1. Mini-program decompilation
Environment preparation
1. Prepare node environment
Download link:https://nodejs.org/en/

The project address comes from:https://github.com/xuedingmiaojun/wxappUnpacker
Specific operations
1. Obtain the mini-program on WeChat PC
Before opening the mini-program with WeChat PC, it is best to find the path of the locally cached mini-program package, generally it is in the WeChat PC installation directory\WeChat Files\WeChat Files\Applet
For example, mine is installed in the root directory of D disk, so the path is: D:\WeChat\WeChat Files\Applet
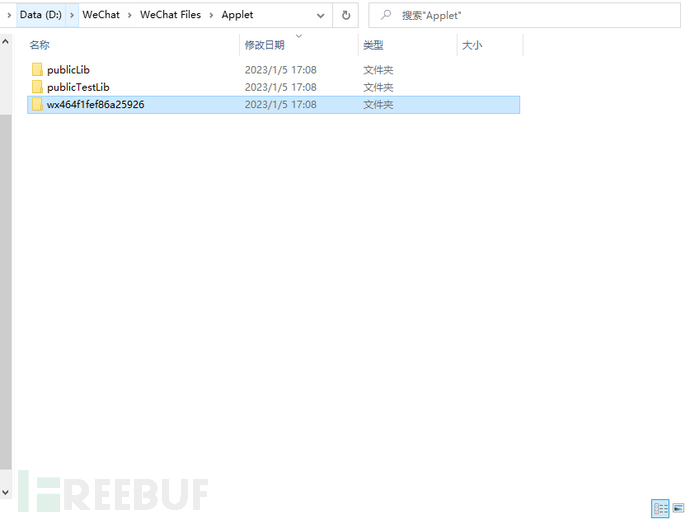
In the figure above, each wx folder represents a mini-program, generally the latest opened mini-program is the first one, if uncertain, you can sort by modification date
Once we find the path, we can open the mini-program with WeChat PC, after opening it, we will find that a new folder has been added to the current directory, which contains the encrypted mini-program package
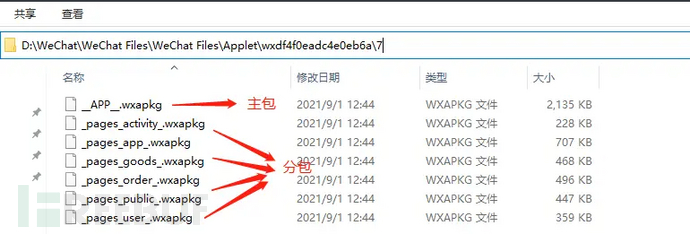
2. Decrypt the package
The package we just obtained cannot be decompiled yet, we must go throughDecryption softwareModification is required to decompile
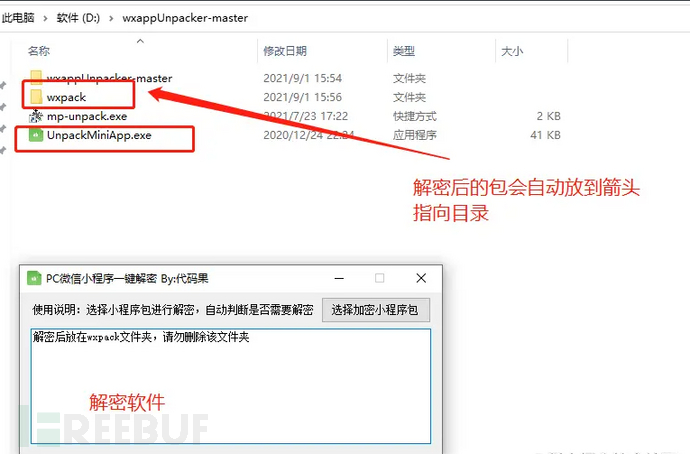
This article demonstrates the process of decompiling a main package and a分包, first modify the main package through the decryption tool
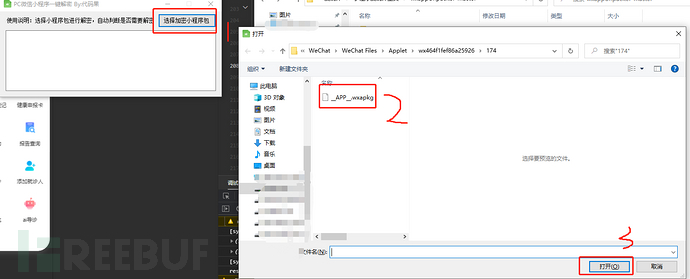
The decrypted main package automatically comes to the wxpack package, the same steps are used to decrypt a分包, the following image is the decrypted one I have done

3. Decompilation
Enter the同级目录 wxpack的同级目录 wxappUnpacker-master, type cmd in the path bar to automatically open the command window of the current directory
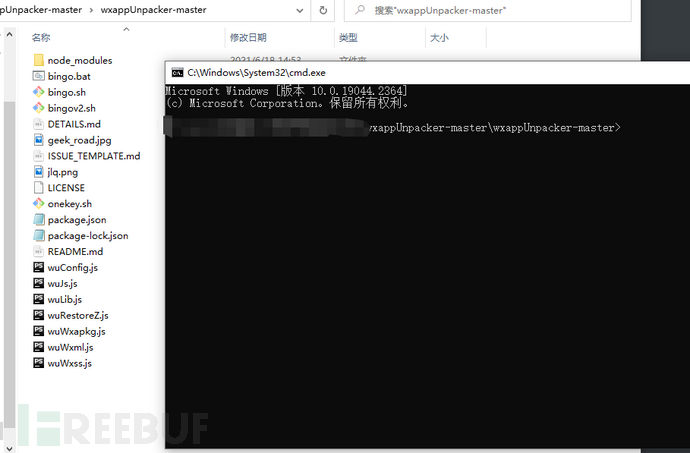
First decompile the main package, and put the decompiled folder intowxpackIn the same directory level
node wuWxapkg.js ..\wxpack\wx464f1fef86a25927.wxapkg
-sIndicates the分包The first one
..\Indicates the output location..\wxpack\_pages_app.wxapkgThe分包 location that needs to be decompiled
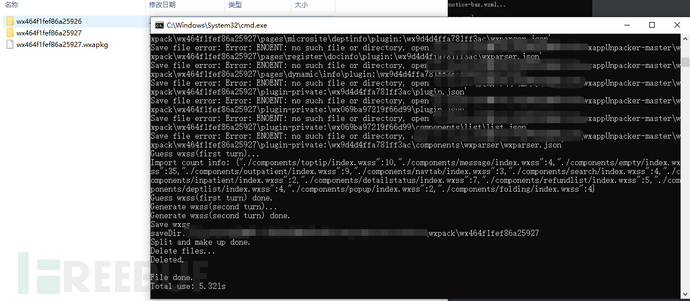
Then import the folder we obtained into the developer tool or notepad++ to view the code, here we import the developer tool
2. Find related js vulnerabilities
The global search decryption finally locates the code block in request.js by checking the code
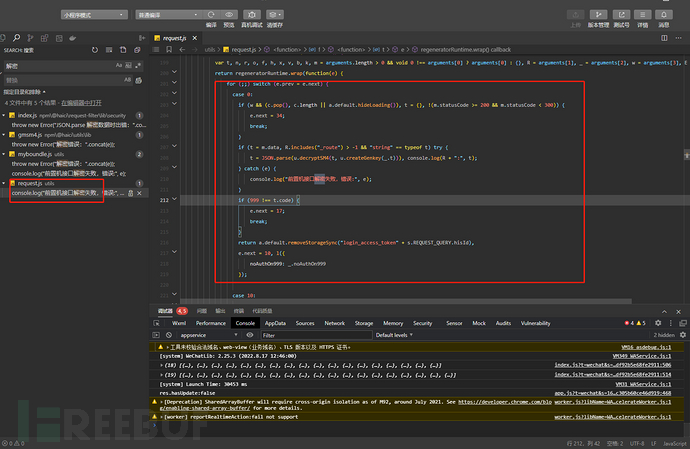
Enter the folder of request.js
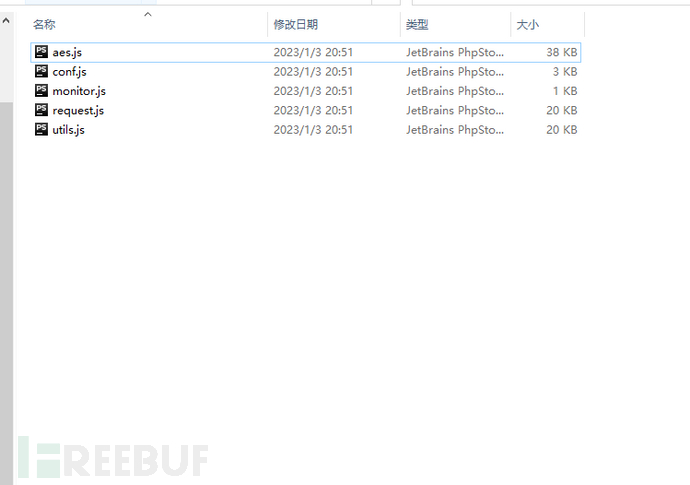
3. Modular loading
Browserify should be installed in advance
3.1. Browserify
Browserify allows you to organize browser-side Javascript code in a way similar to node's require(). By precompiling, it allows front-end Javascript to directly use some libraries installed by Node NPM.
3.2. Installation
Admins open cmd (normal users may fail to install)
npm install -g browserify
3.3. Package the js file
browserify request.js > myboundle.js
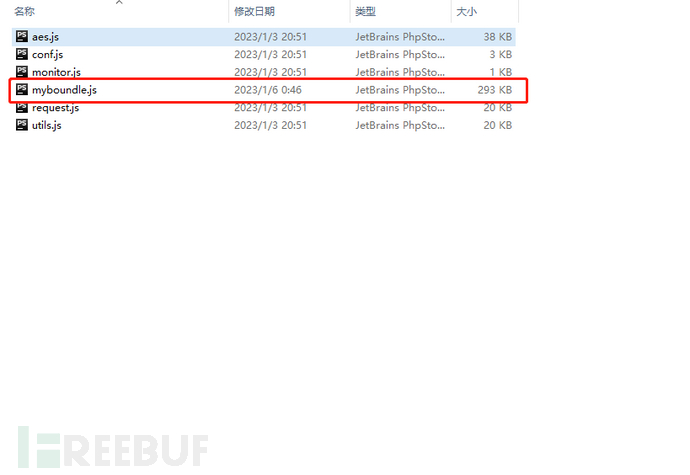
3.4. Modify the js code
var data="WVMNBlsFBgQKWVEPBVgABAFXUFEKVlAGBlRWXVdeWlxRAQcBWQRQUA0GUgcGWwcMAFsBVARRDVkMU1kCBgALWFlfAltQCQIDDFheBV9RB1dXUAMPB1gBAwYHXlZdUA0LVgEDCVlcAF4KCFYAX1ALB1oDBQcAUVQNV1AHUwAAXANYAgwHCABTCVELWg8LAVAFUFAPV19TCQoLWFVdVwpRBAMLDVJYUFFQCQRQXQNbWggDBlADX1UIVg1TBlcKX1AIAg0CUQMFWFcKBlwLUVEHDlBaVF0HCFQDDlULUV0ABQUCXQUNVwg="
var t = JSON.parse(u.decryptSM4(data, u.createGenkey("202300")));
console.log(t)Place the above code in the code block we located
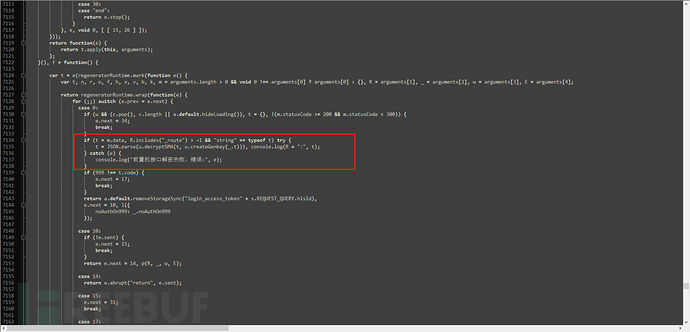
Place it in a suitable position below, note that it should not be inserted into other functions, otherwise it will not start when accessing the page
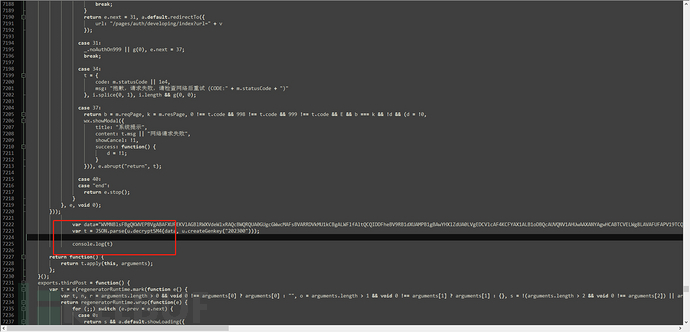
3.5. Write an html file and import the js file
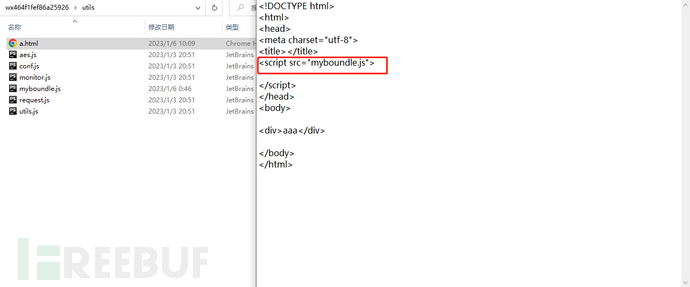
3.6. Access the page and view the console
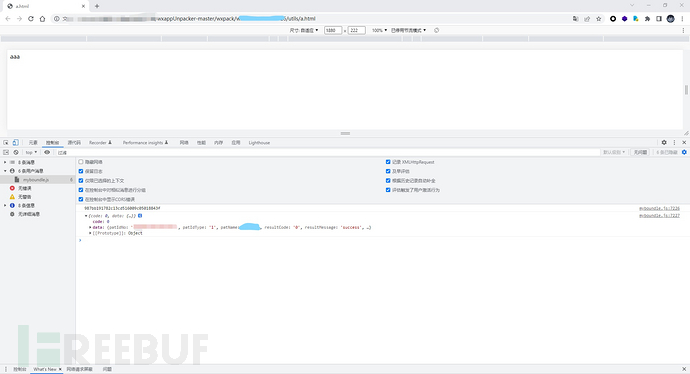
4. Summary
In general, when encountering data leaks or other encrypted data that requires decryption, and when there is no time to view the code and reverse engineer it, this method can be used, which can save a lot of time and is almost an essential skill for laziness. This method is actually similar to integrating the entire js document into a single file, which avoids confusion. Even after the code is obfuscated, this method can still be referred to, because after integrating all the code, even if it is obfuscated, it is still recorded in the same file, so it can be successfully decrypted.
评论已关闭