On January 8, the Information and Communication Administration of the Ministry of Industry and Information Technology announced the list of APPs that infringe on user rights and interests in the second batch, with 15 products listed.
The first batch of 3 companies that did not complete the rectification as required were legally taken off the shelves on January 3.

Most of these are APPs that we are familiar with. Seeing these cannot help but cause us to tremble with fear. Luckin Coffee is one of the afternoon teas we often order, and ZhiMi is the word software we often use for exam preparation. It's simply too careless.
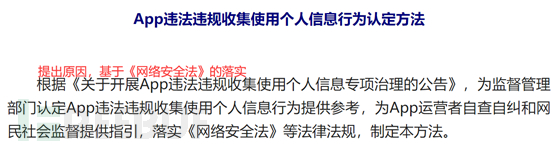
So, after the continuous rectification of website information security, the issue of APP security has gradually been brought to the agenda. Regarding the issuance ofIdentification Method for Illegal and Unauthorized Collection and Use of Personal Information by APPsto conduct a brief analysis of the notice.
One, the release of the identification method
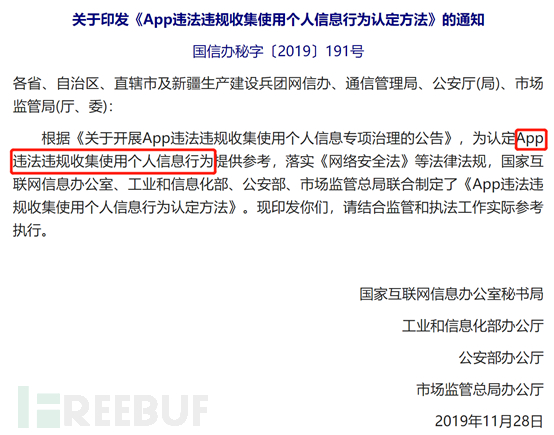
On December 30, 2019, at 8 am, the Cyberspace Administration of China issued a notice to print and distribute the 'Identification Method for Illegal and Unauthorized Collection and Use of Personal Information by APPs', jointly released by the Secretariat of the National Internet Information Office, the General Office of the Ministry of Industry and Information Technology, the General Office of the Ministry of Public Security, and the General Office of the State Administration for Market Regulation. The notice number is Guoxinban Mi Zi [2019] 191, mainly targeting illegal and unauthorized collection and use of personal information by APPs.
Two, the reasons for the identification method
Three, the content is mainly divided into six major parts
The first part
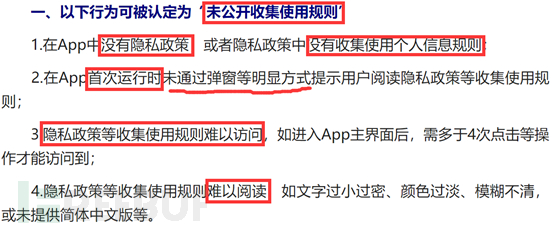
This primarily concerns privacy policies, strictly requiring that APPs must have privacy policies in place, and these policies must include entries on the rules for collecting and using personal information. Users must be prompted to read the privacy policy in a clear manner, such as through pop-ups, upon the first run. Additionally, privacy policies should be easily accessible and readable, with moderate text size and appropriate colors, much like the good examples we have seen with Suning and WeChat.
Part Two
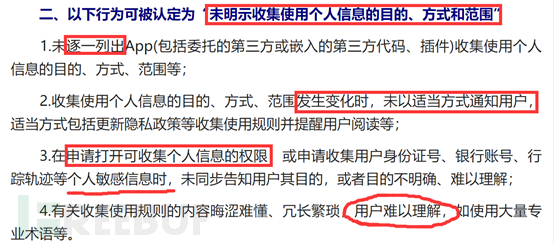
It is mainly about the purpose, method, and scope of personal information. It requires that these points must be listed one by one, and when there is a change, appropriate forms of notification should be used to inform users, such as popping up the privacy policy for users to confirm and agree before continuing to use. If sensitive information collection is involved, it must be informed to the user of the purpose, which must be clear, simple, and straightforward. Moreover, the content of the collection and use rules must also be simple, straightforward, and easy to understand, and it is not allowed to use a large number of professional terms that are difficult for users to understand.
Part Three
It is about the user's consent to collect and use personal information. There are several important points here: first, the user must give explicit consent before collection; it is not allowed to interfere with the user or collect directly; second, it cannot exceed the scope of collection; when there is an update or change, the user needs to re-select or change the permission status; third, the privacy policy should be actively selected by the user and not directly agreed upon, and it is not allowed to deceive or mislead users to collect information illegally or in violation of the rules, while providing a way to withdraw the collection.
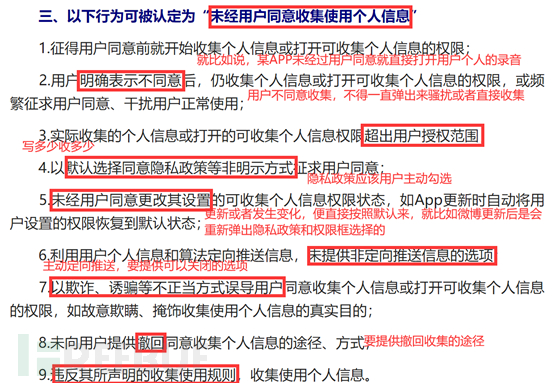
Part Four
It is about the principle of minimizing the collection of personal information. The most important point is that if the user does not agree to collect non-essential personal information or open non-essential permissions, or open multiple collection permissions at one time, and refuses to provide business functions, such as disagreeing with an APP's location permission and then crashing, this is illegal behavior. Moreover, it is not allowed to force users to collect personal information solely due to reasons such as service quality and user experience.
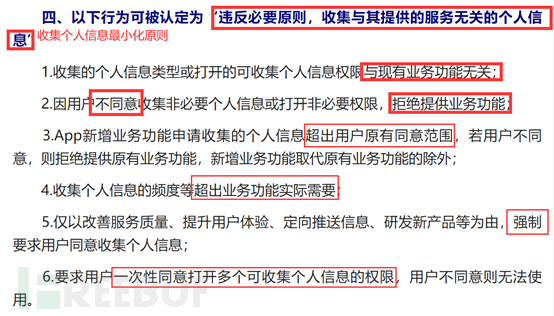
Part Five
It is about the provision of personal information by third parties, indicating that the provision of user personal information to third parties must be with the consent of the user and must be anonymized. Otherwise, many cases of personal information leakage are due to this, where information is transmitted from one place to another, and it is also not allowed to directly transmit data to the background for collection by third parties. In addition, when connecting to third-party applications, it is also necessary to inform users clearly and obtain their consent before providing personal information.
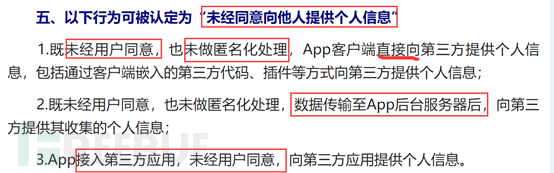
Part Six
It is about the two aspects of user account cancellation, deletion of personal information, and complaints and reports. It requires enterprises to provide effective functions for correcting, deleting personal information, and canceling accounts, and may not set unnecessary or unreasonable conditions. It also requires timely response, and if manual processing is required, the time limit must be specified and may not exceed it. The background must keep track of operational behavior at all times.
Enterprises must also establish and publicize channels for receiving complaints and reports on personal information security, and must commit to deadlines and complete within the specified time.
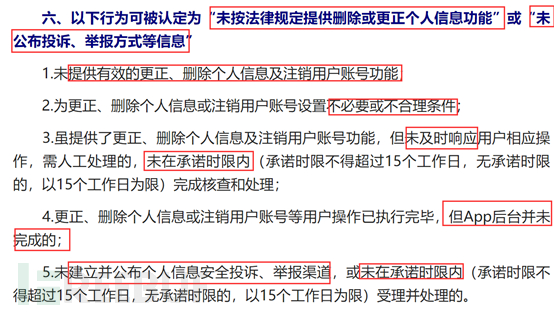 This regulation refines the implementation of the 'Cybersecurity Law' regarding the collection of personal user information by APPs, specifically addressing these six aspects. While it does not involve many technical requirements, it does require that enterprises and users must pay attention to the protection of personal information and sound the horn of victory in the APP's battle!
This regulation refines the implementation of the 'Cybersecurity Law' regarding the collection of personal user information by APPs, specifically addressing these six aspects. While it does not involve many technical requirements, it does require that enterprises and users must pay attention to the protection of personal information and sound the horn of victory in the APP's battle!
*Original Author: Salted Milk Tofu Pudding, this article is part of the FreeBuf Original Reward Plan, reproduction is prohibited without permission
评论已关闭