
Installed and configured on the local deviceMetasploit-FrameworkThe following components are included in the PATH environment variable:
Msfrpcd
Msfvenom
Msfdb
Tool Installation
Precompiled Installation
The general researchers can directly access the [Releases Page】Download precompiled tool code.
Source Code Acquisition
For developers, it is also possible to directly download the source code of this project and manually build it.
Firstly, use the following command to clone the source code of this project locally:
git clone https://github.com/WayzDev/Kage.git
Next, switch to the project directory and install the necessary dependency components for the tool:
cd Kage yarn # Or npm install yarn run dev # Or npm run dev
The following command can be used to build the project code:
yarn run build
Note that if you need to generate APK Payload, please select Raw format from the drop-down menu.
We recommend using electron-vue, as it handles tool dependency components better and reduces the size of the final build code.
Tool Running Screenshots
Tool Dashboard
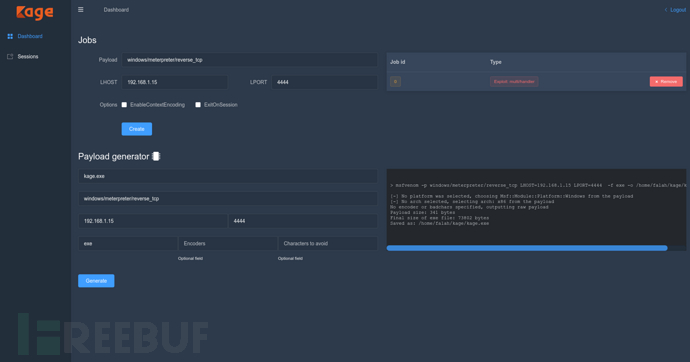
Tool Control Panel
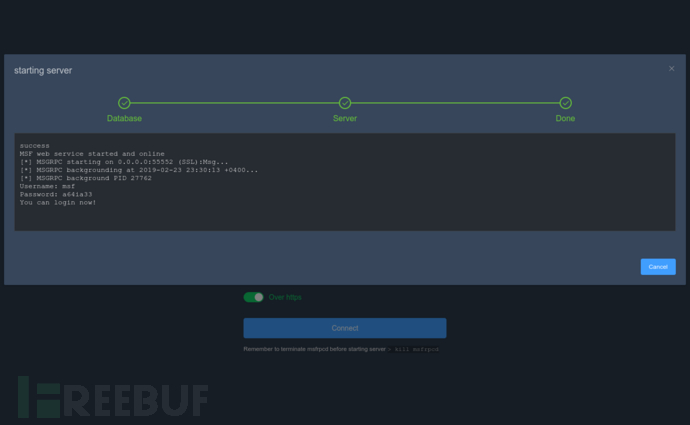
Server Status
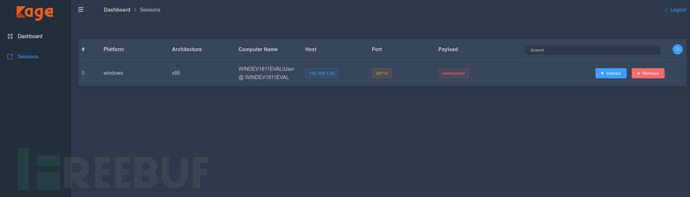
File Management

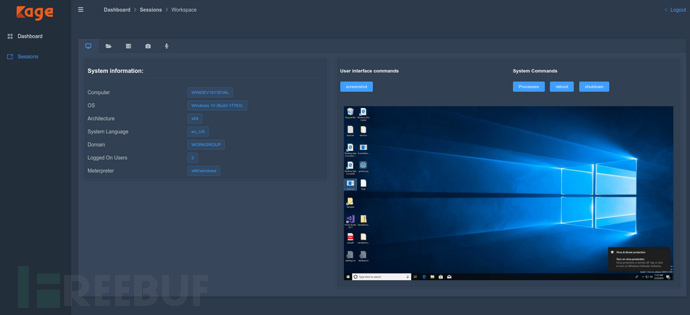
Session Management
Tool Usage Demonstration
Video Address:【Click to Watch】
License Agreement
The development and release of this project followGPL-3.0Open Source License Agreement.
Project Address
Kage:【GitHub Gateway】
Reference Materials
https://github.com/AhMyth/AhMyth-Android-RAT
https://github.com/rapid7/metasploit-framework
https://simulatedgreg.gitbooks.io/electron-vue/content/en/getting_started.html
https://github.com/tomasgvivo/node-msfrpc
https://github.com/SimulatedGREG/electron-vue
https://github.com/vuejs/vue-cli
https://simulatedgreg.gitbooks.io/electron-vue/content/index.html
评论已关闭