Preface
Nowadays, there are countless data security incidents worldwide, and these incidents will have a very serious impact on individuals, enterprises, industries, and even the country, even threatening their security.
In recent years, China has successively promulgated the 'Cybersecurity Law' (June 1, 2017), the 'Data Security Law' (September 1, 2021), and the 'Personal Information Protection Law' (November 1, 2021), which guarantee the security of personal information from the legal and regulatory level, ensuring and restricting the safety and standardization of industry data operations.
Moreover, in recent years, with the frequent occurrence of data leaks, excessive collection of personal information, and the continuous enhancement of awareness and willingness for personal data protection, various industries have begun to pay increasing attention to the construction of 【Data Security System】.
Then the question arises, how should we build a 【Data Security System】? Where should we start? This is a problem that many newcomers, including myself, often face when we start doing data security, so I will also share some of my experiences and ideas on data security during this period, and everyone is welcome to point out any problems at any time.
Propose questions?
1. Why do you need to do data security?
2. What kind of data do you have?
3. Where is your data distributed?
4. Is your data secure? Compliant?
Four Steps to Build a Data Security System!
I. Planning
1. Current Situation Analysis
Analyze whether there are measures for the data security of your own company at present, and what measures have been taken; if the company has professional data security personnel, those with the ability can conduct a data security risk analysis themselves, or if not, you can also find a third-party organization to do a risk analysis to find out what risks and deficiencies exist in the current data security construction of the company.
2. Plan Planning
After recognizing the current situation of your own company, do some targeted planning for the scheme; what needs to be done in the first step, and what needs to be done in the second step?
3. Plan Argumentation
Of course, after a plan is in place, it is necessary to argue for its feasibility and applicability.
Two, Construction
1. Data Security Committee Organizational Structure Construction
Personally, I think that information security and data security are both related but can also be distinguished separately; information security has an organizational structure - the Information Security Leading Group, so data security also has a corresponding organizational structure - the Data Security Committee;
The data security committee is generally divided into four levels: decision-making level, supervision level, management level, and implementation level. The decision-making level and supervision level are generally undertaken by company leaders such as the CEO and CTO, the management level is generally undertaken by special responsible persons, and the implementation level is undertaken by technical personnel and team members, jointly forming the data security committee. More detailed information about the organizational structure will be introduced in a special episode later, so no further explanation is needed here.
2. System of Systems Establishment
The establishment of the system of systems is the same as the establishment of the information security system, and there is a set of specialized data security system of systems existing, and there are also first-level documents, second-level documents, third-level documents, and fourth-level documents (each level corresponds to the documents that can be viewed online), and here are several examples of data security systems such as: 'Data Security Organization Structure and Personnel Management Measures', 'Data Classification and Categorization Management Specification', 'Data Security Management Audit Specification', 'Data Security Emergency Plan', 'Data Security Personnel Training Management Measures' ... More detailed information about the specific systems and their content will be introduced in a special episode later, so no further explanation is needed here.
3. Data Management System Development
Regarding the data management system, such as data classification and categorization systems, data desensitization tools, etc., although there are not many on the market, there are also some, such as the DMS of some cloud services; of course, data security itself is relatively sensitive and diverse. If others are not working, you can also develop a system yourself; although my company is self-developed, I am not a developer, so there is no need for additional sharing here.
4. Personnel Capability Development
Regarding personnel capabilities, management capabilities, technical capabilities, operational capabilities, and compliance capabilities should all be possessed.
Three, Operation
1. Risk Prevention
Reasonable strategy formulation, including security strategies, data management strategies, classification and categorization strategies, sensitive data identification, and other strategies; at the same time, match baseline scanning to detect existing risk points in the system in a timely manner; implement national and industry standards, and do a good job of risk assessment on a regular basis.
2. Monitoring and Early Warning
Do a good job of situation monitoring and daily audit, and ensure timely detection and alarm.
3. Emergency Handling
Make a good emergency plan, and do a good job of review and rectification in a timely manner for security incidents.
Four, Assessment
Generally speaking, data security assessment work is carried out regularly within the company (once a year/specifically according to the actual situation of the company); it can also be entrusted to a specialized third-party risk assessment agency.
Solve the problem!!!
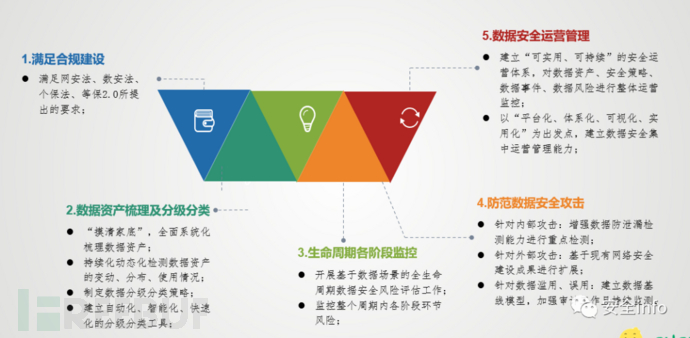
In fact, after fully completing the above four points, the issues mentioned in the previous text can be clearly understood: (Too lazy to type, directly upload the screenshot of the previously made PPT)
More security content sharing can be followed by the official account [Security info]!
最后修改时间:
1. CMS Introduction:
上一篇
2025年03月25日 07:38
1. Find the OEP in eight ways
下一篇
2025年03月25日 08:01
评论已关闭