What is JWT
JWT stands for JSON Web Token. If you understand it literally, it seems to be a token based on JSON format for network transmission. In fact, JWT is a compact Claims statement format designed for transmission in space-limited environments, common scenarios such as HTTP authorization request headers and URI query parameters. JWT will convert Claims into JSON format, and this JSON content will be applied as the payload of the JWS structure or applied as the original string of the JWE structure (encrypted and processed). It uses a message authentication code (Message Authentication Code or abbreviated as MAC) and/or encryption operation to digitally sign or protect the integrity of Claims.Don't worry if you can't understand it, just simply understand: authentication method
Environment setup
# OWASP Juice Shop Lab
Configuration: Kali Docker
# Pull the OWASP Juice Shop container
docker pull bkimminich/juice-shop
# Start container
docker run -d -p 3000:3000 bkimminich/juice-shopSet up access at ip:3000

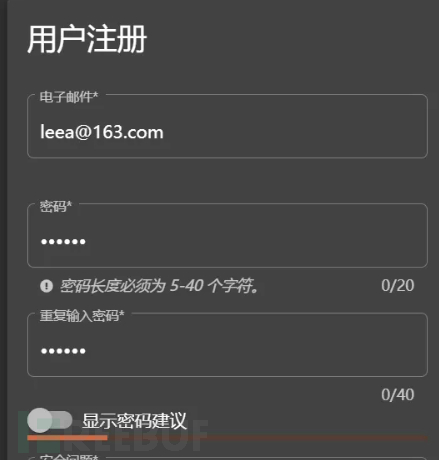
Create an account leea@163.com / 123456
Three parts of JWT
JWT consists of three parts: header, payload, and signatureHeader (HEADER)
A JSON string containing the current token name and the encryption algorithm
{"typ":"JWT","alg":"HS256"}After using base64 encryption
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9Payload (PAYLOAD)
A JSON character string containing some custom information
{"sub":"1234567890","name":"John Doe","admin":true}Use base64 encryption
eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiYWRtaW4iOnRydWV9Signature (VERIFY SIGNATURE)
The base64 encrypted header information is concatenated with the base64 encrypted payload part, then added with the current key, and encrypted with the encryption algorithm in the header
header (base64 after)
payload (base64 after)
secret
This part needs to use the base64 encrypted header and the base64 encrypted payload connected with a dot, and then use the salt secret combined encryption method declared in the header for encryption, and then it constitutes the third part of jwt.
TJVA95OrM7E2cBab30RMHrHDcEfxjoYZgeFONFh7HgQConnect these three parts with a dot to form a complete string, which constitutes the final jwt:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiYWRtaW4iOnRydWV9.TJVA95OrM7E2cBab30RMHrHDcEfxjoYZgeFONFh7HgQPrinciple
After understanding the components of jwt, we know
1. The encryption method is base64 encoded, we can see it, and operate it
2. The payload data is base64 encoded, and it can also be operated
3. The signature is encrypted by the key, we do not know the key, and cannot operateOk, the problem is very clear, the only thing that is stuck with us now is the signature, what methods can we use to bypass the signature?
The answer is very clear: letThe signature is emptyIt can be, first of all, we know that the formation of the signature depends onThe encryption algorithm, key, and payload data in the headerAnd formed, and because we have no way to know the key, it leads to the inability to perform encryption, and even if the payload content can be modified, it is not recognized by the signature behind it, soThe key and the payload data are not the starting pointsHow should we modify the encryption algorithm to make the signature empty? The answer is, when there is no encryption algorithm, that is, the encryption method is None
jwt hijacking reproduction
1. Capture the login packet
We used a newly registered account to log in, capture packets, continuously send packets, and find the request packet with the Authorization header
I introduction of black rose Lucy MaaS products
Git leak && AWS AKSK && AWS Lambda cli && Function Information Leakage && JWT secret leak
ArchKeeper (Introduction): Issues and concepts of the architecture protection platform
Hackers are using Windows RID hijacking technology to create hidden administrative accounts.
How to use Acheron to modify Go programs and try to bypass antivirus product detection.
评论已关闭
