Preface: Only analyze technology without discussing right or wrong, and also provide some circumvention solutions.
Writing this article is just out of curiosity about the fact that many people on a certain career APP seem to not know how PDD found out. In my personal thinking, there are two directions that can be realized:
One is technology + equipment
One is social engineering
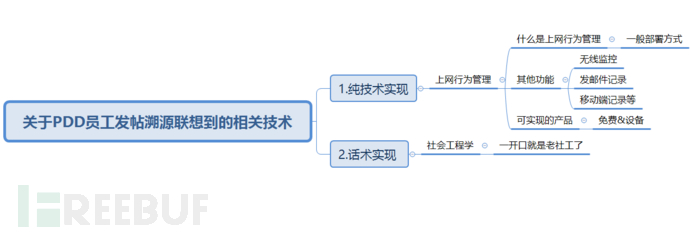
1. Pure technical analysis
There are actually many discussions about checking surveillance cameras and narrowing the scope of inspection, but it is really not necessary. Because as early as 2009, I was exposed to a domestic characteristic device: internet access behavior management.
 Currently, based on publicly available information on the internet, an APP also says it protects user information, but we need to see whether the source of user information leakage comes from the user's own network or from this side of the APP.
Currently, based on publicly available information on the internet, an APP also says it protects user information, but we need to see whether the source of user information leakage comes from the user's own network or from this side of the APP.
Based on my personal intuition, a company of PDD's scale is unlikely to not consider internet access behavior management. I think it is likely that user information leakage comes from the company's internal network of terminal users.
1.1 What is internet access behavior management
If you are interested, you can search Baidu, I will briefly explain it here
Main functions of internet access behavior management:
A: Audit the content of posts by users within the network, such as email, QQ, WeChat, APP information, etc. (Some specific encrypted information, SSL, requires the installation of plugins, and client restrictions can be set so that only plug-in users can access the internet)
B: Implement network restrictions on some specific applications such as: video websites, games,迅雷, QQ, etc., to achieve precise traffic control and complete access restriction.
C: Prohibit access to specific domain names or IPs, and access can also be opened at non-specific times.



In summary:
1. Application layer precise traffic control or prohibition of access.
2. User log auditing function.
3. Including mobile devices.
1.2 Deployment methods for internet access behavior management
Mainstream deployment methods:
Serial deployment, which means connecting the exit gateway router, or having the internet access behavior management device act as the gateway exit.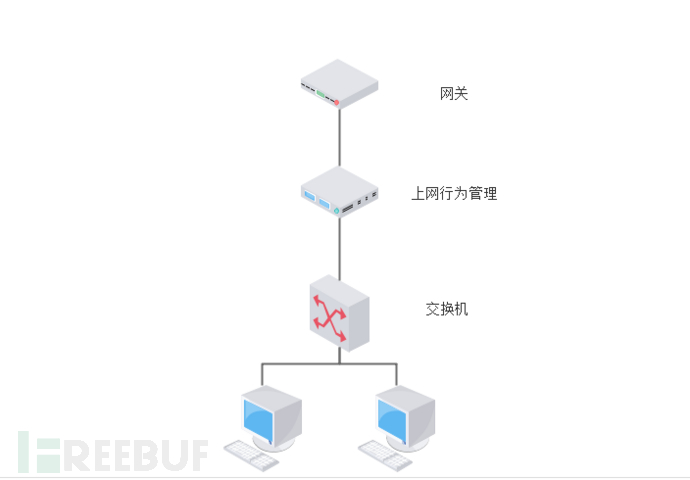
Mirror deployment: Mirror deployment only monitors log data without controlling internet access. (Similar to server log auditing and database auditing devices but only for general clients)
The illustrations I draw are relatively simple, and many actual networks may be dual-line, requiring aggregation or the use of two internet access behavior management devices.
Two, Products that can be realized
Currently, mainstream security manufacturers all have commercial internet behavior management, but in terms of technical maturity, domestic internet behavior management is relatively good for two companies: DeepinServe, Qianxin (formerly known as Netcon Technology, now acquired and merged into Qianxin ICG products). You can also consult manufacturers of interest and get user manuals and product functions for free.
Then, the free riders and the big bear will ask: Is there any open-source and free version for me to experience?
Yes, there is. You just need to buy a soft router hardware from Taobao and install the internet behavior management system to open-source deploy internet behavior management in a small company. (Generally not more than 600, there is also a classic D525 with gigabit soft router available for practice).
 If you are just playing around with virtual machines VM, you do not need hardware costs.
If you are just playing around with virtual machines VM, you do not need hardware costs.
2.1 Recommendations for open-source or free internet behavior management systems
WFilter-NGF 50 clients and below are free
It is an old product over ten years old (with a Chinese version), locally developed, taking an international route, and has weak promotion capabilities in the domestic market, with most users being overseas. It specializes in network monitoring and protocol analysis. It focuses on internet behavior management functions and has done a solid job in web filtering and protocol filtering in internet behavior management. The disadvantage is that it does not have gateway antivirus and active defense functions.
Panabit has a free version with unlimited clients
The first time I saw this company's logo, I gasped, thinking it was Umbrella.


The system itself is based on the freebsd architecture, and it also sells hardware in addition to software, and the software is free. The latest version is 9.2

 Aikua Router System
Aikua Router System
Local products, software is all free, and money is made through selling hardware. There are various rumors about the free version, so they will not be listed one by one. The basic routing functions are all there, but the internet behavior management is quite useless. The Aikua system is believed to be more inclined to do local area network wireless deployment solutions. The management of enterprises is not very good. However, the system is free, which is quite popular.
Three, How to bypass or not be monitored by internet behavior management.
Here are two ideas.
A: Use mobile data or your own hotspot to surf the internet on the mobile end
This is the easiest, basically, it is conscious. However, there are still some stricter places, and self-built hotspots will also alarm within a certain range. (Extremely extreme places).
B: Use internet behavior management that does not recognize the way to surf the internet, and you can bypass it immediately.
In simple terms, it is a global encrypted ladder and similar things. As long as the network access is encrypted when it leaves your network card, the device cannot identify it, and the internet behavior management cannot restrict you.
For example, a game website is blocked and cannot be accessed.
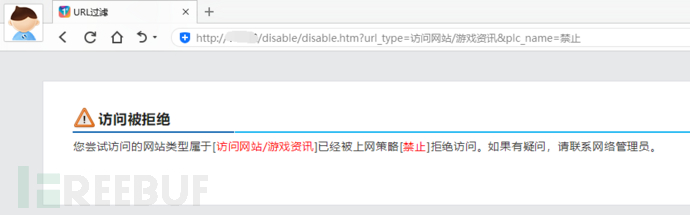
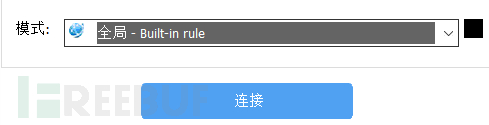
After enabling a global VPN, you can access it (the VPN needs to support a certain level of encrypted transmission).
Four, Social Engineering - Tactics Implementation
Social engineering has a group of hidden experts, that is, the seemingly harmless HRs in everyday life, who often use various tactics to manipulate you, such as salary adjustments, position changes, and optimization.
4.1 It's obvious that it's an old social worker.
The employee who was fired by PDD was too young and confessed to HR. In fact, as long as you insist that it was not posted by you, even if there is evidence of internet behavior management, no one can prove whether you were using your phone or hacked by a trojan at that time.
After all, HR can't prove that this post was posted by you. Lack of social experience, unable to withstand the questioning of the master, and after being bullied by the old HR, he confessed everything. Is it not too beautiful to make your face red? Then you confessed?
From the time the employee who was fired by PDD was summoned to his resignation in 30 minutes, it can be肯定 that HR located a group of people through video surveillance and informants among the employees, and then they would individually interview this group of people. Do you think he knows who posted it? He doesn't know either, he needs to extort the person who posted the post through interviews, key talking points: We have found that the post on XX was posted by you.
Of course, what APP you are using and what bad things you have done, your colleagues around you may also know. To be honest, everyone needs to be on guard against their colleagues, especially in some companies with a large scale, where intrigue and intrigue are also common. HR has set up many informants, and your colleagues may sell you out for a tiny bit of interest.
Combining the data of behavior management above + personal admission, it is basically as solid as a rock.
One should not have the heart to harm others, but one should always be on guard against others.
The longest road I've walked is the HR trick, and I believe many people have such a feeling during interviews or in their work.
There are many tricks that I won't describe one by one.
温馨提示
A special reminder to you.
There has been internet behavior management since 2009, basically now mainstream universities and enterprises will have internet behavior management deployment, be cautious in your words and actions, and be careful. It's just that the amount of data is large and it's difficult to screen. If something happens, you will definitely be found out for sure.
Manual dog head, if you want to cause trouble, refer to my avoidance plan.
评论已关闭
