On March 27, Weibu released a research report on the black-hat gang 'Yinhu' that attacks industries such as finance, securities, and education. 'Yinhu' uses fake tool websites, WeChat, and other instant messaging tools to send Trojan files, tricking employees into clicking, and thereby intruding into the corporate office network.
Weibu Terminal Security Management Platform OneSEC discovered the attack behavior of 'Yinhu' earlier. After further analysis by the Weibu Security Laboratory, it was found that the parent sample has at least 4 exploitation methods that can effectively counter or bypass existing terminal security products (antivirus and EDR). This article will analyze and summarize the characteristics of each bypass method in detail to help everyone effectively respond to the new threats in office networks. (You can also directly view the [Summary of Methods] to quickly understand the characteristics of each attack method)
# Unveiling the Four Bypass Methods of 'Yinhu' #

Weibu summarizes the four bypass methods in the attack process of the 'Yinhu' gang: Misrepresenting Fish, Taking the Place of Another, Disguising the Truth, and Concealing Malice.
01 Misrepresenting Fish in浑水摸鱼:Simulating mouse clicks to construct a legitimate execution chain to load malicious code
After the parent sample disguised as 'xx chat history' is double-clicked by the user, it will release three files:
- vbn.exe is a mouse click simulation program that is not malicious;
- adta.exe is a stock software with a legitimate signature;
- libcef.dll is a malicious DLL file;
Currently, some terminal security products rely on effective file signatures for their trust logic in behavior detection. In this attack method, 'Yinhu' takes advantage of the characteristics of white programs (a certain stock software with a legitimate signature) to disguise itself as a legitimate process chain. The specific execution is shown in the figure below:
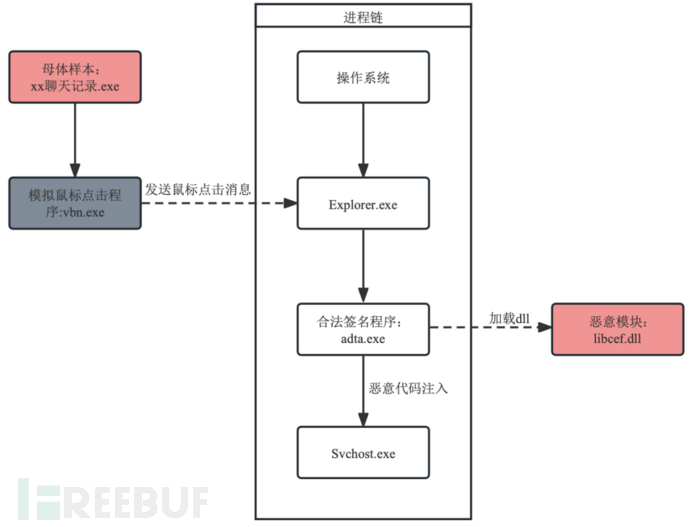
- The mother sample named 'xx Chat Record.exe' first executes vbn.exe;
- vbn.exe simulates mouse click actions to make the Explorer program start adta.exe;
- The adta.exe program loads the libcef.dll file with malicious code;
- adta.exe injects malicious code into svchost execution.
Summary of techniques:
“Silver Fox” successfully constructs an entire 'white exploitation chain', thus easily bypassing the detection of antivirus main defense and EDR. Moreover, using the method of simulated mouse clicks to make Explorer execute is less likely to trace back to the original malicious process.
02 Substitute: Use Microsoft's official program to start the program and load malicious code
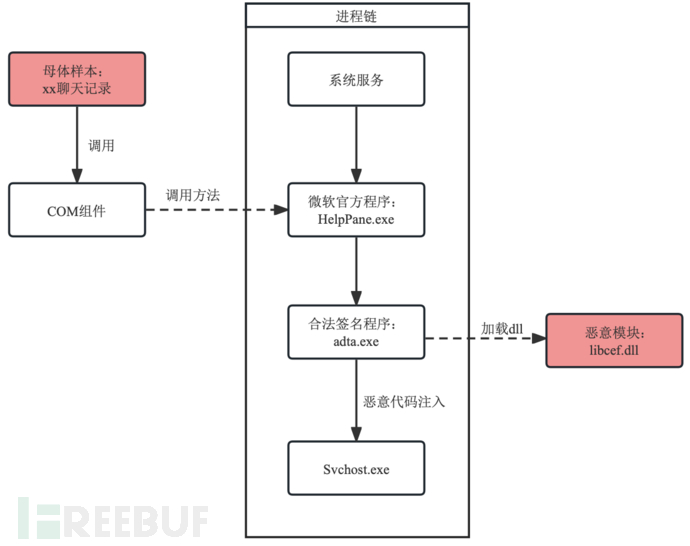
Similar to method 1, the disguised mother sample will also release three files:
- helpPane.exe is the help program provided by Microsoft officially;
- adta.exe is a stock software with a legitimate signature;
- libcef.dll is a malicious DLL file;
Different from method 1, it uses Microsoft's official program to replace the simulated mouse click program. After releasing the file, the mother sample will call the rare interface in the COM component, start the HelpPane.exe program independently through the operating system, and then execute the process similar to method 1, as shown in the figure below:
Summary of techniques:
Compared to method 1, method 2 replaces simulated mouse clicks with COM components, uses the operating system to start the HelpPane.exe program, constructs a 'legitimate' chain, and is more deceptive than the common process Explorer. Moreover, the method of using COM components is less likely to trace back to the original malicious process.
03 Deceive the World: Hidden Malicious Code in Images for Fileless Attacks
This is a common implementation of a fileless attack, with the mother program being a compiled program in Go language, which induces users to click and then the malicious program will first access C&C, download an image, and then load the image into memory. What users see is just an image (which does not affect the normal display of the image), but in fact, the attacker uses some algorithms to embed data into the image.
 The malicious code is hidden in the image downloaded after the reverse connection to C&C
The malicious code is hidden in the image downloaded after the reverse connection to C&C
After that, the Go language program will decrypt this image in memory, release the malicious code, and create a scheduled task to achieve boot-up startup.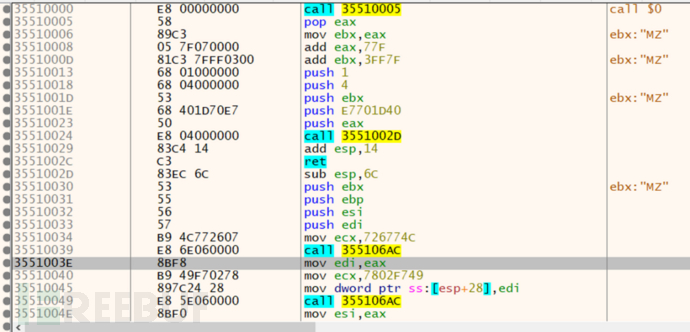
The process diagram of decrypting the malicious code caught in memory by Weibu
Summary of techniques:
Throughout the entire process, there is no malicious code in the Go language program, so antivirus software does not detect it; the malicious code is actually dynamically obtained from the downloaded images, and the entire process does not leave any malicious files on disk, all operations are completed in memory, successfully bypassing the vast majority of antivirus engines, and achieving the purpose of persistent and stable operation through scheduled tasks.
04 Hidden dangers: release malicious code from encrypted files in memory
The parent program uses signature forgery technology to disguise itself as a normal program. Although the signature of this program is invalid, because it does not contain malicious code or malicious features, most anti-virus software will not alarm. Running this program will release three files:
- AvSHpPsh.exe is an executable program without malicious code or features;
- Antikk.dll is a dll file without malicious code or features;
- xm.xml is an encrypted file.
The parent file will first execute the AvSHpPsh.exe program, load the Antikk.dll file, then decrypt the xm.xml file in memory, and execute the payload:
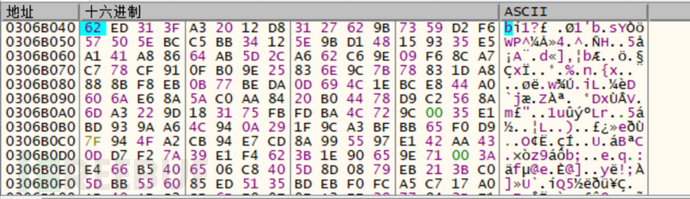 Unencrypted memory code
Unencrypted memory code
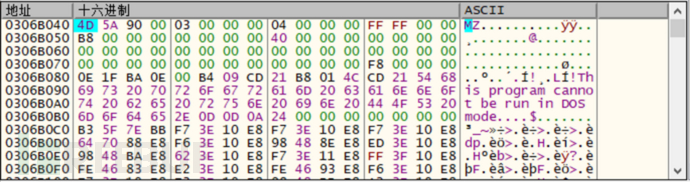 Decrypted memory code
Decrypted memory code
Summary of techniques:
In this attack technique, although the malicious code is locally stored, it is stored in an encrypted form and does not have any suspicious features, making it almost impossible for anti-virus software to detect. The AvSHpPsh.exe program loads and decrypts the malicious code in memory, which can also easily bypass anti-virus software and EDR.
It can be seen that the four bypass techniques used by the 'Silver Fox' gang are all very sophisticated. So how can they be cracked on the terminal?
# How to deal with 'Silver Fox' attacks by EDR # Let terminal security end at the terminal
In the analysis report published on March 27, micro-step announced the IOC and TTPs related to the 'Silver Fox' attack. This article approaches from the terminal perspective, using micro-step's terminal security platform OneSEC, to show the countermeasures for 'Silver Fox'.
From a preventive perspective, the four attack techniques of 'Silver Fox' can be divided into two categories:
The evasion techniques used by techniques one and two are all executed through methods such as伪装白利用, thereby bypassing the behavior detection of anti-virus software and most EDRs. OneSEC uses a two-stage detection method of single point + event, not only detecting behavior but also linking behaviors together for overall detection from the perspective of events. Although it looks 'legal' on the surface, due to its special execution chain and injection methods, it will be identified and detected by OneSEC. The detection chart is as follows:
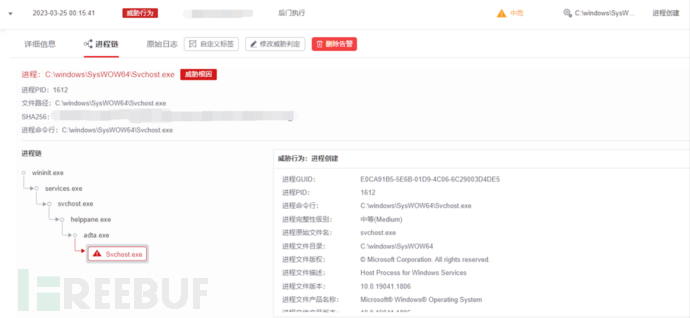 Silver Fox attack gang behavior detection chart
Silver Fox attack gang behavior detection chart
Technically speaking, techniques three and four utilize methods such as hiding malicious code in images and encrypting malicious files, but they all go through two stages: memory decryption and reflection loading. For these two types of attacks, OneSEC can effectively detect them by using a combination of IOA engine and memory scanning:
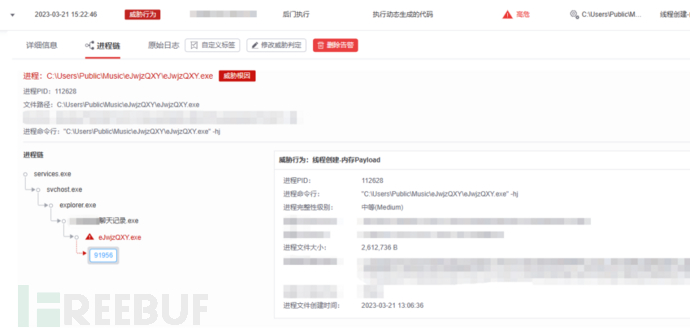
In fact, in addition to OneSEC, micro-steps' threat perception platform TDP, threat intelligence management platform TIP, threat intelligence cloud API, internet security access service OneDNS, and host threat detection and response platform OneEDR all support the detection of this attack event and gang.
评论已关闭