First, preface
The implementation of projects for large enterprises often involves coordination and cooperation among a large number of departments and subsidiaries, which brings about two-sided difficulties: technically, equipment and systems are dispersed and not unified, threat factors and degrees are difficult to perceive, and decision-makers find it hard to describe and make decisions on the current security situation; in terms of work progress, the degree of cooperation among the units under the customer enterprise directly affects the progress and quality of project implementation. How to do a good job in coordination and communication, and smoothly promote the implementation of the project, is also a great test for the security industry.
In this article, we will discuss how to deploy and implement big data security situation awareness projects for large enterprises by combining some cases we have implemented. I hope this article can play the role of 'throwing a brick to attract jade', and if there are better insights, I would appreciate your advice. The author is deeply grateful.
Second, project background
1Customer information

The customer is a large-scale corporate group, with more than 300 investment enterprises under its banner, over 200 fully-owned and controlled investment enterprises, and more than ten thousand employees.
2Project objectives
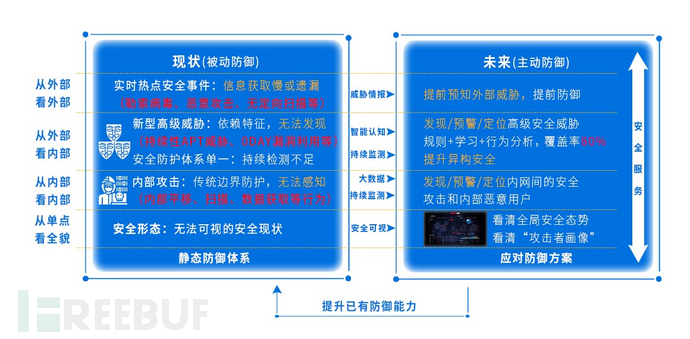
Address the defects in the horizontal security system of the group's information security, realize network-wide security perception, detection, early warning, and operation and maintenance response, combine with security services, enhance the overall security operation level, and enhance the proactive defense capabilities of security.
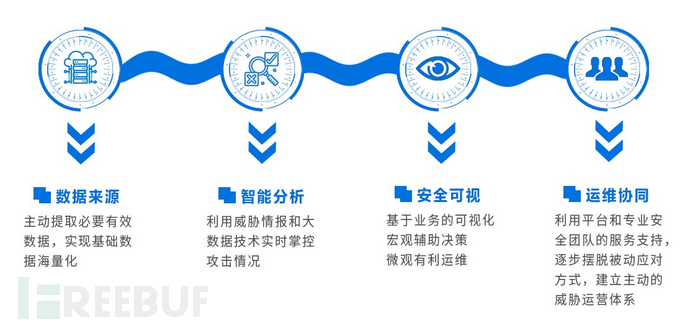
Overall project objectives
Security operation capability objectives
Operation and maintenance capability objectives
Three, solution and implementation
1Project proposal
After analysis, we finally determined such a solution:
Through the deployment of the XIAOTIAN Network Security Situation Awareness System, Cloud Eye Host Intrusion Detection and Security Management System, among which the traffic collection probe is a functional module of the XIAOTIAN Network Security Situation Awareness System, deployed in hardware form.
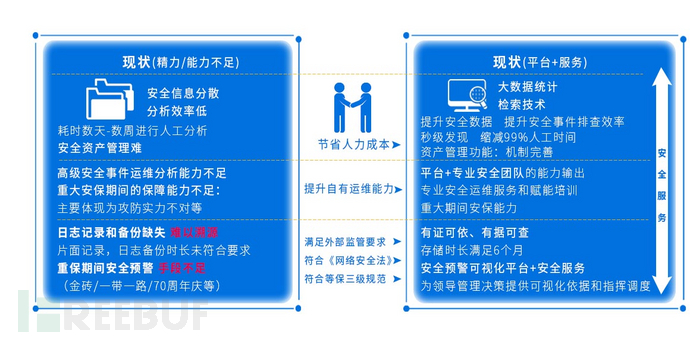
Conducting comprehensive network security data collection, utilizing big data technology, combining threat intelligence, to discover potential security threats in networks and information systems in real-time, presenting the overall security situation of the network, and assisting the group's security operation and maintenance personnel and professional security teams of manufacturers in conducting threat analysis, enhancing proactive defense capabilities.
2, personnel guarantee
To ensure the smooth implementation of the project, we have established a project team of more than 10 people, including positions such as project manager, implementation engineer, security researcher, security service engineer, R&D engineer, and test engineer.
3, implementation process
The overall deployment architecture is shown in the figure below:
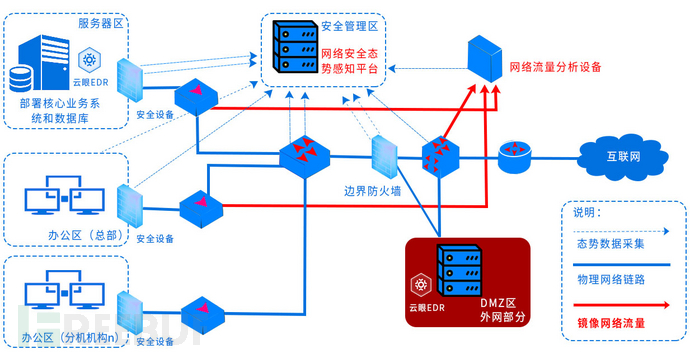
Deployment architecture logic diagram
According to the overall plan, the implementation process is divided into three stages:
First stage: software and hardware equipment online
In the scheme, the software and hardware devices included are: situation awareness platform, EDR platform, traffic analysis equipment. After the preliminary communication and on-site assessment, the situation awareness and EDR platform adopt virtualized server cluster deployment. The specific deployment situation of the situation architecture is shown in the figure below:
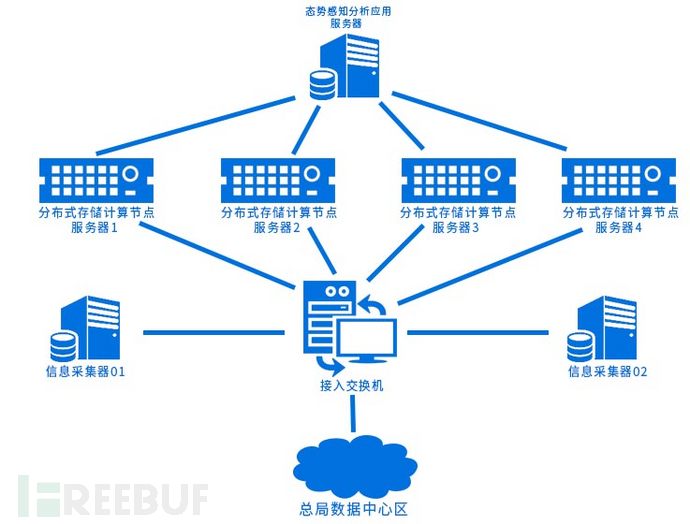
Situation awareness deployment architecture diagram
The specific EDR architecture deployment is shown in the figure below:
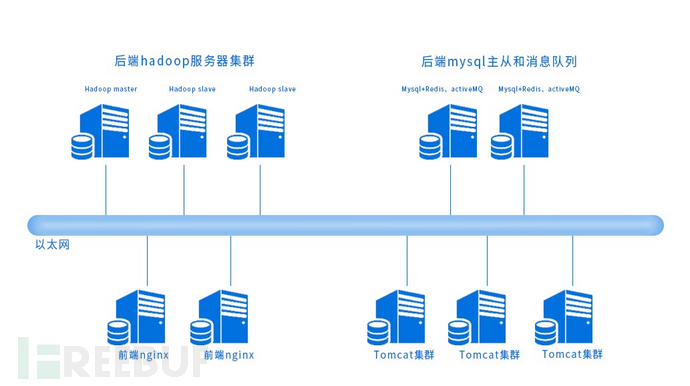
EDR deployment architecture diagram
After a week, the traffic equipment was installed, and the EDR platform and situation awareness platform were deployed according to the plan.
Second stage: data access, log generalization, debugging
Data access and debugging is the focus of the entire project implementation, with the addition of traffic analysis equipment logs pushed to the situation platform, EDR client deployment, event log push to the situation platform, and the logs of some existing security devices and security systems (XX firewall, XX switch, etc.) pushed to the situation platform.
(1) The first month: slow progress
Traffic analysis equipment: After the access traffic, the traffic analysis equipment detects various abnormal events in the group's internal network, the most serious being around 50 servers and office PCs with mining viruses, nearly 100 malicious IP addresses accessed within the internal network, and hundreds of other security alerts. After the customer saw the data, in order to sort out the extremely serious security situation of the entire internal network, the project team carried out multiple discussions and adjusted and improved the treatment plan continuously.
EDR lightweight proxy deployment: After multiple coordination and testing deployments by the project team, the deployment volume in the first month was only a dozen.Through a small number of deployments, we summarize several common problems existing in the internal network servers, mainly including two aspects: vulnerability risks and intrusion threats.
Vulnerability risks: weak passwords, critical high-risk system vulnerabilities, high-risk accounts, configuration defects
Intrusion threats: viruses, trojans, web backdoors, abnormal accounts.
Security device and security management system log generalized optimization: After the relevant device logs and security management system logs are pushed to the situation platform, after two weeks of fine-tuning and optimization of events on the platform, correlation engine optimization, various types of security data and situation elements are comprehensively analyzed and evaluated, presented from multiple dimensions and indicatorized forms, helping management decision-making and operation guidance for the execution layer.
(2) The next month: rapid advancement
The advancement of the project often requires the drive of key events, and the situation platform warned of a major virus security event in the second month, causing multiple key business systems to fail, involving more than 40 servers.
After a major security incident occurs, our project team urgently initiated the emergency response mechanism to assist the customer in handling the situation. We allocated red team attack teams, blue team audit teams, and project implementation team security engineers, worked all night to develop business recovery plans, virus detection and treatment plans, security strengthening plans, and incident analysis plans. The three most critical business systems were restored that night, and security strengthening and protection were done. For three consecutive nights, we assisted the customer in restoring all affected business systems and sorted out the tracing results, providing an initial rectification and protection plan and a subsequent rectification and protection plan.
This sudden security incident makes security protection extremely urgent. In three days, the core area server EDR deployment was expanded to hundreds of machines. The deployment and optimization of simple strategies is a complex process. Based on the issues detected by the platform, after both parties have sorted them out, the subsequent work is divided into rectification, monitoring, and protection.
Rectification: 1. Critical and high-risk vulnerabilities are repaired through the platform (delivered repair plan); 2. A large number of weak passwords are rectified within the deadline; 3. A large number of high-risk accounts are rectified within the deadline; 4. Configuration defects are rectified within the deadline; 5. Virus and trojan cleaning; 6. Baseline optimization.
Monitoring: 1. Anomaly login monitoring; 2. Integrity monitoring; 3. Process monitoring; 4. Operation audit monitoring; 5. Brute force attack monitoring.
Protection: 1. Brute force attack protection; 2. Scan protection; 3. Virus protection; 4. Minimize port protection; 5. Special server process whitelist protection.
Third phase: Expanded promotion trial operation
Promote the connection of all network device logs, all server system logs, all application website logs, promote the deployment of EDR on all servers, and the governance of platform security data.
IV. Project Achievements
By connecting to the network traffic of 10G and above, deploying more than 1000 EDR nodes, and connecting security logs, over 800 threat events were analyzed, and security issues were handled for assets: over 200 servers, over 300 PC terminals. The situational awareness platform discovered a large number of attacks that penetrate the existing security system, and after the special project group's treatment, the network security situation was restored to a good state, the number of compromised servers dropped to 0 per day, and the number of compromised terminal PCs was less than 3 per day, and the overall security is at a level that can be perceived and controlled.
V. Summary
The implementation of projects in large enterprises involves coordination with many departments and subsidiaries, and requires strong support from the customer's decision-making level.
Security incidents are a double-edged sword. On the one hand, they bring very difficult impacts to customers, but on the other hand, they can also bring qualitative changes to the advancement of the project.
The situational awareness platform is a system that requires a large amount of data support, and the host EDR capability can exactly provide a large amount of key data for the situational awareness platform. By associating, analyzing, and intelligently analyzing massive logs, it can monitor the network security information of key information infrastructure in real-time, perceive major cyber attacks in real-time, and further explore the accurate assessment of attack damage, and promptly warn and deal with threats and hidden dangers to key protected targets.
*Author of this article:Safedog, please indicate the source as FreeBuf.COM when reproduced
评论已关闭