DLL Hijacking
1. Introduction to DLL

DLL (Dynamic Link Library) files are dynamic link library files, also known as 'application extensions', and are a type of software file. In Windows, many applications are not complete executable files but are divided into some relatively independent dynamic link libraries, i.e., DLL files, placed in the system. When we execute a program, the corresponding DLL file will be called. An application can use multiple DLL files, and a DLL file may also be used by different applications, such files being called shared DLL files.
2. Principle of DLL Hijacking
Before Windows xp sp2
The directory and order of Windows searching for DLLs:
- The directory of the application corresponding to the process;
- Current directory (Current Directory);
- System directory (obtained through GetSystemDirectory);
- 16-bit system directory;
- Windows directory (obtained through GetWindowsDirectory);
- Each directory in the PATH environment variable;
After Windows xp sp2
The directory and order of Windows searching for DLLs (SafeDllSearchMode is enabled by default):
The default registry is: HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Session Manager\SafeDllSearchMode, the key value is 1
- The directory of the application corresponding to the process (can be understood as the program installation directory, such as C:\ProgramFiles\uTorrent);
- System directory (i.e., %windir%system32);
- 16-bit system directory (i.e., %windir%system);
- Windows directory (i.e., %windir%);
- The current directory (the directory where the running file is located, such as C:\Documents and Settings\Administrator\Desktop\test);
- Each directory in the PATH environment variable;
Above Windows 7 version
If the system no longer has SafeDllSearchMode and adopts KnownDLLs, then any DLL file under this item will be prohibited from being called from the directory where the exe itself is located, and can only be called from the system directory, that is, the SYSTEM32 directory, its registry location is:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\KnownDLLs
Windows 2003 and above, as well as Win7 and above operating systems, determine the path of the DLL to be called by the application through the mechanism of 'DLL Path Search Directory Order' and 'KnownDLLs Registry Item', and then the application loads the DLL into its memory space and executes the corresponding function.
- By default, if the software is installed in the root directory of C drive, rather than C:\Program Files, authenticated users have write permissions to this directory. In addition, software such as perl, python, and ruby are usually added to the path variable. The attacker can write a malicious DLL in the current directory, and the user will be infected as soon as the exe program is run again.
- Combining SafeDllSearchMode + KnownDLLs can be used to prevent DLL hijacking, but if a 'rarely used' DLL, that is, a DLL that has not appeared in the KnownDLLs list, is called, then regardless of whether SafeDllSearchMode is enabled or not, the first order of DLL search is always the current directory of the program. This is a DLL hijacking vulnerability (place a dll with the same name in the same directory as the program in advance, and it will be loaded preferentially during the process of starting the process, achieving hijacking).
3. Find DLL hijacking points
Method one (API Monitor):
Taking D盾 as an example, use API Monitor to find the DLL loaded by D盾

Find DLLs that use relative paths

Check the registry and find that the DLL is not in KnownDLLs and can be hijacked

Use the DLL that can pop up the calculator provided by rattler for verification
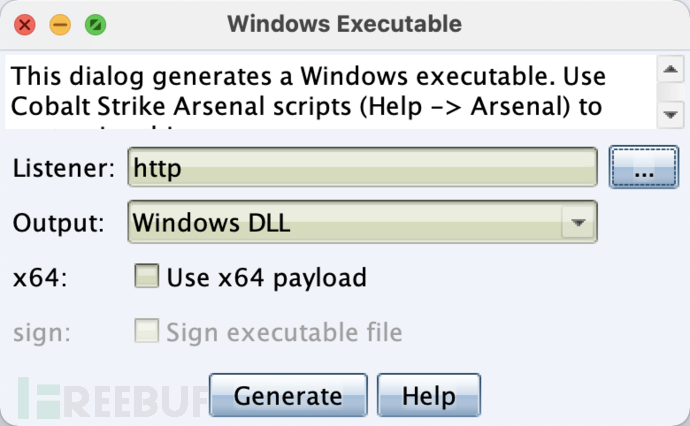
Use CS to generate DLL files
Rename the generated DLL file to cscapi.dll, double-click D盾 to go online

Method two (Rattler):
Use the fully automatic detection tool Rattler to find DLL hijacking:https://github.com/sensepost/rattler
Note: When using this tool, the path of the test software cannot contain Chinese characters.
If the target machine runner needs to hijack an application, you need to kill the process first, then upload the hijack dll and the source dll to complete the replacement.
Rattler_32.exe "C:\Users\lhc\Desktop\Hacker\d_safe_2.1.5.4\D_Safe_Manage.exe" 1

Method three (Windbg Preview+ChkDllHijack):

No DLL that can be hijacked was found
4. DLL killing
Currently, there is no particularly elegant solution
Method one: DLL call to kill exe
// Entry function
BOOL WINAPI DllMain(HMODULE hModule, DWORD dwReason, PVOID pvReserved)
{
if (dwReason == DLL_PROCESS_ATTACH)
{
DisableThreadLibraryCalls(hModule);
}
else if (dwReason == DLL_PROCESS_DETACH)
{
STARTUPINFO si = { sizeof(si) };
PROCESS_INFORMATION pi;
CreateProcess(TEXT("C:\Users\lhc\Desktop\test\test.exe"), NULL, NULL, NULL, false, 0, NULL, NULL, &si, &pi);
}
return TRUE;
}
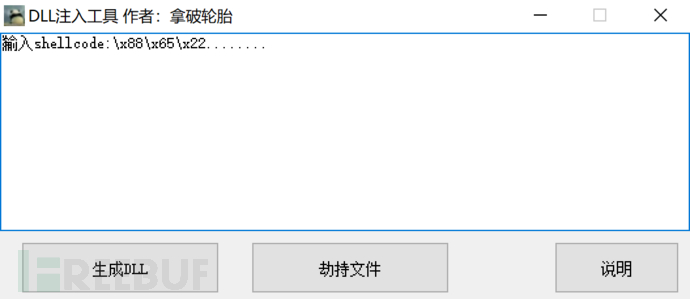
Method two: Napoleon Fetus DLL Hijacking Tool (only for FireEye)


5. Package packaging
DLLs like D shield can be compressed into a package and sent to the victim
It can be used if the package format is usedNSIS to create installation packages
6. Todo
Code implementation of elegant DLL anti-kill
References
https://www.cnblogs.com/swyft/articles/5580342.html
Author: DeepinSafe Blue Lab _ Beijing Tianxiong Team
评论已关闭