The starter dish
Emmmmm, a while ago, I received a red team detection project, oh my~It's been a long time since I fought, I'm ready to show a wave, never expected to go to prison on the mobile end directly, didn't work hard in my youth, no chance to make contributions to the big guys.
Information collection
Several points to pay attention to on the mobile end:

•APP•WeChat Official Account•WeChat Mini-program•Alipay Mini-program
......This little chicken only knows these few
The painful road
Fortunately, the target is quite helpful, with APP, mini-program, and official account, we should first look at the official account, mini-program, and APP in this order.
Official account
Checked the official account, all are used to post soft articles without any points of exploitation, official account over (this water was drawn too quickly)
Mini-program
The mini-program rejected me directly, I didn't even get a chance to see it, one taken down and one rejected.
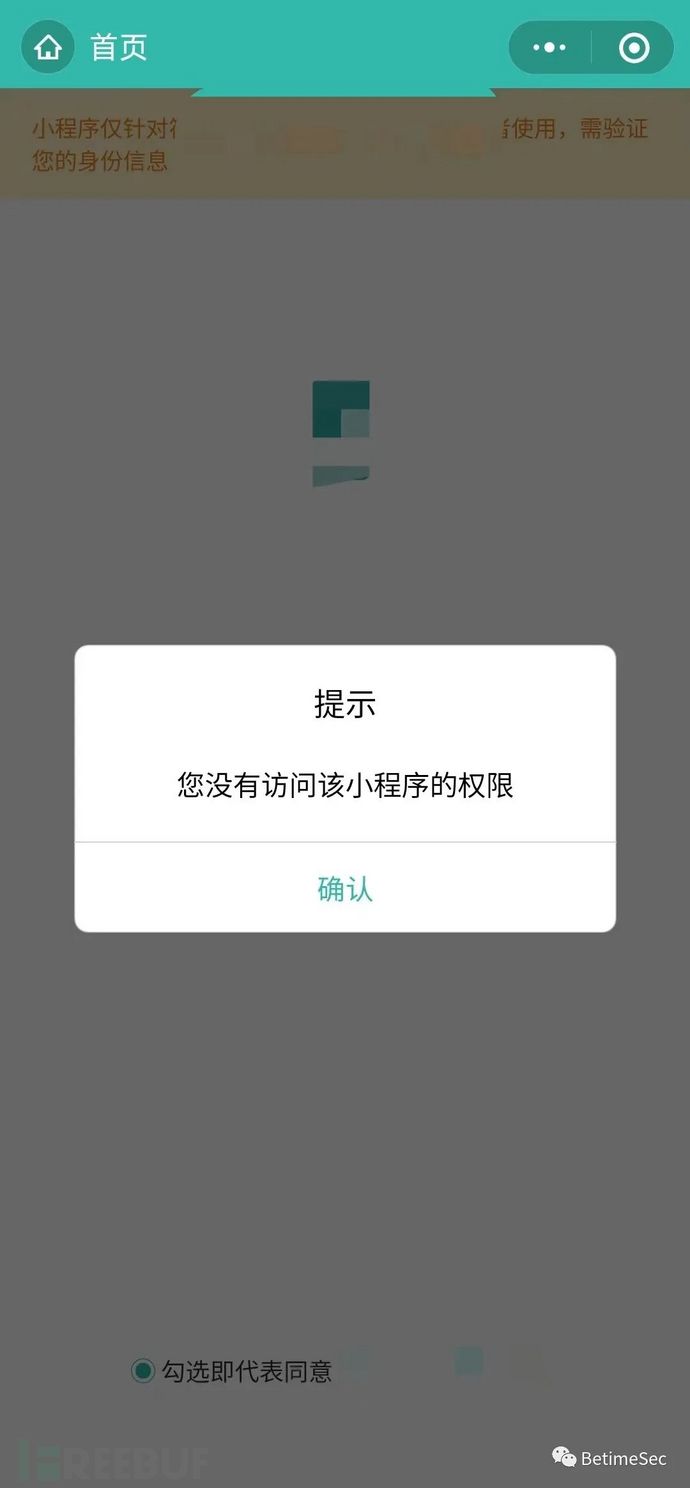

Take a look at this ugly mini-program with the traditional BurpSuite. Hiccup, hasty, catching WeChat mini-programs above Android 7.0 will have certificate issues that prevent catching packets, but! This does not affect the continuation of the operation, bring out Fiddler, forward the traffic to BurpSuite, install the certificate, and listen to the port before trying again
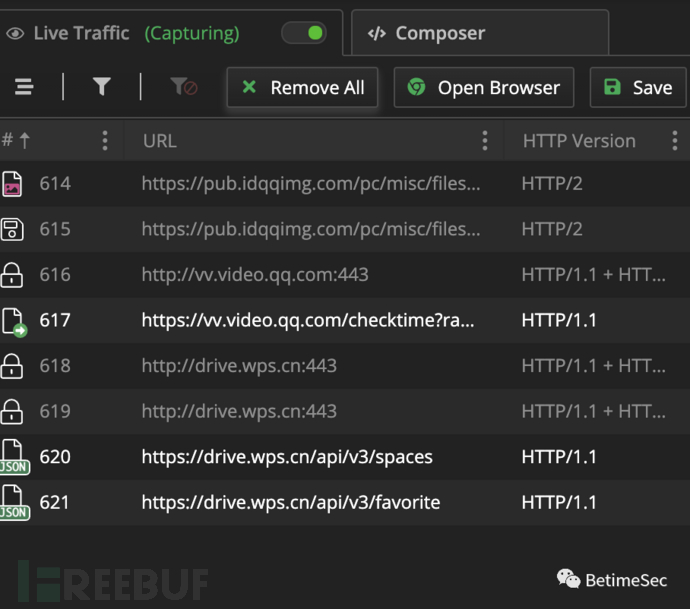
Oh my, a bunch of useless packages, I still haven't waited for the 'it' I want, think back, he should verify my identity because there should be data packets interacting with the server, the men of Sangfor can't give up, continue!!
Open the magic tool SSLUnpinning, get Lsposed ready, the target is directly given to WeChat, witness the moment of wonder, got it! What??!!It turned out that there was no forwarding
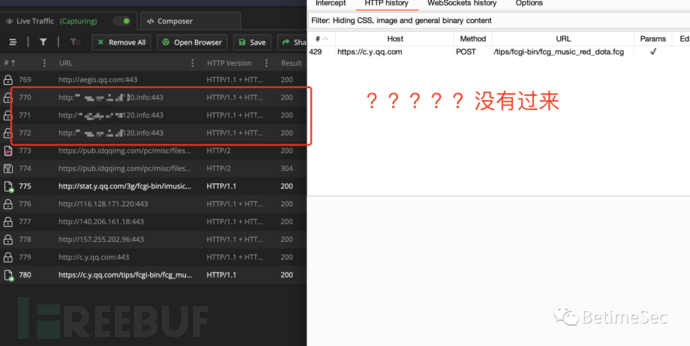
Do you think this is the end? Impossible, there are still treasures, JustTrustMe++ comes out to continue to attack it, cried~Finally, you are here - my data packet. (The original JustTrustMe is no longer effective)
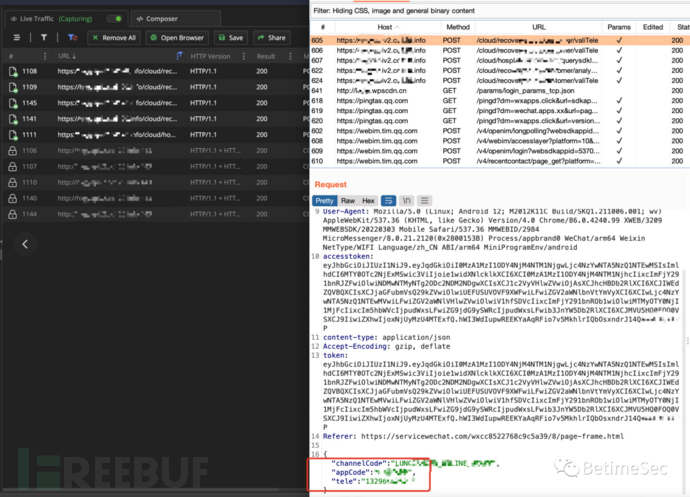
Caught the packet, what's the use? There are still some points to exploit, the mini-program has hurt me, but the process of catching the packet on it is still worth recording and learning.
APP
The app is my last resort, I can't really just float around and risk losing my job.
There are two apps: one for the general public version and another for the internal staff version. I got two APK packages, installed them on the phone.

I flashed the LSposed framework after rooting my own physical machine. I don't like emulators much, as there are various detections which are very inconvenient (the joy of scripts, you don't understand -- manual flip). So I directly installed it on my own phone and set up the proxy to start working.
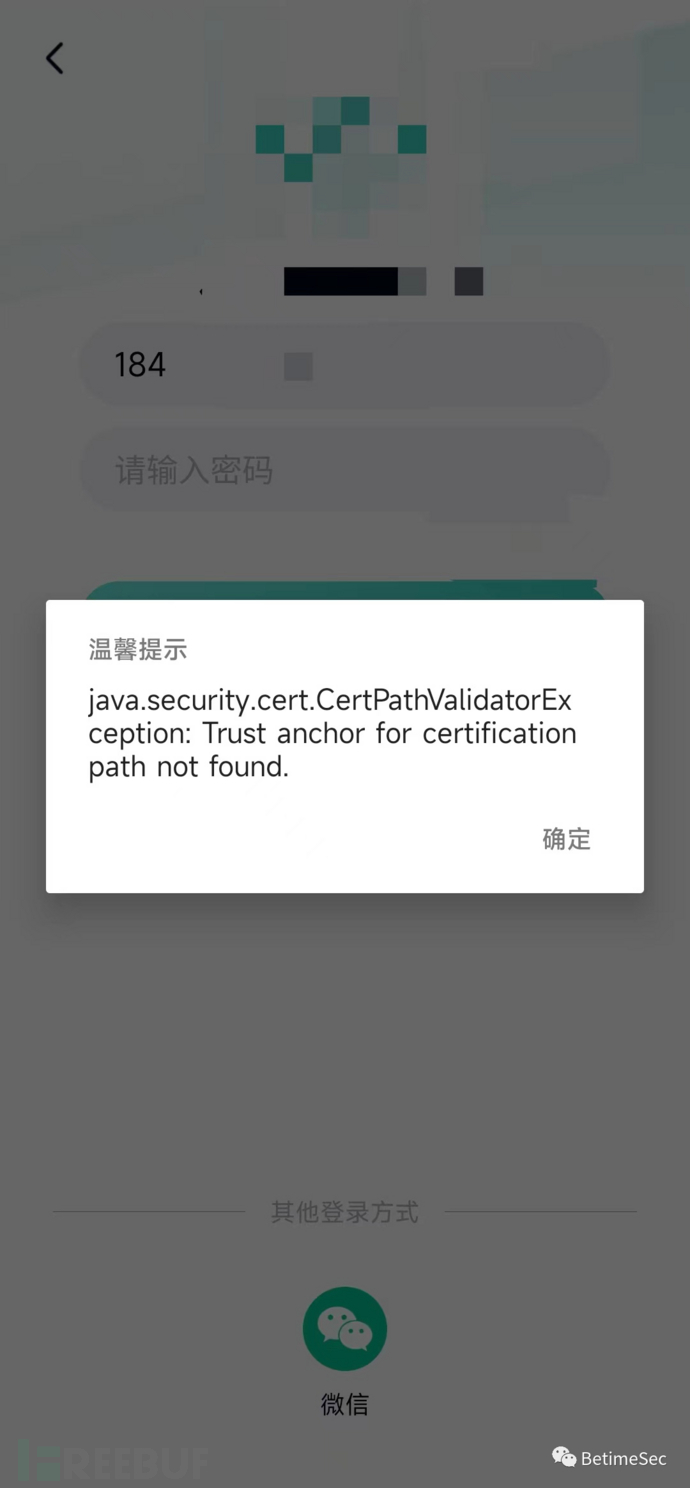
Wow! A heavy blow from above, directly detecting and not letting me in. The old rule, let's try SSLUnpinning first.
There is detection, I'm not worried, and you can't block my account, just keep going.
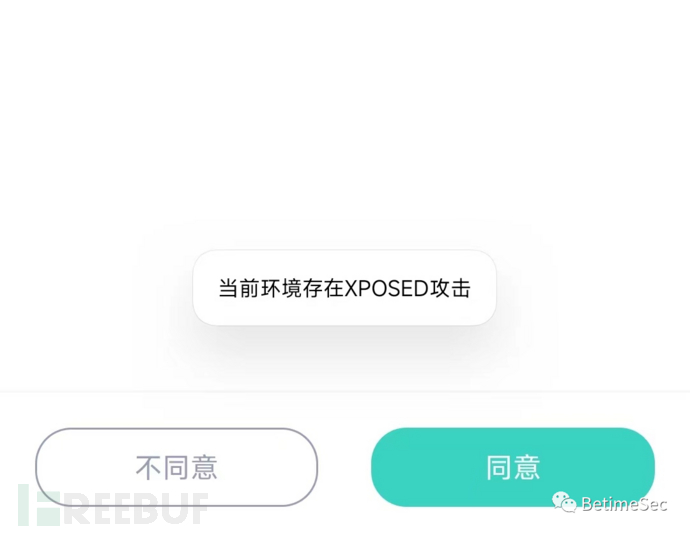
WuHu~ After all the detours, it feels good to get in. A round of operations fierce as a tiger, some connections directly report errors, it seems that the old saying is true, SSLUnpinning is not working anymore. JustTrustMe++ YYDS, let's get started!

The encryption is done well, with too many interfaces, and finally it's all on one person. If you don't have the patience, just use the big hammer.
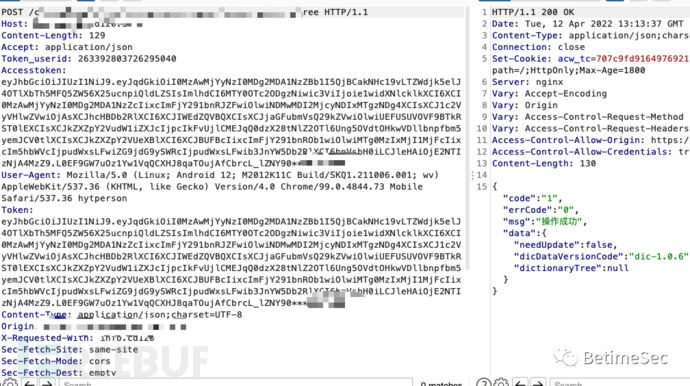
Take a look at the source code after decompilation, emmm, there is a love encryption shell, and the shell is removed all at once: Reflection Master, fdex2, dexdump, all failed. The big guys have written hooks, and I'm just a little brother who can't play. You can also make an obfuscation machine using the Google Pixel 1st generation, but since I don't have a Pixel machine at the moment, I haven't done it.
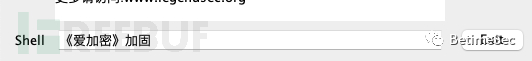
Change the way of thinking. I don't believe that all your APKs are obfuscated. Let's get back to our old ways of information collection. The current new version is 6+, and I found a 4+ version, which is too old, emmmmm, just make do with it. Change the suffix to zip, extract the dex directly into jadx, and search for hard-coded sensitive information: username, password, key, oss, etc. If you're lucky, you can find OSS directly. Indeed, the keys of the old version have expired. Don't worry, there is also another version 5+.

Using the same approach, search for OSS in the decompilation and directly double it out. Both oss connections were successfully tested. The frontend is over.
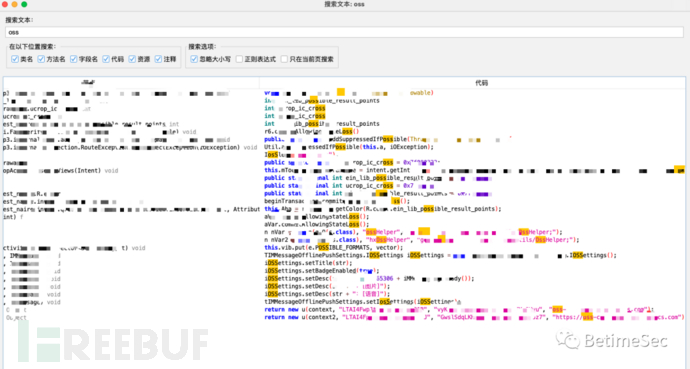
I never expected that the internal apk used by the target did not have any obfuscation. This is something I never expected. After decompiling, I found only one oss, and one of the two before was a duplicate, emmmmm.
Finally
The target app has been obfuscated, checking for trusted certificates and runtime environment. Fortunately, there are no restrictions on runtime environment and proxy, otherwise I would have to find a way to hide Magisk and LSposed again. Generally, I rarely use emulators, and good apps will check for ROOT and emulators, which can be very麻烦. It's more convenient to directly buy a physical machine and flash the framework. Since the time is limited this time, I didn't go deep into the obfuscation, just ran the existing obfuscation tool. Daily penetration may focus more on the backend, but there may also be surprises in the frontend hard-coded in the source code, as well as historical versions.
评论已关闭