I. Event Summary
Recently, during the Windows terminal threat hunting, a Windows spyware was captured that spreads and distributes through crack software websites. After the victim clicks to run the malware, it will steal sensitive information such as account numbers, passwords, browsing history, cookies, desktop specific format files, installed application information, operating system information, and desktop screenshots from the victim's computer, encrypt and compress it in memory, and send it to the remote C2 server. At the same time, the analysis found that the malware author understands how to decompress and expand large files, memory loading, and uses AutoIT to counter online sandboxes & intelligence, local AV & EDR security protection mechanisms.
II. Event Analysis
0x01 Method of transmission
0. The victim accesses the software crack website to download Snagit crack software by searching for the keyword 'snagit 2024 key' on Google
1. Crack software download website https://trycracksetup.com/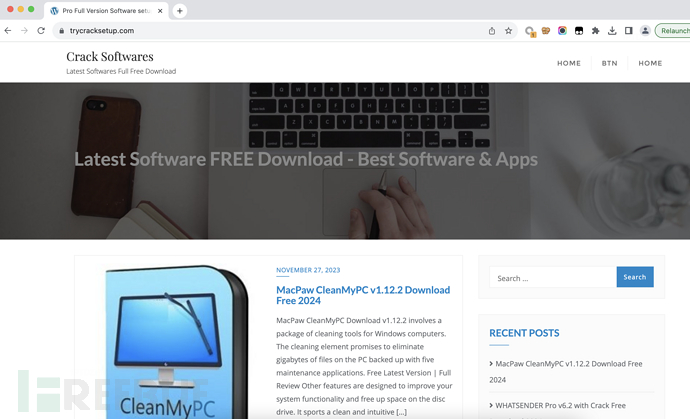
2. The downloaded crack software page
3. Click the download crack package button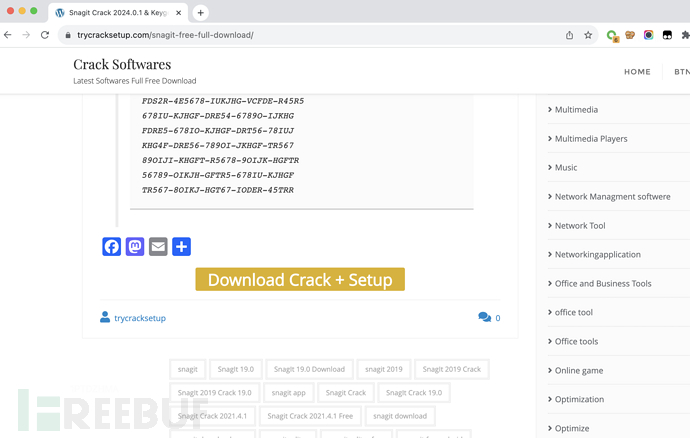
4. It will then jump to a randomly assigned download address page (the download address page that jumps each time you click the download crack package button is different)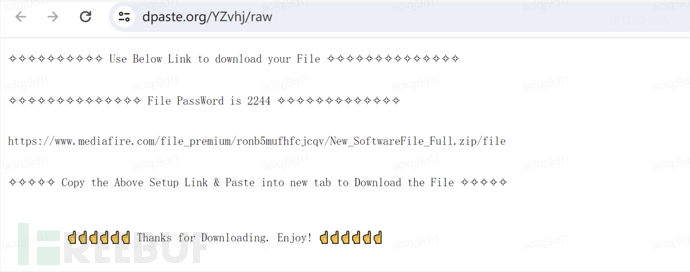
5. Access the mediafire drive link inside to download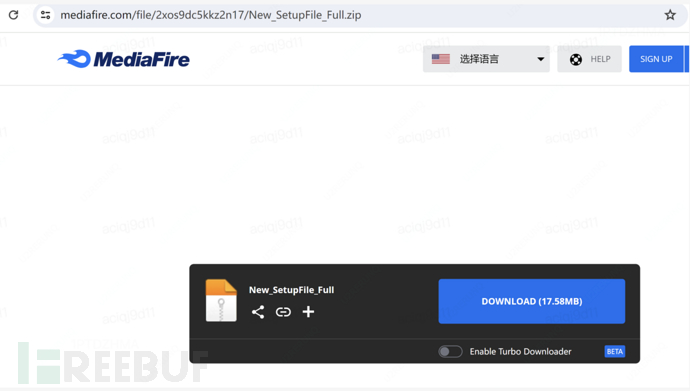
6. The downloaded file is a RAR compressed package, with a size of about 18MB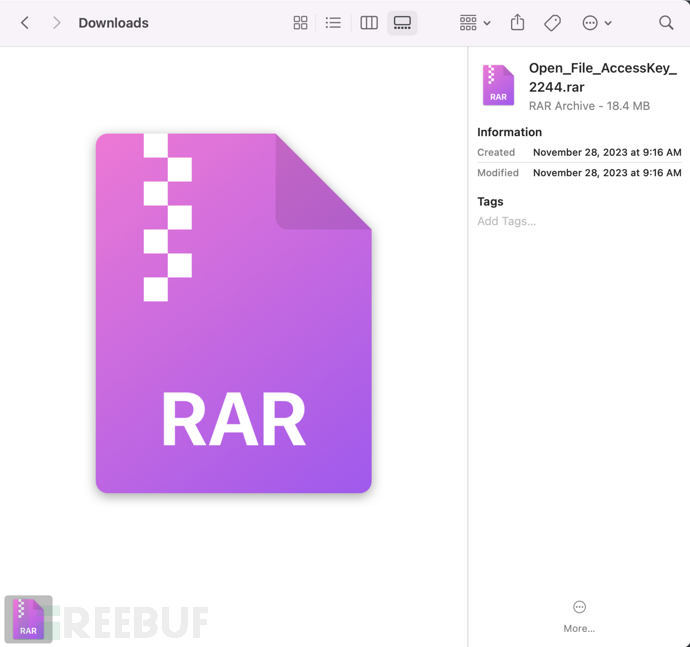
7. After entering the password to unzip, two files were released, one Note.txt, and one 715.9MB setup_x64_86.exe executable file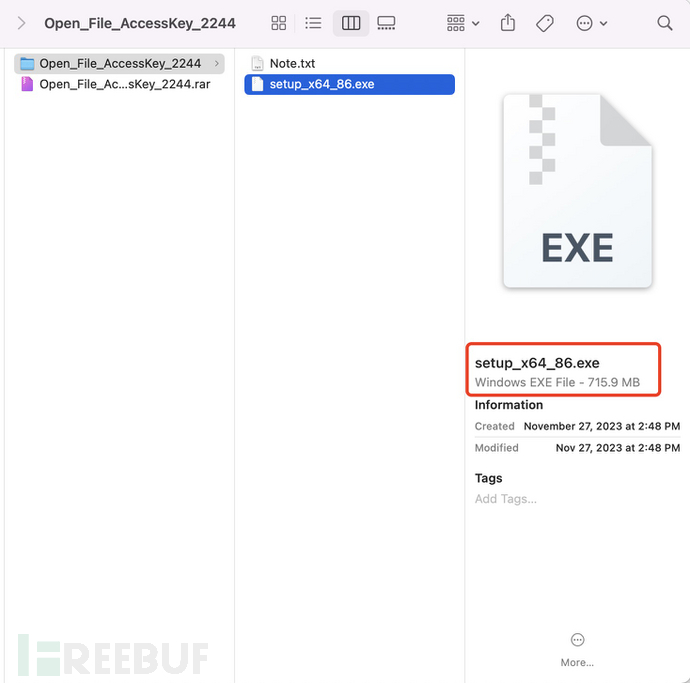
setup_x64_86.exe HASH INFO
MD5: 8BE7E723295D8EE67C973EB4AB51D763
SHA1: 705728719729924DA518C17894FC94719EA9F6EF
SHA256: AA9E931BFABC3ABDBA085C7FDFC64848EF281E9C2C631DEF4D3F4EFAE2CA2F82
SHA512: 62051780288D38483D42A237A8DAEFECAEE6326996E1174422C178CC171C1C0A6D266A049A753FAE2B0E8578B1616740F42C2CFB3874E8521460F7CFAA15BA2A
8. PE file is unsigned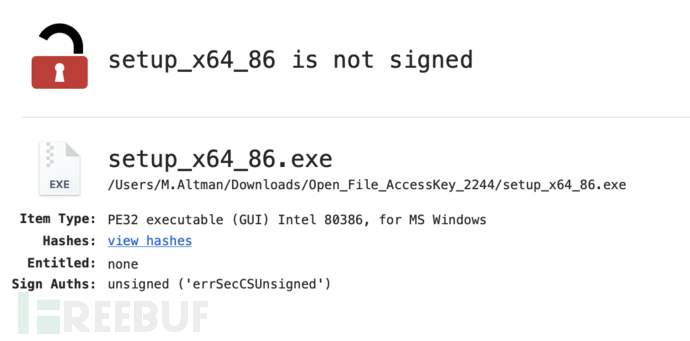
9. File related hash has no intelligence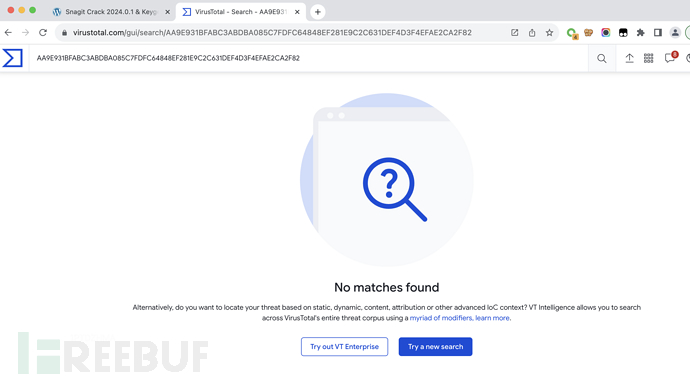
10. The maximum file that the sandbox allows to upload is 650MB, but this file is 715.9MB. The developer of the trojan used the method of decompressing and inflating large files to bypass the online sandbox dynamic behavior analysis and static intelligence query.
0x02 Behavior Analysis
Local dynamic analysis found that after running the trojan, it first checks whether it is running repeatedly. If the %AppData%/Xuginida directory exists, exit.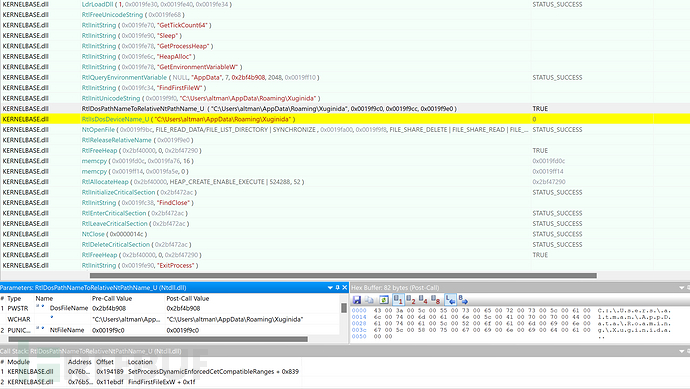
If the %AppData%/Xuginida directory does not exist, create the %AppData%/Xuginida directory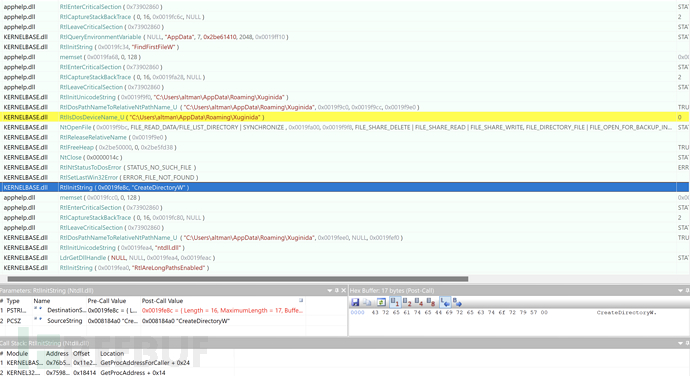
0x021 Obtain Screen Capture
After the environment detection is passed, the screen capture is obtained next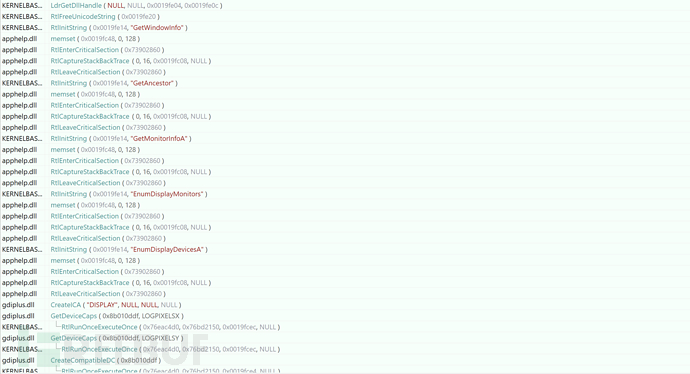
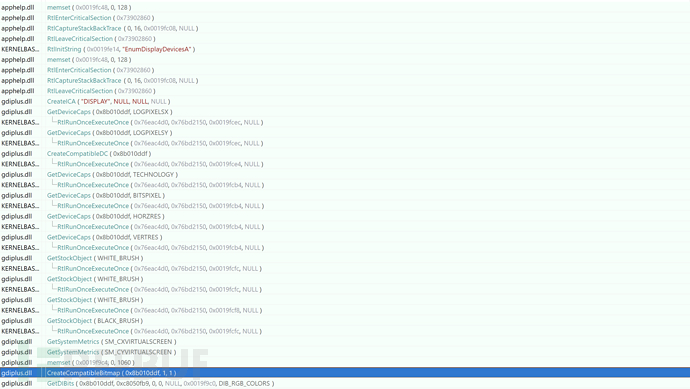
Name the obtained screenshot file as $SCREEN.JPEG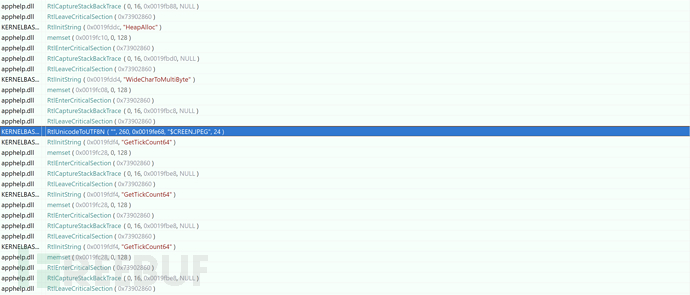
0x022 Obtain System Information
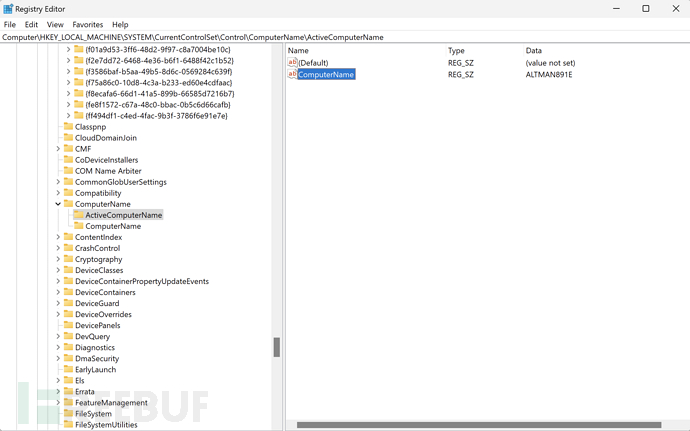
1. Obtain Computer Name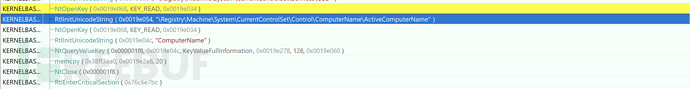
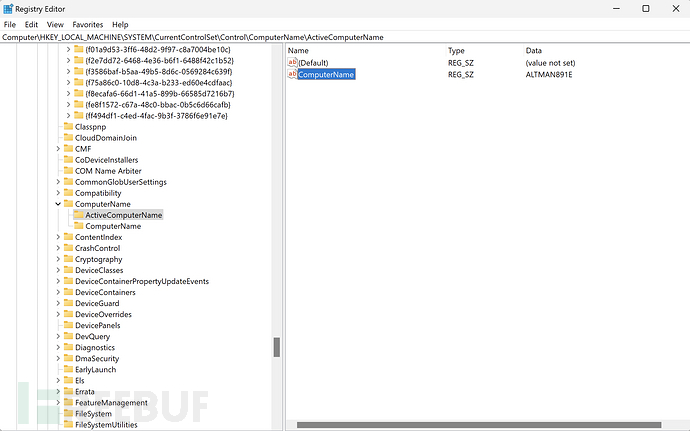
2. Obtain System Version Information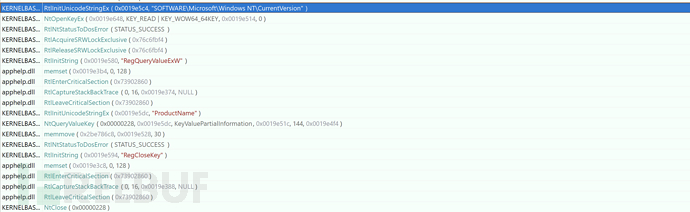
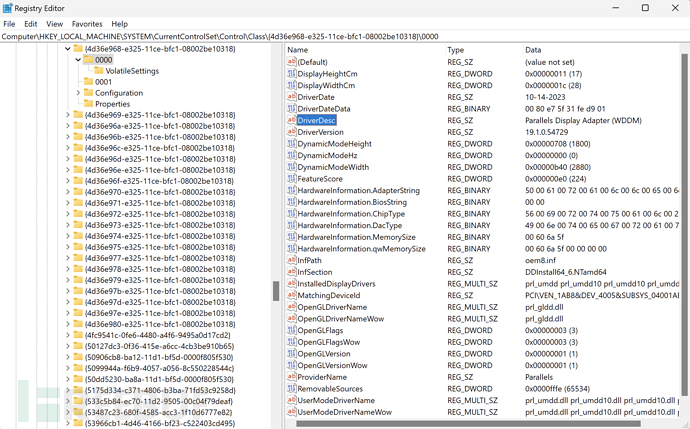
3. Obtain Description Information of Drivers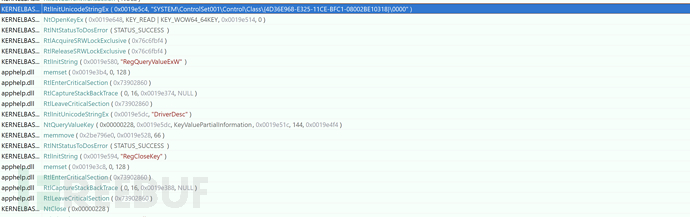
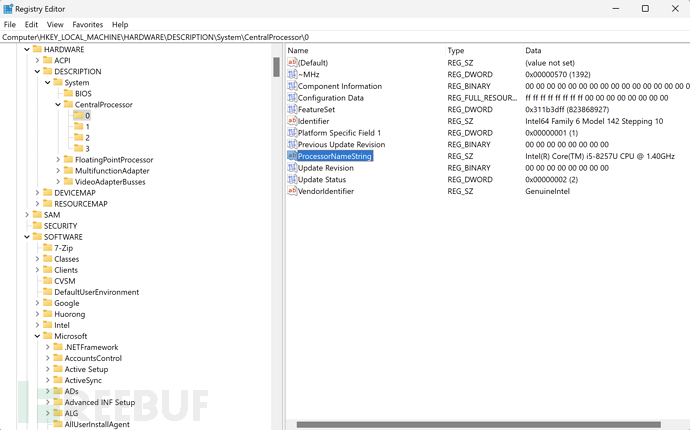
4. Obtain Processor Information of the Machine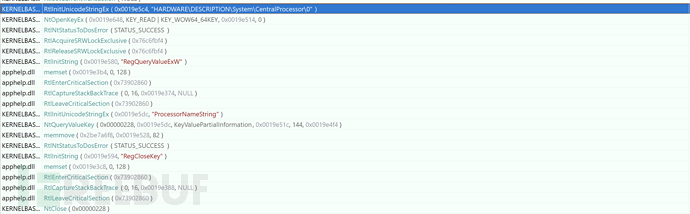
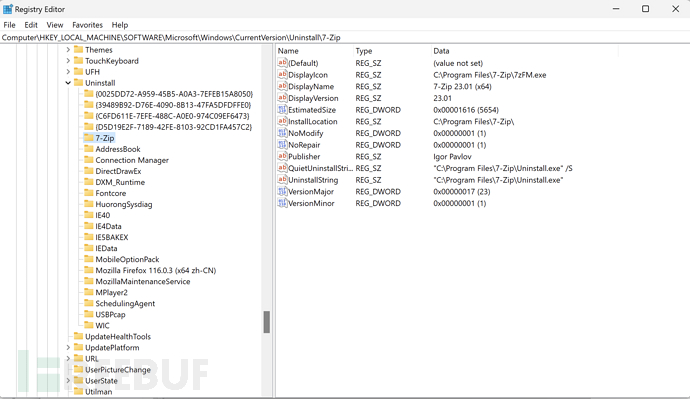
0x023 Obtain Applications Installed on the Computer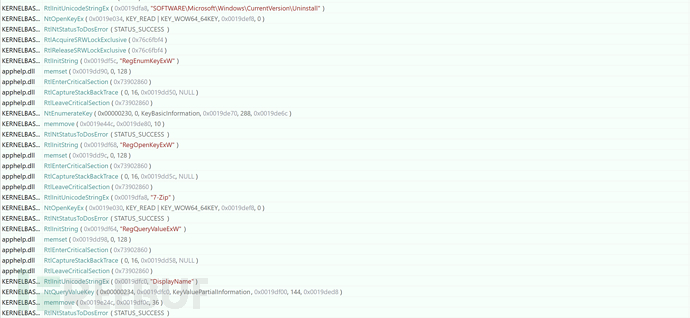
0x024 Obtain Sensitive Browser Information
1. Obtain Sensitive Configuration File of Chrome Browser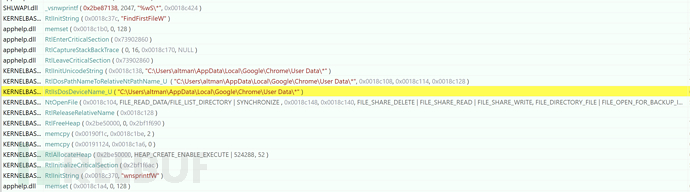
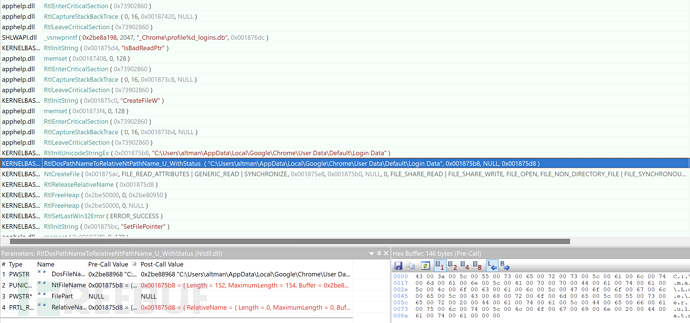
2. Obtain Sensitive Configuration File of Firefox Browser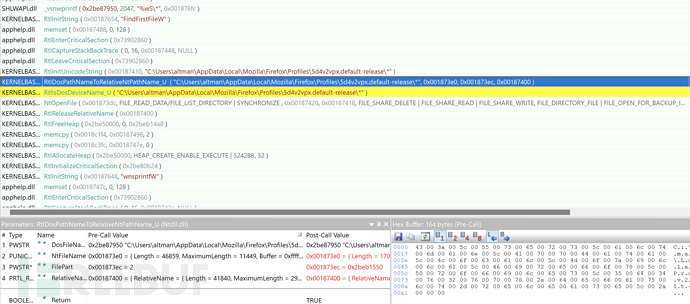
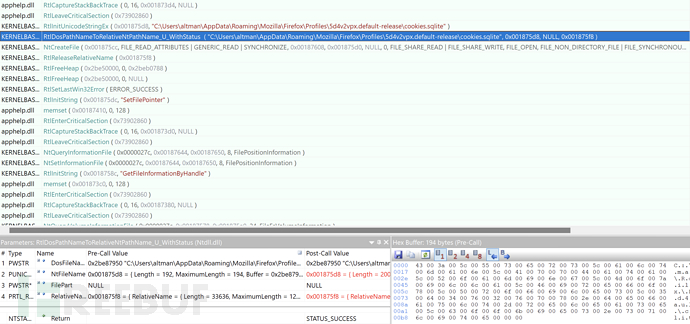
3. Obtain Sensitive Configuration File of Edge Browser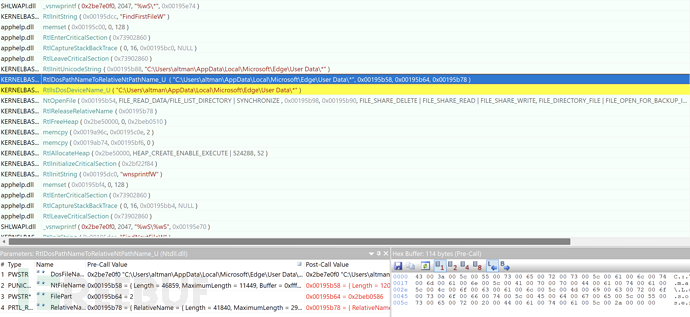
0x025 Obtain Files in Specific Format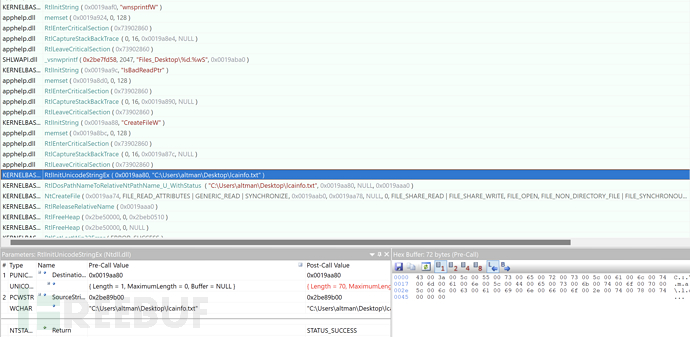
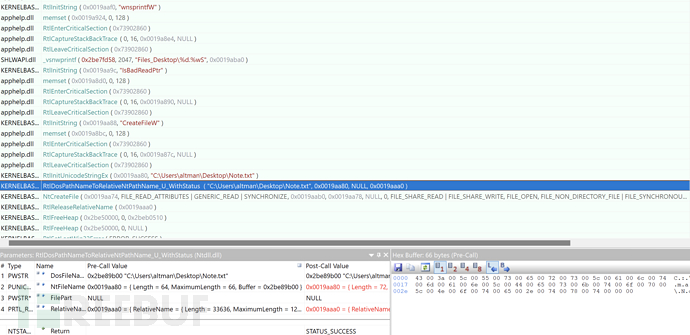
0x026 Send Out Stolen Sensitive Information
After stealing sensitive information, compress the stolen files in memory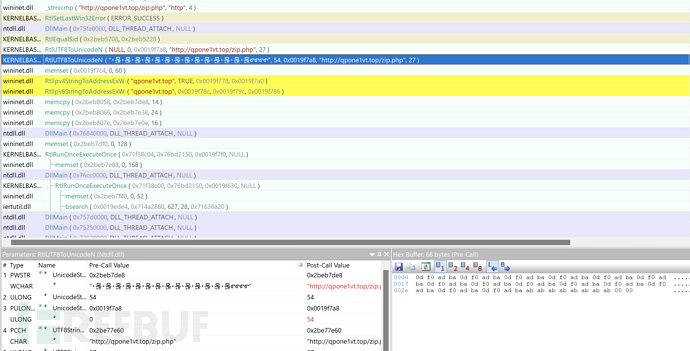
Send the compressed package of obtained sensitive information to qpone1vt.top/zip.php
Content of the Zip Compression Package Sent Out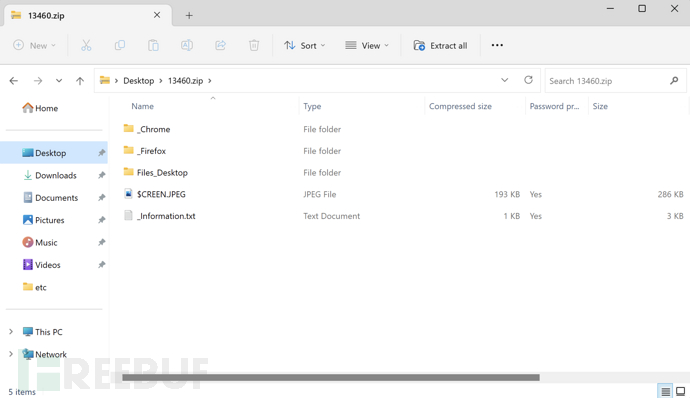
Chrome Browser Sensitive Configuration File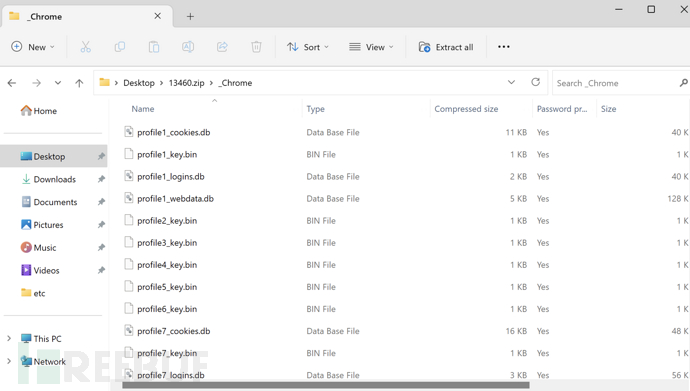
Firefox Browser Sensitive Configuration File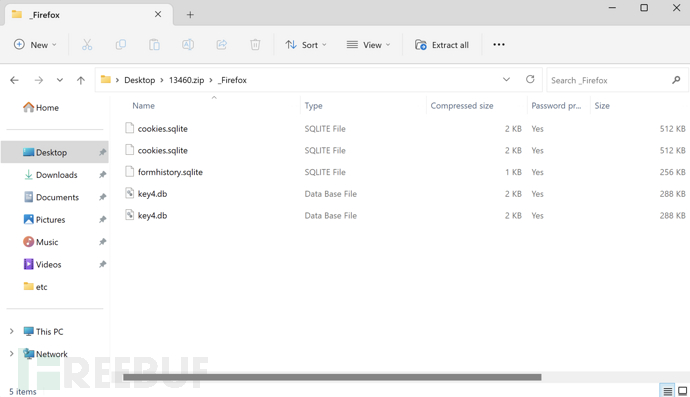
Obtained specific format files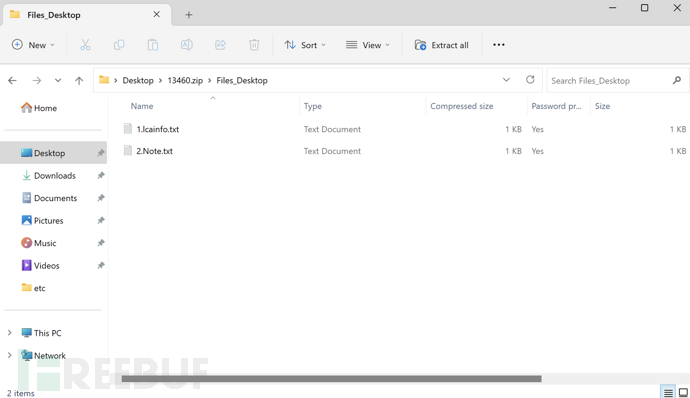
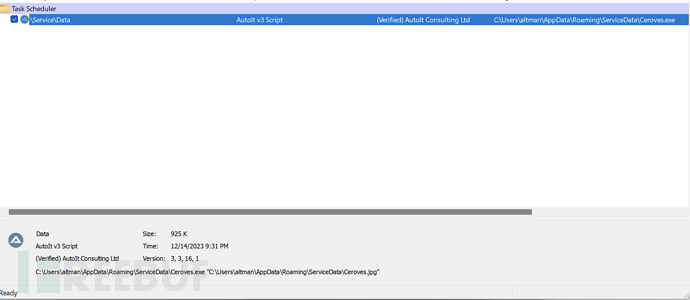
0x027 Create Task Scheduler to Maintain Permissions
Release the signed Ceroves.exe (AutoIT V3 script loader) and Ceroves.jpg (AutoIT V3 malicious script) to the %AppData%/Service/Data directory, and execute in a white + black memory manner to bypass the corresponding security mechanisms.
Ceroves.exe, an AutoIT V3 script loader with a legitimate signature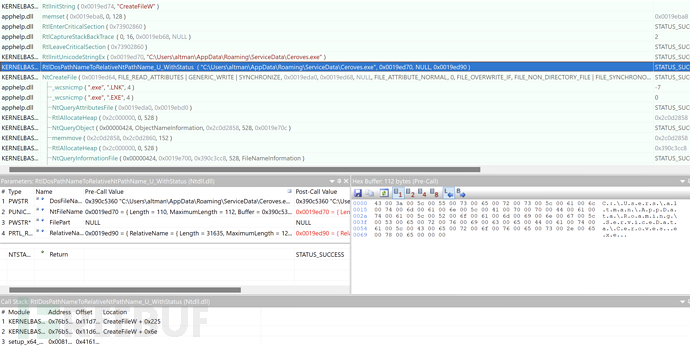
Ceroves.jpg, a malicious AutoIT V3 script after obfuscation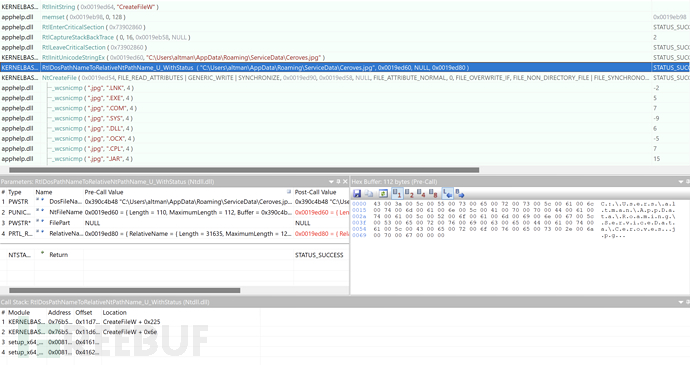
Task Scheduler File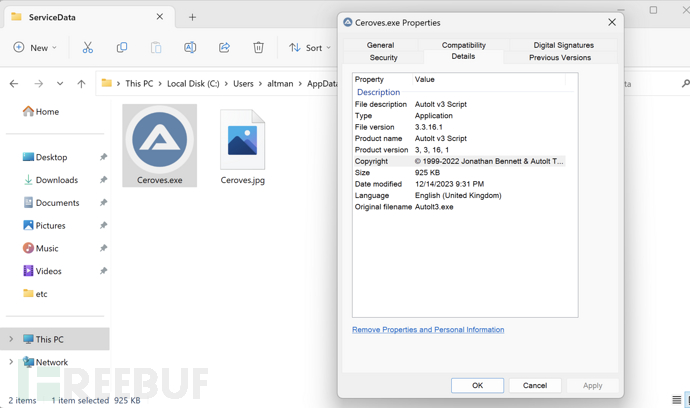
Create a task scheduler named /Service/Data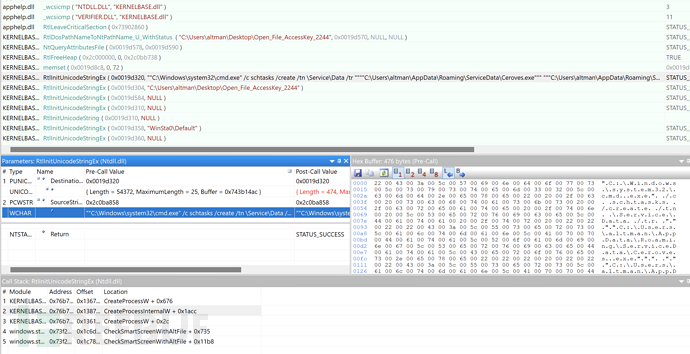
Task Scheduler Details: Running in a white-black memory loading method, undetected by 360, Huorong, and Defender security software throughout the process.
0x03 Behavior Detection
It should be noted that, at the time of writing this analysis article, the malware can still bypass the detection of 360, Huorong, and Defender, successfully stealing sensitive information from the victims' computers. The following lists several detection methods based on suspicious behavior dimensions for unknown threats.
1. Suspicious Firefox Sensitive Credentials Acquisition Behavior
2. Suspicious Edge Sensitive Credentials Acquisition Behavior
3. Suspicious Chrome Sensitive Credentials Acquisition Behavior
4. Suspicious Task Scheduler Creation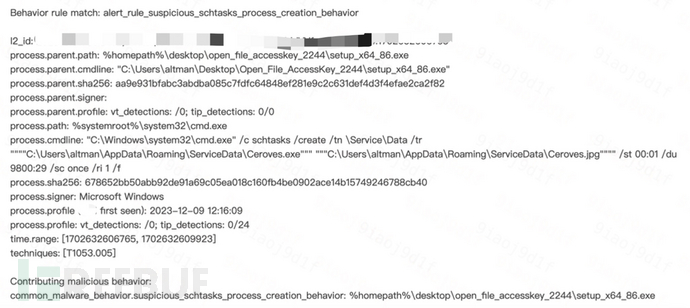
Chapter 3 - Event Summary
Reviewing this Windows spyware incident reveals that the essence of such security incidents is still a problem with the terminal software supply chain management. If corporate employees can obtain the required software within the corporate internal network, then it is highly likely that they will not go out to download and install cracked software provided by third-party untrusted sources. I think it is possible to target this terminal software supply chain poisoning risk scenario from the three aspects of before, during, and after the event.
Before the event: Establish the security baseline for office terminals, provide employees with a trusted official software download channel within the corporate internal network, regularly conduct safety risk awareness training for employees, and continuously improve the basic defense capability of office terminals and the safety awareness of employees;
During the event: Based on the ATT&CK framework, through attack simulation, data analysis, strategy development & optimization, continuously improve the threat awareness capability of office terminals;
After the event: Establish a rapid止血 SOP mechanism for emergency response, review mechanism, reward and punishment reporting system, and continuously improve the risk disposal capability of office terminals;
Chapter 4 - Appendices - IOC
C2&Malicious Domains
130.193.43.88:80
qpone1vt.top
https://trycracksetup.com/
https://profullversion.com/
SHA256
AA9E931BFABC3ABDBA085C7FDFC64848EF281E9C2C631DEF4D3F4EFAE2CA2F82
Analysis of macOS spyware, are you still dare to download cracked macOS software easily?
GuLoader malicious software downloader: from 'COVID-19' phishing to 'SF Express' phishing
Analysis of the Agent Tesla spyware disguised as a screen saver program
Analysis of MontysThree industrial espionage software
Analysis of the early StrelaStealer initial infection chain and Payload
评论已关闭