Public security organs shall carry out at least one security check annually on network operators of the third level and above. Where relevant industries are involved, security checks may be conducted together with the competent industry departments. Where necessary, public security organs may entrust social forces to provide technical support. Network operators shall assist and cooperate, and provide relevant data and information as required by public security organs. Article 55Public security organs shall deal with network security incidents in accordance with relevant regulations, carry out incident investigations, determine the responsibilities of the incidents, and investigate and deal with criminal activities that危害 network security. Where necessary, network operators may be ordered to take emergency measures such as blocking information transmission, suspending network operations, and backing up relevant data. Network operators shall cooperate and support public security organs and other departments in investigating and dealing with incidents. Article 61Network operators and technical support units shall provide support and assistance to public security organs and national security organs for the law enforcement activities of maintaining national security and investigating crimes. |
Basic Requirements for Network Security Level Protection of Information Security Technology (GB/T 22239-2019) | Taking the level protection level three as an example 8.1.7 Security Management Organization 8.1.7.1 Position Setting This requirement includes: a) A committee or leading group for guiding and managing network security work should be established, with the highest leader appointed or authorized by the unit's main leader; b) A functional department for network security management should be established, and positions such as security directors and responsible persons for various aspects of security management should be established, and the responsibilities of each responsible person should be defined; c) Positions such as system administrators, audit administrators, and security administrators should be established, and the responsibilities of each department and position should be defined. 8.1.7.2 Personnel Allocation This requirement includes: a) A certain number of system administrators, audit administrators, and security administrators should be appointed; b) A full-time security administrator should be appointed and should not be concurrently held in another position. 8.1.7.3 Authorization and Approval This requirement includes: a) Authorization and approval matters, departments, and approvers should be clearly defined according to the responsibilities of each department and position; b) Approval procedures should be established for matters such as system changes, important operations, physical access, and system access, and the approval process should be executed according to the established procedures, and a hierarchical approval system should be established for important activities; c) It should regularly review and approve matters, and timely update the information of projects, departments, and individuals requiring authorization and approval. 8.1.7.4 Communication and Cooperation This requirement includes: a) It is necessary to strengthen cooperation and communication among various management personnel, internal organizations, and network security management departments, hold regular coordination meetings, and collaborate to handle network security issues together; b) Strengthen cooperation and communication with cyber security functional departments, various suppliers, industry experts, and security organizations; c) A list of affiliated units should be established, including the name of the affiliated unit, cooperation content, contact person, and contact information, and the like. 8.1.7.5 Audit and Inspection This requirement includes: a) Regular routine security inspections should be conducted, including daily operation of the system, system vulnerabilities, and data backup, and the like; b) Regular comprehensive security inspections should be conducted, including the effectiveness of existing security technology measures, consistency of security configuration and security policies, and implementation of security management systems; c) A security inspection form should be developed to implement security inspections, summarize security inspection data, form a security inspection report, and report the results of the security inspection. 8.1.8 Security Management Personnel 8. 1.8. 1 Personnel Recruitment This requirement includes: a) A designated department or personnel should be designated or authorized to be responsible for personnel recruitment; b) The identity, security background, professional qualifications or qualifications of the newly employed personnel should be reviewed, and their technical skills should be assessed; c) A confidentiality agreement should be signed with the newly employed personnel, and a job responsibility agreement should be signed with key position personnel. 8.1.8.2 Personnel Off-Duty This requirement includes: a) All access rights of off-duty personnel should be terminated in a timely manner, and various identity documents, keys, badges, and other soft and hardware provided by the organization should be collected back; and equipment; b) Strict transfer procedures should be followed, and a confidentiality obligation after transfer should be promised before leaving. 8.1.8.3 Security Awareness Education and Training This requirement includes: a) Security awareness education and job skill training should be provided for all types of personnel, and relevant security responsibilities and disciplinary measures should be informed; b) Different training programs should be developed for different positions, including training on security basics, job operation procedures, and the like; c) Skills assessment should be conducted regularly for personnel in different positions. 8.1.8.4 External Personnel Access Management This requirement includes: a) A written application should be submitted before external personnel physically access the controlled area, and after approval, a designated person should accompany them throughout the process and register and file a record; b) A written application should be submitted before external personnel access the controlled network access system, and after approval, an account should be opened and permissions allocated by a designated person. and register and file a record; c) After external personnel leave the scene, their access rights should be cleared in a timely manner; d) External personnel who obtain system access authorization shall sign a confidentiality agreement and shall not perform unauthorized operations, nor copy or leak any sensitive information. |
《Information Security Technology Security Protection Requirements for Key Information Infrastructure (Draft for Review) | 6.3 Security Management Organization a) The operator shall establish a committee or leading group for guiding and managing cyber security work, led by the main responsible person of the organization, set up a special cyber security management organization (hereinafter referred to as 'security management organization'), clarify the person in charge and the post, establish and implement cyber security assessment and supervision and accountability mechanisms. b) The main personnel of the safety management organization should participate in the informationization decision-making of this organization. c) Relevant personnel of the safety management organization should participate in national, industry, or industry cyber security related activities, obtain cyber security dynamics in a timely manner, and convey them to relevant departments and personnel. 6.4 Security personnel The operator should: a) Conduct security background checks and security skill assessments for the heads of safety management organizations and key position personnel, and only those who meet the requirements can take up their positions. Key positions include system management, network management, and safety management positions directly related to key business systems. Key positions should be managed by special personnel and be equipped with management by two or more people. b) Establish a network security training and education system, regularly carry out post-based network security training and skill assessment, and stipulate the appropriate annual training duration for key information infrastructure personnel and network security key position personnel. The content of training and education should include relevant systems and regulations of network security, network security protection technology, and network security risk awareness. c) Conduct a security background check for personnel before they take up their positions, and when necessary or when the identity or security background of personnel changes (for example, obtaining non-Chinese nationality), a re-examination of the security background should be conducted according to the situation. When personnel change internal positions, the logical and physical access permissions of the transferred personnel to the key information infrastructure should be reassessed, the access permissions should be modified, and relevant personnel or roles should be notified. When personnel leave their positions, all access permissions of the leaving personnel should be terminated in a timely manner, the hardware and software equipment related to identity authentication should be收回, and a departure interview should be conducted and relevant personnel or roles should be notified. d) Clarify the security and confidentiality responsibilities and obligations of staff, including security responsibilities, reward and punishment mechanisms, and confidentiality periods after leaving office. If necessary, sign a security and confidentiality agreement. |
Secret laws and administrative regulations, the security protection laws and regulations of military networks, relevant regulations of this industry and unit, responsibilities and businesses proposed by the operator itself, etc. | |
Note 1: After the formal issuance of the 'Regulations on the Security Protection Grade Protection of Cyberspace' (draft for comments) and the 'Technical Specification for Information Security - Security Protection Requirements for Key Information Infrastructure' (review draft), the operator shall sort out its relevant responsibilities and obligations in accordance with the latest requirements.
Note 2: After the formal implementation of the 'Data Security Law of the People's Republic of China', the 'Personal Information Protection Law of the People's Republic of China', and the 'Regulations on the Security Protection of Key Information Infrastructure', the operator shall fulfill its relevant responsibilities and obligations in accordance with the law.
Main work requirements for establishing a special safety management organization
When the operator establishes a special safety management organization, it should clarify its main work requirements. The main work requirements include:
(1) When the operator establishes a special safety management organization, it should comply with the relevant policies, laws and regulations, and standard specifications of the country and the industry and field where it is located, and meet the actual needs of its key information infrastructure protection.
(2) When the operator establishes a special safety management organization, it should follow the 'three synchronous' principle of 'synchronous planning, synchronous construction, and synchronous use' to plan, construct, and operate the special safety management organization synchronously.
(3) When establishing a special security management organization, operators should follow the requirements of defining the plan, post, position, personnel, goal, system, and work process.
(4) When establishing a special security management organization, operators should identify key positions, carry out security background checks, clarify authorization approval matters, procedures, and information-based decision-making participation mechanisms, complete responsibility separation, establish communication and cooperation mechanisms among various positions, security management organizations, using departments, external national cyber information departments, the Ministry of Public Security of the State Council, and protection work departments. At the same time, guide, standardize, and constrain the above-mentioned content through safety management systems.
(5) Operators should design a management mechanism for security personnel from aspects such as personnel review, personnel selection, personnel transfer, personnel departure, responsibility separation, safety awareness education, and professional skill training. Through safety management systems, it is clarified to provide guidance, constraints, and standards for the relevant work of managing security personnel.
(6) The post setting of the security management organization should be based on the principle of meeting the needs of routine security protection work and covering the routine cybersecurity activities that need to be carried out.
(7) Operators should complete the establishment or adjustment of the security management organization as early as possible in the development and construction phase. If it is not possible to mobilize sufficient personnel to establish or adjust the security management organization, a plan for establishing and improving the post should be formulated, and the organization or adjustment of the security management organization should be gradually established or adjusted, or cybersecurity service providers should be invited to assist in the protection of critical information infrastructure.
(8) Operators should sign a confidentiality agreement with cybersecurity service providers participating in the protection of critical information infrastructure.
4. Special Security Management Organization Design
The author will combine China's relevant policies, laws and regulations on the protection of critical information infrastructure, the requirements of the national standards and specifications to be released in the future, with ITIL practice, operator cybersecurity construction, operation and guarantee practice, to discuss the design of a special security management organization. The organizational structure of the special security management organization is shown in the following figure:
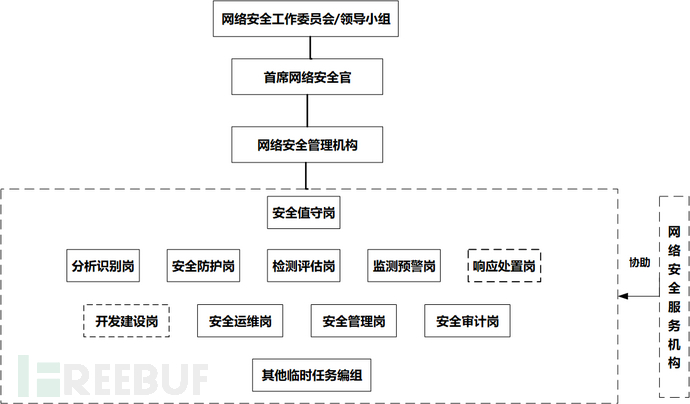 Note: The dashed box in the figure indicates that this position may consist of multiple entity roles.
Note: The dashed box in the figure indicates that this position may consist of multiple entity roles.
4.1 Cybersecurity Work Committee/Leading Group
Establish a Cybersecurity Work Committee or Leading Group to guide and manage the protection of critical information infrastructure, with the first person in charge of the unit serving as the highest leader. The main person in charge of the operator is the first person responsible for the security protection of the unit's critical information infrastructure, responsible for overall leadership and organization of all aspects of the protection of critical information infrastructure, responsible for establishing and improving the cybersecurity responsibility system and organizing implementation, and fully responsible for the security protection work of the unit's critical information infrastructure.
4.2 Chief Cybersecurity Officer
Establish a Chief Cybersecurity Officer, responsible to the Cybersecurity Work Committee or Leading Group, and in charge of all matters related to the protection of critical information infrastructure. The Chief Cybersecurity Officer may set up several assistants according to specific needs, to assist in the protection of critical information infrastructure. Assistants should generally be selected from key positions.
Different operators may have different titles for the Chief Cybersecurity Officer, the key point is that the operator should set up a position or role similar to the Chief Cybersecurity Officer to specifically be responsible for all matters related to the protection of key information infrastructure.
4.3 Network Security Management Organization
The security management organization separates the operator's network security responsibilities from informationization responsibilities and equips full-time network security personnel to engage in relevant work related to the protection of key information infrastructure.
The security management organization is composed of full-time personnel engaged in specific different work related to the protection of key information infrastructure. Depending on the different work in network security, it can be divided into roles such as security on-duty post, analysis and identification post, security protection post, detection and evaluation post, monitoring and early warning post, response and disposal post, development and construction post, security operation and maintenance post, security management post, security audit post, and other temporary task groups.
4.3.1 Security On-Duty Post
The security on-duty post can be a type of entity position, consisting of at least 2 people and implementing A/B roles. The main responsibilities and obligations include the following:
(1) Responsible for receiving external input on the relevant requirements for the protection of key information infrastructure, sorting out, analyzing relevant policies, laws, regulations, and standards of the state and the operator's industry and field regarding the protection of key information infrastructure, as well as supervision and compliance requirements;
(2) Responsible for receiving internal network security needs input and consultation from business departments and users of key information infrastructure;
Operation and maintenance on-duty of key information infrastructure, etc;
(3) Assist in establishing and improving security on-duty documents.
4.3.2 Development and Construction Post
The post of development and construction is not a single type of position and may consist of relevant roles from multiple departments of the operator, such as involving procurement roles when purchasing products or services. The operator should appoint a dedicated person to be responsible for the management of work related to development and construction and establish a coordination mechanism. The main responsibilities and obligations include the following:
(1) Responsible for the grading and filing, level evaluation, coordination, and other work related to the protection level of key information infrastructure (including newly built, reconstructed, or expanded);
(2) Compilation, amendment, and review of security design, construction, and implementation plans;
(3) Procurement of network products or services, including assistance in reviewing products or services that may affect national security;
(4) Management of in-house and outsourced software development;
(5) Management of project implementation, acceptance, and delivery;
(6) Supply chain management;
(7) Assist in formulating the long-term development plan for the network security of the unit and compiling the network security budget, etc.;
(8) Assist in establishing and improving security management systems and operational procedures in areas such as grading and filing, level evaluation, project planning, implementation, acceptance, delivery, procurement of network products or services, in-house and outsourced software management, selection and management of service suppliers, supply chain management, and other related documents.
4.3.3 Security Operation and Maintenance Position
The security operation and maintenance position can be regarded as a type of entity position, which can be composed of multiple people according to actual needs, responsible for carrying out regular security operation and maintenance work. The main responsibilities and obligations include the following:
(1) Unified operation and maintenance management of various equipment involved in the protection of key information infrastructure;
(2) Maintenance of network security baselines;
(3) Maintenance of basic configuration information, including network topology, version and patch information, etc., and implementation of change control;
(4) Backup and recovery management, including regular backup, formulating backup recovery strategies and procedures, etc.;
(5) Management of security operation and maintenance behavior specifications;
(6) Assist security managers in establishing and improving the system documents and operational procedures for security operation and maintenance;
4.3.4 Security Management Position
The security management position can be regarded as a type of entity position, which can be composed of multiple people according to actual needs, responsible for carrying out regular security management work. The main responsibilities and obligations include the following:
(1) Key position management;
(2) Physical environment management;
(3) Asset management;
(4) Media management;
(5) Password management;
(6) Change management;
(7) Outsourced operation and maintenance management;
(8) Security assessment management;
(9) Training management;
(10) Assist the Chief Cybersecurity Officer in formulating the long-term development plan for the unit's network security and compiling the network security budget;
(11) Assist the security auditor in conducting internal audits of the security management system;
(12) Assist the Chief Cybersecurity Officer in统筹 resources, establish and implement a number of systems, operational procedures, network security assessment and supervision and accountability mechanisms, etc. for the protection of the unit's key information infrastructure;
(13) Formulate various types of security management systems, processes, specifications, and operation procedures, etc. documents;
4.3.5 Security Audit Position
The security audit position can be regarded as a type of entity position, which can be composed of multiple people according to actual needs, responsible for carrying out regular security audit work. The main responsibilities and obligations include the following:
(1) Responsible for auditing the relevant network security behavior activities of the protection of key information infrastructure, checking whether the activities comply with the security strategies and operational procedures established by the operator, and evaluating their effectiveness and accuracy, identifying security violations, grasping the security status, and proposing improvement suggestions;
(2) Responsible for internal audits of the security management system;
(3) Assist security managers in formulating relevant system documents for security audits;
4.3.6 Analysis and Identification Position
The analysis and identification position can be regarded as a type of entity position, which can be composed of multiple people according to actual needs, responsible for carrying out regular analysis and identification work. The main responsibilities and obligations include the following:
(1) Responsible for business identification (chain), supply chain, etc., including the identification of assets, vulnerabilities, threats, and other risks;
(2) Identify the boundaries of key information infrastructure;
(3) Maintain the list of key information infrastructure;
(4) Maintain the network security risk management plan;
(5) Assist in relevant work in the following aspects: security protection, detection and evaluation, monitoring and early warning, technical countermeasures, event handling, etc.;
(6) Assist security personnel in establishing and improving identification documents for key information infrastructure.
4.3.7 Security Protection Position
The security protection position can be regarded as a type of entity position, composed of multiple people according to actual needs, responsible for carrying out regular security protection work. Mainly fulfill the following responsibilities and obligations:
(1) Formulate security protection strategies based on the requirements of the network security compliance system, relevant policy laws and regulations for the protection of key information infrastructure in our country, the internal network security baseline of the operator, the special security protection needs of this unit, and the requirements of the comprehensive network security defense system;
(2) Maintain and ensure the effectiveness of security protection measures;
(3) Assist in event handling, emergency response, and offensive and defensive countermeasures, etc;
(4) Assist in the related aspects of analysis and identification, detection and evaluation, monitoring and early warning, etc;
(5) Assist security personnel in establishing and improving relevant systems, strategies, operational procedures, and other documents for network security protection;
4.3.8 Detection and Evaluation Position
The detection and evaluation position can be regarded as a type of entity position, composed of multiple people according to actual needs, responsible for carrying out regular detection and evaluation work. Mainly fulfill the following responsibilities and obligations:
(1) Conduct at least one network security detection and risk assessment for key information infrastructure annually, either independently or by entrusting a network security service provider, timely rectify any identified security issues, propose repair and rectification suggestions for identified issues, assist relevant departments in security rectification, and track the disposal process;
(2) Establish a regular security detection and evaluation system and a comprehensive security detection and evaluation system;
(3) Be responsible for reporting major risks and potential hazards identified through detection and evaluation;
(4) Conduct regular security inspections, including the effectiveness of existing security technical measures, consistency of security configuration and security policies, and the implementation of security management systems, etc., and form a security inspection report for reporting;
(5) Cooperate with the protection work department to carry out network security inspection and detection of key information infrastructure;
(6) Assist in the analysis and identification, security protection, monitoring and early warning, technical countermeasures, event handling, and other related aspects;
(7) Assist security personnel in establishing and improving the security detection and evaluation system and procedures for key information infrastructure;
4.3.9 Monitoring and Early Warning Position
The monitoring and early warning position can be regarded as a type of entity position, composed of multiple people according to actual needs, responsible for carrying out regular monitoring and early warning work. Mainly fulfill the following responsibilities and obligations:
(1) Carry out the regular network security monitoring, early warning, and information reporting work of this unit, including receiving network security bulletins and early warning information from external sources and reporting the monitoring and early warning situation to the security management agency or the Chief Security Officer or directly responsible supervisor;
(2) Establish a working mechanism for monitoring and early warning and information reporting;
(3) Develop monitoring strategies, including defining the monitoring objects, processes, and content;
(4) Define the grading standards for early warning information of this organization, establish early warning information response and disposal procedures, and clarify the reporting, response, and disposal processes for different levels of early warning information;
(5) Assist in the analysis and identification, security protection, detection and evaluation, technical countermeasures, event handling, and other related aspects;
(6) Assist in establishing and improving documents for network security monitoring, early warning, and information notification.
4.3.10 Response and Disposal Position
The response and disposal position is not a single type of position, and may be composed of related roles from multiple departments of the operator, such as system administrators related to business departments when involved in event disposal. The operator should appoint a person in charge of the management of response and disposal related work and establish a coordination mechanism. The main responsibilities and obligations include the following:
(1) Carry out the response and disposal work of network security incidents in the unit, eliminate potential hazards, prevent the expansion of harm, and be able to restore key business and information systems to a known state;
(2) Report security incidents to internal departments or personnel that may be affected, and to other units or organizations related to the external key business chain and the event;
(3) Carry out necessary network security traceability, investigation and evidence analysis work;
(4) Organize the preparation of emergency plans, emergency exercises, and defense and attack countermeasures of the unit's network security, and continuously improve them;
(5) Assist in the relevant work of analysis and identification, security protection, detection and evaluation, monitoring and early warning, etc.
(6) Assist in establishing and improving systems and emergency plans for the management of network security incidents.
4.4 Other Temporary Task Groups
Other temporary task groups are different from permanent positions, and are temporary positions established to complete a certain type of task or demand when there is a specific task or need, by temporarily allocating resources. For example:
—When the key information infrastructure needs to be shut down, the operator selects personnel from relevant departments, and invites network security service institutions and external experts to join when necessary, to jointly establish a retirement and disposal working group, standardize the implementation process of the retirement and disposal activities, and ensure the smooth progress of the entire retirement and disposal activities. After the retirement and disposal activities are completed, the working group is dissolved.
4.5 Network Security Service Institutions
The operator can also entrust network security service institutions to assist the unit in carrying out relevant work related to the protection of key information infrastructure. However, according to the principle of 'who manages, who is responsible; who operates, who is responsible', the operator should fulfill the basic requirements of 'the unchanged responsibility for security management, the unchanged data ownership relationship, and the unchanged security management standards'.
V. Operation of Specialized Security Management Institutions
The design of the above positions is not fixed and immutable. The operator can reorganize the positions according to the actual situation of the unit.
The operator can also further divide the functions of the positions described above. According to the importance of key business and the complexity of security protection work, each position can also be in the form of a working group. The working group can also be divided into permanent groups and temporary task groups according to the nature of specific work. For example:
To ensure the stable and continuous operation of the business of key information infrastructure, the operator designs an operation and maintenance team as a permanent working group to carry out routine operation and maintenance work.
The operator may further clarify the responsibilities and business of the above positions according to the actual situation, so that the design of the responsibilities and obligations of the positions and roles can better meet and conform to the needs of the unit.。
Operators rely on the security management institution to carry out regular security protection work.
Operators should design and clarify authorization and approval matters, approval departments, and approvers based on job responsibilities. They should establish approval procedures for matters such as system changes, important operations, physical access, and system access, and implement the approval process according to the approval procedures, establish a hierarchical approval system for important activities, and regularly review approval matters, update the information of projects that require authorization and approval, approval departments, and approvers in a timely manner. For example:
——The monitoring and early warning post is in the form of a working group. Members need to issue notice information or early warning information, should first report to the group leader and the Chief Information Security Officer, and if necessary, the Chief Information Security Officer should also report to the first person in charge of the Network Security Work Committee or the leading group. After approval, it can be released through relevant procedures.
Operators should establish a list of matters related to the participation of security management institution personnel in decision-making on network security and informationization, as well as working mechanisms.
Operators should design a management mechanism for security personnel from aspects such as personnel review, personnel selection, personnel transfer, personnel resignation, separation of duties, safety awareness education, and professional skill training.
Operators should enhance cooperation and communication between various management personnel, internal organizations of the organization, and network security management departments, hold coordination meetings regularly, and collaborate in handling network security issues; strengthen cooperation and communication with network security functional departments, various suppliers, industry experts, and security organizations; and establish a list of external cooperation units, including the name of the external unit, cooperation content, contact person, and contact information. For example:
Operators can design a joint meeting system to enhance communication and cooperation between different positions or work groups, and hold joint meetings regularly or irregularly to collaborate in handling network security issues. At the same time, they should strengthen cooperation and communication with network security service institutions, network security research institutions, industry experts, protection departments, and other security organizations.
Operators should regularly conduct routine security checks, including the daily operation of the system, system vulnerabilities, and data backup. They should also conduct comprehensive security checks regularly, including the effectiveness of existing security technical measures, consistency of security configuration and security strategies, and the implementation of security management systems. They should formulate security check tables to implement security checks, summarize security check data, and form security check reports, and communicate the results of the security checks.
Summary
Due to the limited space, the author will not describe in detail the establishment and operation of security management institutions. This article is merely some thoughts of the author on the design and operation of the organizational structure of security management institutions, combined with practice, based on the requirements of relevant policies, laws and regulations, standards and specifications for the protection of key information infrastructure in our country. It only represents the author's personal opinion and does not necessarily mature or meet the actual needs of any operator. This article may have shortcomings and please feel free to point them out.
评论已关闭