How can EDR break through fileless attacks that bypass anti-virus software?
In recent years, large-scale offensive and defensive exercises have been flourishing, with red and blue teams showcasing their unique skills in combat, and fileless attacks and other difficult-to-detect techniques becoming increasingly common. Sometimes, all it takes for the HR of a blue team to open a job applicant's resume, and the computer is hacked.

How can new attack methods that bypass traditional terminal security be captured, processed quickly and efficiently, and retain the important score of the blue team? The figure below is a detailed attack chain diagram captured by EDR within one minute after the attack.
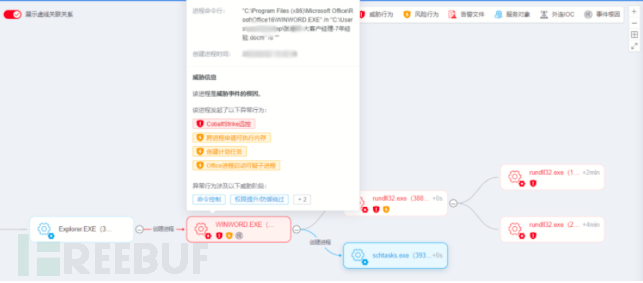
The threat detected in the figure above is the widespread CobaltStrike (CS horse) in various offensive and defensive exercises, which has affected a considerable number of security practitioners.
The biggest feature of fileless attacks is that the malicious code runs directly in memory. Some people might think: Can memory scanning detect malicious code?
The game between effective detection and performance consumption
So-called memory scanning is to match the memory data of running processes with known remote control, Shellcode, fileless attack frameworks, and other features to find malicious code and detect threats. Theoretically, memory scanning can indeed find malicious code. However, in practical application, it is not very useful. The reasons are two:
- Memory scanning consumes a lot of system resources: compared to file scanning, which faces KB or MB-level files, memory scanning usually faces GB-level memory data, which requires a lot of system resources, leading to slow response or lagging of the terminal;
- It is difficult to determine the timing of memory scanning: during the operation of the terminal, memory data is constantly changing. The memory features themselves may only appear stably at certain times, and early or late scanning may result in false positives; and, some malicious programs also use encrypted memory data to avoid scanning, decrypting data only at specific times to carry out attacks;
Theoretically, memory scanning can achieve comprehensive and zero死角 coverage of all monitoring points, which is technically feasible, but this will consume a lot of system resources, and almost no user will accept it. In combination with the characteristics of variable memory data, this means that it is no different from trying to find a needle in a haystack to detect malicious code solely through memory scanning. Is there really no way out?
From a large amount of practical experience, the behavior detection technology in EDR can not only effectively detect fileless attacks but can also be used to trigger and cooperate with memory scanning to achieve a 'multi-dimensional strike' on new threats such as fileless attacks.
EDR behavior detection makes fileless attacks invisible.
Behavior detection technology in EDR is different from the file detection technology of antivirus software. It focuses on detecting behaviors during the execution of programs/codes, including but not limited to process creation, driver loading, registry modification, disk access, memory access, and network connections. Compared with the behaviors generated by normal program execution, the behaviors generated by network attacks for purposes such as persistence, privilege escalation, and hiding against detection have obvious characteristics. Behavior detection technology is to collect and utilize these characteristics to detect threats. Although malicious code not yet written to disk cannot trigger the antivirus software's detection and killing capabilities, the malicious operations performed by the malicious code during execution are effectively recorded, analyzed, and captured by EDR. For example, attackers usually obtain credentials to perform persistence actions, and these actions will all be analyzed and captured by EDR.
With}}The fileless attack event in the previous articleFor example:
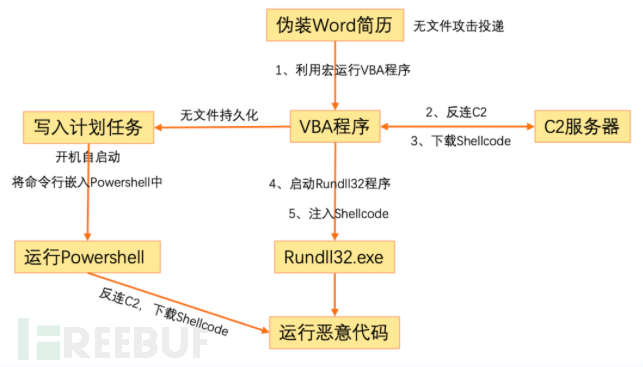
EDR can detect and associate a series of (risk) behaviors behind a single click:
- Secondly, during the startup process of Rundll32, the Office process performed a remote thread injection on Rundll32, forcibly
- In addition, the Office process also wrote a very suspicious scheduled task through macros, making the CS horse keep starting up, and the behavior of creating a scheduled task using powershell will also be accurately detected by EDR.
However, do you think that EDR is just like this? The advanced EDR behavior detection does not stop here.
Advanced EDR will not give up any technology, and it can also be combined with memory scanning technology:
Through a large number of real cases, it can be seen that in the face of those attack methods that directly run malicious code in memory, EDR behavior detection can capture the attack behavior after injection and accurately detect it, and can also start memory scanning when detecting risk behavior, making memory scanning 'aim where to strike'.
Therefore, in the case mentioned earlier, the process of Rundll32 performing remote thread injection, which is also the process of loading malicious code, as long as EDR can accurately capture this behavior, at this time, calling up memory scanning can detect the CS horse features in memory, and prove the original abnormal behavior as a solid fileless attack event.
Throughout the process, the combination of EDR behavior detection and memory scanning technology is used, from suspicious behavior to the final alarm, taking less than 1 minute.
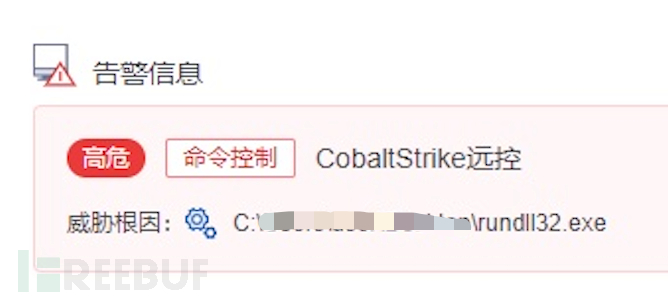
As long as there is network attack, there will be abnormal behaviors different from normal program operation. EDR is through recording and storing the behavior data of terminal systems, and using various data analysis technologies for screening to accurately detect unknown, new, and high-risk threats.
Moreover, EDR technology is not contradictory to antivirus software based on file detection technology. The two are not a 'choose one or the other' relationship, but a complementary and complementary relationship.
But for most enterprises, detection is not the ultimate goal; what is more important is response and disposal. How to trace and dispose of threats found through EDR? Please look forward to the next article.
评论已关闭