From the first appearance of the StrelaStealer malware in 2022 to the present, the threat actors behind StrelaStealer have initiated multiple large-scale email attack campaigns, and there is no sign of slowing down at present.
The StrelaStealer malware can steal email login data from mainstream email clients and send it back to the threat actors' C2 server. Once the attack is successful, the threat actors will be able to access the target users' email login information and perform the next threat operations based on this information.


Recently, the security researchers at Unit 24 have once again discovered a series of large-scale malicious activities related to StrelaStealer, in which more than 100 organizations in the European Union and North America were affected to varying degrees. In this series of activities, threat actors used spam emails containing malicious attachments, which ultimately executed the StrelaStealer DLL Payload on the target users' devices.
To successfully bypass security detection, threat actors will continuously modify the file format of malicious attachments in emails to evade security detection mechanisms based on signatures and patterns. In addition, threat actors will also use more advanced and complex obfuscation and anti-analysis techniques to update the DLL Payload, which greatly increases the difficulty for security personnel to analyze it.
This article will delve into the technical evolution strategies of the StrelaStealer malware from the beginning of 2024 to the present, as well as the related attack timeline.
About StrelaStealer
On November 8, 2022, DCSO_CyTec published a blog post about StrelaStealer on Medium, which was the first time the StrelaStealer malware was exposed to the public. StrelaStealer is an email credential stealing malware, since its appearance, the threat actors behind StrelaStealer have launched multiple large-scale email malicious activities, targeting users usually located in the European Union and North America.
The last large-scale malicious activity of StrelaStealer occurred around November 2023, and in late January 2024, they launched a new activity targeting multiple industries in the European Union and North America.
In the related activities, the basic target of StrelaStealer has not changed much, and the DLL Payload can still be identified through strela. However, the threat actors have been continuously updating the StrelaStealer malware to try to evade security detection.
The new variant versions of StrelaStealer can now be distributed through a compressed JScript, and updated obfuscation techniques are used in its DLL Payload. This article will also provide more relevant technical analysis and details.
The last large-scale malicious activity in 2023
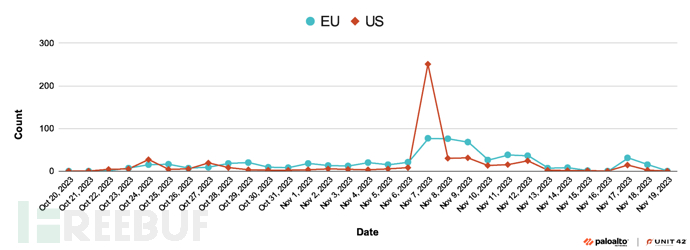
Since the appearance of StrelaStealer, researchers have observed that its threat actors have launched multiple large-scale malicious activities. According to the findings of WildFire researchers, the last large-scale malicious activity of StrelaStealer malware in 2023 occurred in November, with the main targets being organizations in North America and the European Union. The following figure shows the timeline of this malicious activity in November 2023:
The latest large-scale malicious activity in early 2024
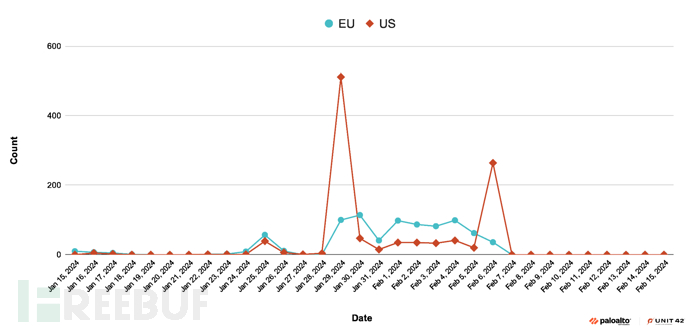
In January 2024, the threat actor behind StrelaStealer launched another large-scale malicious activity, targeting organizations in the same geographic region. The following figure shows the timeline of attack activities around January 29, 2024 (reaching the peak of attacks around the 29th):
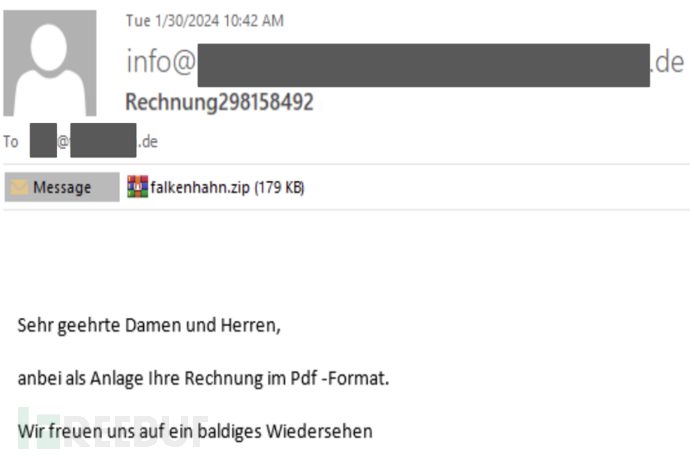
Among them, the StrelaStealer spam uses localized languages customized for the target, and the email subject uses the pattern "Factura/Rechnung/invoice####" (related to financial invoices). The following figure shows an example of spam in the German version:
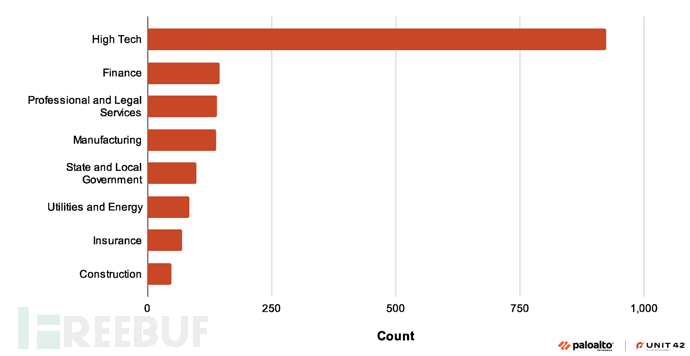
Although the recent large-scale malicious activity seems to target a wider range of industries, organizations in the high-tech industry have always been the main target of StrelaStealer. The following figure shows the top eight industries with the most frequent attacks by StrelaStealer samples:
Technical analysis of the new StrelaStealer variant
Analysis of the early StrelaStealer initial infection chain and Payload
Early versions of StrelaStealer mainly infected target systems through malicious emails with .iso file attachments. These malicious .iso files contained an .lnk file and an HTML file, and this technology took advantage of multilingual files, which could perform different processing operations according to the execution application scenario and context.
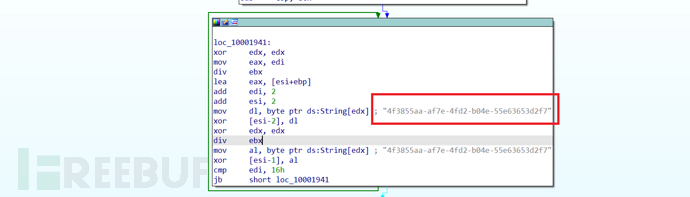
When the target user clicks the .lnk file in the .iso file, the HTML file will be executed immediately, and rundll32.exe will be called to execute the embedded StrelaStealer Payload. The initial Payload will contain some encrypted strings, which will be decrypted using a fixed XOR key during execution. The decryption key is shown in the figure below:
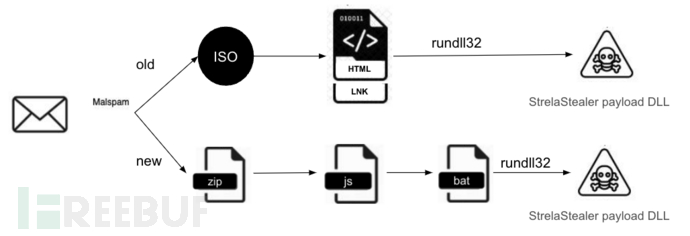
Updated StrelaStealer infection chain
The current version of StrelaStealer can be spread through phishing emails containing ZIP file attachments. Once the target user downloads and opens the compressed file, the target system will be infected with a JScript file.
Next, this JScript file will download a Base64 encrypted file and a batch file. The Base64 encrypted file will be decoded using the certutil -f decode command, and finally create a PE DLL file. Depending on the specific user permissions, the file will either be stored in the %appdata%\temp path on the local disk or stored in the c:\temp folder. Next, the malicious software will use rundll32.exe to execute the DLL file through the exported hello function.
The following figure shows the comparison of the infection chain of different versions of StrelaStealer:
Updated encapsulator
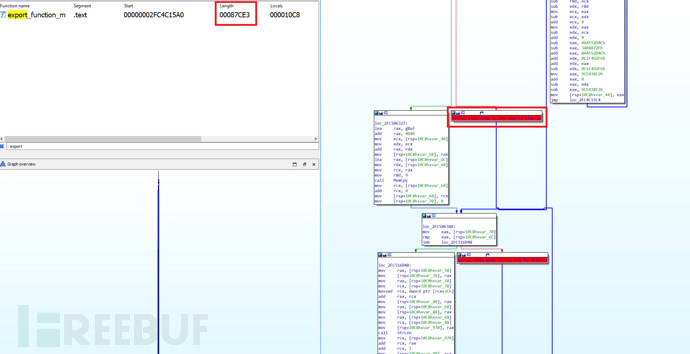
In the latest StrelaStealer samples observed in January 2024, the encapsulator has been significantly updated and has adopted a control flow obfuscation technique to increase the difficulty of security analysis.
The initial function shown in the figure below contains a very long code block composed of a large number of arithmetic instructions, which is the control flow obfuscation technology implemented by the latest StrelaStealer sample, and this reverse engineering technology may cause the sample to execute out of time in the sandbox environment:
But whether it is the new version or the old version of the StrelaStealer sample, their Payload are DLL files with malicious export functions and can execute attacks. The following figure shows a comparison of the malicious export functions of the DLL Payload of the new and old version samples:
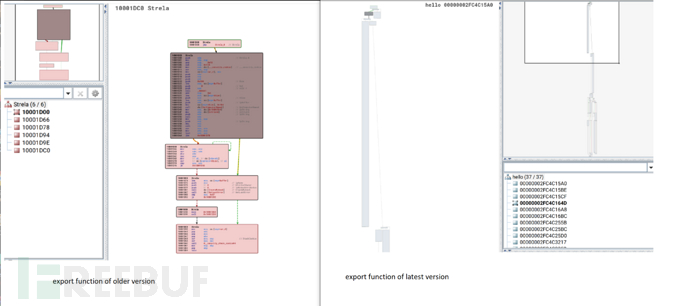
We can clearly see that the obfuscation level of the old version of StrelaStealer (on the left side of the top image) is actually not high, as these function code blocks are still readable after disassembly. However, the new version of StrelaStealer (on the right side of the top image) uses control flow obfuscation techniques to evade security analysis and detection.
StrelaStealer will also use Payload size and decryption key to decrypt the Payload. The decrypted Payload is a PE file mapped in memory, which is very different from the PE files in the early versions of StrelaStealer. The following figure shows the encrypted Payload:
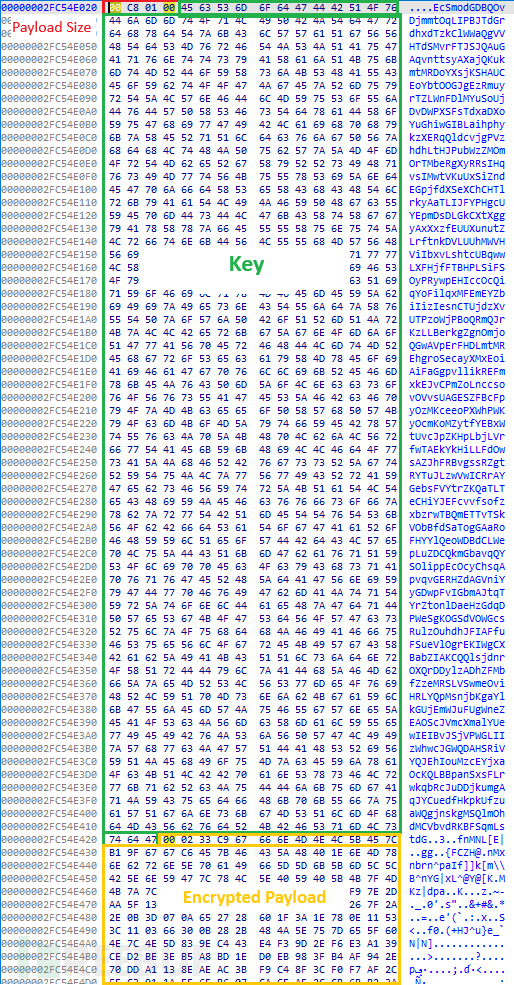
After decrypting the Payload, we will see strings like strela, server.php, key4.db, and login.json, which also indicates that the Payload is related to StrelaStealer.
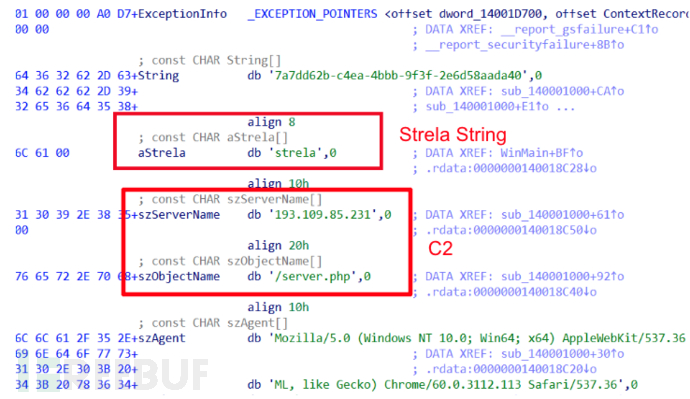
The main purpose of StrelaStealer is to steal email login data from mainstream email clients and send it to the C2 server defined in the malware configuration. The following figure shows the StrelaStealer string and C2 server name information:
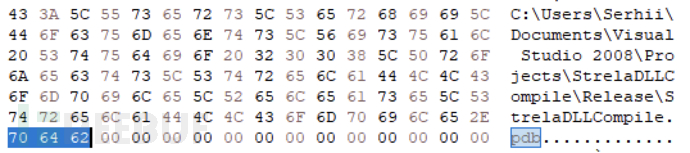
The threat actors of StrelaStealer have introduced many technical upgrades and modifications, which are very likely to be in order to evade security detection and analysis. For example, the PDB string (a compiler-built-in debugging symbol string) that existed in the early versions of StrelaStealer is no longer found in the latest activity samples, which also increases the stealthiness of the StrelaStealer binary file. The following figure shows the PDB string of an early StrelaStealer sample:
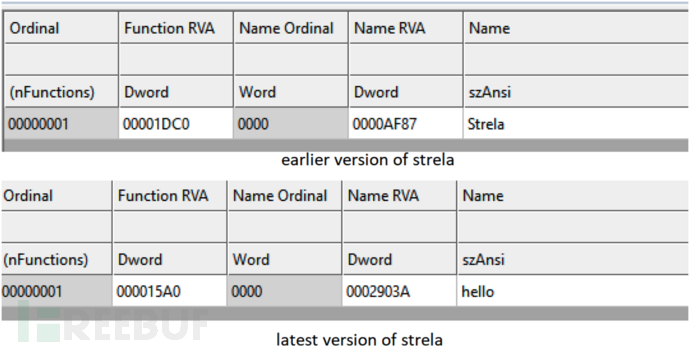
The following figure shows that StrelaStealer has changed the export name from Strela to hello:
Summary
StrelaStealer is an active email credential stealing malware that evolves and improves continuously. With each wave of new large-scale malicious email campaigns, threat actors update the email attachments and DLL Payload of their initial infection chain to better evade security detection.
Information stealing malware has always been a threat to user data security. The various obfuscation techniques and updates adopted by StrelaStealer are not particularly novel, but they are still an effective method for signature change and detection evasion.
References
https://learn.microsoft.com/en-us/windows-server/administration/windows-commands/certutil#-decode
Reference links
评论已关闭