Recently, AsiaInfo Security intercepted a new variant of the Maze ransomware. What is different about this virus is that after encrypting the data, it will loop the recording of encrypted files to notify the victim that they have been infected with ransomware. AsiaInfo Security named it Ransom.Win32.MAZE.E.
The Maze ransomware, also known as ChaCha ransomware, first appeared in May 2019. Due to its continuous activity, AsiaInfo Security has been tracking the dynamics of this ransomware. We found that it has been particularly active this month with frequent updates. In the early stages, the virus mainly used exploit toolkits such as Fallout and Spelevo to spread through web hijacking or through fake websites伪装 as legitimate cryptocurrency exchange applications.

The latest in-the-wild sample we intercepted is a lure document titled RSA SecurID (named Trojan.W97M.DEDEX.S by AsiaInfo Security), which spreads malicious macro code. The document诱导 victims to run the file and activate the macro code. The macro code reads data from forms, then parses it, and its main function is to download the main body file of the Maze ransomware. For different variants, the download address and file name of the ransomware body will change. After running the downloaded Maze ransomware, it will encrypt the data in the system. After completing the encryption, the virus will not delete itself but will loop the recording of encrypted files to notify the victim that they have been infected with ransomware.
Detailed analysis of the virus
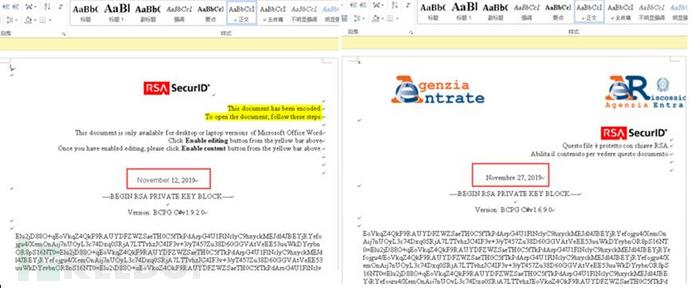
TitleRSA SecurIDBait document analysis
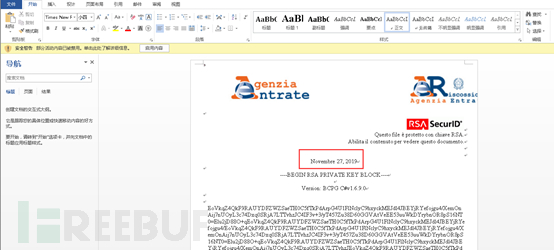
[Bait document with the title RSA SecurID]
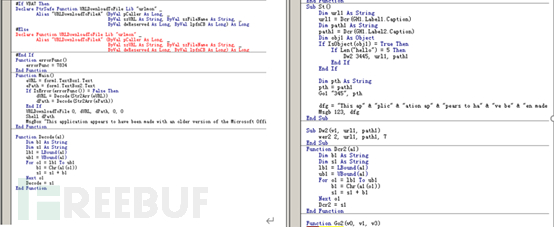
Read the data in the form, download and execute the maze ransomware main file:
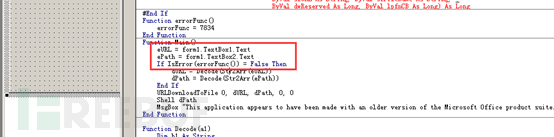
The data in the form is as follows:
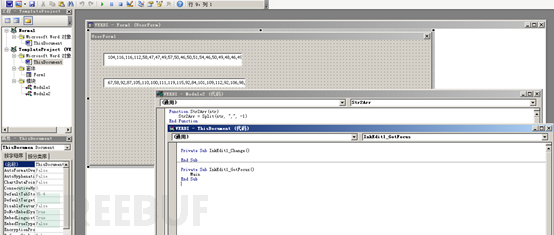
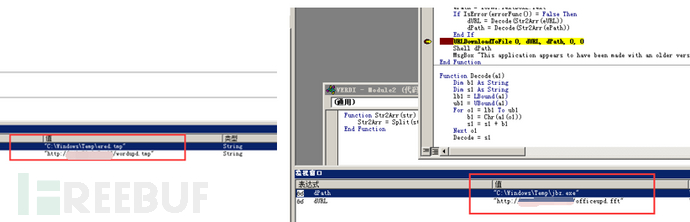
Through debugging, the macro code decrypts the data in the form, then downloads and executes the main file of the maze ransomware from the remote server hxxp://192.xxx.210.xxx/officeupd.fft to C:\Windows\Temp\jbz.exe, and then executes the malicious program as shown below:
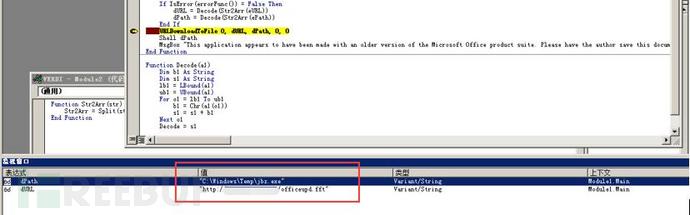
Sample comparative analysis
Bait documents of different variants with the title RSA SecurID, whose content is different:
The download address and name of the ransomware main file also change:
The malicious macro code in the document also changes, but the overall program flow is still the same:
Ransomware main fileofficeupd.fftAnalysis
The ransomware main file decrypts and executes the real ransomware payload in memory through an outer shell program:
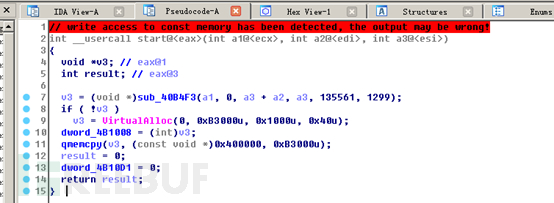
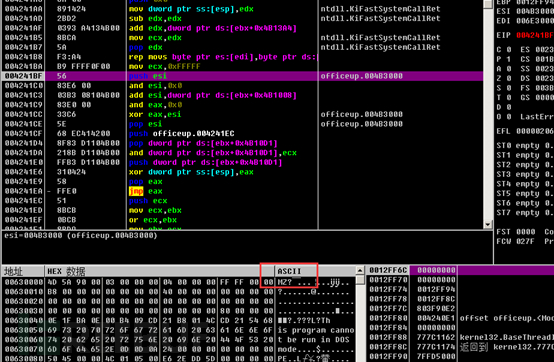
Then jump to the entry point to execute the core code:
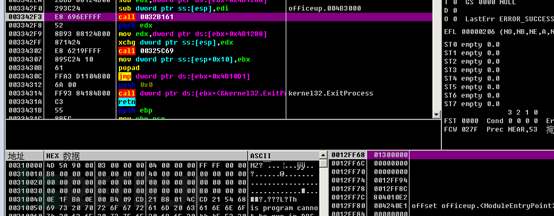
After encrypting the files, the system volume shadow copy information will also be deleted:
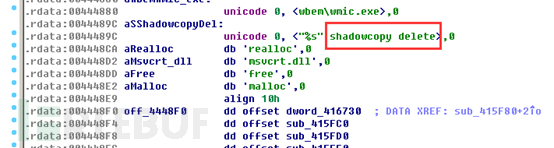
The file extension of the encrypted files by this ransomware is a random file name:
After encrypting the files, the desktop background image will be modified:
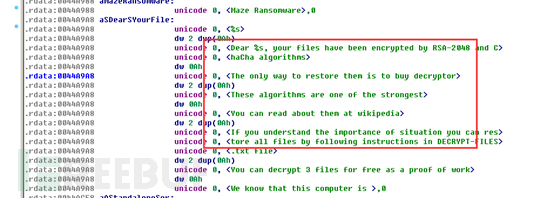
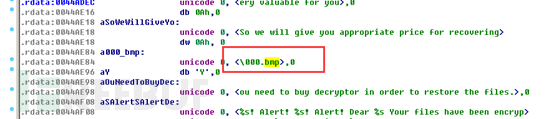
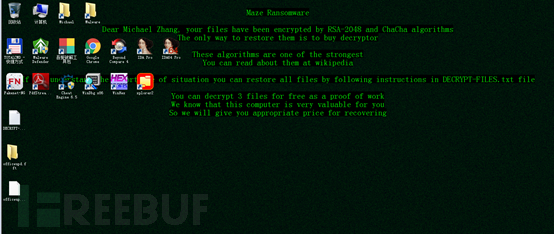
The ransomware prompt information file DECRYPT-FILES.txt is as follows:
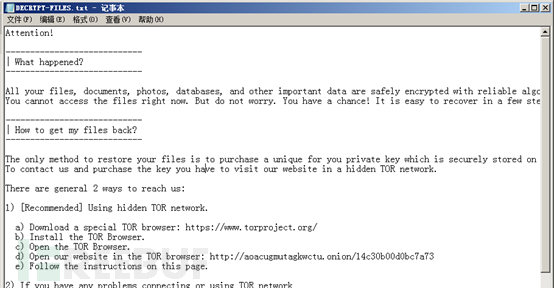
Solution
Do not click on emails and attachments from unknown sources;
Do not click on links in emails from unknown sources;
Please download applications from official websites;
Do not download and install applications randomly when browsing web pages;
Use strong passwords, avoid weak password, and change passwords regularly;
Apply all system and application patches;
Try to turn off unnecessary file sharing;
Please backup important documents. The best practice for backup is to follow the 3-2-1 rule, which means making at least three copies, saving them in two different formats, and storing the copies in different locations.
IOC
| Filesha-1 | File name | AsiaInfo Security detection name |
|---|---|---|
| 37facdc5167a2de80a4d328920579e31 | VERDI.doc | Trojan.W97M.DEDEX.S |
| e3648731a36105980f5fae6b4afe614b | officeupd.fft | Ransom.Win32.MAZE.E |
*Author: AsiaInfo Security, please indicate the source as FreeBuf.COM when reproduced
评论已关闭