
The main advantage of this framework is that it allows us to reuse Linux's Wi-Fi functionality to implement security tests more easily. For example, the framework can help us connect to (protected) Wi-Fi networks and broadcast beacons for test clients. Generally, any Wi-Fi functionality of Linux can be reused to implement security tests more quickly.
Wi-Fi Framework architecture
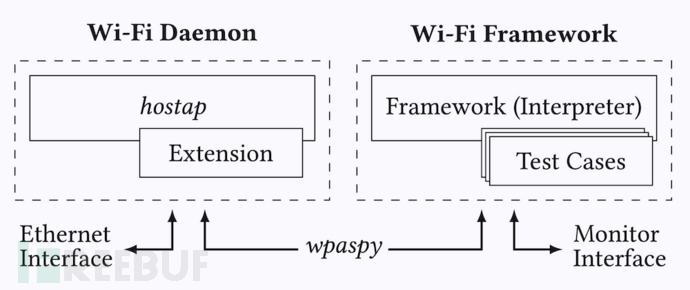
The following figure shows the architecture of the Wi-Fi daemon and framework components in the Wi-Fi Framework:
Tool installation
This framework can run on local Linux systems or virtual machines.
Firstly, we need to use the following command to clone the project source code to the local machine:
git clone https://github.com/domienschepers/wifi-framework.git
Next, use the following command to install the dependency components required by the tool:
apt-get update apt-get install git make gcc python3-venv net-tools apt-get install libdbus-1-dev libnl-3-dev libnl-genl-3-dev libnl-route-3-dev libssl-dev
After installation, use the following command to install the framework:
cd https://www.freebuf.com/articles/dependencies https://www.freebuf.com/articles/wireless/build.sh cd https://www.freebuf.com/articles/setup https://www.freebuf.com/articles/wireless/pysetup.sh
Libwifi
The libwifi library is used as a git submodule and needs to be manually installed:
git submodule init git submodule update
Tool usage
Initialize and activate the Python environment:
source setup/venv/bin/activate
Simulate Wi-Fi network interface:
https://www.freebuf.com/articles/wireless/setup-hwsim.sh 4
Run the tool and create a test case:
usage: run.py [-h] [--config CONFIG] [--binary BINARY] [--debug DEBUG] iface name
Specify network configuration information:
cd setup ln -s supplicant-wpa3-personal.conf supplicant.conf
Tool Usage Example
Assuming that we now need to test whether the client uses a zero-key to encrypt frame data, and this situation may occur during a key reinstallation attack. With the help of the Wi-Fi Framework, we do not need to reimplement all the functions of the access point, but only write the following test cases:
class ExampleKrackZerokey(Test):
name = "example-krack-zero-key"
kind = Test.Authenticator
def __init__(self):
super().__init__([
# Replay 4-Way Handshake Message 3/4.
Action( trigger=Trigger.Connected, action=Action.Function ),
# Receive all frames and search for one encrypted with an all-zero key.
Action( trigger=Trigger.NoTrigger, action=Action.Receive ),
# When we receive such a frame, we can terminate the test.
Action( trigger=Trigger.Received, action=Action.Terminate )
])
def resend(self, station):
# Resend 4-Way Handshake Message 3/4.
station.wpaspy_command("RESEND_M3 " + station.clientmac )
def receive(self, station, frame):
if frame[Dot11].addr2 != station.clientmac or not frame.haslayer(Dot11CCMP):
return False
# Check if CCMP-encrypted frame can be decrypted using an all-zero key
plaintext = decrypt_ccmp(frame.getlayer(Dot11), tk=b"\x00"*16)
if plaintext is None: return False
# We received a valid plaintext frame!
log(STATUS,'Client encrypted a frame with an all-zero key!', color="green")
return TrueThe above test cases will create an access point that a client can connect to. After the client connects, it will send 4 handshake messages to the client. Next, the vulnerable client will start using all-zero encryption for the key, and the test case will automatically detect this situation.
We can also use simulated Wi-Fi to run the above test cases:
https://www.freebuf.com/articles/wireless/setup/setup-hwsim.sh 4 source setup/venv/bin/activate https://www.freebuf.com/articles/wireless/run.py wlan1 example-krack-zero-key
Project Address
Wi-Fi Framework:【GitHub Gateway】
Reference Materials
https://github.com/vanhoefm/libwifi
https://www.krackattacks.com/#demo
https://dl.acm.org/doi/10.1145/3448300.3468261
https://github.com/vanhoefm/fragattacks
https://github.com/domienschepers/wifi-framework/blob/master/docs/EXAMPLES.md
Improving Threat Detection Capabilities with the MITRE ATT&CK Security Knowledge Framework
An unrigorous and unscientific experiment about wireless signal relay
Git leak && AWS AKSK && AWS Lambda cli && Function Information Leakage && JWT secret leak
Aftermath: A free and open-source event response framework for macOS
How to use GeoWiFi and search for WiFi geographic coordinates through BSSID and SSID
Analysis of PyTorch library RPC framework deserialization RCE vulnerability (CVE
评论已关闭