Overview
In the process of daily operation analysis, it is rare to analyze the logs of remote control software such as Sunflower and Todesk. Regarding these two software, the most common issues related to them in the daily operation analysis may be alerts of illegal software use, and in most cases, such software is prohibited in the internal network. Fortunately, I recently did a simple analysis of the Sunflower log, and this article will analyze the logs of these two common software. There is already an article on the platform.Todesk Log Analysis, which can be referred to by everyone, and this article also draws on the characteristics provided by this article for analysis.
Todesk
ToDesk is a multi-platform remote control software that supports cross-platform collaborative operations on mainstream operating systems such as Windows, Linux, Mac, Android, and iOS.

By default, the Todesk log files are stored in the Logs directory at the same level as the installation directory, in versions before 4.7, there are files starting with 'service' and 'client' in the directory. The 'service' files represent the logs of being remotely controlled by others, and the 'client' files represent the logs of remotely controlling others. In versions after 4.7 including 4.7, there are no files starting with 'client' in the directory.
v4.6.2.3 Log Directory Structure VS v4.7.0.2 Log Directory Structure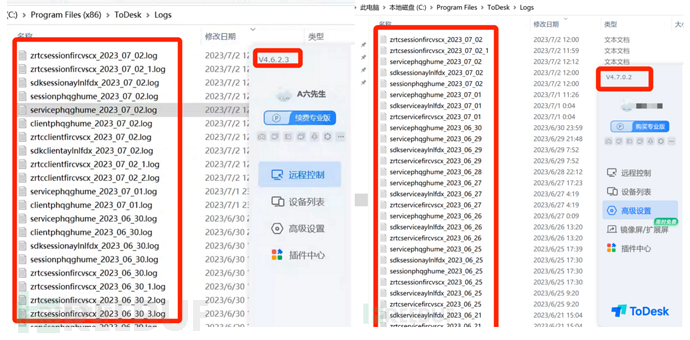
v4.6 Log Analysis
The log analysis of versions before v4.7 can be referred to in this articleTodesk Log AnalysisAnalysis.
Remote control of other hosts from the local host
Search for the log behavior of this machine remotely controlling other hosts through the client log. Match the keyword 'Room createMuxRoom server'.
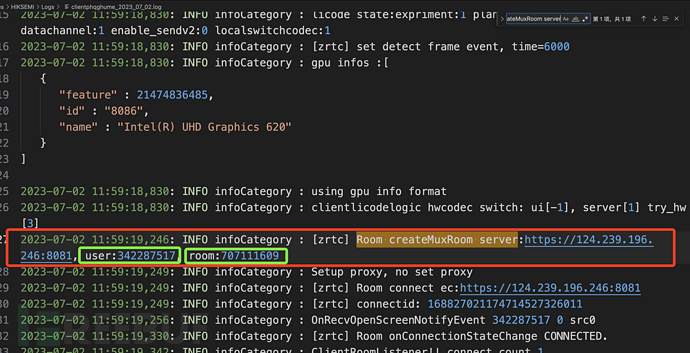
where user represents the code of this device, and room represents the code of the remote control device.
Match the keyword 'Upnp stop' to find the records of closed links.
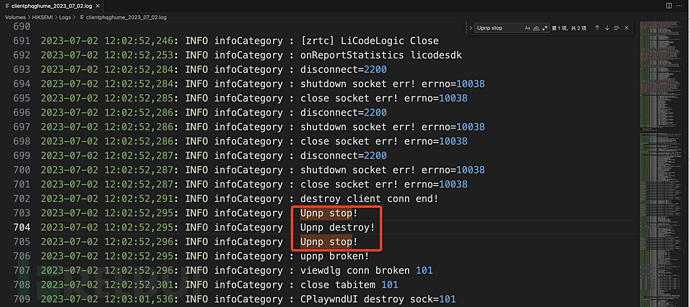
Record of this machine being remotely controlled by other hosts
By matching the keyword 'tcp begin connect' in the server log, you can see the remote connection records and the IP address of the other end. The IP address with port 443 can be ignored as it is the official server address.
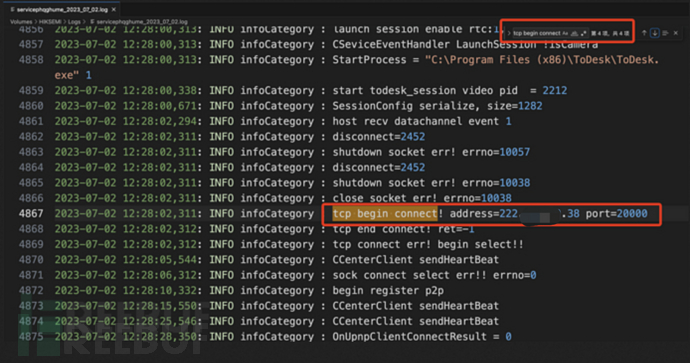
The log above shows the connection records of the port 20000. By reverse lookup of the address, we can confirm that it is the address of the remote host we are connected to.
Log analysis of v4.7
There are no log files starting with 'client' in the log directory of v4.7, so we directly analyze the server log.
Remote control of other hosts from the local host
Since there is no client log, the method mentioned in v4.6 does not apply in v4.7. You can match the keyword 'client recv connect request,' in the log.
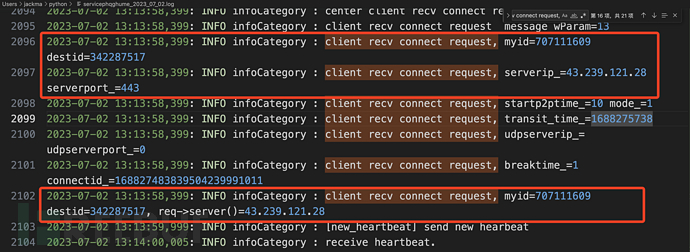
myid represents the code of this device, and destid represents the code of the remote control device.
Record of this machine being remotely controlled by other hosts
The method of searching for the remote control records of this machine by other hosts in the server log is consistent with that in v4.6. Similarly, by matching the keyword 'tcp begin connect', you can see the remote connection records and the IP address of the other end. The IP address with port 443 can be ignored as it is the official server address.
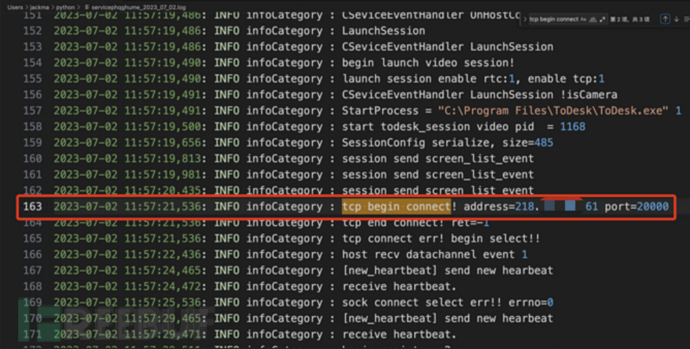
The log above shows the connection records of the port 20000. By reverse lookup of the address, we can confirm that it is the address of the remote host we are connected to.
Sunflower
Sunflower remote control software is a remote control software with many years of remote control technology experience, which can remotely control mobile phones, remote desktop connections, remote boot, remote management, and provide enterprise remote office, enterprise IT operations and maintenance, technical support, and other enterprise remote solutions in various industries.
V 13.3 Log Analysis
Remote control of other hosts from the local host
For the log analysis of sunflower, it can be combined with【Sunflower Remote Control】Local Extraction of Connection Log Analysis + Phone Number ExtractionFor reference and learning. Since the opportunity to use sunflower is less in daily life, the analysis of the log of the latest version of sunflower is directly carried out.
Analysis of the control end log
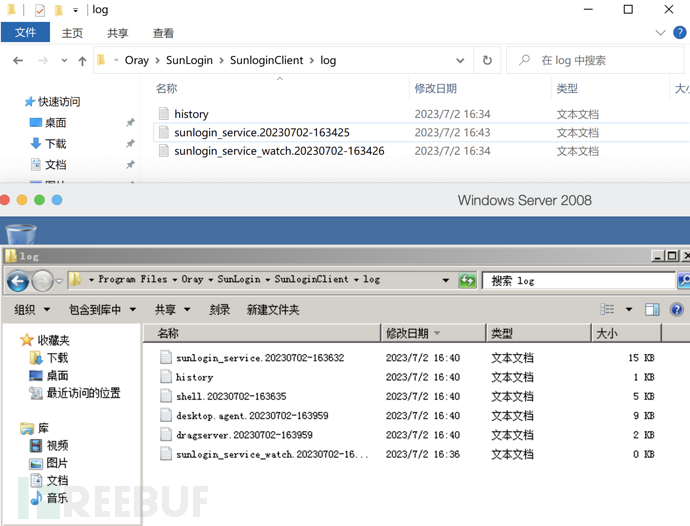
The figure above shows the directory structure of the local control end log and the controlled end log files. First, analyze the local control end log files (named with sunlogin_service.+time):
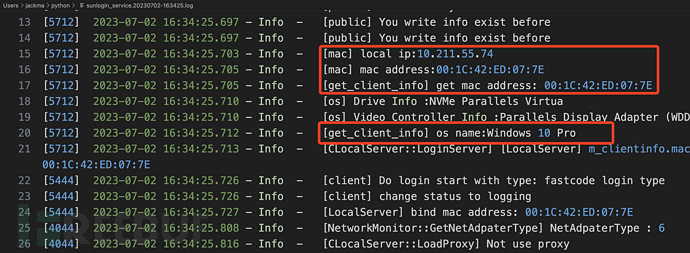
Firstly, the IP information, MAC address, operating system information, and other information of the current host.
Secondly, login success:
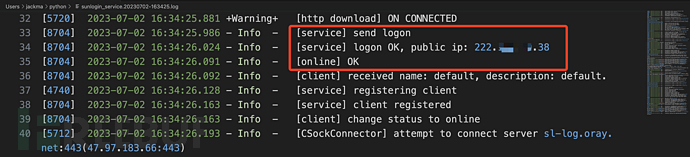
There are also some network connection behaviors in the local control end log, such as port 443, which is mostly the resolution address of some sunflower website domain names. I did not find any valuable information in the local control end log. If you have more discoveries, you can also send me a private message.
Analysis of the controlled end log
Compared with the control end log, the controlled end log is more abundant, starting with the directory structure, as follows:
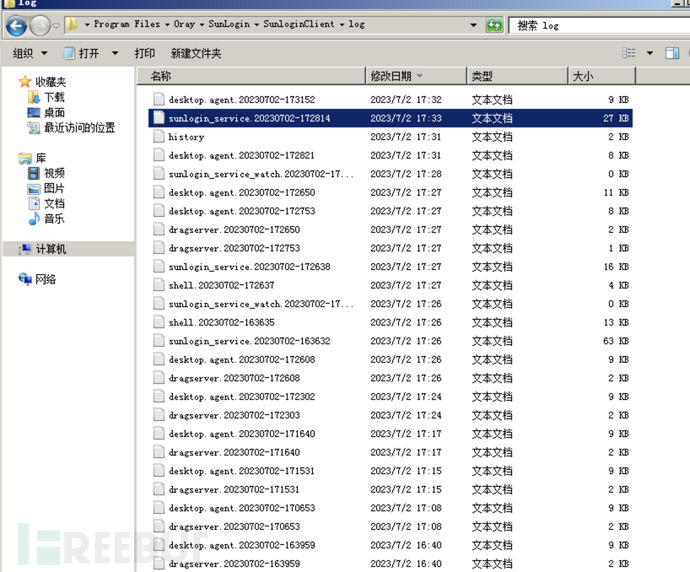
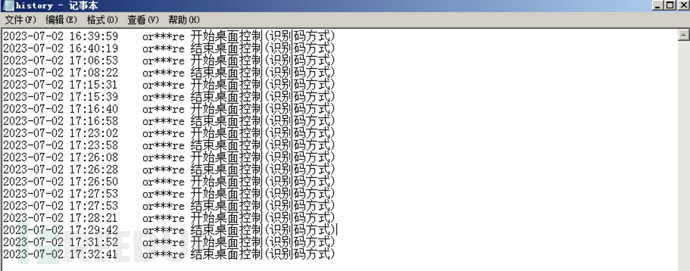
It is recommended to pay attention to files named with sunlogin_service.+time and history files. First, look at the history file, which records the time and connection method (identifier) of the remote connection. It is very important to locate the time node in the daily analysis process.
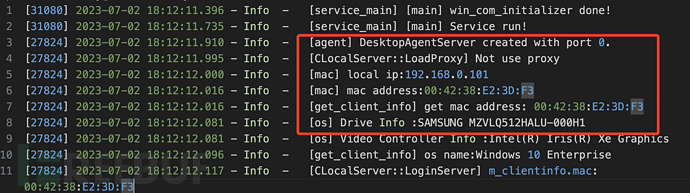
Next are files named with sunlogin_service.+time, which are also used to obtain local IP, MAC, hostname, and other information:
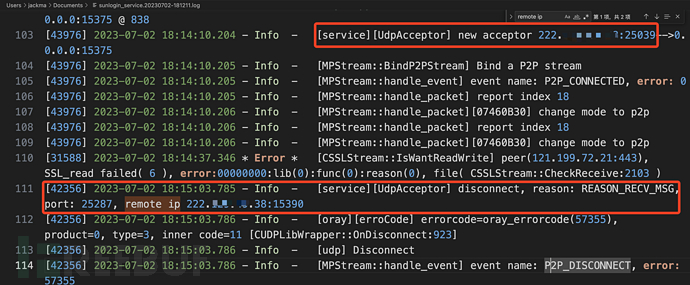
Directly matching 'remote ip' in the original log can see the control end's host exit IP address.
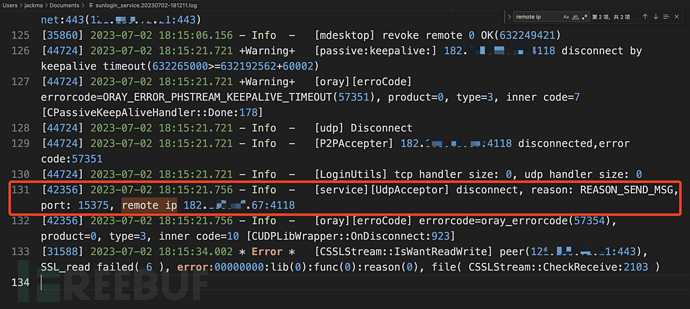
The IP address of the port 4118 is the resolution address of the sunflower-related domain name, which can be ignored. If you are not sure, you can use the IP resolution domain function of the intelligence platform for confirmation.
Summary
In the daily analysis process, it is possible to analyze and locate anomalies by combining the above features. At the same time, attention should be paid to the changes in log between different versions. The log format is not immutable. It can also be extracted by simulating various common scenarios. After all,Practice is the only criterion for testing truth.If you have a better method or idea, please send me a private message.
Reference
https://www.freebuf.com/articles/endpoint/363274.html
https://zhuanlan.zhihu.com/p/558745599?utm_id=0
Follow the Cybersecurity Medicine Water Brother to fight the target field (emergency response)
Analysis of macOS spyware, are you still dare to download cracked macOS software easily?
Analysis of MontysThree industrial espionage software
How to use SystemInformer to monitor system resources, debug software, and detect malware
Emergency response of the Windows system from the perspective of permission maintenance
Analysis of Windows spyware, will you still easily download Windows crack software?
评论已关闭