01/7 The core of enterprises adopting outsourcing models is to seek cheapness
The core reason for any enterprise to recruit outsourcing personnel is only one: to reduce costs. The low labor cost of enterprises is simply because the wages given to outsourcing personnel are low, and when the wages are low, the personnel turnover is necessarily high. It is easy for personnel to move, and naturally not subject to control, because leaving is just a matter of not getting along well, and this amount of money wants to endure the anger of others.
This is the true appearance of outsourcing. From the perspective of enterprises, the key words of outsourcing are cheap, high liquidity, and difficult to ensure data security.
02/7 IT architecture characteristics in outsourcing scenarios
The working mode of enterprise outsourcing personnel is divided into many types. From the perspective of the enterprise, the simplest way to divide them is on-site outsourcing and off-site outsourcing, that is, to distinguish them based on whether the outsourcing personnel stay in the company's internal office. On-site outsourcing personnel work within the company, and the company can more conveniently control the quality and efficiency of their work. The cost to the company is that it has to prepare office space and equipment, which increases the overall human resource cost.
From the perspective of outsourced personnel, the outsourcing model can be simply divided into two types: outsourcing work with centralized fixed office spaces (provided by the principal enterprise or outsourcing supplier) and outsourcing work without space restrictions (crowdsourcing and part-time model, suitable for full-time mothers and similar groups working from home).
1. Outsourcing with centralized office spaces
The principal enterprise or outsourcing supplier provides a dedicated working place and equipment for outsourcing, and coordinates management processes that are different from those of formal employees. Outsourced personnel access the principal enterprise's internal systems by jumping through VPNs in fixed office spaces.
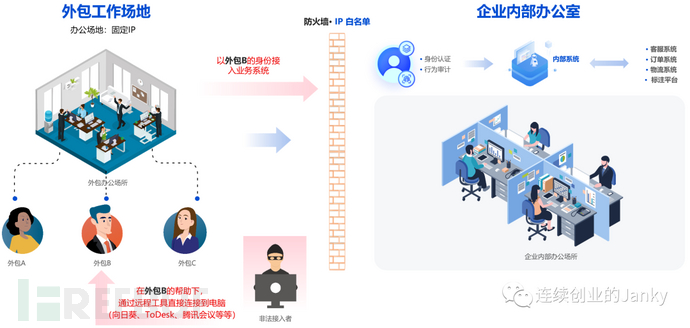
2. Crowdsourcing and outsourcing model
Full-time mothers, university students, and people with special disabilities can work flexibly as part-time employees, log in to the company's internal systems from any location through the company's VPN to carry out office work, which is suitable for regular jobs such as customer service and data annotation.
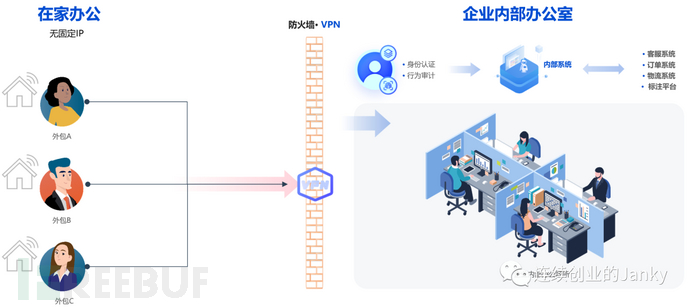
03/7 Can VPN protect data security?
No matter which office model is adopted, VPNs are indispensable. VPNs, or the zero-trust products that have been very popular in recent years, to what extent can they ensure the security of enterprise data?
In essence, for the protection of data, VPNs prevent external threats, not internal spies. In plain language, we can say that VPNs are actually to prevent mysterious hackers, a scene often seen in science fiction movies, where technical experts open a small black window on the computer, perform a series of operations, and then intrude into the company's network, wandering around freely within the company.
However, the reality we face is that for most enterprises, especially small and medium-sized enterprises, where can there be enough interest to drive hackers to specifically target your company for intrusion. Network intrusion is strictly prohibited by the state, and if caught, you will have to serve time (if you can't do the time, don't do the crime). Purely for show hackers are a minority, and those who hack into the company system have their own purposes, so they usually target the wealthy, either extorting money or stealing high-value data to sell on the black market.
The occurrence of data leakage in general enterprises is mostly attributed to those individuals who can normally use the company's systems and data. As the saying goes, it is difficult to prevent a thief in the house.This is not aimed at anyone in particular, it is aimed at everyone.
04/7 The systematic security risks of outsourcing and crowdsourcing are no different from those of formal employees.
Actually, the only security risk and cost brought about by the special identity of outsourced personnel is that they have a high level of mobility, and the company has a low control over the personnel. The regulations and security measures that work for regular employees are at least halved in effect when applied to outsourced personnel.
Just like the family planning policy at that time, with the iron rice bowl as the handle, the personnel in state-owned enterprises are tightly controlled, but for the rural areas in remote regions and various private sectors, the courage to exceed the birth limit is still great.
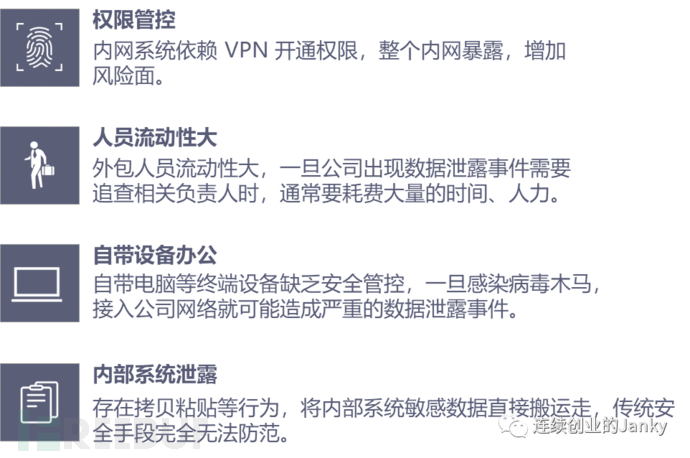
In addition, those malicious outsourced employees or formal employees, the way they truly steal company data is the same. The data security risks can be summarized as the data security risks of accessing the company's internal systems in open environments. Open environments are different from the strict isolation of internal and external networks in office modes. For those internet-based, e-commerce natured enterprises, even formal employees work in open environments on a daily basis, and home office and remote office are also of this nature.
05/7 Open office environment, where are the data security risks
The above has been proven. Whether it is outsourced personnel or formal employees, the real data security risk is actually how to protect the company's data assets in open environments. Formal employees do not gain better security protection just because they are sitting in the company's own office, and outsourced employees should not bear greater suspicion because of their natural 'being outside'.
To make everyone more intuitively aware of the data security issues in open environments, let's imagine the following scenario. In a typical internet company, employees can freely access the company's internal systems (knowledge base, CRM, OA, etc.) on their office computers, and can also access the internet at will (weibo, Taobao, CSDN code copying, following hot searches). Although employees are in the office, that is a common open office environment that we are accustomed to.
How do corporate data leak out? Let me simulate it for you. Suppose you download a data file from the company system, and then want to take this file out of the office computer, you might think of doing this:
What you are thinking | Actually |
Copy out with a USB flash drive | Such behavior is recorded and reported to security personnel by the security software on the computer |
Send out via QQ | Such behavior is recorded and reported to security personnel by the security software on the computer |
Upload to Baidu Cloud | Such behavior is recorded and reported to security personnel by the security software on the computer |
Send out an email attachment, and you also changed the file name and extension | Such behavior is recorded and reported to security personnel by the security gateways on the network |
Upload to an unknown niche cloud disk | You are likely to get what you want because the security software on your computer does not recognize this cloud disk |
Copy the file content directly to an external platform | Alright, you are really good, you almost always get what you want |
Is the result very surprising? Even though enterprises have been following the information security guidelines conveyed from the West for decades, allowing professional security teams to build an iron wall of security on office equipment, such a simple Copy/Paste can easily break through. Very few security personnel will think about it, the security methods of Europe and America are born for the PC era, for military internal networks, and to safeguard the overall social credit system of Europe and America.
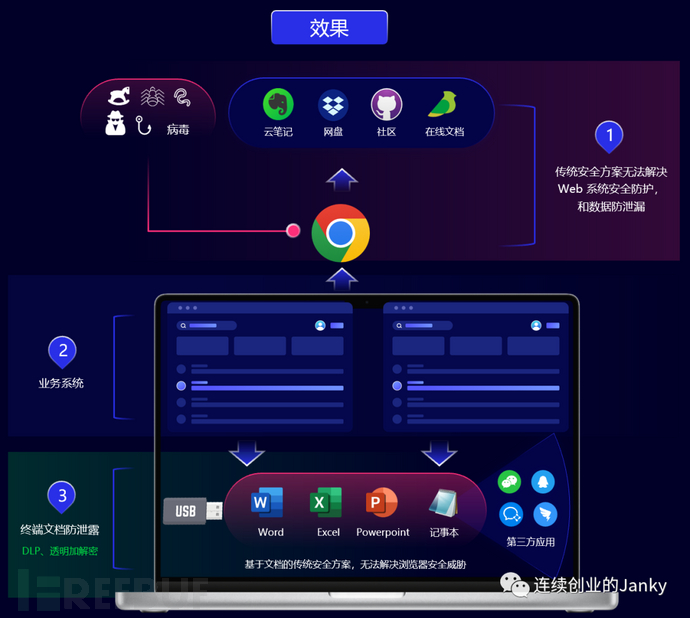
06/7 Openly use external services, and controlledly use office systems
No one wants to return to a Stone Age lifestyle voluntarily, and most enterprises cannot accept strict isolation between the internal and external networks, sacrificing efficiency for extreme security. How to balance the freedom of using the Internet and ensure the security of enterprise data, Duhu has chosen a new paradigm different from all traditional security technologies and methods, using the security office space technology provided by Shadowing to establish a digital security boundary for office systems and enterprise data, allowing the open Internet and enterprise office to be safely integrated together.
After entering the mobile Internet era, the popular saying in the security circle is that boundary thinking is outdated, but this sentence can't stand scrutiny. A more rigorous statement is that traditional boundary methods are outdated, and we need new ideas, new technologies, and new methods to establish new boundaries to protect data security.Security always emphasizes boundariesHowever, what we are experiencing is the transition from tangible physical boundaries to digital virtual boundaries, and how to draw this boundary is still in the stage of showing off or deliberately avoiding it.
The boundaries of Shadowing are drawn using a browser, dividing the office system and the Internet into a clear boundary, and using security policies to finely control the flow of data. Without changing the user experience, sacrificing office efficiency, or modifying the application system, it also solves the problem of enterprise data security.
 (Contact the author for the solution)
(Contact the author for the solution)
07/7 Outsourcing personnel earn the least money, do the dirtiest work, and suffer the greatest injustice
It is only because of the difference in编制 that outsourcing personnel have to bear such great malice, which is a common reality in the workplace. The existence of outsourcing is a blessing for many people, and it is not without helplessness to be labeled as an outsourcer. Full-time mothers, students, and people with disabilities can earn some living expenses through their own labor, which is the most commendable aspect of the outsourcing model.
However, there is still a group of people who may have been thrown out of former big companies due to the age limit of 35, or may not have a bright academic background, or may have randomly joined a well-known outsourcing company right after graduation, or may not be able to enter general enterprises due to a mismatched major. Therefore, they have been forced to undergo a role transformation as outsourcing personnel, continuing to engage in the work they are good at, and still being admitted by those甲方 companies that directly recruit but do not allow recruitment. These people are still very capable, even more so than regular employees. However, they can't help but suffer from prejudice and differential treatment everywhere, with different pay for the same work, less pay for more work, different office areas, different badges, different team-building activities, and different system permissions. Domestic甲方companies go to great lengths and pay attention to every detail to tell those hardworking outsourcers that their status is different. It is always the outsourcers who take the blame, just like when discussing data security, there is a subconscious belief that outsourcers have far greater risks than regular employees, which is absurd.
评论已关闭