Previous context
Overview of the security system architecture
Outline of the article
1. What is DDoS
2. Principles of DDoS
3. Types and characteristics of DDoS
4. Clear premise of the anti-D solution
5. How to discuss the importance of the anti-D solution with the company's higher-ups
6. Prevention of some DDoS types
7. How to choose the third-party anti-D cleaning
8. Consultation (the author's WeChat QR code is attached at the end for readers to receive free security construction consultation)
Main theme of the article
The purpose of this article is to elaborate on how to present an anti-DDoS solution to the higher-ups, what points should be paid attention to when presenting an anti-DDoS solution, and how to make an anti-D solution more persuasive to get the higher-ups to agree to implement it. The article is more inclined towards enterprise management and will discuss some basic DDoS attack types and basic defenses, without delving into the technical level. It is suitable for middle and senior security managers and party A security construction personnel to read.
Main text
Due to work reasons and some personal reasons, I have been out of the scene for a while, and the series of enterprise security system architecture analysis has been paused for nearly a year. Today, it is updated again, and the previous chapters are available from my previous【Series of articles】can be reviewed.
This time, let's talk about the construction of anti-DDoS solutions. The reason why we have moved from the previous WAF to today's anti-D is because during this period of time, we have dealt with a lot of high traffic, and my company is an Internet financial company that has been severely affected by DDoS attacks, resulting in significant losses. This article will discuss how to propose high-quality anti-DDoS solution suggestions to the company's higher-ups.
Without further ado, let's first explain what DDoS is to the higher-ups.
Definition of DDoS
Distributed Denial of Service attacks (DDoS for short, with the English meaning being Distributed Denial of Service) refer to multiple attackers at different locations launching attacks on one or more targets simultaneously, or a single attacker controlling multiple machines at different locations and using these machines to attack the victim simultaneously. Since the attack origin is distributed across different places, this type of attack is called a Distributed Denial of Service attack, and it can involve multiple attackers.
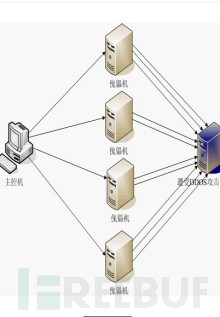
The above is the official language of Baidu Encyclopedia, translated into common language is that many clients access the server simultaneously with large traffic, which may lead to the following situations:
1. Business bandwidth is fully utilized, causing normal transaction traffic to be unable to proceed
2. Large traffic impact causes the server IP to be pulled into a black hole by the operator, resulting in all clients being unable to access
3. Large traffic impact causes server load to skyrocket, resulting in server paralysis
Among all DDoS attacks, large traffic is a characteristic. Of course, this does not include DoS attacks that exploit vulnerabilities, such as bluescreen attacks, or attacks targeting IIS, such as MS15-034. Such attacks require protection at the system and component level, such as patching or enabling security risk identification and interception products, such as WAF. So, how to distinguish malicious traffic from normal traffic in large traffic has become the focus of the solution.
The premise of the anti-DDoS solution and the high-level understanding
Firstly, before this solution was presented, when I discussed the incident analysis of DDoS attacks with the high-level management, I specifically emphasized some content. These contents must be agreed upon by everyone, otherwise, it is not necessary to consider how to solve the business disaster caused by DDoS attacks:
Since DDoS belongs to flood attack of traffic, defense against DDoS requires absorbing all the flood traffic, then performing internal screening and filtering. The server cluster performance and bandwidth requirements of the cleaning center are extremely high, and generally, enterprises cannot undertake the task of building a cleaning center. They need to rely on the power of operators. And due to the characteristics of the cloud, the boundary firewall is uncontrollable, and only three-party access can be achieved through domain name resolution.
Emphasized Analysis:
1. To resist DDoS, it is necessary to withstand peak traffic
2. Data cleaning requires extremely strong server performance, capable of quickly processing peak traffic and completing analysis and filtering functions
3. The cloud boundary firewall is uncontrollable, and before the traffic reaches the front-end load balancer, the boundary firewall of the operator and the cloud vendor will directly pull the front-end LB into a black hole. Therefore, if defense is conducted in the cloud, traffic cannot pass directly through the cloud
When negotiating the scheme with the high-level management, it is necessary to pay attention to the following points:
1. In the eyes of the high-level management, the safety officer is responsible for the overall handling of the security incident at a low cost, even zero cost
2. Once a security incident occurs, the responsibility is that of the safety officer, regardless of whether the incident is something that the safety officer can resolve
3. Once there is a cost loss, it is necessary to let the high-level management know that the safety officer will try to save costs to the fullest extent possible under the condition of meeting the needs
4. High-level concerns are about balancing input and output, so it is necessary to make an advance estimate of asset loss and the ratio of input to output
High-level Cognitive Stop-loss Algorithm
Here, I would like to introduce an algorithm
Annual Loss Expectancy (ALE) = Asset Value (AV) * Exposure Factor (EF) * Annual Occurrence Probability (ARO)
For example, a trading system can bring in 10
评论已关闭
