Driven by the development of cloud computing, multi-tenant technology has gained rapid development and widespread application. While achieving resource/data permission isolation between multiple tenants at the technical level, cloud platforms also bring new challenges to their own security management work.
In this way, tenants are more convenient,The difficulty of managing many tenants for the '包租公' has increased.
During the development and application of enterprise business in the cloud, automated asset risk management and self-inspection capabilities are needed. However, most cloud-native asset risk management tools lack the ability to control multiple tenants uniformly and are difficult to effectively manage the complex and massive assets of various tenants in the cloud.
It is difficult to achieve unified control of multi-tenant assets
Although most cloud platforms have their own vulnerability scanning capabilities, they cannot meet the needs of enterprises for unified control of cloud tenant and asset risks.
Low discovery rate of cloud asset risks
Although traditional asset risk management tools have the ability to control multiple tenants uniformly, the characteristics of their deployment architecture prevent them from deeply integrating with cloud platform architecture and from effectively detecting risks in cloud assets from a cloud-native perspective.
How to achieve effective asset risk management under the cloud environment architecture, and balance the expansion of cloud assets with security, which makes countless cloud platform operation and maintenance engineers feel frustrated.

Don't be afraid!
There are no permanent difficulties to hinder, only break-out leaders who stand up.The multi-tenant asset risk management solution for cloud platforms, to break down the困扰 cloud platforms'

Targeted treatment, with both looks and substance
Multi-tenant asset risk management solution for cloud platforms
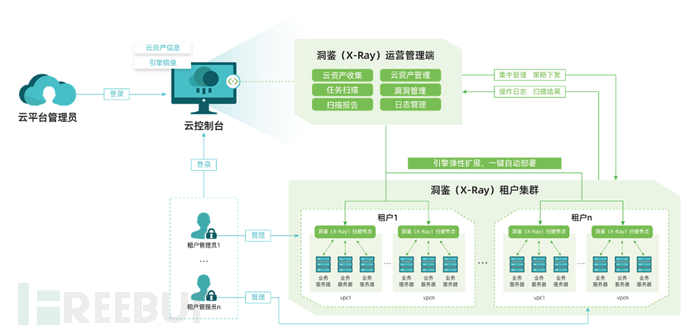
This solution adopts the lightweight distributed deployment mode of the X-Ray security assessment system, deeply adapts to cloud architecture, integrates into the cloud management platform, uses one management end on the cloud platform to centrally manage all scanning nodes, avoiding the disadvantages of deploying a complete scanner within the VPC. The solution supports one-click automatic deployment and startup on the tenant side, automatically completes network environment checks and resource quotas on the basis of strict isolation of cloud tenant data permissions, realizing flexible expansion and unified control of scanning nodes on the tenant side.
The operation and management end of X-Ray can perform unified management and security monitoring of all tenant assets on the cloud platform, and can issue scanning tasks when necessary to ensure the overall security of the cloud platform; the scanning nodes on the tenant side support risk detection and management of the tenant's own assets. X-Ray is deeply integrated with the cloud account system, realizing vertical asset management from top to bottom.
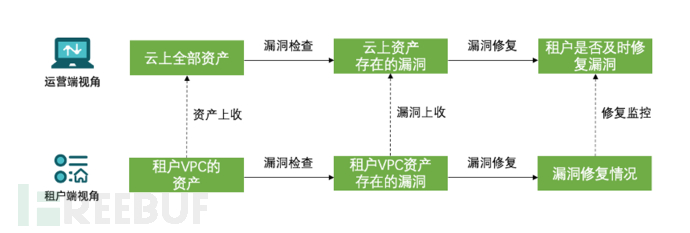
At the same time, the X-Ray platform itself has the ability of multi-tenant elastic expansion, supporting horizontal expansion of scanning nodes from few to many, meeting the needs of cloud tenants to expand at any time and flexibly adapt to cloud scenarios. Ultimately, it enables enterprise security builders to configure in a cascading manner, centrally manage, unify the issuance of scanning strategies, and collect operation logs.
Value and Advantages
Distributed architecture, flexible expansion of scanning nodes
The solution relies on the lightweight distributed deployment architecture of X-Ray, and can implement multiple scanning node deployments on the tenant side, supporting high-concurrency process scanning, improving detection efficiency.
Asset isolation, supporting cloud tenant cascading management
X-Ray can implement partition isolation management and scanning according to the cloud tenant architecture system, and strictly divide the permissions of different regional administrators, meeting the cascading scanning management needs of the headquarters of multi-branch subordinate departments of cloud tenants.
Precise vulnerability detection, efficient identification of asset risk points
X-Ray achieves comprehensive vulnerability scanning coverage of cloud platform assets through self-启发式 vulnerability detection algorithms, combined with semantic analysis and diversified detection rules, ensuring accuracy without affecting customer business.
Concentrated control of asset risks, achieving efficient operation and maintenance
X-Ray, based on the operation end and tenant end of the cloud platform, supports unified management of all tenants and their assets on the cloud platform, issuance of scanning strategies, collection of scanning results and operation logs, etc., for centralized control, effective centralized management of cloud platform assets and asset risks, and realization of efficient and safe operation and maintenance.
In the process of the implementation of a domestic leading bank customer project of the multi-tenant asset risk management solution for cloud platforms, the solution provided the customer with the ability to centrally manage multi-tenant cloud platforms, detect cloud platform asset risks, and track the risk lifecycle, ensuring the customer's supervision needs for the overall security of cloud assets.
The digital transformation of various industries is in full swing, how to eliminate the concerns about enterprise cloud security construction?
Multi-tenant asset risk management"TrickIt has been sincerely offered, have you got it?
评论已关闭